- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
Authors: Dheeraj Kumar, and Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in January. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
In January 2024, Threat Labs analyzed and monitored the following major threat categories: Increasing macOS cyber threats, exploitation of Ivanti Connect Secure VPN, active malicious campaigns, and the analysis and review of the ransomware attack on Boeing.
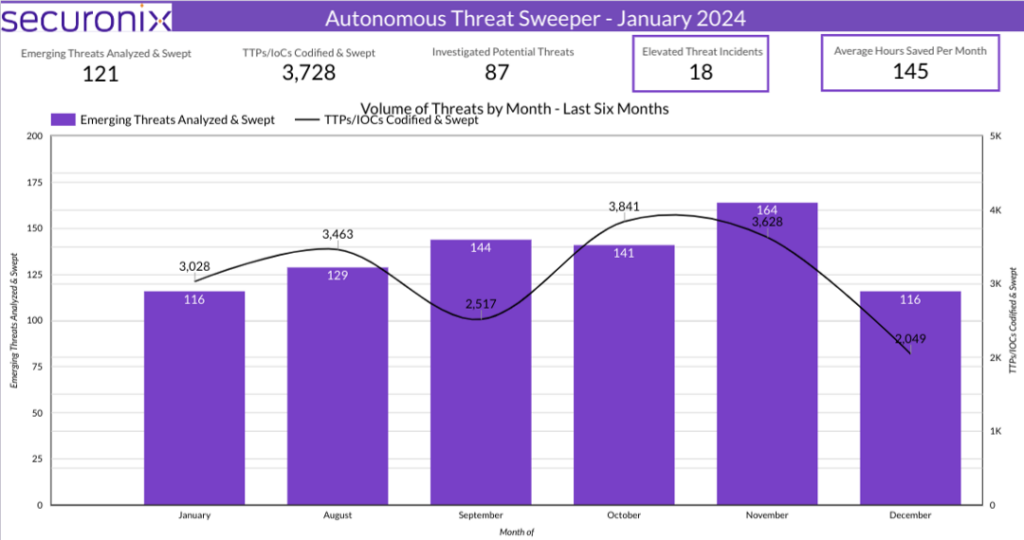
Last month Securonix Autonomous Threat Sweeper identified and analyzed 3,728 TTPs and IoCs, 121 emerging threats, investigated 87 potential threats, and elevated 18 threat incidents. The top data sources swept against include Cloud Application Audit, Cloud Content Management, Cloud Antivirus/Malware/EDR, Data Loss Prevention, and Email/Email Security.
macOS cyber threats on the rise (Originally published in January 2024)
Macs, computers running macOS, have several benefits despite their high cost, particularly in terms of security and usability. Apple continuously employs a variety of cutting-edge security techniques to protect its users. Despite its many security measures, macOS is not impervious to modern cyberattacks like other operating systems.
An increasing tendency of macOS malware to become “wild” or be actively used in bilateral attacks has been observed by our ATS team this month.
The macOS “wild” activity started at the beginning of the new year. A Clever Blog Name researcher Greg Lesnewich has observed an Apple macOS backdoor SpectralBlur tracked as TA444 family that is similar to a known malware family tied to North Korean threat actors. SpectralBlur backdoor can upload/download files, run a shell, update its configuration, delete files, hibernate, or sleep, based on commands issued from the C2 server. The malware is very similar to KANDYKORN (or SockRacket), a progressive implant that operates as a remote access trojan by taking control of a compromised host.
There has been a rise in the reporting of infostealers that target macOS since last year and has not slowed down. Variants of Atomic Stealer, macOS MetaStealer, RealStealer, and others were seen throughout last year.
InMarch 2023 Atomic Stealer the inaugural MacOS-targeting stealer offered a sophisticated panel for $3000 a month. Boasting advanced features such as keychain extraction, password retrieval, and browser data theft, it recently evolved with encrypted strings and anti-VM checks. The threat minimizes traces on infected devices, presenting a formidable challenge to cybersecurity.
The next target was an attack on macOS wallet applications Exodus3 and Bitcoin Core. Xavier Mertens, an ISC SANS researcher found a malicious Python script searching for occurrences of these applications. Jamf Threat Labs researchers also observed activity in pirated macOS applications. These apps were similar to ZuRu malware, downloading and executing multiple payloads to compromise machines in the background. It detected a series of pirated macOS applications that were modified to communicate to the attacker infrastructure and were hosted on Chinese pirating websites to gain victims.
