- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Nitish Singh, and Nikhil Kumar Chadha
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in November 2024. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
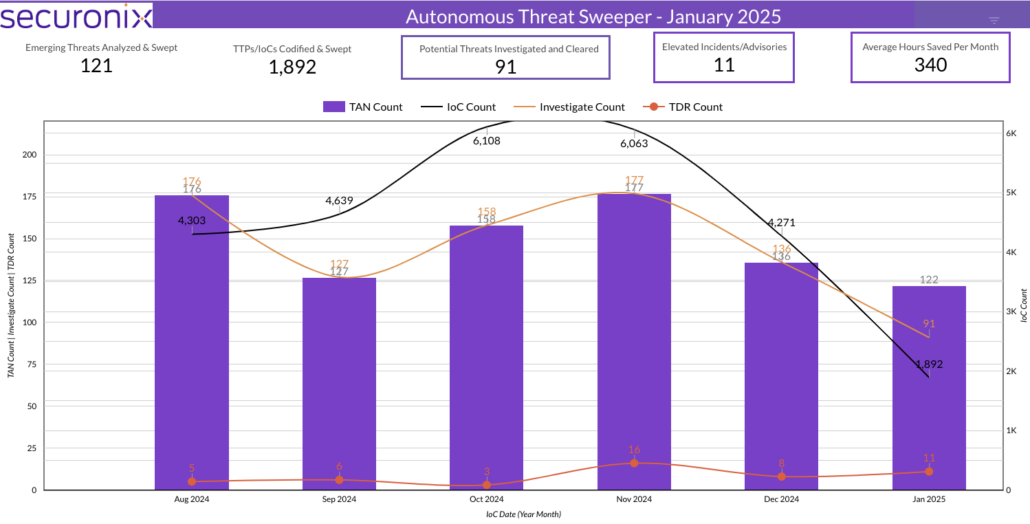
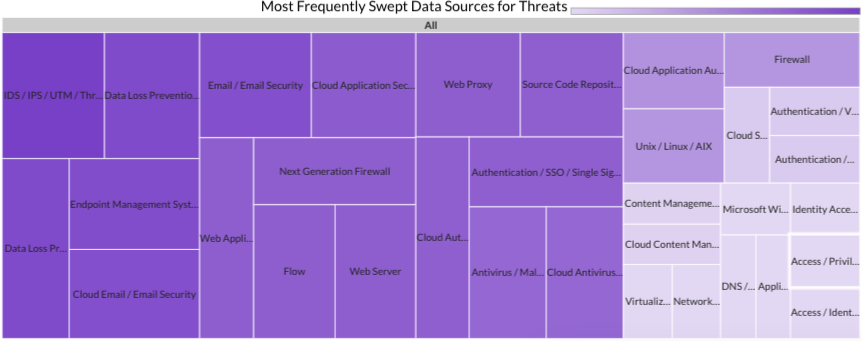
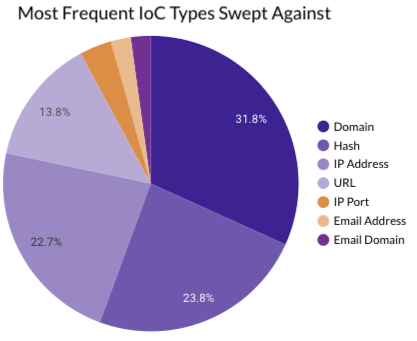
Last month Securonix Autonomous Threat Sweeper identified and analyzed 1,892 TTPs and IoCs, 121 emerging threats, investigated 91 potential threats, and elevated 11 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
Cyberhaven Browser Extension Compromise
(Originally published in January 2025)
In December 2024, Cyberhaven, a data loss prevention (DLP) cybersecurity company, suffered a significant security breach following a phishing attack that compromised an administrative account for the Chrome Web Store. This led to the publication of a malicious browser extension under Cyberhaven’s name, which was available for several hours before being detected and removed. The extension targeted web-based accounts like Facebook Business, stealing sensitive data such as session cookies and logging user inputs via DOM-tree manipulation.
