- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in June. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
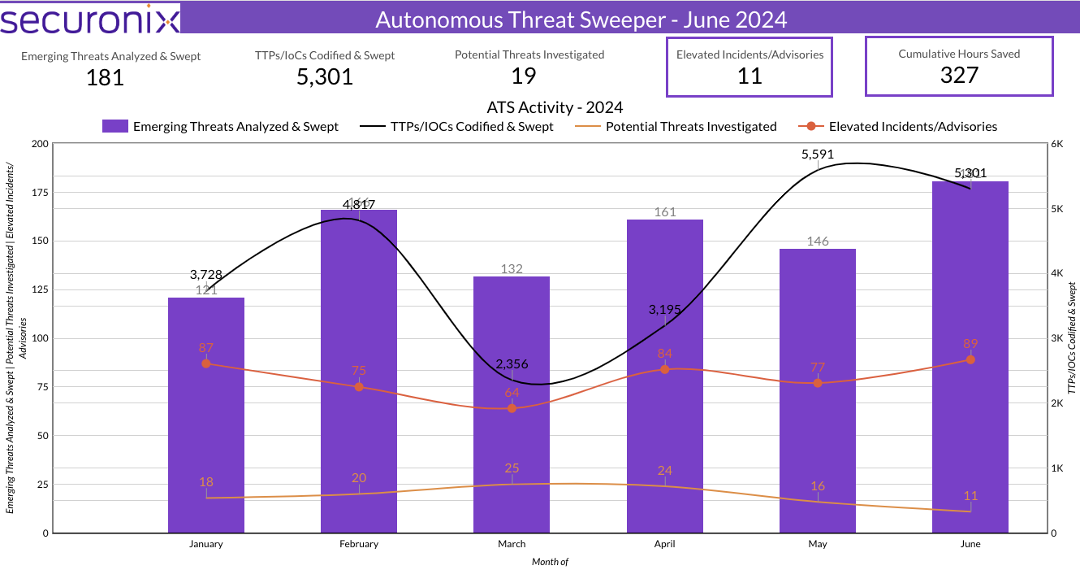
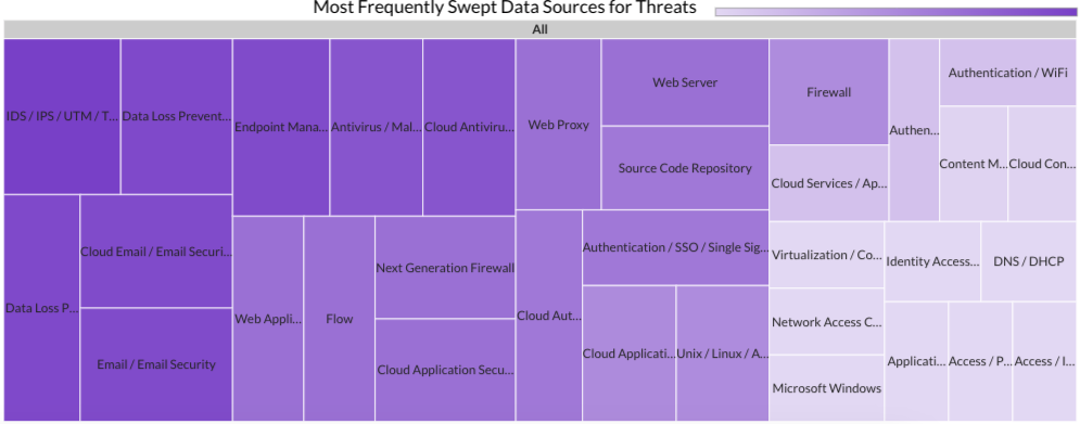
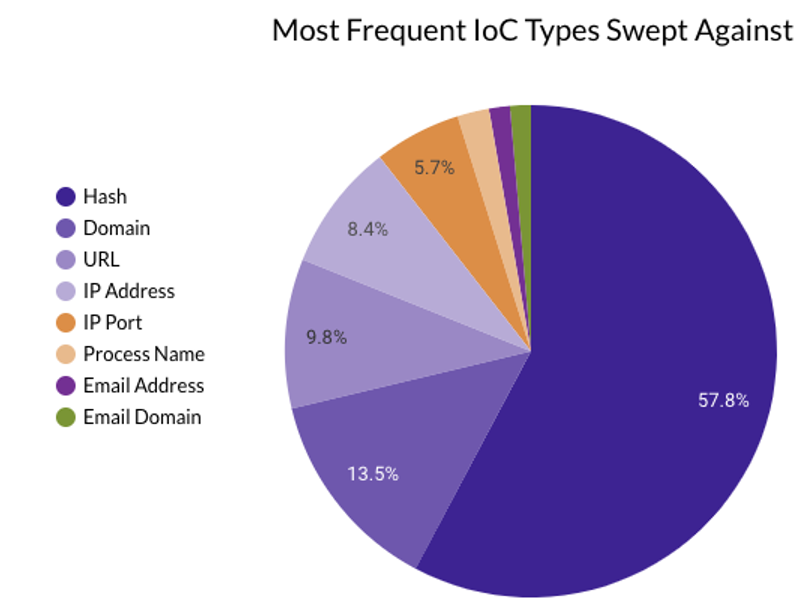
Last month Securonix Autonomous Threat Sweeper identified and analyzed 5,301 TTPs and IoCs, 181 emerging threats, investigated 89 potential threats, and elevated 11 threat incidents. The top data sources swept against include Cloud Application Audit, Cloud Content Management, Cloud Antivirus/Malware/EDR, Data Loss Prevention, and Email/Email Security.
Snowflake Breach
Snowflake has observed and examined a hike in cyber threat activity against some of its customer accounts. They believe that there is an ongoing industry-wide, identity-based attack to obtain customer data. Based on research, these types of attacks are performed using their customers’ user credentials which were exposed through unrelated cyber threat activity. Snowflake believes this activity does not result from any vulnerability, misconfiguration, or malicious actions within the product.
To Back up Snowflakes claim that a string of customer data breaches was down to customer security failures rather than what it said was a limited incident at Snowflake itself, they brought in two of the most well-known incident response companies globally: Mandiant and CrowdStrike.
In 10th June 2024, Mandiant issued a report about a threat campaign that targeted Snowflake customer database instances with the aim of stealing data and asking for money. Snowflake is a multi-cloud data warehousing platform that is used to save and process huge amounts of structured and unstructured information. This cluster of