- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in February 2025. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
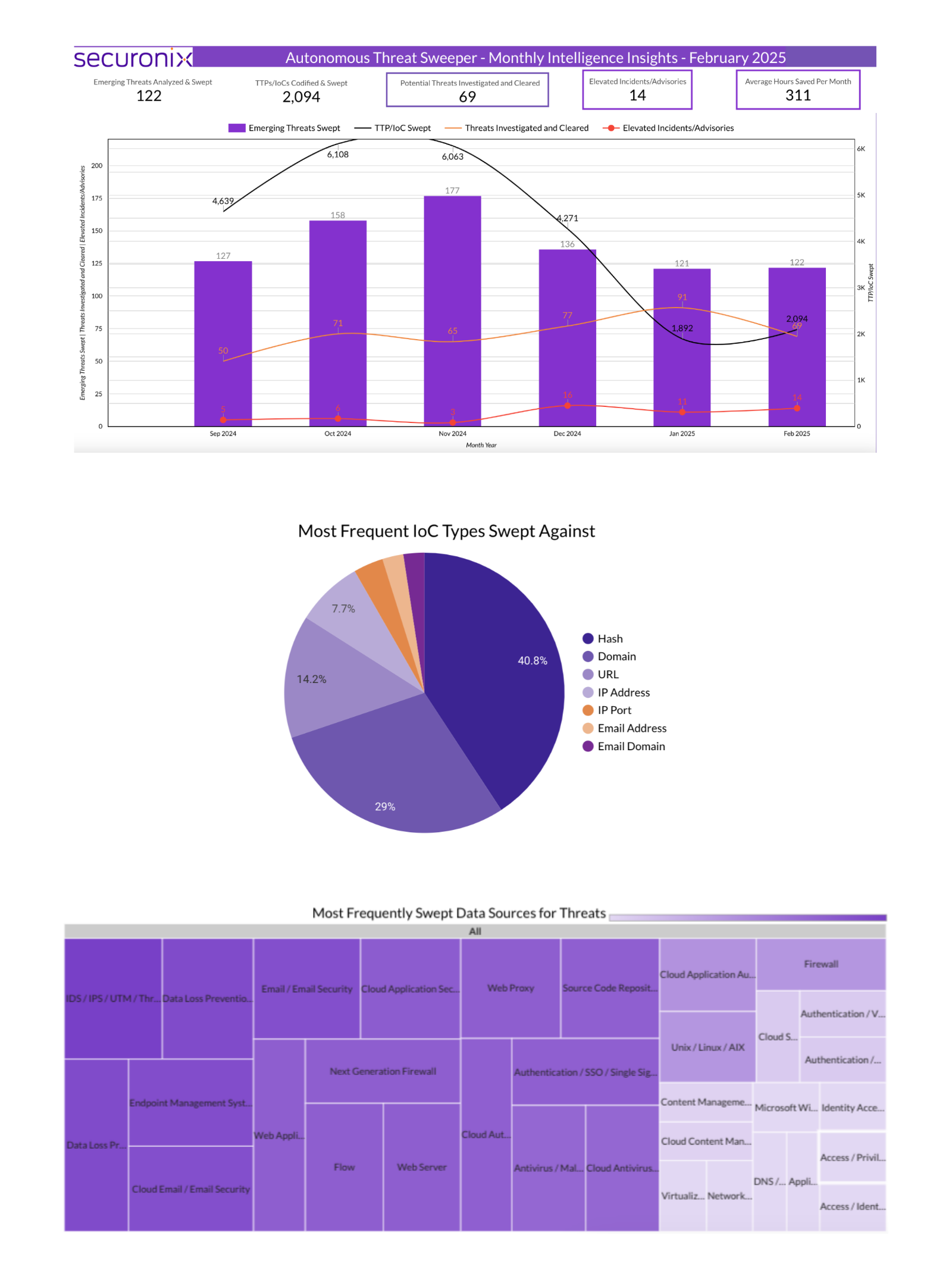
Last month Securonix Autonomous Threat Sweeper identified and analyzed 2,094 TTPs and IoCs, 122 emerging threats, investigated 69 potential threats, and elevated 14 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
Analyzing DEEP#DRIVE
(Originally published in February 2025)
The Securonix Threat Research team has identified an ongoing and highly sophisticated cyber campaign, named DEEP#DRIVE, attributed to the North Korean threat group Kimsuky. This multi-stage attack specifically targets South Korean businesses, government organizations, and cryptocurrency users through carefully crafted phishing lures written in Korean. Disguised as legitimate documents, these lures exploit trusted file formats and cloud platforms like Dropbox to evade traditional security measures.