A malicious browser extension, active from December 25 to December 26, 2024, exfiltrated data to a command-and-control domain (cyberhavenext[.]pro). The extension was detected and removed by Cyberhaven’s security team within 60 minutes, but sensitive data may have been compromised during the breach. No other systems or accounts were affected. Organizations using Cyberhaven’s DLP solution should update to version 24.10.5+ to prevent further exploitation. This incident highlights the vulnerabilities of browser extensions, even those from trusted sources, and stresses the need for improved extension management, continuous monitoring, enhanced phishing prevention, and quick responses to security threats.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this campaign.
- Promptly remove the compromised extension from all affected systems and update to a safe, verified version (e.g., 24.10.5+) to prevent further exploitation. Ensure the update is deployed across all affected endpoints and user devices to close the security gap.
- Implement continuous monitoring for abnormal behavior in browser extensions, such as unusual network traffic to unknown domains, unauthorized access to session cookies, or DOM manipulation. Set up alerts to detect these signs early and enable a swift response to prevent data exfiltration.
- Strengthen phishing prevention efforts by training employees to recognize suspicious communications and implement multi-factor authentication (MFA) on all critical accounts, particularly those with administrative access to app stores and extension management tools.
- Reassess extension management protocols to ensure strict controls are in place for extension installation, updates, and access permissions. Enforce the use of a trusted extension allowlist and conduct regular audits to detect unauthorized changes or new, potentially malicious extensions.
- 112 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Cyberhaven Browser Extension Compromise include but are not limited to the following:
- Monitor for OAuth requests originating from unfamiliar domains, such as supportchromestore[.]com, forextensions[.]com, or checkpolicy[.]site, and investigate any unexpected OAuth authorizations or unusual permission requests granted to extensions.
- Monitor for the addition of new or unrecognized content scripts in the extension, particularly those with the <all_urls> permission in the manifest, and ensure they do not access sensitive data such as cookies, session storage, authentication tokens, or configuration files like cyberhavenext_ext_manage stored in local storage.
- Monitor for outbound network connections to suspicious or unknown domains/IPs, especially those linked to attacker-controlled infrastructure (e.g., cyberhavenext[.]pro, 136[.]244[.]115[.]219).
- Monitor for scripts that execute commands like chrome.storage.local.get() to retrieve sensitive stored data.
Tags: Atta Type: Phishing, Target: Chrome Web Store
The exploitation of CVE-2025-0282 and CVE-2025-0283
(Originally published in January 2025)
This month’s report highlights the discovery of two critical vulnerabilities (CVE-2025-0282 and CVE-2025-0283) in Ivanti’s Connect Secure, Policy Secure, and ZTA gateway solutions. These flaws enable remote code execution and privilege escalation, mostly targeting outward-facing assets required for secure remote connections.
CISA and the FBI also published a combined advisory on exploits that target Ivanti CSA vulnerabilities (CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380). Threat actors utilized chained attacks to bypass administrative controls, execute remote code, and steal credentials. These vulnerabilities were exploited in chained attacks targeting Ivanti CSA versions 4.6 (end-of-life) and certain 5.0.x versions.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these vulnerabilities.
- To ensure continued support, it is essential to upgrade to the latest supported version of Ivanti CSA. Please be aware that Ivanti CSA 4.6 has reached its end of life (EOL) and will no longer receive patches or updates for third-party libraries. Upgrade now to maintain full support.
- Implementing application controls to regulate software execution, including the allowlisting of remote access programs, is crucial. These controls should prevent the installation and execution of unauthorized portable versions of remote access and other software. A well-configured application allowlisting solution will block the execution of any application not explicitly listed. Allowlisting is especially important, as antivirus solutions may not detect malicious portable executables that use compression, encryption, or obfuscation techniques.
