- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
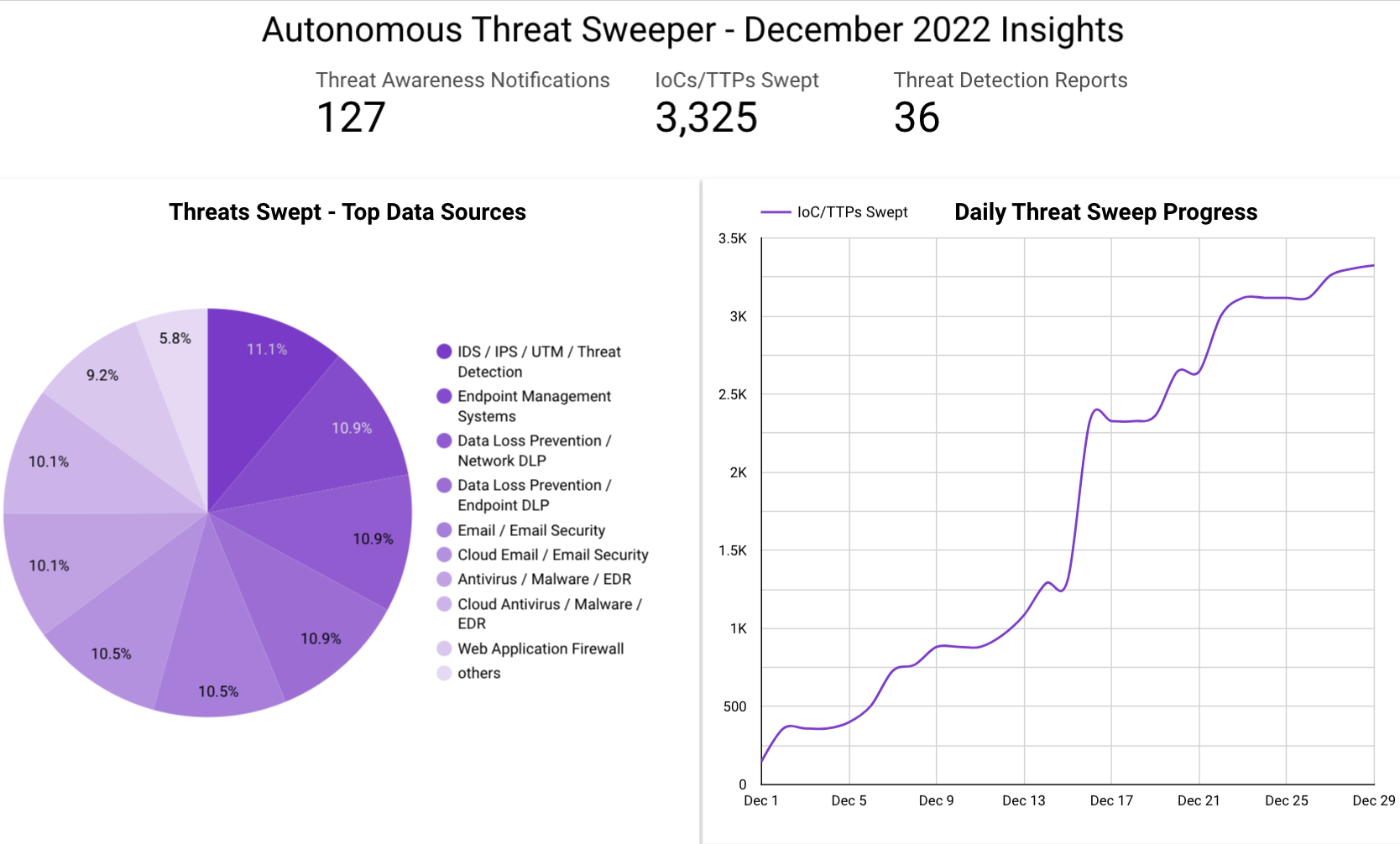
The Monthly Intelligence Insights provides a summary of curated industry leading top threats monitored and analyzed by Securonix Threat Labs during December. The report additionally provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In December, Threat Labs has analyzed and monitored major threat categories, including multiple cyber campaigns involving ransomware and malware. Of note are new threat groups named Agrius, STEPPY#KAVACH which is targeting Israel, the United Arab Emirates, and India. In addition, Signed Microsoft drivers use in ransomware attacks, FortiOS SSL-VPN vulnerability was exploited, Zerobot was updated with new exploits.
