- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov, Den Iuzvyk
Created: 5/10/2021
Last Updated: 5/14/2021
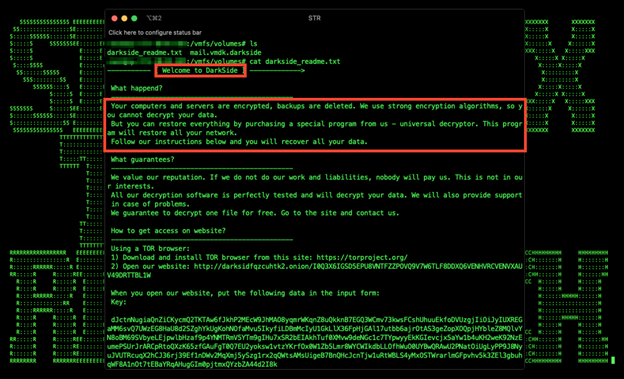
Figure 1: Darkside/RE$HOOD Ransomware Attack in Progress
Introduction
Securonix Threat Labs R&D/Securonix Threat Research team has been actively monitoring and investigating the details of the critical targeted Darkside ransomware attacks (tracked by Securonix Threat Research as RE$HOOD) with some of the recent victims including Colonial Pipeline Networks, and many others (see Figure 1).
Darkside/RE$HOOD is an active malicious ransomware operator (MRO) that also offers a ransomware-as-a-service (RaaS) affiliate program. Securonix Threat Research has observed at least 64 victims being exploited by Darkside/RE$HOOD MRO or its affiliates since January 2021.
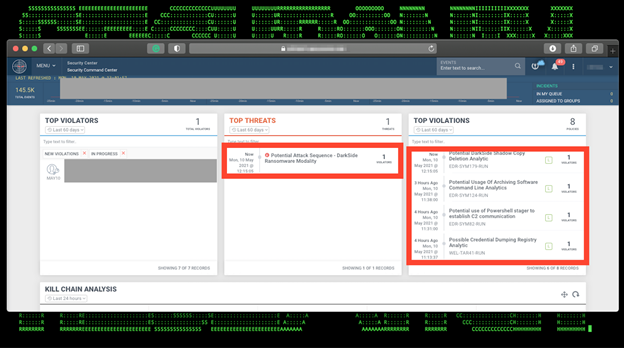
Figure 2: Example of the Darkside/RE$HOOD MRO Detection in Securonix Labs
Darkside/RE$HOOD Attacks – Detection Update
Based on the initial security analysis results of the malicious artifacts associated with the Darkside/RE$HOOD threat and its affiliates performed by Securonix Threat Labs, we’ve confirmed that some of the existing Securonix Behavior Analytics/Security Analytics can help detect the malicious behaviors/activity associated with the Darkside ransomware attacks (see Figure 2).
Some high-level examples of some of the relevant Securonix behavior analytics/predictive indicators to increase the chances of early detection of the malicious activity associated with the Darkside/RE$HOOD, including potential future variants of attacks, include:
- Potential Use of Powershell Stager to Establish C2 Communication Analytic
- Potential Exfiltration RClone Process Analytic
- Possible Decoding PE or DLL From b64 Via Certutil Analytic
- Possible Credential Dumping Registry Analytic
- Potential DarkSide/RE$HOOD Shadow Copy Deletion Analytic
- Potential Exfiltration MEGAcmdShell Process Analytic
and others.
Darkside Attacks – Threat Hunting – Sample Spotter Search Queries
Please find below some examples of the trivial Spotter queries to assist with initial threat hunting/retrohunting/identifying some possible attack behaviors based on the details above.
Note: Because of the rapidly changing attack landscape, the recommendation is not to rely on static IOAs/queries alone and to also implement the relevant Securonix analytics/predictive indicators for the best possible protection.
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND destinationprocessname ENDS WITH “powershell.exe” AND resourcecustomfield1 CONTAINS “a7e08519-4a54-6099-4d02-000000000400”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND resourcecustomfield1 CONTAINS ” a ” AND ((resourcecustomfield1 CONTAINS “-hp” OR resourcecustomfield1 CONTAINS “-p” OR resourcecustomfield1 CONTAINS “-dw” OR resourcecustomfield1 CONTAINS “-tb” OR resourcecustomfield1 CONTAINS “-ta” OR resourcecustomfield1 CONTAINS “/hp” OR resourcecustomfield1 CONTAINS “/p” OR resourcecustomfield1 CONTAINS “/dw” OR resourcecustomfield1 CONTAINS “/tb” OR resourcecustomfield1 CONTAINS “/t”) OR (resourcecustomfield1 CONTAINS “-p” OR resourcecustomfield1 CONTAINS “-sdel”))
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND (resourcecustomfield1 CONTAINS “DownloadFile(” OR resourcecustomfield1 CONTAINS “Invoke-WebRequest” OR resourcecustomfield1 CONTAINS “Invoke-Shellcode” OR resourcecustomfield1 CONTAINS “Net.WebClient”) AND (resourcecustomfield1 NOT CONTAINS “webex” AND resourcecustomfield1 NOT CONTAINS “MicrosoftEdge”)
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND (resourcecustomfield1 CONTAINS “save” OR resourcecustomfield1 CONTAINS “export”) AND (resourcecustomfield1 CONTAINS “hklm\sam” OR resourcecustomfield1 CONTAINS “hklm\system” OR resourcecustomfield1 CONTAINS “hklm\security”)
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND destinationprocessname ENDS WITH “certutil.exe” AND (resourcecustomfield1 CONTAINS “.dll” OR resourcecustomfield1 CONTAINS “.exe”)
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” and (resourcecustomfield1 CONTAINS “DllHost.exe” and resourcecustomfield1 contains “/Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}” OR resourcecustomfield1 CONTAINS “/Processid:{D2E7041B-2927-42fb-8E9F-7CE93B6DC937}”)
and others.
Darkside/RE$HOOD Attacks – Additional Technical Analysis and Recommendations
Log/Data Sources
To increase the chances of detecting this malicious activity associated with the Darkside/RE$HOOD MRO earlier, some of the recommended log/data sources to collect/leverage:
- Powershell logs
- Proxy logs
- Raw EDR logs
- Storage/Backup system logs
- RDP Logs
- VPN/jump server logs (e.g. Citrix)
- Network appliance logs
- MFA/authentication logs
- Firewall logs
and others.
Mitigation
Here are some of the Securonix recommendations to help customers prevent and/or mitigate possible attacks by Darkside/RE$HOOD MRO more effectively:
- Review your backup version retention policies and make sure that your backups are stored in a location that cannot be accessed/encrypted by operator placed targeted ransomware. (e.g. consider remote write-only backup locations)
- Review your MFA conditional access policies to implement detection and mitigation procedures to enable early detection and mitigation of possible MFA bypass attack vectors relevant to the MFA implementations leveraged within your organization.
- Implement security monitoring for your automated backup systems to enable early detection of possible malicious disruptions by ransomware operators and affiliates as part of a potential breach.
- Implement security monitoring, particularly for high-value targets (HVT), including users and critical systems in your environments to detect possible malicious ransomware operator placement activities earlier.
- Follow the relevant ransomware frameworks and guidelines from CISA, IST, NIT, UK National Cyber Security Centre, Europol, and other relevant entities to help mitigate ransomware risk.