The attackers utilize PowerShell scripts for payload delivery, reconnaissance, and executing additional malware. Key tactics include leveraging Dropbox for both payload distribution and data exfiltration, maintaining persistence through scheduled tasks, and employing code obfuscation to avoid detection. Despite the short lifespan of their infrastructure, the methods used strongly align with Kimsuky’s known tactics.
The campaign operates by tricking users into downloading compressed files containing malicious shortcut files. These shortcuts initiate the execution of PowerShell scripts, which then download further payloads, establish persistence, and erase traces of the attack. The phishing documents are carefully crafted to be relevant and appealing to the target audience, such as safety plans for logistics facilities, increasing the likelihood of successful execution. To further evade suspicion, the attackers use legitimate-looking task names and execute processes in hidden windows.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this campaign.
- To mitigate risks associated with this campaign, exercise caution when handling emails, especially unsolicited ones that emphasize urgency. Avoid downloading attachments or files from unknown sources, as phishing emails often deliver malicious payloads through direct attachments or external download links. Common file types used in these attacks include Office documents (.pptx, .docx, .xlsx), compressed files (zip, rar, iso), and PDFs.
- Be particularly wary of shortcut files (.lnk), which threat actors frequently use for code execution in phishing-based attacks.
- Monitor malware staging directories closely, paying special attention to script-related activity in world-writable directories. In this case, the attackers staged their operations in the following directory: C:\Users\<username>\AppData\Roaming
- To enhance detection and response, we strongly recommend implementing robust endpoint logging. This includes enabling process-level logging through tools like Sysmon and PowerShell logging to improve visibility and detection of malicious activity.
- 34 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the DEEP#DRIVE campaign include but are not limited to the following:
- Monitor for the .lnk file disguised as legitimate documents, including names such as 종신안내장V02_곽성환D.pdf.pdf.
- Monitor for the .lnk file created a scheduled task named ChromeUpdateTaskMachine to ensure the periodic execution of malicious scripts.
- Monitor for the scripts such as system_first.ps1 gathered detailed system information, including IP address, OS details, antivirus products and running processes, exfiltrating this data to Dropbox.
Tags: Attack Campaign: DEEP#DRIVE | Threat Actor Location: North Korea | APT Group: Kimsuky | Target: South Korean business and government sectors
Two New Threat Actors (TA2726 & TA2727) and Mac Malware
(Originally published in February 2025)
In mid-February, cybersecurity researchers discovered a new malware campaign leveraging web injects to deliver FrigidStealer, a macOS information-stealing malware. The campaign is linked to a newly identified threat actor, TA2727, which also distributes Lumma Stealer (Windows) and Marcher (Android).
TA2727 is known for using fake update lures to distribute malware and is connected to TA2726, a malicious traffic distribution system (TDS) operator that facilitates malware distribution. TA2726 works with other financially motivated actors, including TA569, which spreads the SocGholish (FakeUpdates) malware via compromised websites.
TA2727 and TA569 both rely on malicious JavaScript injects to trick users into downloading malware disguised as browser updates. However, TA2727 tailors its attacks based on geography and device type. For instance, Windows users in France and the U.K. may receive Hijack Loader, which deploys Lumma Stealer, while Android users are targeted with the Marcher banking trojan.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this campaign.
- Educate employees on fake update scams and the risks of downloading files from untrusted sources. Encourage users to report suspicious activity to security teams.
- Configure Group Policy settings to prevent users from downloading and executing JavaScript, MSI, and DMG files from untrusted sources.
- Use browser isolation solutions to prevent compromised websites from executing malicious scripts, reducing the risk of malware infection via web injects.
- Set up firewalls and secure web gateways to restrict access to known malicious domains. Implement DNS filtering solutions to block users from accessing compromised websites.