- It is important to strictly limit the use of Remote Desktop Protocol (RDP) and other remote desktop services. When RDP is necessary, ensure strict adherence to best practices, such as those outlined in [CPG 2.W]. These include:
- Auditing the network for systems utilizing RDP.
- Closing any unused RDP ports.
- Enforcing account lockouts after a set number of failed login attempts.
- Implementing phishing-resistant multifactor authentication (MFA).
- Logging all RDP login attempts for monitoring and analysis.
- Configure the Windows Registry to prompt for User Account Control (UAC) approval for any PsExec operations that require administrator privileges. This helps mitigate the risk of lateral movement through PsExec by adding an additional layer of security.
- 14 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Ivanti Vulnerability Exploit Campaign include but are not limited to the following:
- Monitor for repeated IFT connection errors by checking Ivanti appliances debug logs for statements like Invalid IFT packet received from unauthenticated client, which indicates future exploitation attempts.
- Monitor for process injection activity by looking for instances of processes like svchost.exe being launched in a suspended state, which indicates process hollowing attempts.
- Monitor for DLL sideloading by identifying suspicious DLL files, such as vixDiskLib.dll and deelevator64.dll, that are loaded by legal executables such as DeElevate64.exe and vmdisk.exe.
- Monitor for lateral movement activities by tracing RDP connections from Ivanti appliances to other systems and identifying the use of credential dumping programs such as package.dll.
- Monitor for credential harvesting tools by looking for custom scripts like ldap.pl that used to extract credentials.
Tags: Campaign: Ivanti Exploit Campaign | Target Application: Ivanti Connect Secure, Policy Secure, Neurons for ZTA Gateways | Vulnerabilities Exploited: CVE-2025-0282 (RCE), CVE-2025-0283 (Privilege Escalation) | Attack Techniques: Buffer Overflow, Process Injection, DLL Sideloading, Credential Harvesting
Black Basta Deploying Multiple Malware
(Originally published in January 2025)
The cybersecurity threat landscape continues to evolve with increasing sophistication, as ransomware groups like Black Basta leverage advanced social engineering, custom malware, and cutting-edge evasion techniques.
Black Basta has adapted its tactics to deploy phishing emails, impersonate IT support via Microsoft Teams, and exploit remote access tools (e.g., AnyDesk, QuickAssist, TeamViewer) to gain initial access. Their sophisticated malware arsenal includes credential-stealing Zbot, evasive DarkGate, and custom tools designed to bypass security measures. The group is particularly active in sectors such as healthcare, finance, and national security.
The group has employed a range of evasive tactics, including obfuscated malware payloads, process hollowing, and the exploitation of legitimate platforms like SharePoint for malware distribution. Additionally, QR codes are being used to bypass multi-factor authentication (MFA).
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from the Black Basta campaign.
- Implement robust email filtering systems to block phishing emails, including those with malicious attachments and links. Utilize advanced threat protection tools to detect phishing attempts that may bypass traditional filters.
- Restrict and closely monitor the use of remote access tools such as AnyDesk, QuickAssist, and TeamViewer. Employ network segmentation and enforce access policies to limit remote tool installation to authorized personnel only.
- Enforce the use of multi-factor authentication (MFA) across all critical systems to add an additional layer of protection against account compromise.
- Use behavioral analysis tools to detect abnormal activity on endpoints, such as unusual process creation or injection (e.g., process hollowing), and monitor for signs of malware execution.
- 28 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Ransomware: Black Basta, Attack Type: Phishing, Social Engineering, Payloads: Zbot, DarkGate, Target Sector: Healthcare, Finance, Manufacturing
APT’s Activity (Lazarus & TA397)
(Originally published in January 2025)
This month’s intelligence highlights two prominent cyber threats and these groups highlight the evolving landscape of cyber threats, with advanced techniques and a focus on stealing critical information.