activity is tracked by Mandiant as UNC5537, which they believe is a financially motivated actor who has stolen many records from the environments of Snowflake customers. Using stolen customer credentials, UNC5537 systematically compromises Snowflake customer instances, advertising victim data on cybercrime forums for sale, and attempting to extort multiple victims.
Threat Labs summary
This campaign’s broad impact is the result of an expanding infostealer market and missed chances to enhance credential security:
- UNC5537 probably accessed many different channels of infostealer logs that enabled it to aggregate credentials for Snowflake victim instances. The underground economy on infostealers is also very strong, with huge lists of stolen credentials being available both within and outside the dark web.
- Many of these affected customer instances had no multi-factor authentication implemented on them, and in some cases, their passwords hadn’t been changed as far back as four years. Network allow-lists are also not employed to restrict access to trusted locations.
- 363 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Snowflake Breach include but are not limited to the following:
- Monitor for Snowflake account for Detecting suspicious failed login attempts.
Tags: Threat Actor: UNC5537 | Targeting: Customer Data
PHP vulnerability under active exploit
This month, multiple vendors, one of them ISC.SANS shared their detection of probes for PHP vulnerability CVE-2024-4577 which affects CGI mode in certain locales. It lets OS command injection via user-supplied parameters to “php.exe” on Windows. Watchtwr Labs says PHP is only vulnerable if used in CGI mode in Chinese and Japanese locales.