- 10 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat Actor: TA2726 and TA2727 | Malware: FrigidStealer
Cyber Espionage Campaigns
(Originally published in February 2025)
The REF7707 and BadPilot campaigns highlight the evolving threat landscape targeting government entities and critical infrastructure. REF7707 employs malware and cloud-based C2 for stealthy lateral movement, while BadPilot, linked to Russia’s GRU, leverages RMM tools to infiltrate global sectors, emphasizing the rising sophistication of state-sponsored cyber operations.
REF7707 is a newly discovered cyber campaign targeting government entities, with a particular focus on a foreign ministry in South America. This operation utilizes multiple malware families, including FinalDraft, GuidLoader, and PathLoader, to establish persistence and deploy malicious payloads. The attackers facilitate lateral movement within compromised networks by exploiting spoofed credentials and leveraging the Windows remote management tool. Additionally, they use cloud services such as the Microsoft Graph API for command-and-control (C2) communication, blending malicious traffic with legitimate network activity to evade detection.
The BadPilot campaign is a newly uncovered, highly sophisticated cyber operation active since 2021 and attributed to a subgroup of the Russian state-sponsored threat actor Seashell Blizzard, also known as Sandworm. Operating under Russia’s Military Intelligence Unit 74455 (GRU), this campaign signifies a surge in Russian cyber activities targeting critical infrastructure on a global scale. BadPilot primarily compromises internet-facing systems to establish long-term persistence and conduct targeted network operations. Its targets span multiple sectors, including energy, oil and gas, telecommunications, shipping, arms manufacturing, and government entities. The group utilizes Remote Monitoring and Management (RMM) tools such as Atera Agent and Splashtop Remote Services for command-and-control (C2) operations. BadPilot has extended its operations across North America, Europe, Central Asia, and the Middle East.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these campaigns.
- Block the execution of certutil.exe, WinrsHost.exe, diskshadow.exe, and CDB.exe using Windows AppLocker or Software Restriction Policies (SRP) to prevent the misuse of Living Off the Land Binaries (LOLBins).
- Prevent credential theft by monitoring unauthorized access to SAM, SYSTEM, SECURITY registry hives, and the Active Directory database (ntds.dit), enabling LSASS memory protection to block credential dumping, and implementing Privileged Access Management (PAM) to restrict access to administrative credentials.
- Enforce multifactor authentication (MFA) as a critical layer of identity security, while mitigating advanced threats like AiTM phishing by leveraging phishing-resistant methods such as FIDO tokens or Microsoft Authenticator with passkey, and avoiding telephony-based MFA to prevent SIM-jacking risks.
- Enable Network Level Authentication for Remote Desktop Service connections.
- 40 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the REF7707 include but are not limited to the following:
- Monitor for the file name: SoftwareDistribution.txt (The adversary executed an unknown script).
- Monitor for file name: FontDrvHost.exe (The attacker downloaded fontdrvhost.exe, fontdrvhost.rar, config.ini, and wmsetup.log to the C:\ProgramData\ directory; from there, the attacker moved to several other Windows endpoints.)
- Monitor and restrict the execution of LOLBins (Living Off the Land Binaries) such as certutil.exe for downloading remote files, WinrsHost.exe spawning unusual child processes, diskshadow.exe performing shadow copy operations linked to credential dumping, and CDB.exe initiating network connections or executing suspicious command-line arguments.
- Monitor and prevent credential theft by monitoring the use of diskshadow.exe for creating shadow copies (T1003.003 – NTDS.dit extraction), unauthorized access to SAM, SYSTEM, and SECURITY registry hives (Windows Event ID 4656), LSASS process memory dumping (e.g., `procdump.exe -ma lsass.exe`), and Mimikatz-like behavior or custom tools used for credential extraction.
TTPs related to the BadPilot include but are not limited to the following:
- Monitor for RMM tools like Atera Agent and Splashtop Remote Services, as attackers leverage them for persistence and C2 communication.
- Monitor for rclone.exe for potential data exfiltration and reg.exe for credential access.
- Monitor regularly Ivanti devices for vulnerabilities (CVE-2024-1709 & CVE-2023-48788) to prevent the deployment of malicious RMM tools.
