- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in May. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
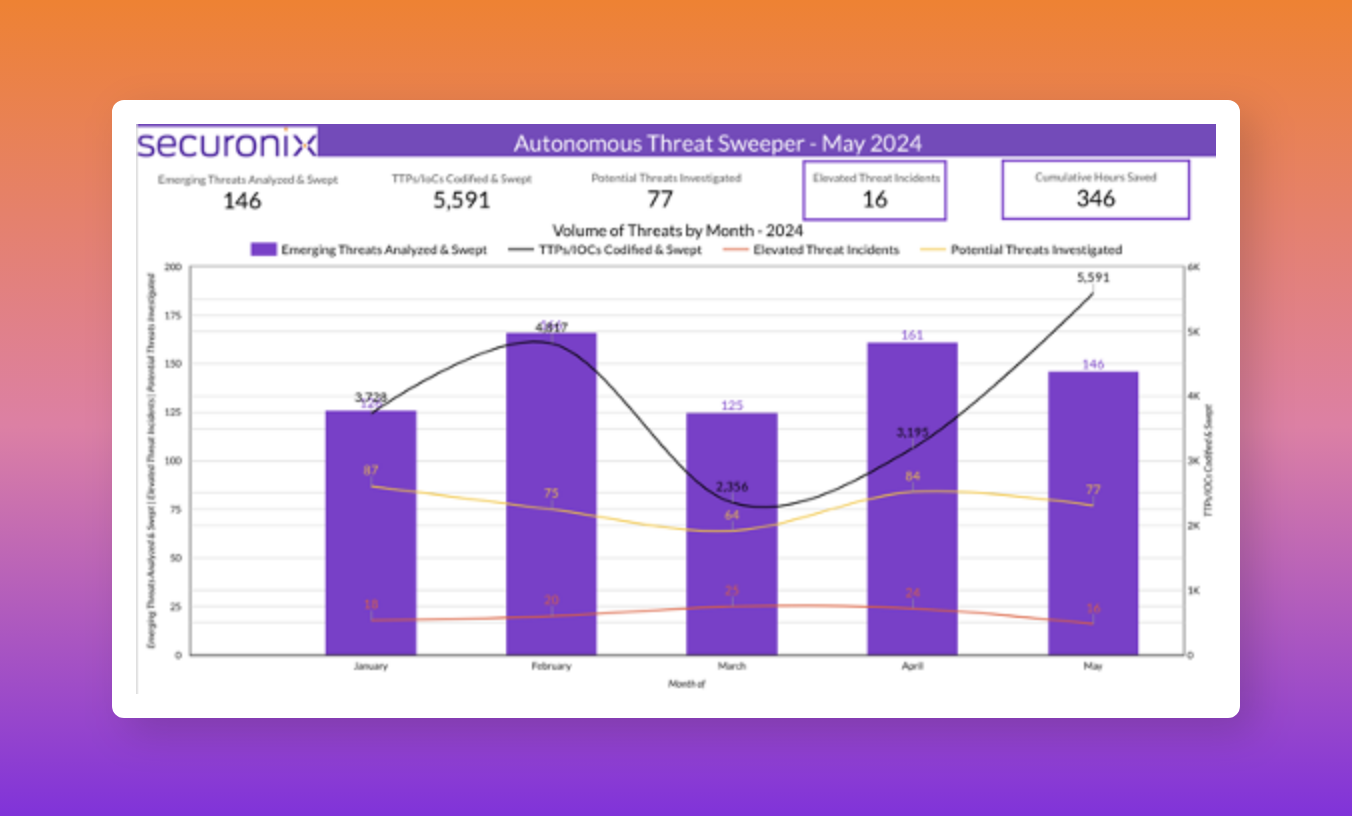
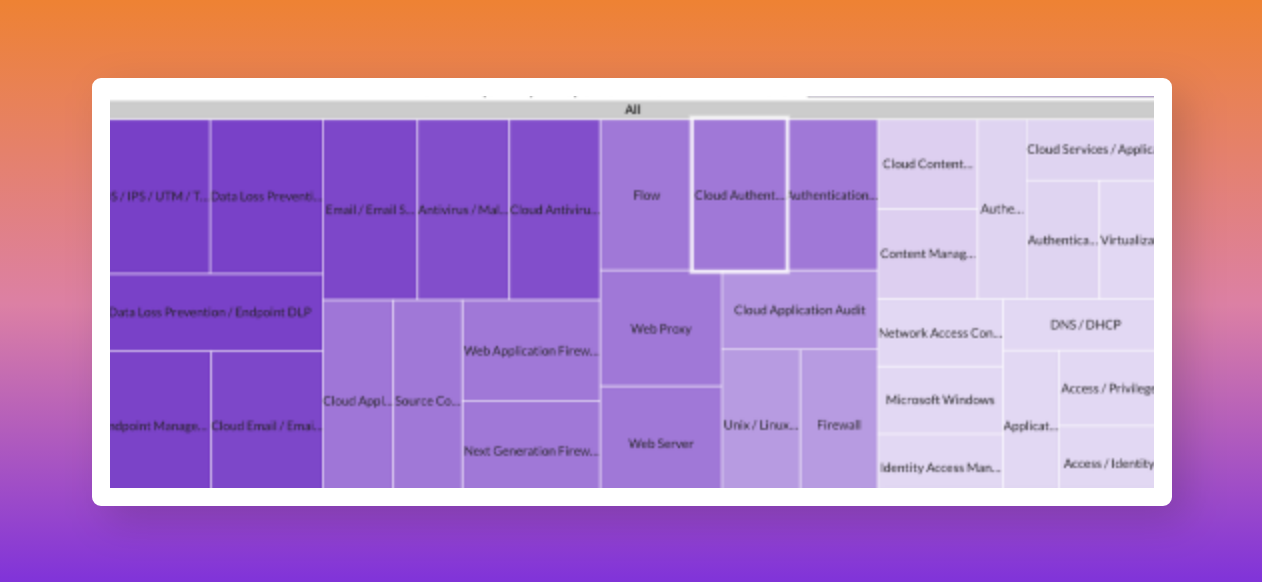
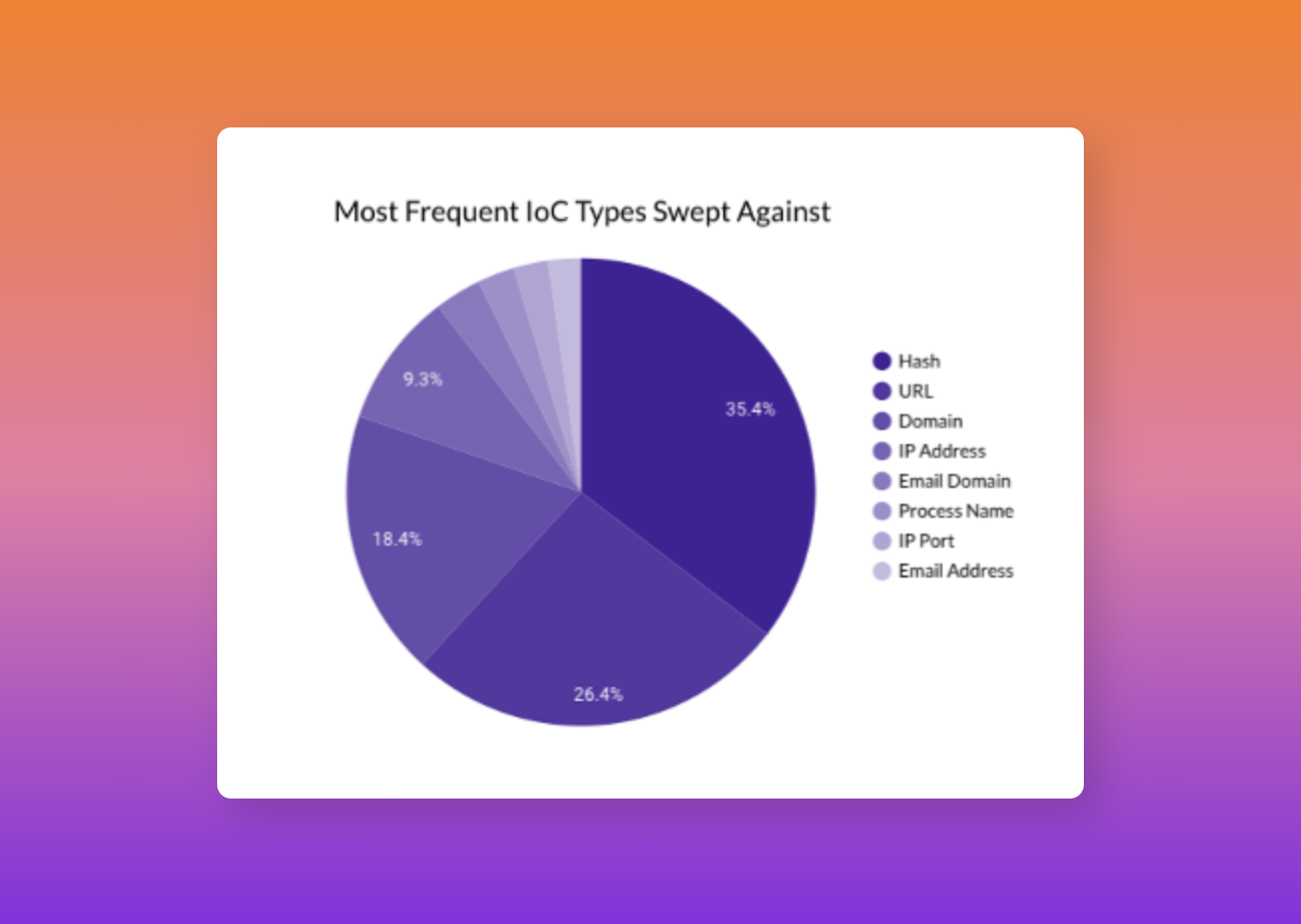
Last month Securonix Autonomous Threat Sweeper identified and analyzed 5,591 TTPs and IoCs, 146 emerging threats, investigated 77 potential threats, and elevated 16 threat incidents. The top data sources swept against include Cloud Application Audit, Cloud Content Management, Cloud Antivirus/Malware/EDR, Data Loss Prevention, and Email/Email Security.
Sophisticated cyberattack targeting MITRE’s NERVE network
(Originally published in May 2024)
The cyber attack on the not-for-profit organization, exploiting zero-day vulnerabilities in Ivanti Connect Secure (ICS) and manipulating the VMware environment, reveals a concerning level of sophistication. The threat actor’s approach involved creating rogue virtual machines (VMs) within the VMware infrastructure using compromised vCenter Server access.