Lazarus Group: This advanced threat actor has targeted cryptocurrency-related entities with a highly sophisticated attack. They compromised the Uniswap Sniper Bot project by injecting malicious code into an Electron-based executable. When the executable is run, it installs the legitimate tool but simultaneously downloads harmful payloads aimed at stealing sensitive data, particularly cryptocurrency wallet information from browsers like Chrome, Brave, and Opera. The attack utilizes complex obfuscation methods to evade detection and involves a multi-stage process where additional payloads—such as keyloggers and clipboard recorders—are pulled in. The Lazarus group also operates remote command-and-control servers to manage the attack, demonstrating their focus on cryptocurrency practitioners and open-source projects in the space. The group’s use of cross-platform tools (Python, JavaScript, and Electron) allows them to target a wide range of systems, including Windows, macOS, and Linux.
TA397 (Bitter): Known for its espionage activities, the Bitter group, also referred to as TA397, is actively targeting critical sectors such as government, energy, telecommunications, defense, and engineering in the EMEA and APAC regions. Their primary goal is information theft, with a focus on acquiring sensitive data and intellectual property. Bitter uses highly targeted spearphishing campaigns to infiltrate networks, deploying malware like WmRAT and MiyaRAT to maintain persistence and exfiltrate valuable data.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat activities.
- Users should refrain from downloading and running executable files, especially from unverified or unofficial sources. This includes checking the integrity of open-source projects before running compiled executables and ensuring they have not been tampered with.
- Organizations and individuals should implement robust cybersecurity measures, including up-to-date antivirus software, regular system scans, and continuous monitoring for unusual activity. Additionally, enabling two-factor authentication (2FA) on cryptocurrency wallets and accounts can provide an extra layer of protection.
- Implement advanced email filtering solutions that can detect and block spearphishing emails, particularly those containing malicious RAR archives and decoy PDF files. Leverage sandboxing and attachment scanning technologies to detect embedded malicious payloads. Ensure that users are trained on recognizing suspicious emails, especially those with unexpected attachments or links, to reduce the risk of initial compromise.
- Prioritize patching of the critical vulnerabilities exploited by TA397, specifically CVE-2018-0802, CVE-2017-11882, CVE-2021-26858, and CVE-2021-27065. In addition, enhance endpoint protection by deploying behavior-based detection tools that can identify suspicious activities, such as the creation of scheduled tasks or communication with known C2 servers. This will help identify and block RAT deployment and data exfiltration attempts before they can escalate.
- 24 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Lazarus group include but are not limited to the following:
- Monitor for outbound traffic from IP: 86.104.74[.]51 (C&C servers). Also, Pay attention to unusual port usage, such as port 1224 or 1244.
- Monitor the system for any signs of obfuscated code or scripts, specifically targeting the file named TokenHash.js, as it is intentionally obfuscated to avoid detection.
- Monitor for the creation of files in unexpected directories (e.g., %userprofile%\.sysinfo or %userprofile%\.n2\).
Tags: APT Group: Lazarus, TA397 | Target Sector: Cryptocurrency-related entities, Government, Energy, Telecommunications, Defense, and Engineering | Target Regions: EMEA, APAC | Malware: WmRAT, MiyaRAT
Ransomware Threat Overview
(Originally published in January 2025)
This month, the FunkSec, Nnice, Hellcat, and Morpheus ransomware groups have continued to focus on high-value sectors, using sophisticated tactics to carry out their attacks. FunkSec has adopted double extortion methods, combining aggressive strategies with DLS capabilities. Nnice targets Windows systems with advanced encryption techniques. Meanwhile, Hellcat and Morpheus operators offer pre-built tools to their affiliates, facilitating the deployment of ransomware.