Tags: Campaign: REF7707, BadPilot | Payloads: FinalDraft, GuidLoader, PathLoader | Target Sector: Energy, oil and gas, telecommunications, shipping, government entities | Target Countries: South America, North America, Europe, Central Asia and Middle East.
APT’s Activity (Winnti & Kimsuky)
(Originally published in February 2025)
In February 2025, Winnti Group targeted Japanese industries via the RevivalStone campaign, exploiting SQL injection vulnerabilities. Kimsuky used spear-phishing with LNK files to deploy PebbleDash backdoor and an RDP Wrapper. Both groups focused on data theft and persistence, posing significant threats to critical sectors.
Winnti Group – The China-based APT group known as Winnti, also referred to as APT41, has launched a cyber campaign called RevivalStone, first identified in 2024. This campaign specifically targets Japanese organizations in key sectors, including manufacturing, materials, and energy. RevivalStone employs an upgraded version of the Winnti malware, featuring enhanced capabilities. The attack begins with SQL injection exploits in web-facing ERP systems, allowing the deployment of web shells such as China Chopper, Behinder, and sqlmap file uploader to gain initial access. These web shells enable reconnaissance, credential harvesting, and lateral movement within the compromised networks. Winnti is known for targeting intellectual property and sensitive data across various industries, including gaming, pharmaceuticals, aerospace, and, more recently, Japan’s critical infrastructure.
Kimsuky Group – A North Korean state-sponsored threat actor active since 2013, has been targeting organizations across the United States, Japan, Russia, Vietnam, and multiple European nations. Recently, the group has intensified its use of spear-phishing tactics, delivering malware through LNK files disguised as legitimate documents. When executed, these files trigger PowerShell or Mshta commands, which download and install the PebbleDash backdoor along with a custom-built RDP Wrapper, enabling remote system control. Kimsuky also employs proxy malware to facilitate communication between infected systems and external networks. These proxies allow the group to bypass network restrictions and maintain persistence within compromised environments.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat activities.
- Regularly updating ERP software, web applications, and databases, implementing strict input validation with parameterized queries, and restricting database user permissions are essential measures to prevent SQL injection attacks and minimize potential damage.
- Regularly scanning for unauthorized file modifications, disabling unnecessary scripting features on public-facing servers, and restricting access to web administration panels with multi-factor authentication (MFA) are crucial steps to prevent web shell deployments and unauthorized access.
- Deploying advanced email security solutions to detect malicious LNK, PowerShell, and Mshta-based payloads, utilizing sandboxing to analyze attachments before delivery, and blocking LNK files from untrusted sources are crucial measures to prevent spear-phishing attacks.
- Configuring Group Policy to block LNK execution from email attachments and restricting Mshta.exe and PowerShell execution for untrusted scripts are essential steps to prevent malware deployment and execution.
- 12 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Winnti group include but are not limited to the following:
- Monitor for a modified DLL file: TSMSISrv.dll (DLL hijacking).
- Monitor for execution of file mresgui.dll, which is the Winnti Loader.
- Monitor for the DAT file which loads Winnti RAT.
- Monitor for the Winnti Rootkit Installer: amonitor.sys (“%SystemRoot%\System32\drivers\”).
- Monitor for the obfuscation using XOR or ChaCha20.
TTPs related to the Kimsuky group include but are not limited to the following:
- Monitor for the shortcut files with document-like icons (.LNK) initiating malicious commands using PowerShell or Mshta.
- Monitor for a self-developed RDP Wrapper which is used to enable remote access on non-RDP-supported systems.
- Monitor for the creation of mutexes like “MYLPROJECT” or “LPROXYMUTEX.” [“C:\Programdata\USOShared2\version.ini”] (Proxy Tools).
- Monitor for keyloggers store keystroke data in files: joeLog.txt and jLog.txt (“C:\Programdata\joeLog.txt” and “C:\Programdata\jLog.txt”).
- Monitor for file: wbemback.dat which is loading into memory for stealthy execution (“%SystemDirectory%\wbemback.dat”).
- Monitor for file: “Invoke-ReflectivePEInjection.ps1” for stealthy PowerShell-based payload execution (“%ALLUSERSPROFILE%\USOShared\Prosd\”).