To establish covert communication channels, the attacker deployed a JSP web shell (known as BEEFLUSH) within the vCenter Server’s Tomcat server. This shell was then used to execute a Python-based tunneling tool, facilitating SSH connections between the adversary’s VMs and the ESXi hypervisor infrastructure. This tactic effectively bypasses traditional detection methods, allowing the attacker to operate undetected.
The motive behind these actions seems two-fold: firstly, to evade detection by masking malicious activities from centralized management interfaces like vCenter, and secondly, to maintain persistent access while minimizing the risk of discovery. By leveraging existing infrastructure components and operating within the virtualized environment, the threat actor aims to blend in with legitimate traffic and operations, making detection more challenging.
Threat Labs summary
Securonix Threat Labs recommends caution against these attacks and deploying the following protective measures against increased threats:
- According to the VMware PSIRT team, enabling a secure boot is the most effective countermeasure against the persistence technique. Secure boot is a security feature that verifies the integrity of a host’s boot process, reducing the possibility of unwanted changes.
- Enabling a secure boot is one safeguard against adversaries attempting to obtain permanent access to the VMware environment. Secure boot protects against malicious code injection by checking the integrity of the boot process.
- This countermeasure is consistent with MITRE’s ATT&CK Mitigation: Boot Integrity (M1046).
- Using secure boot, organizations can strengthen the boot process and prevent adversaries from avoiding detection or gaining unauthorized access to critical systems.
- 6 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Target: MITRE’s NERVE Network | Exploitation: Ivanti Connect Secure Zero-Day vulnerabilities tracked as CVE-2023–46805 and CVE-2024–21887
The Latest Social Engineering Scheme of Black Basta
(Originally published in May 2024)
The rise of Black Basta ransomware as a significant threat, along with its affiliates’ tactics, highlights the evolving challenges in global cybersecurity. According to a joint report by CISA, the FBI, HHS, and MS-ISAC, Black Basta ransomware attacks have impacted over 500 organizations and targeted critical infrastructure sectors between May 2022 and May 2024.