| FunkSec Ransomware | FunkSec, a new ransomware group that appeared in December 2024, operates under the Ransomware-as-a-Service (RaaS) model, enabling affiliates to use its malicious tools in attacks. The ransomware was developed by an inexperienced Algerian developer using AI. Despite its newcomer status, FunkSec quickly gained notoriety for its aggressive tactics, compromising 85 victims in just over a month. The group is known for its relatively low ransom demands and its practice of selling stolen data at discounted prices to maximize profits and damage the reputation of its targets. |
| Nice Ransomware | First appearing in January 2025, Nnice ransomware has rapidly evolved into a significant threat due to its sophisticated functionality. This new strain of ransomware primarily targets Windows systems, encrypting files by appending the “.xdddd” extension and leaving a ransom note titled “Readme.txt” outlining recovery instructions. It employs advanced evasion techniques, including bootkits, rootkits, and DLL side-loading, making detection and removal challenging.
The attack leverages various MITRE ATT&CK techniques involving persistence, privilege escalation, and defense evasion tactics. It also targets essential system information and has the potential to disrupt system recovery efforts. |
| HellCat and Morpheus RaaS Operators | The HellCat and Morpheus ransomware operations, which emerged in 2024 and 2025 respectively, share almost identical payloads and tactics, suggesting a shared infrastructure or codebase. Both are part of the Ransomware-as-a-Service (RaaS) landscape, with HellCat known for its public image and attacks on high-value targets, and Morpheus focusing on the pharmaceutical and manufacturing sectors.
The payloads used by both operations are 64-bit PE files, approximately 18KB in size. They employ the Windows Cryptographic API for encryption and maintain the original file extensions after encryption. Both also exclude specific file types and system folders from the encryption process. Additionally, the ransom notes from both operations follow the same template, further indicating a connection. Evidence suggests that a common affiliate is responsible for uploading payloads for both ransomware operations, pointing to the possibility that they are using a shared builder or codebase. While there are similarities with Underground Team Ransomware, there’s no evidence to suggest direct collaboration. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware campaigns.
- Implement robust file integrity monitoring and behavioral analysis tools to detect unusual encryption patterns, especially those that do not alter file extensions, as seen with HellCat and Morpheus.
- To counter evolving ransomware threats like FunkSec, organizations should employ advanced threat detection systems that focus on behavioral analysis rather than signature-based detection alone. These systems can identify unusual patterns in file system behavior (such as mass file encryption) and system modifications (like disabling security tools), allowing for early detection before full-scale damage occurs.
- Deploy EDR tools across all endpoints to detect unusual behaviors or file modifications associated with ransomware. These tools can help identify and block the execution of the Nnice ransomware in real-time, minimizing the impact of an infection.
- 18 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the FunkSec ransomware group include but are not limited to the following:
- Monitor for unusual spikes in file system activity, especially involving the modification of file extensions (e.g., changing files to .funksec or other non-standard extensions).
- Monitor for abnormal attempts to run executables with administrative privileges (e.g., using “runas” or similar commands).
TTPs related to the Nnice ransomware group include but are not limited to the following:
- Monitor for Salsa20 and RSA-2048 encryption algorithms.
- Monitor for filename”Readme.txt” and .xddd extension.
TTPs related to the HellCat and Morpheus RaaS Operators include but are not limited to the following:
- Monitor for the encryption of specific file types while excluding known file extensions (such as .dll, .sys, .exe, .drv, .com, .cat.), which can be used to identify malicious encryption attempts.
- Monitor for execution of executables with unusual file sizes or unfamiliar names in network and endpoint logs. In this case, malicious payloads may be small (around 18KB) and use typical Windows APIs (e.g., BCryptEncrypt) for encryption.
- Monitor for executing processes arguments passed to executables, such as encryptor.exe {path} or encryptor.exe ww.
- Monitor for filename er.bat which is used to execute ransomware on target systems.
Tags: Ransomware Group: FunkSec, Nnice, HellCat and Morpheus RaaS Operators | Target: Windows System | Target Sector: Pharmaceutical, Manufacturing
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Dheeraj Kumar, and Sina Chehreghani