And the final threat seen was related to cryptowallets that didn’t escape another macOS backdoor threat. Researchers at Securelist have discovered a new type of macOS malware that was previously unidentified and was using software that had been cracked. With the backdoor, the threat proved much more serious than installing a proxy server without authorization.
TTPs related to the macOS cyber threats include but are not limited to the following:
- Monitor for suspicious file names
- Monitor for MacOS file system structure and locations used by Atomic Stealer
- Monitor for KeySteal uses the name ‘ChatGPT’ for its executable
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from this campaign.
- TA444 continues to run rapidly and ferociously with these new types of MacOS malware. By searching for comparable phrases, we were able to connect KandyKorn to SpectralBlur (which, once more samples were found, we further related to TA444). Eventually, a phishing effort affected our visibility and caused KandyKorn to be taken down.
- The persisting difficulties faced by macOS corporate users are highlighted by the presence and adaptability of macOS infostealers such as KeySteal, Atomic InfoStealer, and CherryPie. Apple has been working hard to update its XProtect signature database, but these fast changing malware strains are still managing to get away.
- In addition to encrypted strings, the updated version seems to carry out extra enumeration on the compromised system, and as far as I could observe, the ZIP archive is no longer written to the disk. Without a doubt, the goal of the most recent version of AMOS is to leave as little evidence as possible on the compromised computers. For whatever reason, one of the wallet addresses in the updated version is misspelled, and it should read acmacodkjbdgmoleeebolmdjonilkdbch instead of acmacodkjbdgmoleebolmdjonilkdbch.
- 107 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Target: macOS cyber threats | Attack Type: backdoor, infostealer, and malware
Ivanti Connect Secure VPN exploited (Originally published in January 2024)
In mid-December 2023 Volexity experts discovered unusual activity within a client’s network by. Their investigation revealed the use of web shells on a number of internal and external web servers, which were linked to the company’s Ivanti Connect Secure (ICS) VPN appliance.
Investigators found that the unusual activity began on December 3 and that the Ivanti Connect Secure VPN appliance had both disabled and erased its data.
The deployment of an exploit chain using zero-day vulnerabilities reported as CVE-2023-46805 and CVE-2024-21887 was validated by further research. By taking advantage of these flaws, the attacker was able to execute code remotely and get around authentication.
With a high CVSS score of 8.2, CVE-2023-46805 was able to bypass authentication in the online component of Ivanti Policy Secure, 9.x, and 22.x versions of Ivanti Connect Secure. Bypassing control checks allows remote attackers to get access to resources that are forbidden.
CVE-2024-21887 (Critical, 9.1 CVSS Score command injection vulnerability exists in the web components of Ivanti Policy Secure and Ivanti Connect Secure (9.x, 22.x). It permits an authenticated administrator to use crafted requests to execute arbitrary commands.
A third party published a proof of concept (PoC) on January 16, 2024, which led to an increase in the scope of exploitation. In addition to the existing threat, Ivanti disclosed two additional vulnerabilities on January 31: CVE-2024-21888, which is a privilege escalation flaw, and CVE-2024-21893, which is an SSRF web vulnerability. These vulnerabilities increase the need for action and increased security awareness while the manufacturer continues to work on developing and delivering suitable mitigations.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this vulnerability.
- Ivanti released an update to the advisory for vulnerabilities CVE-2023-46805 and CVE-2024-21887 on January 20, 2024, highlighting a significant warning on a race condition that was found during the transfer of device configurations. Due to this race condition, clients are left defenseless and XML remediation is seriously threatened.
- The warning update states that forcing new device configurations that include XML causes disruptions to critical web services makes the mitigation useless. Customers that use Pulse One or nSA for configuration pushes, in full or in part, are affected as well. Customers using XML-enabled appliances are strongly encouraged by Ivanti to cease pushing configurations until the appliance has received a patch.
- Additionally, according to the business, threat actors were seen attempting to take advantage of Ivanti’s Internal Integrity Checker (ICT). All clients are urged to use the external ICT as a precaution, as it now has improved capabilities that will eventually be incorporated into the internal ICT.
- Furthermore, Ivanti advises customers to run both internal and external ICT simultaneously with continuous monitoring because, while it reminds users to use the most recent versions of both, it claims that ICT only captures a snapshot of the appliance’s current state and may not be able to detect threat actor activity if the appliance is cleaned up.
