- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of industry leading top threats monitored and analyzed by Securonix Threat Labs during the month of August. The report additionally provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
During the month, Threat Labs analyzed and monitored multiple major threat categories, including several ransomware operations, malware campaigns, attacks on hospitality and travel firms, persistent phishing and credential theft campaigns leading to intrusions and data theft from Russia and the SEABORGIUM threat actor. Of note was an attack in the beginning of the month on Cisco by Yanluowang ransomware group which breached its corporate network in late May. The attackers could only harvest and steal non-sensitive data from a Box folder linked to a compromised employee’s account. The vulnerability was identified in the Ring Android app that exposed the data and camera recordings of Ring app users on Android devices.
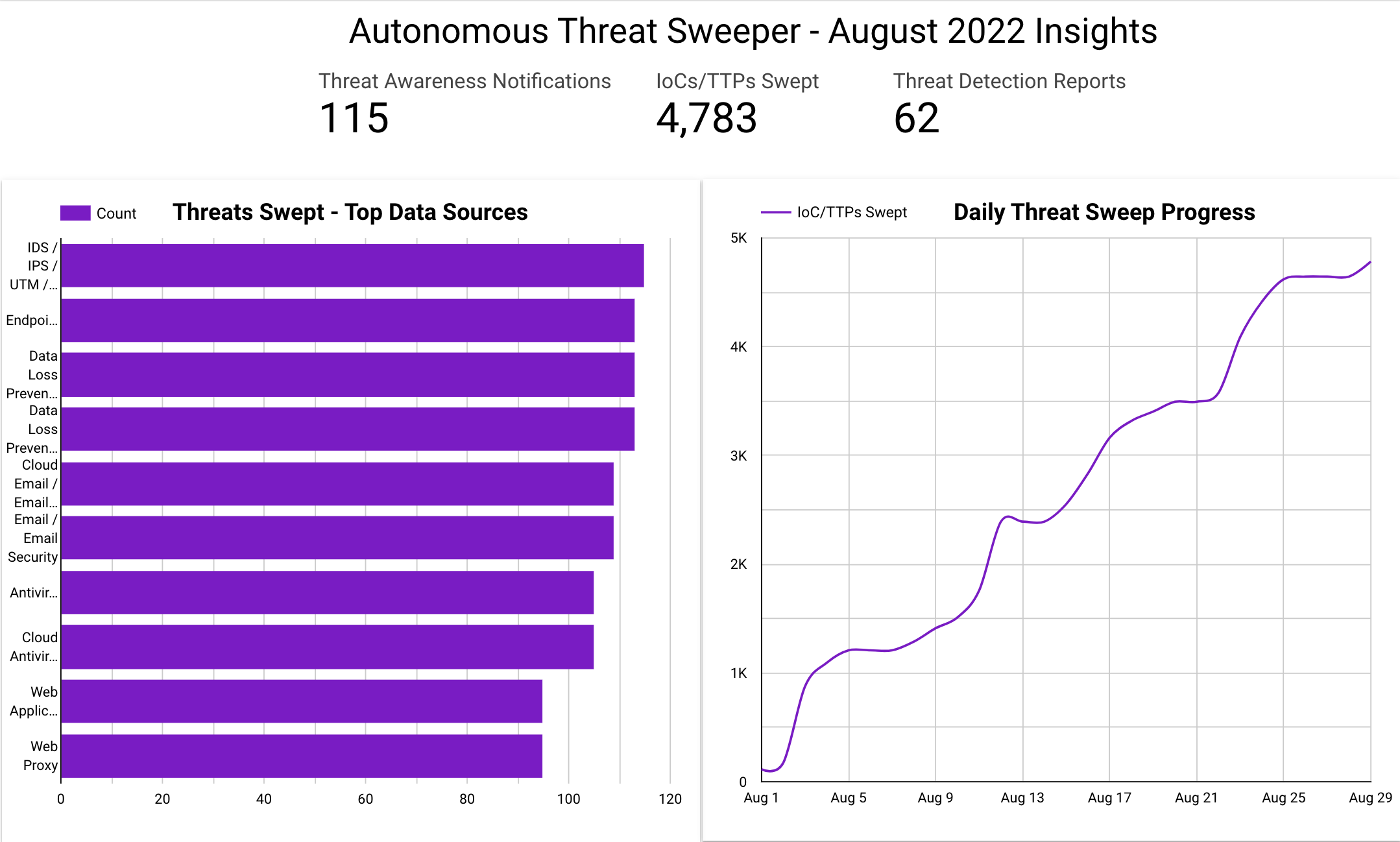
In August, Securonix Autonomous Threat Sweeper identified 4,783 IOCs, 115 distinct threats, and reported 62 threat detections. The top data sources swept against include endpoint management systems, cloud application security broker, web proxy, and web application firewall.