According to Imperva Threat Researchers, attackers use the recently discovered PHP vulnerability, CVE-2024-4577. Since June 8th, they have seen attacker activity utilizing this vulnerability to distribute malware, which they have now identified as part of the “TellYouThePass” ransomware campaign. TellYouThePass is a ransomware campaign that has been spotted since 2019, targeting both businesses and individuals on Windows and Linux computers. It frequently makes use of CVE-2021-44228 (Apache Log4j), while it has also been observed to make use of CVE-2023-46604 as well.
Bitdefender has also notified about the active exploitation of the vulnerability in PHP. CVE-2024-4577 is a critical flaw affecting PHP versions 5.x and newer on Windows servers, enabling attackers to remotely execute PHP code on compromised servers. This vulnerability originates from how PHP manages character conversions, particularly for languages such as Chinese or Japanese. Exploiting this flaw allows attackers to gain control over servers, posing risks to data confidentiality, system integrity, and availability. Cybercriminals, including groups like “TellYouThePass,” have been actively scanning and exploiting this vulnerability for malicious purposes.
According to Imperva Threat Researchers, attackers use the recently discovered PHP vulnerability, CVE-2024-4577. Since June 8th, they have seen attacker activity utilizing this vulnerability to distribute malware, which they have now identified as part of the “TellYouThePass” ransomware campaign. TellYouThePass is a ransomware campaign that has been spotted since 2019, targeting both businesses and individuals on Windows and Linux computers. It frequently makes use of CVE-2021-44228 (Apache Log4j), while it has also been observed to make use of CVE-2023-46604 as well.
CRIL researchers also analyzed PHP critical Remote Code Execution (RCE) CVE-2024-4577 Vulnerability. PHP. This Vulnerability affects PHP installations on Windows operating systems due to errors in character encoding conversions, particularly impacting the “Best Fit” feature. Exploiting this vulnerability allows attackers to execute arbitrary code remotely posing serious risks.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this vulnerability.
- Monitor for detecting Specific Exploit Patterns in HTTP Requests.
- It is imperative to take immediate action and implement a comprehensive set of security measures. This includes promptly applying patches to address known vulnerabilities, conducting thorough code reviews and audits, and implementing strict access controls and authentication mechanisms to prevent unauthorized access to critical project repositories.
- Additionally, organizations should prioritize training and awareness initiatives to educate project contributors and maintainers about common security threats and best practices for secure coding. Collaborating with industry peers and participating in information-sharing initiatives can further enhance the collective ability to detect and respond to supply-chain attacks effectively.
- By adopting a proactive and collaborative approach to security and implementing the recommended measures, organizations can strengthen the security posture of open-source projects and mitigate the risk of supply-chain attacks.
- 40 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: PHP vulnerability: CVE-2024-4577 | Affected platforms: Windows and Linux computers |Ransomware campaign: “TellYouThePass”
Attacks on the Indian Government
Researchers at Volexity have discovered a cyber-espionage effort carried out by a possible threat actor based in Pakistan, which Volexity is presently monitoring under the alias UTA0137. Volexity lists the malware employed in these latest attacks as DISGOMOJI, which is built for Linux systems and written in Golang. Volexity is confident that UTA0137 has espionage-related goals and a mandate to target government entities in India.
Also, researchers from Cisco Talos have revealed Operation Celestial Force, a new malware operation that has been active since at least 2018. It is still in use today, using a Windows-based malware loader known as HeavyLift in addition to the Android-based malware GravityRAT. A stand-alone program they are referring to as GravityAdmin is responsible for managing all GravityRAT and HeavyLift infections. It performs malicious operations on a compromised device. Analysis of the panel binaries reveals that they are intended to administer and execute numerous campaigns at the same time, each with its own admin panel and codename.
Threat Labs summary
Securonix Threat Labs recommends caution against these attacks and deploying the following protective measures against increased threats:
- Monitor for detecting Execution of Zenity Utility for Social Engineering
- Monitor for detecting Downloads from Suspicious Domains”
- Monitor for detecting GravityRAT Infection on Windows and HeavyLift Loader Activity on Windows
- Monitor for detecting Suspicious Login Attempts via GravityAdmin
- 316 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the DISGOMOJI malware include but are not limited to the following:
- Monitor for detection Execution of Zenity Utility for Social Engineering.