Furthermore, a number of vulnerabilities were found in Adning and Kaswara plugins. In addition, Raspberry Robin malware is targeting the telecom AND government sector. Also, identified a new Trojan dubbed as CryWiper which is targeting Russian courts and mayoral offices.
In December, Securonix Autonomous Threat Sweeper identified 2,773 IOCs, 120 distinct threats, and reported 67 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email / Email Security.
New CryWiper Trojan
(Originally published on December 2022)
On December 2 Kaspersky shared that they had discovered a new Trojan which was named CryWiper. For now it was pointing out that CryWiper only targeted Russian courts and mayoral offices, but could change in the future.
CryWiper, named for the distinctive ‘.cry’ extension which it appends onto files, appears on first impression to be a new ransomware strain. Victims’ devices seemed encrypted and a ransom note was left demanding money be sent to a bitcoin wallet address. However, the files are actually corrupted beyond recovery.
The Trojan corrupts any data that’s not crucial for the functioning of the operating system. It doesn’t impact files with extensions .exe, .dll, .lnk, .sys or .msi, and ignores several system folders in the C:Windows directory. The malware focuses on databases, archives, and user documents.
Threat Labs summary
- Leverage our findings to deploy protective measures against the new CryWiper Trojan.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 6 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the new CryWiper Trojan include but are not limited to the following:
- Monitor for Trojan sample found along the following path:
- c:\windows\system32\browserupdate.exe
- Monitor for creation of scheduled tasks.
- MITRE Tactic : Persistence
- MITRE Technique :Scheduled Task/Job: Scheduled Task
- Examples :
- schtasks /create /f /sc minute /mo 5 /ru SYSTEM /tn BrowserUpdate /tr C:\\Windows\\system32\\browserupdate.exe
- Monitor for suspicious commandline parameters executed by cmd.exe which the attacker uses to prepare the machines such as deletion of shadowcopies
Tags: Malware: CryWiper malware | Target Sector: Government Russian courts and mayoral offices
Ransomware incidents
(Originally published on December 2022)
Ransomware incidents continued this month. Microsoft revoked several hardware developer accounts after drivers signed through their profiles were used in cyberattacks, including ransomware incidents. Multiple researchers including Mandiant explain that threat actors are utilizing malicious kernel-mode hardware drivers whose trust is verified with Authenticode signatures from Microsoft’s Windows Hardware Developer Program. The criminals signed their AV-killer malware, closely related to one known as BURNTCIGAR, with a legitimate WHCP certificate.
During the investigation of this suspicious activity on a customer network, researcher Sophos X-Ops’ rapid response team found a pair of files left behind on some compromised machines. The two files are tied together to terminate processes or services used by a variety of endpoint security product vendors.
Because the rapid response team blocked the attackers from the systems to stop their malicious actions, they weren’t sure how to figure out which ransomware the attackers meant to deploy. However, methods used and files left behind offer an intriguing clue about the group behind the attack.
In their analysis Sophos X-Ops found that the pair of executable files — a cryptographically signed Windows driver (signed with a legitimate signing certificate) and an executable “loader” application meant to install the driver — were used in a failed attempt to disable endpoint security on targeted machines.
Prior research by other companies indicate that threat actors who used this tool in attacks later attempted to deploy ransomware called Cuba.
Threat Labs summary
- Leverage our findings to deploy protective measures for ransomware incidents
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 67 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Increased malware campaigns
(Originally published on December 2022)
A Raspberry Robin worm campaign has targeted Latin American, Australian, and European telecommunications and government office systems. Argentina has reported the largest number of infections, followed by Australia, Mexico, Croatia, Italy, Brazil, France, India, and Colombia.