According to a joint report published in collaboration with the Department of Health and Human Services (HHS) and the Multi-State Information Sharing and Analysis Center (MS-ISAC), the group encrypted and stole data from at least 12 out of 16 critical infrastructure sectors.
Another effort involves financially motivated cybercriminals using social engineering techniques to infect victims’ networks with Black Basta ransomware payloads by abusing the Windows Quick Assist feature. Since at least mid-May 2024, Microsoft has been looking into this effort. Based on their observations, the threat group (known as Storm-1811) began attacking the target by email bombing them after they had registered their addresses with different email subscription services.
Additionally, a social engineering campaign that has been targeting various managed detection and response (MDR) customers has been uncovered by Rapid7 and ReliaQuest. In one instance, a threat actor called the user and offered help after flooding their inbox with spam. When a user starts to get a lot of spam emails, the attack starts. The threat actor poses as an IT support representative, offering help and telling the user to download a remote access tool, which gives the attacker first access.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threats: In addition to creating detection rules, defenders can dramatically take the following steps to improve their systems’ resilience against these emerging threats.
- To prevent newly registered domains, impose policies on network proxy devices.
- Application control policies can be used to limit RMM usage to authorized software only.
- We advise using application allow listing solutions, like AppLocker or Microsoft Defender Application Control, to prevent any unapproved RMM solutions from operating within the environment and baselining the environment for any installed remote monitoring and management solutions
- 225 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Ransomware: Black Basta | Campaign: Social Engineering | Target: Managed Detection and Response (MDR) Customers, 500 organizations and targeted critical infrastructure sectors
Malware Distribution via Cloud Services
(Originally published in May 2024)
The Securonix Threat Research team has identified a novel attack campaign known as CLOUD#REVERSER, which has been seen staging malicious payloads via trusted cloud storage providers like Dropbox and Google Drive.
Because Google Drive and Dropbox are used as staging platforms to oversee file uploads and downloads, the VBScript and PowerShell scripts in the CLOUD#REVERSER naturally entail command-and-control-like operations. The scripts are intended to fetch files that fit specified patterns, implying that they are waiting for commands or scripts stored in Google Drive or Dropbox.
The attack chain begins with a phishing email that includes a ZIP archive file with an executable disguised as a Microsoft Excel file. In a unique twist, the filename employs the hidden right-to-left override (RLO) Unicode character (U+202E) to reverse the order of the characters following that character in the string.
This causes the victim to see the filename “RFQ-101432620247fl*U+202E*xslx.exe” instead of “RFQ-101432620247flexe.xlsx,” leading them to believe that they are opening an Excel document.
It is intended for the executable to drop eight payloads in total, which include a decoy Excel file (“20240416.xlsx”) and a heavily obfuscated Visual Basic (VB) Script (“3156.vbs”) that shows the user the XLSX file in order to continue the ruse and start two more scripts called “i4703.vbs” and “i6050.vbs.”
Threat Labs summary
Securonix Threat Labs advised the following for prevention and detection in the context of unwanted emails: always proceed with caution when responding to such emails, particularly if they appear unexpected or urgent.
- Phishing emails and creative lures remain common methods of malware delivery for threat actors. Users must be aware of the strategies used by attackers to trick their victims into installing malware. In the case of the CLOUD#REVERSER campaign, double extensions were employed to mislead the user into running a single executable file from a ZIP file. Its icon was altered to resemble a standard Microsoft Excel file to give the executable file further a genuine appearance.
- It is advisable to avoid downloading files or attachments from untrusted sources. The most common file formats are pdf, iso, rar, and zip. There were zip files utilized in this campaign.
- Keep an eye out for common malware staging directories, particularly for any activity involving scripts in world-writable directories. In this campaign, the threat actors are staged in the C:\ProgramData directory.
- The threat actors used encrypted channels via Dropbox and Google servers via encrypted API connections during different stages of the CLOUD#REVERSER campaign in order to stage and exfiltrate data. For this reason, we highly advise implementing comprehensive endpoint logging features. To increase log detection coverage, this involves utilizing additional process-level logging tools like Sysmon and PowerShell logging.
- 16 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the CLOUD#REVERSER include but are not limited to the following:
- Monitor for Windows Powershell Activity Query specifically looking for messages that contain references to Dropbox API or Google Drive URLs.
