- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Dheeraj Kumar, Ella Dragun, Securonix Threat Labs
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in November. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In November 2023, Threat Labs analyzed and monitored major threat categories: Israel-Hamas cyber war, SEO#LURKER attack campaign, infection chains on Middle Eastern government entities, attacks on the energy sector and nuclear energy firms, and the Scattered Spider campaign.
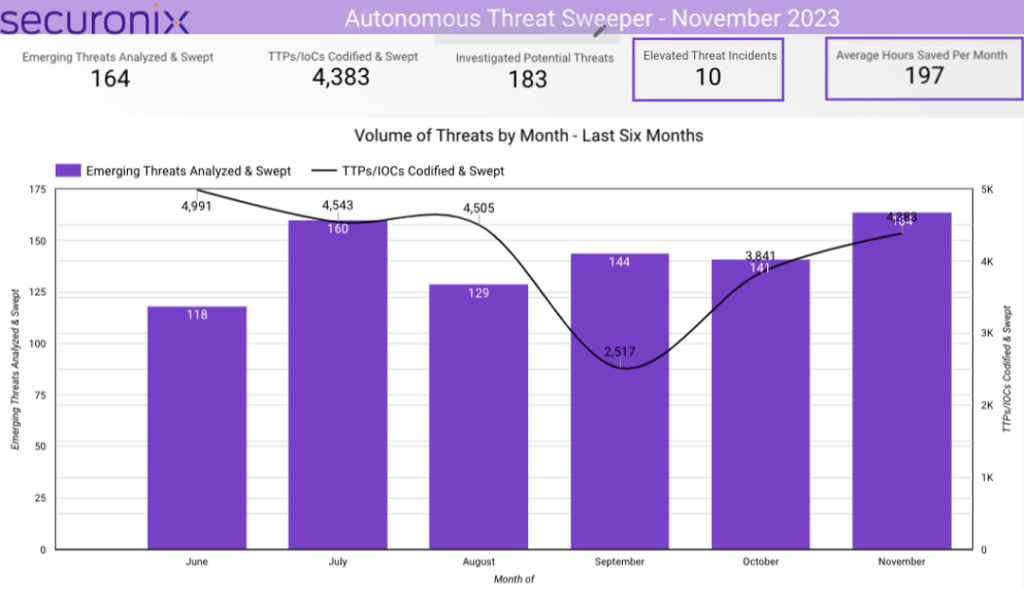
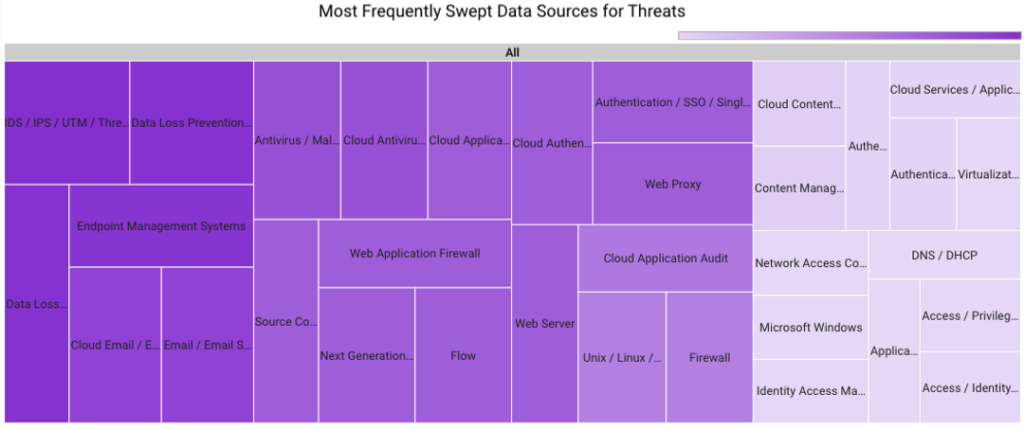
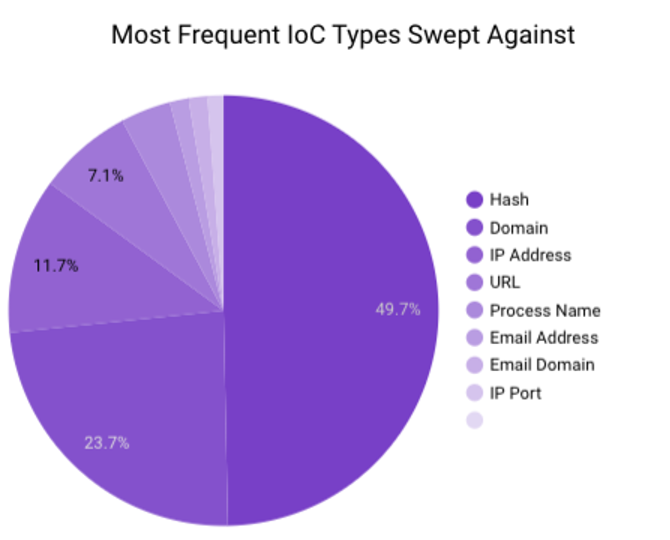
In November 2023, Securonix Autonomous Threat Sweeper identified 4,383 TTPs and IoCs, analyzed 164 emerging threats, investigated 183 potential threats and elevated 10 threat incidents. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
SEO#LURKER attack campaign (Originally published in November 2023)
Fake search results and fake Google ads are being used by threat actors to deceive people into installing malware when they intend to download safe applications like WinSCP. Securonix is monitoring the activities under the handle SEO#LURKER. When users click on the malicious advertisement or search result they are taken to a WordPress website that has been compromised, which leads to a phishing site under the control of the attacker. It is believed that the threat actors use Google’s Dynamic Search Ads (DSAs), which display fake ads that direct victims to the compromised website by automatically generating ads based on the user’s search term, which is WinSCP in this case.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from this campaign.
- The intricate, multi-phase attack chain’s main objective is to trick visitors into clicking on the fake winccp[.]net page and downloading the malware.