Tags: APT Group: Winnti, Kimsuky| Target Sector: Gaming, Pharmaceuticals, Aerospace, and Critical Infrastructure | Target Regions: The United States, Japan, Russia, Vietnam, and European nations. | Malware: Pebble Bash, RDP Wrapper
Ransomware Trends & Threat Analysis
(Originally published in February 2025)
In February 2025, cybersecurity threats intensified with multiple ransomware campaigns. Ghost (Cring) ransomware continued targeting critical industries using exploits like CVE-2018-13379 to gain access, disable security tools, and encrypt files. LockBit ransomware attackers exploited CVE-2023-22527 in Atlassian Confluence to infiltrate systems, exfiltrate data, and deploy ransomware within hours. Abyss Locker remained active, breaching networks via unpatched VPN appliances and harvesting credentials from backup systems. These attacks highlight the ongoing risk posed by ransomware groups leveraging known vulnerabilities, credential theft, and lateral movement techniques to compromise organizations across sectors.
| Ghost (Cring) Ransomware | A joint advisory was released in February 2025 by CISA, the FBI, and MS-ISAC regarding Ghost (Cring) ransomware, a financially motivated threat active since 2021. This ransomware group targets industries with high operational dependencies, such as healthcare, financial services, government agencies, critical infrastructure, manufacturing, education, professional services, and retail. Key targets include hospitals, financial institutions, industrial control systems, educational institutions, legal firms, and e-commerce platforms, all of which hold valuable data and face significant operational consequences from attacks. The group uses advanced evasion techniques and exploits vulnerable internet-facing systems, outdated software, and weak security configurations to encrypt critical data and demand ransoms.
Ghost (Cring) ransomware uses a multi-stage attack methodology, beginning with exploiting known vulnerabilities, such as CVE-2018-13379 in Fortinet’s FortiOS, to gain initial access. Attackers then use stolen credentials for lateral movement before deploying the ransomware via remote execution tools like PsExec and WMI. Once inside, Ghost (Cring) escalates privileges, disables security tools, and terminates critical processes to evade detection. It then encrypts files using AES-256 and RSA-2048, appending unique extensions and demanding ransom payments in cryptocurrency. To ensure persistence, the ransomware creates scheduled tasks, modifies system registries, and may use fileless techniques, making detection and removal challenging. |
| Confluence Exploit Triggers LockBit Ransomware | In February 2025, hackers exploited a critical vulnerability (CVE-2023-22527) in an Atlassian Confluence server to deploy LockBit ransomware. The attackers gained access by remotely executing malicious OGNL expressions through the flaw. Once inside, they performed system reconnaissance, attempted to install AnyDesk, and established persistent access using Metasploit.
The attackers moved laterally via RDP, extracted credentials with Mimikatz, and exfiltrated data to MEGA.io using Rclone. They then deployed LockBit ransomware using PDQ Deploy and manual execution to ensure widespread encryption. The attack lasted just over two hours and ended with ransom notes and modified desktop backgrounds on compromised systems. |
| Abyss Locker Ransomware | Abyss Locker, a ransomware group known for its swift and targeted attacks on critical network infrastructure, has been active since 2023. Despite numerous incidents involving Abyss Locker in 2024, researchers found limited publicly available technical documentation on the group’s operations.
Typically, Abyss Locker’s attack flow starts by exploiting vulnerabilities in unpatched VPN appliances, such as SonicWall VPNs with known vulnerabilities like CVE-2021-20038, to gain initial access to internal networks. The attackers then deploy tunneling tools to maintain their foothold within the compromised network. Credential harvesting is a primary objective once Abyss Locker has infiltrated a network. The group frequently targets backup appliances, especially those that use high-privileged service accounts. For example, Abyss Locker has been known to leverage modified versions of the open-source PowerShell script ‘Veeam-Get-Creds.ps1’ to extract credentials from Veeam backup systems. In addition to deploying obfuscated versions of the script, the group has used other techniques, such as dumping the Windows SAM and Security registry hives, to steal credential material. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware campaigns.
- Ensure regular system backups are stored offline or segmented from source systems to enable recovery without ransom payment.
- Apply security updates to operating systems, software, and firmware within a risk-informed timeframe to mitigate exploit risks.