Yanluowang ransomware group
(Originally published on August 2022)
According to Cisco, on 24 May 2022, the Yanluowang ransomware group breached their corporate network. It was caused by a phishing attack targeting one of their employees’ Google accounts that contained corporate credentials. In addition, the hackers were only able to find and steal non-sensitive information from the folder in that employee’s account. Cisco reported that the threat actor has been removed from the environment and has shown persistence by repeatedly attempting to gain access in the weeks following the attack. However, none of these attempts were successful.
Threat Labs summary:
- Threat Labs observed that the threat actor maintained access, minimized forensic artifacts, and increased access to systems after obtaining initial access.
- Observations from Threat Labs suggest the attack was carried out by an adversary previously referred to as an initial access broker (IAB) associated with UNC2447, Lapsus$, and Yanluowang ransomware.
- Securonix Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 96 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the threat actor/vector that can be detected include but are not limited to the following. We recommend these actions:
- Monitor for the rare and suspicious commands attempting to dump NTDS from domain controllers.
- Example: powershell ntdsutil.exe ‘ac i ntds’ ‘ifm’ ‘create full c:\users\public’ q q
- Monitor for the abnormal spike in SMB (TCP/445) traffic from domain controllers.
- Monitor for the combination of new accounts created, addition of these accounts to the local administrators group and subsequent removal of the previously created local administrator account.
- Example: C:\Windows\system32\net user z Lh199211* /add
- C:\Windows\system32\net localgroup administrators z /add net user z /delete
- Monitor for the rare and suspicious commands to dump hashes from SAM via registry.
- Example: reg save hklm\system system
- reg save hklm\sam sam
- reg save HKLM\security sec
- Monitor for modification of firewall configurations to enable RDP access to systems.
- Example: netsh advfirewall firewall set rule group=remote desktop new enable=Yes
- Monitor for the execution of utilities and commands to clear event logs.
- Example: wevtutil.exe el
- wevtutil.exe cl [LOGNAME]
- Monitor the spike in installation of remote access tools, such as TeamViewer and LogMeIn.
- Detect attackers carrying out Windows logon bypass techniques where they leverage sethc.exe and narrator.exe to get a command prompt without logging in to the system.
- Example: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe /v Debugger /t REG_SZ /d C:\windows\system32\cmd.exe /f
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe /v Debugger /t REG_SZ /d C:\windows\system32\cmd.exe /f
Tags: Adversaries: Yanluowang ransomware, Lapsus$, UNC2447 cybercrime gang | Target: Cisco | Tool: Cobalt Strike, PowerSploit, Mimi Katz, Impacket
Manjusaka offensive framework
(Originally published on August 2022)
An offensive framework developed by Chinese threat actors called Manjusaka, which is related to Sliver and Cobalt Strike, has been observed targeting both Windows and Linux. In addition to being fully functional, the command and control framework has a user interface in simplified Chinese and can generate new implants with customized configurations easily, increasing the likelihood that malicious actors will adopt this framework more widely.
Threat Labs summary:
- Securonix Threat Labs has continued to monitor actively running campaigns by Chinese threat actors called “Manjusaka” as it began spreading rapidly.
- Threat Labs has observed that the campaign uses lure documents themed around COVID-19 and the Haixi Mongol and Tibetan Autonomous Prefecture and Qinghai Province. On infected endpoints, Cobalt Strike beacons were delivered by these maldocs.
- Threat Labs encourages all organizations to be diligent against such easily available tools and frameworks that can be misused by a variety of threat actors.