- The right setting of the referrer header is necessary for traffic from the gaweeweb[.]com website to the fake winsccp[.]net website. If the referrer is not set correctly, the user is ‘Rickrolled’ and directed to the iconic Rick Astley YouTube video.
- The last payload is a ZIP file (“WinSCP_v.6.1.zip”) containing an executable setup that uses DLL side-loading to load and run a DLL file called python311.dll that is contained in the archive.
- 21 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the SEO#LURKER attack campaign include but are not limited to the following:
- Web Proxy Activity:
- Search for activities in the “activity” index related to the Web Proxy functionality.
- Narrow down the results to events where the destination address is one of three specified IP addresses.
- Additionally, filter by destination port, allowing only port 443 or 8443.
- Endpoint management systems – network connections:
- Focus on activities in the “activity” index related to endpoint management systems functionality.
- Look for events where the device action is either “Network connection detected” or “Network connection detected (rule: NetworkConnect).”
- Filter further by destination hostnames containing specific domains.
- Endpoint management systems – MSI.dll activity:
- Search for activities in the “activity” index related to endpoint management systems functionality.
- Specifically, look for events with a base event ID of 7 and where customstring67 ends with “\msi.dll.”
- Exclude events where customstring67 contains “\windows\system32” or “\windows\syswow64.”
- Endpoint management systems – schtasks.exe activity:
- Focus on activities in the “activity” index related to endpoint management systems functionality.
- Look for events related to process creation (various device actions) where the destination process name is “schtasks.exe.”
- Further filter by resource custom field 1 containing “\Appdata\Local” or “\Appdata\Roaming.”