- Restrict lateral movement by micro-segmenting critical infrastructure, using VLANs, and enforcing inter-VLAN communication through stateful firewalls.
- Require phishing-resistant MFA for privileged and email accounts, enforce PAM solutions, and limit administrative privileges to protect credentials.
- 86 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Abyss Locker Ransomware include but are not limited to the following:
- Threat actors target backup and high-privilege accounts by executing PowerShell scripts like veeam11.ps1 or Veeam-Get-Creds.ps1 with suspicious command-line arguments, along with unauthorized registry or file access to credential stores such as SAM, SECURITY, or NTDS.dit.
- Adversaries prepare for lateral movement by enumerating Active Directory objects using PowerShell commands like Get-ADUser and Get-ADComputer, leveraging built-in Windows tools such as net use, wmic, and schtasks to map shared resources, and initiating unexpected logins on critical systems, especially with administrative accounts.
- Threat actors attempt defense evasion by modifying the registry to disable Windows Defender (DisableAntiSpyware=1) and executing known security evasion tools such as powerrun, SophosAV.exe, and auSophos.exe to bypass security controls.
- Adversaries employ BYOVD (Bring Your Own Vulnerable Driver) techniques by loading unsigned drivers like UpdateDrv.sys (Zemana Anti-Logger) and performing unauthorized kernel modifications or driver installations outside of expected update cycles to evade security defenses.
- Threat actors establish Command & Control (C2) by deploying tools like Chisel, WinSW-x64.exe, or OpenSSH for persistent SSH tunnels, configuring hidden services such as WMI Helper Agent or renamed apache2, and initiating connections to external IPs over uncommon ports (e.g., 443, 48000). Indicators of anomalous network activity may include large volumes of encrypted traffic to cloud services like AWS or BackBlaze, reverse SSH tunnels (ssh -R 127.0.0.1:48000 to external hosts), and unauthorized access attempts to NAS storage or backup servers.
- Adversaries stage data for exfiltration and deploy ransomware by renaming Rclone as ltsvc.exe to evade detection, transferring large files outside normal business hours, and performing unusual batch modifications of file extensions (e.g., .Abyss, .crypt). Additionally, they tamper with system recovery by deleting volume shadow copies (vssadmin delete shadows /all), modifying backup retention policies, and clearing event logs to erase forensic traces.
TTPs related to the Confluence Exploit Triggers LockBit Ransomware include but are not limited to the following:
- Monitor for attempts to download remote administration tools like AnyDesk via curl and mshta.
- Monitor for execution of malicious PowerShell scripts to inject shellcode into memory (VirtualAlloc, VirtualProtect).
- Monitor for the creation of a new local administrator account (backup) and adding it to the Administrators group (Windows Security Events 4720, 4732).
- Monitor for execution of Mimikatz (Sysmon Event ID 1, 10, 11), dumping LSASS memory for credentials.
- Monitor for use of Veeam-Get-Creds-New.ps1 script to extract stored backup credentials.
- Monitor for clearing Windows Event Logs (wevtutil cl) and deletion of attacker artifacts (Rclone config, batch scripts).
- Monitor for RDP logins from the beachhead server (Event ID 4624 showing multiple interactive logins).
- Monitor for use of Rclone to transfer files to Mega.io (Suricata alerts on HTTP POST requests) and data staged in C:\temp and quickly deleted after verification.
- Monitor for deployment of LockBit ransomware using PDQ Deploy, as evidenced by PDQDeployRunner- execution logs, or manually execute it on critical servers such as Exchange, File Share, and Backup systems. They may leverage batch files (asd.bat, test.bat) to trigger ransomware encryption, stop essential services like Exchange and SQL (net stop MSExchangeUM, *taskkill /f /im sql), and encrypt files with a .rhddiicoE extension while dropping a ransom note.
Tags: Ransomware Group: LockBit, Abyss Locker, Ghost (Cring) | Vulnerability Expoilited: Atlassian Confluence server (CVE-2023-22527), Fortinet FortiOS appliances (CVE-2018-13379), Servers running Adobe ColdFusion (CVE-2010-2861 and CVE-2009-3960), Microsoft SharePoint (CVE-2019-0604), and Microsoft Exchange (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207)
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh, and Nikhil Kumar Chadha