- 14 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Tool: Manjusaka, Cobalt Strike, Sliver | Target: Windows, Linux | Threat Actor Location: China
IcedID malware dominant in August
(Originally published on August 2022)
Securonix Threat Labs has continued to monitor top malware activities and observed the IcedID threat that has been circulating lately. This IcedID malware continues to be an active malware in our current threat landscape.
This month the IcedID threat circulated multiple times with different exploits. IcedID is a service provider that has been tracked as a direction to ransomware, but also has been noted on the “dark web” service that can be used to load some of the ransomware itself.
This month multiple researchers from Walmart Global Tech Blog, Palo Alto Unit 42 Intel, and ISC SANS published their analyses and observations. Walmart Global tech Blog mentioned PrivateLoader continues to function as an effective loading service, recently leveraging the use of SmokeLoader for their payloads. By collecting some sample domains it indicated that these domains are simply proxies but behind them sits a massive operation performing millions of loads for various customers. Also, Palo Alto Unit 42 Intel Unit monitored OSINT sources and identified a new infection of IcedID delivering CobaltStrike which was posted on Twitter reporting that the IcedID (Bokbot) infection led to CobaltStrike. An ISC SANS researcher further provided their analysis of IcedID malware using Dark VNC activity and Cobalt Strike. This method was used by threat actor Monster Libra (also known as TA551 or Shathak) who has started distributing a new IcedID infection generated from a password-protected zip archive sent by Monster Libra.
Threat Labs summary:
- Threat Labs has continued to monitor the IcedID malware campaign after it began spreading rapidly.
- Threat Labs has observed that the campaign IcedID aka BokBot mainly targets businesses and steals payment information; it also acts as a loader and can deliver other viruses or download additional modules.
- Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 83 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the threat actor/vector include but are not limited to the following. We recommend these actions:
- Monitor for macros-enabled attachments from email.
- Monitor for persistence from suspicious scheduled tasks that are created post the execution of the macros-enabled attachment.
Tags: Malware: Dark VNC, Cobalt Strike, Bokbot, IcedID, PrivateLoader, SmokeLoader | Target: user financial information |
Zeppelin ransomware
(Originally published on August 2022)
This month both CISA and the FBI have observed and warned about the revival of the Zeppelin malware targeting a range of critical infrastructure organizations by exploiting RDP and firewall vulnerabilities.
First seen in 2019, the agencies warn that Zeppelin ransomware is back recruiting new exploitations and encryption tactics in campaigns against industries particularly healthcare and critical infrastructure organizations.
Zeppelin actors are accessing victim networks through RDP exploitation, SonicWall firewall vulnerabilities, and phishing campaigns.
Threat Labs summary:
- Threat Labs has continued to monitor Zeppelin actors’ activities.
- Zeppelin actors trick users into clicking on malicious attachments disguised as advertisements to execute malicious macros.
- Zeppelin actors request ransom payments in Bitcoin, which range from several thousand dollars to over a million dollars.
- The threat actors also have a double extortion strategy model by threatening to leak stolen files in case the victims don’t pay the ransom.
- 144 IOCs are available on our Threat Labs home page and automatically swept against Securonix Autonomous Threat Sweeper customers.
Tags: Malware: Zeppelin, Vega, RaaS | Target: Medical, Healthcare, Technology, Defense, Critical Infrastructure
Malware campaigns leveraging “Dark Utilities” platform
(Originally published on August 2022)
Recently, ‘Dark Utilities‘, a C2 platform that provides adversaries with full-featured capabilities, was released. It is marketed as a method of enabling remote access, command execution, distributed denial-of-service (DDoS) attacks, and cryptocurrency mining operations on infected systems. Additionally, It supports Windows, Linux, and Python implementations at a starting price of just EUR 9,99. The servers are hosted in the Interplanetary File System (IPFS), making them resilient to content moderation and law enforcement interference.
Threat Labs summary:
- Threat Labs has continued to monitor the threat actors’ activities as it began spreading rapidly once again.
- Securonix Threat Labs has identified that the platform is hosted on the clear internet and Tor network with roughly 3,000 users enrolled.