- Monitor for detecting Downloads from Suspicious Domains.
TTPs related to the Operation Celestial Force include but are not limited to the following:
- Monitor for detecting GravityRAT Infection on Windows and HeavyLift Loader Activity on Windows.
- Monitor for detecting Suspicious Login Attempts via GravityAdmin.
Tags: Threat actor: the alias UTA0137 | Goal: Espionage-related goals and a mandate to target government entities in India
Chinese cyber espionage campaigns
Active Chinese cyber espionage campaigns are involved in systematic, state-sponsored efforts to infiltrate foreign networks and steal sensitive information. Intending to gain geopolitical benefits, these operations frequently target businesses, organizations, and governments throughout the world. The attack executed by groups like UNC3886, Crimson Palace, Mustang Panda, and Velvet Ant, employ sophisticated tactics such as rootkit use, malware variants, and custom backdoors on F5 BIG-IP appliances.
| Campaigns | Description |
| UNC3886 espionage operations | UNC3886, a suspicious Chinese threat actor employs public open-source rootkits called ‘Reptile’ and ‘Medusa,’ and attackers have installed them in VMware ESXi to stay undetected while conducting credential theft, command execution, and lateral movement. |
| Crimson Palace | Since at least March 2023, Chinese state-sponsored actors have targeted a government agency as part of a cyberespionage campaign known as Crimson Palace. The campaign leveraged new malware variants and three different activity clusters, which suggest a concerted attack. The three activity clusters were linked to well-known Chinese threat groups, including “BackdoorDiplomacy,” “REF5961,” “Worok,” “TA428,” and the APT41 subgroup Earth Longzhi. |
| Mustang Panda APT Group | A cyber espionage campaign belonging to the Chinese-backed Mustang Panda APT group was found targeting government entities and NGOs in Vietnam using detailed Windows shortcut (LNK) files with tax compliance or education-related themes. Methods used included legitimate tools such as forfiles.exe When carrying out the attack, and malicious scripting languages on the victim file to achieve this purpose of infiltration as well as evasive maneuvers that embed these lured files inside a few others to evade antivirus detection. |
| Noodle RAT | Chinese-speaking threat actors have been using the cross-platform malware known as Noodle RAT, which was previously undocumented, for cybercrimes and espionage purposes for a long time. While this backdoor was previously classified as a version of Gh0st RAT and Rekoobe, researchers claim it is not simply a variant of existing malware, but an entirely new form. Noodle RAT, also known as ANGRYREBEL and Nood RAT, is available in both Windows and Linux variants and is thought to have been in use since at least July 2016. |
| Velvet Ant APT Group | The Velvet Ant group of alleged Chinese cyberespionage actors is using F5 BIG-IP appliances to install proprietary malware to establish a persistent connection to the internal network and collect data. According to a report, that discovered the intrusion after being called in to investigate the cyberattack, Velvet Ant established multiple footholds across the network, including a legacy F5 BIG-IP appliance that served as an internal command and control (C2) server. The infected F5 BIG-IP devices allowed the threat actors to obtain critical customer and financial information from the organization for three years without being noticed. |
| Chinese Espionage Targets Asian Telecom Operators | Since at least 2021, cyber espionage groups associated with China have been linked to a long-running campaign that has compromised various telecom operators based in a single Asian country. The attackers installed backdoors on the networks of the target firms and attempted to steal credentials. The attacks also targeted an unnamed telecom services company and a university in another Asian country. |
| ChamelGang APT Group | SentinelLabs who collaborated with Recorded Future have observed and reported two separate threat groups that are specializing in attacking the government and critical infrastructure sectors around the world between 2021 and 2023. One of these clusters has been linked to the Chinese APT group ChamelGang (a.k.a. CamoFei). The second cluster is similar to previous attacks attributed to suspected Chinese and North Korean APT groups whereas the first one stands out from the usual modus operandi of those teams. Most actions within the activities of these clusters include launching ransomware or data encryption tools, indicating a major risk to organizational data security and operational continuity across industry sectors. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these malicious campaigns.