Upon analysis, real and fake payloads were found in the main malware routine. When sandboxing tools detect the malicious code, the fake payload is loaded; however, the real payload remains hidden under packing layers and connects to Tor later.
After being installed, a custom Tor client embedded in the malware connects with the hard-coded .onion address and waits for further instructions from the real payload using shared memory once installed. In the Tor client process, the real payload uses the name of a legitimate Windows process like dllhost.exe, regsvr32.exe, and rundll32.exe.
In the another campaign, Microsoft researcher spotted an upgraded version of Zerobot (aka ZeroStresser) that was able to attack more Internet of Things (IoT) devices and exploit vulnerabilities in Apache and Apache Spark (CVE-2022-33891 respectively) as well as enhanced DDoS attack capabilities.
Insecure devices with default/weak credentials can be exploited by the Zerobot botnet through brute force attacks. In their study, researchers observed the bot trying to access the device through SSH and Telnet on ports 23 and 2323 by using eight common usernames and 130 passwords for IoT devices. Furthermore, they detected numerous attempts to connect to SSH and telnet ports 22 and 23, as well as attempts to open ports through port-knocking on 80, 8080, 8888, and 2323.
Threat Labs summary
Securonix Threat Labs was following up actively monitor running campaigns by multiple threat actors that are targeting world-wide as they began spreading rapidly once again.
- Threat Labs observed that infection with Raspberry Robin malware occurs when malicious USB drives with the included .LNK file are inserted and double-clicked.
- Threat Labs observed that a total of seven additional types of DDoS attacks are supported by the updated Zerobot variant, including UDP_RAW, TCP_XMAS, ICMP_FLOOD, TCP_SYN, TCP_ACK, TCP_SYNACK, and TCP_CUSTOM attacks.
- 48 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the a Zerobot include but are not limited to the following:
- Monitor for the presence of the following filenames in the directory – $HOME/.config/ssh.service/sshf
- – ‘sshf’
Tags: Malware: Raspberry Robin, Zerobot Botnet, Go-based | Target Sector: Telecommunication service providers, Government system
Agrius Iranian threat group on the rise
(Originally published on December 2022)
According to a WeliveSecurity advisory, Agrius, a new Iranian group targeting victims in Israel and the United Arab Emirates since 2020 initially distributes a wiper. Recently the group deployed a new wiper named Fantasy. Most of its code base comes from Apostle, Agrius’s previous wiper. In December, FortiGuard Labsteam observed a new botnet written in the Go language being distributed through IoT vulnerabilities and categorized it as critical. This botnet, known as Zerobot, contains several modules, including self-replication, attacks for different protocols, and self-propagation. It also communicates with its command-and-control server using the WebSocket protocol. The report showed how this malware leverages vulnerabilities and examines its behavior once inside an infected device.
Threat Labs summary
- Securonix Threat Labs recommends leveraging our findings to deploy protective measures against the threat group.
- Secure credentials by restricting where accounts and credentials can be used and by using local device credential protection features.
- Securonix Threat Labs recommends monitoring the tools deployed by Agrius operators to victim systems, through means unknown, which were:
- 7 IOCs are available on our Threat Labs home page repository and automatically swept against for Autonomous Threat Sweeper customers.
TTPs related to the a new wiper Fantasy include but are not limited to the following:
- Monitor for execution of process such as mimikatz.exe ,pypykatz .exe & lsass.exe which is used for credential dumping
- Monitor for fantasy45.exe and fantasy35.exe file, It collects a list of fixed drives but excludes the drive where the %WINDOWS% directory exists.