Tags: Threat Name: SEO#LURKER | Target: WordPress website, Google’s Dynamic Search Ads (DSAs) | Target Product: WinSCP
Israel-Hamas cyber war (Originally published in November 2023)
Cyberthreats have increased since the crisis erupted on October 7, 2023, when Hamas took a militant posture against Israel. For instance, a number of hacktivists who support Hamas and Palestine in conjunction with state-sponsored aggressors have launched cyber attacks on Israeli companies with the intention of completely ruining the country’s economy. Victim companies responded by contacting Israeli CERT and law enforcement, who then worked with the Incident Response team to try and recover from the breaches.
During this period following the start of the Israel-Hamas War, MuddyWater launched a new social engineering campaign against Israel. Researchers discovered two archives stored on “Storyblok” on October 30th that had a brand-new, multi-stage infection vector. It includes hidden files, an executable file meant to reveal a bogus document while running the remote administration program Advanced Monitoring Agent, and an LNK file that starts the infection.
Experts have uncovered SysJoker, a cross-platform backdoor implemented in Rust that is thought to have been used by a threat actor connected to Hamas to attack Israel during the current conflict in the region.
Also, cyber experts have issued a warning regarding a Windows variant of wiper malware that was previously seen attacking Linux systems in cyberattacks directed towards Israel.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these campaigns.
- In January 2022, Intezer released public documentation on SysJoker, characterizing it as a C++ backdoor that can access a text file hosted on Google Drive that has a hard-coded URL, allowing it to gather system information and establish contact with an attacker-controlled server.
- Following the start of the Israel-Hamas war, a group with ties to Iran began targeting the Middle East’s transportation, logistics, and technology sectors, particularly those in Israel, in October 2023.
- The Windows version shows that the attack is being expanded to target application servers and end user computers, confirming that the threat actors behind the wiper are still developing the virus.
- We recommend that in order to identify and address any exposed administrative interfaces, companies conduct a comprehensive External Attack Surface Assessment. It is also critical to increase cybersecurity awareness and enable MFA for all employees.
- 43 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Iran Group MuddyWater Targeting Israel include but are not limited to the following:
- Monitor for the presence of the following filenames in the directory – /usr/lib64/seahorses/
- – ‘kbioset’
- – ‘cpc’
- – ‘kkdmflush’
- – ‘soss’
- – ‘sshod’
- – ‘nethoogs’
- – ‘iftoop’
- – ‘iptraof’
TTPs related to the Extensive Data-Wiping Operation Aimed Against Israel include but are not limited to the following:
- Monitor execution of following processes:
- exe, HolyLocker.exe and BTLC.exe
- Detects for a following command line in which the malware creates or deletes a scheduled task called lockertask and can be used for Persistence:
- exe /Q /c schtasks /create /tn lockertask /tr [File] /sc minute /mo 1 /F /ru system 1> \\127.0.0.1\ADMIN$\__[randomnumber] 2>&1
Tags: APT Group: MuddyWater | Campaign: Social Engineering | Target Geo-Location: Israel | Malware: Storyblok, SysJoker, Wiper | Affected System: Windows, Linux | Target Sector: Middle East’s transportation, logistics, technology sectors
Infection chain attacks on Middle Eastern government entities (Originally published in November 2023)
The TA402, a Middle Eastern advanced persistent threat (APT) group, is consistently engaged in extremely targeted activity, pursuing less than five organizations with any single campaign. They maintain a strong focus on government entities based in the Middle East and North Africa and historically have operated in the interests of the Palestinian territories and overlap with public reporting on Molerats, Gaza Cybergang, Frankenstein, and WIRTE.
From July to October 2023, Proofpoint researchers observed the TA402 group executing targeted phishing campaigns against Middle East and North Africa government entities using an unique infection chain called IronWind. The group used a variety of its attack methods to deliver the multifunctional malware. TA402 campaigns involved phishing emails with lures related to economic themes or regional conflicts, utilizing compromised email accounts to deliver malware that communicated with a command-and-control domain. The IronWind downloader initiated a multi-stage infection process, involving a .NET executable and shellcode, aimed at espionage and intelligence collection. The group consistently employed geofencing techniques to hinder detection and maintained a focus on specific targets, despite ongoing regional conflicts. This activity demonstrates TA402’s persistent and evolving approach to cyber espionage.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this vulnerability.