- Limit outbound internet traffic.
- Limit lateral movement throughout the network.
- Enhance security hardening of legacy servers.
- Mitigate credential harvesting.
- Protect public-facing devices.
- 391 IoCs are available on our Threat Labs home page repository and have been swept for Autonomous Threat Sweeper customers.
TTPs related to the Crimson Palace include but are not limited to the following:
- Monitor DLL Sideloading Detection.
- Monitor to detect suspicious Scheduled Task Creation.
TTPs related to the Velvet Ant APT Group include but are not limited to the following:
- Monitor to detect executions of known PlugX-related files.
- Monitor for suspicious process creations.
TTPs related to the Chinese espionage targets Asian telecom operators include but are not limited to the following:
- Monitor to detect suspicious processes that may be logging keystrokes.
Tags: Threat Actor: UNC3886, Crimson Palace, Mustang Panda, Velvet Ant, ChamelGang | Malware: Noodle RAT | Target Sector: Government, NGOs, Telecom | Target Country: Vietnam
PHANTOM#SPIKE attack campaign
A new phishing campaign has been discovered by the Securonix Threat Research team targeting individuals in Pakistan. This campaign uses a custom backdoor called PHANTOM#SPIKE. Military-themed phishing tactics have been used by the perpetrators behind this operation who are leveraging documents linked to the International Military-Technical Forum Army 2024, a genuine event organized by the Russian Ministry of Defense that will take place in Moscow in mid-August 2024.
The threat actors employed ZIP files containing password-protected payload packages which they used to gain remote access to target devices through to avoid detection. The key feature of this campaign is its simplicity and use of straightforward payloads.
The victims receive emails with ZIP archives claiming to contain meeting minutes from the forum. Once opened, the archive has a harmless Microsoft Compiled HTML Help (CHM) file inside it. When an individual opens this file and clicks on any part of it, a hidden executable known as “RuntimeIndexer.exe” is silently initiated in the background.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this malicious campaign.
- Be Cautious with Downloads: Never download a file or attachment from untrusted sources like email, social media, and messaging applications. Malware is often distributed via ZIP files.
- Check File Extensions: Make sure you crosscheck the extension of any file you want to open with its expected type. To facilitate this process switch on file extensions visibility in your operating system’s settings or right-click on a file and click Properties.
- Watch Important Folders: Frequently inspect directories that are vulnerable to malware attacks, such as C:\ProgramData and %APPDATA%. This is particularly important on script-based activities indicating a security risk.
- Utilize Strong Endpoint Logging: Put in place adequate endpoint logging tools that provide extensive data at the process level. Sysmon tool and enhanced PowerShell logging are extremely useful when it comes to identifying suspicious activities especially those utilizing encrypted channels such as SSL/TLS (port 443).
- Keep Updated And Be Adaptive: Learn about new evolving threats like PHANTOM#SPIKE campaign which uses encryption for evasion purposes. Adapt your security defenses as well as monitoring strategies to be able to counter sophisticated cyber threats.
- 13 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the PHANTOM#SPIKE include but are not limited to the following:
- Monitor suspicious PowerShell and command line activity.