- Threat Labs encourages all organizations to be aware of these C2aaS platforms and ensure that they have security controls in place to help protect the environment.
- 71 IOCs are available on our Threat Labs home page and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Platform: Dark Utilities | Attack Type: Remote access, Command Execution, Distributed denial-of-service (DDoS), Cryptocurrency Mining | Target devices Windows, Linux, Python-based
SEABORGIUM phishing campaign
(Originally published on August 2022)
A Russia-linked threat actor SEABORGIUM’s phishing campaign was interrupted by Microsoft. The campaign is persistent hacking and targeting people and organizations in NATO countries for credential and data theft, intrusions, and hack-and-leak campaigns tied to espionage.
The threat actors have been using the information to impersonate individuals known to the target and contacted them using new email accounts with email addresses or aliases configured to match the names or aliases of the impersonated individuals, Microsoft said.
Threat Labs summary:
- Threat Labs has continued to monitor the threat actors’ phishing campaign.
- Based on some of the observations, Microsoft suspects that the threat actor uses social media platforms, personal directories, and general open-source intelligence (OSINT) to support their reconnaissance efforts.
- Threat actors could use fake identities to contact targeted individuals and trick them into downloading attachments sent through phishing messages.
- Phishing messages used PDF attachments or links to file or document hosting services, or to OneDrive accounts hosting the PDF documents.
- 69 IOCs are available on our Threat Labs home page and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Malware: SEABORGIUM, Phishing, Microsoft | Target: Higher Education, Consulting, Defense, Government |Threat Actor Location: Russia
Orchard botnet
(Originally published on August 2022)
Orchard, a new botnet, uses the account transaction information of Bitcoin creator Satoshi Nakamoto to generate domain names in order to hide its command-and-control infrastructure (C2). An important characteristic of this botnet is that it belongs to a family of botnets that uses DGA technology. Its latest version is for mining and using more unpredictable information, such as transaction information of Bitcoin accounts, as input to DGA, making detection more difficult. It has appeared in three different versions with varying programming languages and DGA implementations, indicating the Orchard botnet family remains active and demands our attention. Additionally, it infects USB storage devices to spread malware by uploading device and user information.
Threat Labs summary:
- Threat Labs has continued to monitor Orchard Botnet with the rise of recent activity.
- According to a report, over 3,000 hosts in China have been victimized by the malware.
- Securonix Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 24 IOCs are available on our Threat Labs home page and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Malware: Orchard Botnet, XMRig mining program
TA558 targets hospitality and travel firms
(Originally published on August 2022)
Small threat actors, namely the TA558 group, are targeting hospitality, hotel, and travel organizations primarily with Portuguese and Spanish speakers. The group operates typically in Latin America, but they are also targeting Western Europe and North America. It uses multiple malware in its attacks, including Loda RAT, Vjw0rm, and Revenge RAT, by using phishing campaigns with hotel booking lures. As a result, the malware was repurposed to steal personal and financial data from hotel customers, including credit card information, perform lateral movement, and deliver additional payloads.
Threat Labs summary:
- Securonix Threat Labs has continued to monitor actively running campaigns by Latin America threat actors TA558 as it began spreading rapidly.
- Threat Lab has observed that since 2018, this group has employed consistent tactics, techniques, and procedures to attempt to install a variety of malware, including Loda RAT, Vjw0rm, and Revenge RAT.
- According to Threat Labs, operational tempo was higher than previously observed for TA558, during 2022.
- Threat Lab has observed TA558 adopting new tactics, techniques, and procedures in its campaigns in place of macro-enabled documents.
- 30 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the threat actor/vector that can be detected include but are not limited to the following. We recommend these actions:
- Look for rare powershell commands executed with unusual urls which are used to download and execute the AsyncRAT.
- Check for unusual scheduled tasks execution where the persistence is achieved by masquerading services such as spotify.
Tags: Adversaries: TA558 | Malware: Loda RAT, Vjw0rm, Revenge RAT | Target Geo-Location: Portugal, Spain, Western Europe, North America | Threat Actor Location: Latin America
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Github page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Dhanaraj K R , Tim Johny, Mohammad Zibran, Sina Chehreghani