Tags: Threat Actor Location: Iran | Target: Israel HR and IT consulting firms, South Africa, Hong Kong | Wiper: Fantasy
Vulnerabilities exploited in December
(Originally published on December 2022)
Fortinet warned customers to upgrade the installs to fix an actively exploited FortiOS SSL-VPN vulnerability, tracked as CVE-2022-42475. This vulnerability has a CVSSv3.1 score of 9.3 and lets attackers obtain remote code execution on the Fortinet SSL VPN systems by sending a special masquerading request due to a heap-based buffer overflow vulnerability in the FortiOS SSL VPN service.
According to Wordfence researchers, they have observed attempts in attacks with larger spikes which could lead to exploiting an arbitrary file upload vulnerability in Kaswara Modern VC Addons v. 3.0.1. The other vulnerability was discovered was an arbitrary file upload and arbitrary file deletion vulnerability in the Adning Advertising plugin v. 1.5.5. It noticed these spikes are occurring over holidays and weekends. Researchers notified the plugin’s author of the vulnerabilities, and they worked fast to release a patched version within 24 hours.
Threat Labs summary
- Securonix Threat Labs has continued to actively monitor vulnerabilities and exploits while identifying notable vulnerabilities that could have a tremendous impact if not addressed.
- Securonix Threat Labs recommends updating vulnerable applications to the latest version immediately and following the mitigation guidelines.
- 15 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Vulnerability: Adning plugin, the Kaswara Modern VC Addons, FortiOS SSL-VPN | Exploitation: Unauthorized Access, Remote Code Execution, Privilege Escalation
Threat exploitation activities in December
(Originally published on December 2022)
Once again Iranian exploitation activities are continuing as of December 2022. PHOSPHORUS TTPs include the likely exploitation of common exploits like Log4J and ProxyShell to target unpatched vulnerable systems. The group targets energy, government, and technology companies based in Europe, the Middle East, the United States, and other countries/regions.
According to telemetry data, 107[.]173[.]231[.]114 remains active, and security vendors have reported that it is believed PHOSPHORUS activities are associated with a common command and control (C2) server (107[.]173[.]231[.]114 – ColoCrossing, US). There are also several domain names that have similar structures that are associated with this IP address based on passive DNS information.
In another, one of the new malicious attack campaigns identified by Securonix Threat Research team that is targeting victims who are likely to be government employees and the threat actor tracked as STEPPY#KAVACH.
It has been observed that .LNK files are used to execute code that leads to the downloading and execution of a malicious C# payload that functions like a remote access trojan (RAT).
By using phishing emails, attackers entice users into opening a shortcut file (.LNK) that executes a remote .HTA payload using mshta.exe Windows utility. Furthermore, there are many similarities between this STEPPY#KAVACH attack campaign and previous campaigns launched by APT36 / SideCopy / TransparentTribe, all of which originated in Pakistan.
Threat Labs summary
Securonix Threat Labs was following up actively monitor running campaigns by multiple threat actors that are targeting world-wide government sectors as they began spreading rapidly once again.
- Threat Labs observed that the majority of the PHOSPHORUS domains in the attack cluster are registered with Porkbun, and some of them are also associated with opportunistic ransomware attacks.
- Threat Labs observed that India’s Income Tax Department pertaining to the Delhi region’s official website is incometaxdelhi[.]org, which has been compromised and It is no longer possible to download the malicious file from the portal. In next phase, upon running the .HTA file, obfuscated JavaScript code is executed that displays a decoy image file containing an announcement that the Indian Ministry of Defence had sent a year earlier in December 2021.
- 34 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the a STEPPY#KAVACH include but are not limited to the following:
- Monitor for rare instances of mshta.exe spawning powershell.exe, cscript.exe, wscript.exe, msiexec.exe, rundll32.exe and msbuild.exe.
- Monitor for spike in random javascript files being created and saved to directory – \ProgramData\
- Monitor the usage of mshta.exe, making external network connections.
- Monitor for spike in traffic over the ports 3309, 3310 and 3311.
Tags: Threat Actor: PHOSPHORUS, STEPPY#KAVACH | Threat Actor Location: Iran, Pakistan
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R, Tim Johny