- 35 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Ivanti Connect Secure VPN exploited include but are not limited to the following:
- Monitor for web users executing abnormal wget commands from linux shell to download additional tooling and communicate to C2 servers:
- sh -c “wget -t 1 –server-response
Tags: Target: Ivanti Connect Secure VPN | Vulnerabilities: CVE-2023-46805, CVE-2024-21887 | Attack Type: Zero-Day
Malware campaigns (Originally published in January 2024)
The CISA issued warnings that threat actors using the AndroxGh0st malware are building a botnet for victim identification and exploitation in target networks. First discovered by Lacework in December 2022, AndroxGh0st is a Python-based malware that served as the model for a number of programs that are similar to it, including AlienFox, GreenBot (also known as Maintenance), Legion, and Predator.
The cloud attack tool may access Laravel environment files and take credentials for well-known apps like SendGrid, Microsoft Office 365, Amazon Web Services (AWS), and Twilio by infecting servers that are known to have security issues.
A sophisticated Microsoft Office-based attack targeting well-known corporate executives in the lead up to a nation’s general elections has been discovered by Forcepoint X-Labs. An ostensibly innocuous email about casting a ballot in the next general election initiates the attack. The email continues, enumerating a few things that voters ought to abstain from doing on election day.
It’s interesting to note that the email never specifically invites the recipient to open any attachments, although the Voting Instructions.docx document is one.
Investigations have shown that well-known corporate executives have received several copies of the same material. Although the attackers’ motivations are unknown now, it’s possible that they want to keep tabs on voter sentiment.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these malicious campaigns.
- SMTP abuse may be facilitated by AndroxGh0st through many capabilities such as web shell deployment, credential and API exploitation, and scanning.
- The virus particularly looks for and parses AWS keys, but it may also produce keys for brute-force attacks.
- The connection type is now shown as an image, and UpdateMode is set to Always instead of “OnCall,” which is a significant change between this and the Follina exploits of 2023. By default, the script runs automatically when a document is opened.
- As with the Microsoft diagnostic tool exploit observed in the Follina attack chain, we think there is a second stage dropper that takes advantage of a fresh Windows vulnerability.
- 33 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the malware campaigns include but are not limited to the following:
- Monitor for rare filenames with extension – .HLJkNskOq
Tags: Malware: Androxgh0st | Target: .env files, Microsoft Office | Attack Type: Phishing
LockBit’s attack on Boeing (Originally published in January 2024)
Boeing, a major player in the aerospace industry, is looking into a hack that may have affected its parts and distribution business. The LockBit ransomware group claimed to have gained access to the company’s network and taken data.
As part of an ongoing investigation, Boeing has established cooperation with law enforcement and regulatory authorities and stated that the event did not affect flight safety.
The RaaS+ targeted ransomware attack that struck Boeing in late October 2023 was successful. The victim information release platform, to which LockBit belongs, claimed in a message dated October 27, 2023, to have taken a significant quantity of Boeing’s confidential information and used it as leverage over the company. The group threatened the breach would become public knowledge if it didn’t get in touch with LockBit before November 2, 2023. Following that, Boeing was removed from the victim list for a while until November 7, when LockBit added Boeing back to the victim list and released 4 gigabytes of data because Boeing had disregarded its warnings. The LockBit organization made public 21.6 GB data that had been taken from Boeing on November 10, possibly as a result of the two parties’ inability to reach an agreement. Media sources had stated that the amount had been twice counted, combining enlarged and compressed data.
Threat Labs summary
The following main events and techniques during the attack on Boeing are summarized below.
- Boeing was hit by the LockBit ransomware, which released over 43GB of files when the corporation declined to pay a ransom.
- The majority of the information on the hacking group’s leak website is from backups of several systems, the most recent of which has a timestamp of October 22.
- On October 27, the ransomware perpetrator listed Boeing on their website and gave the business until November 2 to get in touch and start talks.
- At the time, the hackers claimed to have taken “a tremendous amount of sensitive data” and were prepared to release it.
- 19 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the attack on Boeing include but are not limited to the following:
- Monitor execution of “Maui.exe” which leads to malicious files creation on execution
- Check for filenames maui.exe, maui.log, maui.key, maui.evd, aui.exe
Tags: Ransomware: LockBit | Target Company: Boeing
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R