Tags: Malware: PHANTOM#SPIKE | Target: individuals (Comman People) | Target Country: Pakistan | Attack Type: Phishing
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R
Search Query References:
| Campaign | Search Query | Functionality |
| PHP Vulnerability | rg_functionality=”web proxy” and requesturl CONTAINS “%php-cgi/php-cgi.exe?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input%” and requestclientapplication CONTAINS “Go-http-client/1.1” | Web proxy |
| DISGOMOJI malware | rg_functionality = “Antivirus / Malware / EDR” and processname CONTAINS “zenity” or filename CONTAINS “zenity” and message CONTAINS “–text=Firefox update required” or description CONTAINS “–text=Firefox update required”
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND resourcecustomfield1 CONTAINS “.x86_64-linux-gnu” |
Antivirus / Malware / EDR
Endpoint Management Systems |
| Operation Celestial Force Force Targeting Indian Entities | rg_functionality=”Antivirus / Malware / EDR” AND (processname CONTAINS “GravityRAT” OR filename CONTAINS “GravityRAT”) AND (deviceaction=”Process Create” OR deviceaction=”File Create”)
rg_functionality=”Endpoint Management Systems” AND (processname CONTAINS “HeavyLift” OR filename CONTAINS “HeavyLift”) AND (deviceaction=”Process Create” OR deviceaction=”File Create”) AND (commandline CONTAINS “Electron” OR scriptname CONTAINS “Electron”) rg_functionality CONTAINS “Authentication / Login Activity” AND (username CONTAINS “admin” OR username CONTAINS “operator”) AND (authmethod CONTAINS “password” AND destinationhostname CONTAINS “GravityAdmin”) |
Antivirus / Malware / EDR
Endpoint Management Systems Authentication / Login Activity |
| Snowflake Breach | rg_functionality = “Microsoft Windows” and baseeventid= 4625 and accountname NOT CONTAINS $ and accountname CONTAINS “Snowflake” | Microsoft Windows |
| Crimson Palace | Monitor to DLL Sideloading Detection
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname ENDS WITH “vmnat.exe” OR destinationprocessname ENDS WITH “instsrv.exe” OR destinationprocessname ENDS WITH “srvany.exe” AND resourcecustomfield1 CONTAINS “C:\Program Files (x86)\VMware\VMware Workstation\vmnat.exe Monitor to detect suspicious Scheduled Task Creation rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “SyntheticProcessRollUp2” OR deviceaction = “WmiCreateProcess” OR deviceaction = “Trace Executed Process” OR deviceaction = “Process” OR deviceaction = “Childproc” OR deviceaction = “Procstart” OR deviceaction = “Process Activity: Launched”) AND resourcecustomfield1 contains “”schtasks /create”” AND destinationprocessname ENDS WITH “instsrv.exe” OR destinationprocessname ENDS WITH “srvany.exe” |
Endpoint Management SystemsEndpoint Management Systems |
| Velvet Ant APT group | Monitor to detect executions of known PlugX-related files
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname ENDS WITH “iviewers.exe” AND resourcecustomfield1 CONTAINS “C:\Documents and Settings\All Users\Application Data\iviewers.exe” Monitor for suspicious process creations rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname ENDS WITH “svchost.exe” OR destinationprocessname ENDS WITH “iviewers.exe” |
Endpoint Management SystemsEndpoint Management Systems |
| Chinese Espionage Targets Asian Telecom Operators | Monitor to detect suspicious processes that may be logging keystrokes.
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname ENDS WITH “RasTls.dll” OR destinationprocessname ENDS WITH “Coolclient” OR destinationprocessname ENDS WITH “fspmapi.dll” OR destinationprocessname ENDS WITH “security.dll” AND resourcecustomfield1 CONTAINS “%temp%” OR resourcecustomfield1 CONTAINS “%appdata%” Monitor to sideloading activities by looking for legitimate executables loading unusual DLLs. rg_functionality = “Endpoint Management Systems” and processname CONTAINS “VLC Media Player” or processname = fsstm.exe or processname = msproxy.exe AND destinationprocessname ENDS WITH “RasTls.dll” OR destinationprocessname ENDS WITH “libvlc.exe” OR destinationprocessname ENDS WITH “fspmapi.dll” OR destinationprocessname ENDS WITH “security.dll” |
Endpoint Management Systems
Endpoint Management Systems |
| PHANTOM#SPIKE | Monitor Suspicious PowerShell and Command Line Activity
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname ENDS WITH “schtasks.exe” AND resourcecustomfield1 CONTAINS “\Users\Public rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Network connection detected” OR deviceaction = “Network connection detected (rule: NetworkConnect)”) AND destinationhostname CONTAINS “ip-api.com” |
Endpoint Management SystemsEndpoint Management Systems |
Note: These queries in Silo June be prone to false positives and we recommend leveraging it with other stages of the attack progression to increase the likelihood of true positives