- Continually perform backups and store the results either offline or on a different network.
- On your computer, smartphone, and other connected devices, turn on automatic software upgrades whenever possible.
- Conduct employee awareness training on a regular basis.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against malware, BlueCharlie specifically.
- Use a trusted antivirus and internet security software suite on all connected devices, including your computer, laptop, and mobile.
- Avoid opening email attachments without first verifying their legitimacy and clicking on dubious links.
- 22 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the infection chains on Middle East-Based government entities include but are not limited to the following:
- Monitor for rare file names with the extension .HLJkNskOq
Tags: Attack Type: Infection chain | Target Geo-Location: Government entities based in the Middle East and North Africa
Attacks on the energy sector and on nuclear energy firms (Originally published in November 2023)
Resecurity has observed an increasing rise in ransomware operators attacking the energy sector, including nuclear facilities and related research entities. Over the last year, ransomware attackers have targeted energy installations in North America, Asia, and the European Union.
Resecurity identified a potential breach of Doosan’s Active Directory and other nuclear research organizations, as well as a BlackCat ransomware attack on the European energy sector in February 2022. Additionally, threat actors have been targeting nuclear-energy firms and related entities, such as Brazil’s National Nuclear Energy Commission, Israel’s Neve Ne’eman nuclear reactor, and Indonesia’s National Nuclear Energy Agency (Batan). In April 2022, Oil India Limited (OIL) was hit by a ransomware attack, and in March 2022, State Electric Company Limited (STELCO) in Maldives experienced a ransomware attack by the Hive group.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from these ransomware.
- Continually perform backups and store the results either offline or on a different network.
- On your computer, smartphone, and other connected devices, turn on automatic software upgrades whenever possible.
- Conduct employee awareness training on a regular basis.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against malware, BlueCharlie specifically.
- Use a trusted antivirus and internet security software suite on all connected devices, including your computer, laptop, and mobile.
- Avoid opening email attachments without first verifying their legitimacy and clicking on dubious links.
- 8 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Target Sectors: the energy sector, including nuclear facilities and related research entities | Target Geo-Location: North America, Asia, and the European Union.
Scattered Spider (Originally published in November 2023)
U.S. cybersecurity and intelligence agencies released a combined advisory about Scattered Spider, a cybercriminal group ,known to use sophisticated phishing techniques to infiltrate targets. These threat actors usually use a variety of social engineering strategies to steal data for extortion. Recently, the agencies added the BlackCat/ALPHV ransomware to their arsenal of tools.
The threat actor was the focus of a detailed Microsoft analysis last month, in which the tech giant referred to it as “one of the most dangerous financial criminal groups.” It is also known by the names Muddled Libra, Octo Tempest, 0ktapus, Scatter Swine, Star Fraud, and UNC3944.
Experts in social engineering, Scattered Spider is recognized for their ability to acquire credentials, install remote access tools, and get beyond multi-factor authentication (MFA) using phishing, prompt bombing, and SIM switching attacks.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this campaign.
- Like LAPSUS$, Scattered Spider is purportedly a part of a broader Gen Z cybercrime ecosystem that goes by the name of the Com (sometimes written Comm), and has turned to swatting attacks and violent behavior.
- Phasing IT and help desk workers through phone calls or SMS messages to target employees and obtain higher access to the networks is one of its noteworthy strategies.
- Following a successful initial entry, remote access trojans and stealers like AveMaria (aka Warzone RAT), Raccoon Stealer, and Vidar Stealer are deployed together with genuine remote access tunneling tools like Fleetdeck.io, Ngrok, and Pulseway.
- 3 IoCs are available on our Threat Labs home page and have been swept against Autonomous Threat Sweeper customers.
Tags: APT Group: Scattered Spider | Attack Type: Phishing, Prompt Bombing, SIM swapping
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R