- Monitor endpoint management systems for specific process creation activities related to svchost.exe. It focuses on processes that are created with a particular set of parameters (-k netsvcs -p -s Schedule) and involve files in the \ProgramData directory. This could be used to detect suspicious behavior or the presence of malware that abuses svchost.exe for persistence or other malicious activities.
Tags: Campaign: CLOUD#REVERSER | SIEM | Weapon: Phishing email bearing a ZIP archive file, which contains an executable that masquerades as a Microsoft Excel file | Payload Delivery: Leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads
The DNS attack campaigns
(Originally published in May 2024)
This month was a rise of DNS campaigns including a Sophisticated DNS Centric Operation, the exploit of weak DMARC Security Policies, and a couple of campaigns using DNS tunneling.
Researchers from Infoblox presented a groundbreaking study on Muddling Meerkat, a sophisticated actor believed to be a Chinese nation-state entity, conducting extensive operations through DNS queries. The operations, which began around October 2019, involve the utilization of Chinese IP space, manipulation of the Great Firewall, and the creation of false MX records. Despite appearing akin to DNS DDoS attacks, the true motivations behind Muddling Meerkat’s activities remain elusive. The research underscores the actor’s expertise in DNS manipulation and highlights the challenges in detecting and attributing such complex cyber threats.
Also, The FBI and the NSA jointly issued this advisory to highlight attempts by the Democratic People’s Republic of Korea (DPRK, a.k.a. North Korea) Kimsuky cyber actors to exploit improperly configured DNS Domain-based Message Authentication, Reporting, and Conformance (DMARC) record policies to conceal social engineering attempts. Without properly configured DMARC policies, malicious cyber actors can send spoofed emails as if they came from a legitimate domain’s email exchange. North Korea using these attacks to collect intelligence on geopolitical events, adversary foreign policy strategies, and any information affecting North Korean interests by gaining illicit access to targets’ private documents, research, and communications.
And another campaign information came from the Palo Alto research team who shared the details of their case study on new applications of domain name system (DNS) tunneling that they found in the wild. These techniques expand beyond DNS tunneling only for command and control (C2) and virtual private network (VPN) purposes. Palo Alto researchers detected three recent campaigns using DNS tunneling for purposes outside of traditional C2 and VPN use: scanning and tracking. In scanning, adversaries employ DNS tunneling to scan a victim’s network infrastructure and gather information useful for future attacks. In tracking, adversaries use DNS tunneling techniques to track the delivery of malicious emails and monitor the use of Content Delivery Networks.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these malicious campaigns.
- Provide the appropriate security awareness training to your personnel as MuddyWater uses spear phishing.
- Regularly apply security patches and updates to the software.
- Apply the least privilege approach across the network, with a focus on important systems and services.
- Apply best practices to secure domain controllers (DC).
- Set up multifactor authentication (MFA) to prevent lateral movement.
- 91 IoCs are available on our Threat Labs home page repository and have been swept for Autonomous Threat Sweeper customers.
Tags: Threat Actor: Muddling Meerkat, Kimsuky| Advanced WildFire, Cortex XDR, DNS security, DNS tunneling, next-generation firewall, Prisma Cloud
Active phishing campaigns
(Originally published in May 2024)
Multi-Component Banking trojan and its expanding LATAM-Focused Campaigns were observed this month. A sophisticated banking trojan operating globally as a Malware-as-a-Service (MaaS). It targets over 1500 banking applications across 60+ countries, with a recent surge in phishing campaigns impersonating government entities in Latin America. These campaigns, notably in Mexico and Argentina, employ urgent messages to lure victims into downloading malicious files disguised as legitimate documents. With advanced features like string decryption and dynamic domain generation, Grandoreiro poses a significant threat to online banking security, highlighting the evolving landscape of cyber threats in the region.
It is encouraged that organizations that may be impacted by these campaigns review the following recommendations:
- Exercise caution with emails and PDFs prompting a file download
- Monitor network traffic for multiple consecutive requests to http://ip-api.com/json as a potential indicator of a Grandoreiro infection
- Consider blocking pre-calculated DGA domains via DNS
- Monitor registry Run keys used for persistence
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Install and configure endpoint security software
- Update relevant network security monitoring rules
- 28 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat: Grandoreiro banking trojan | Targets: Central and South America, Africa, Europe, the Pacific, Spain, Japan, the Netherlands, and Italy
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R