- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in November 2024. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
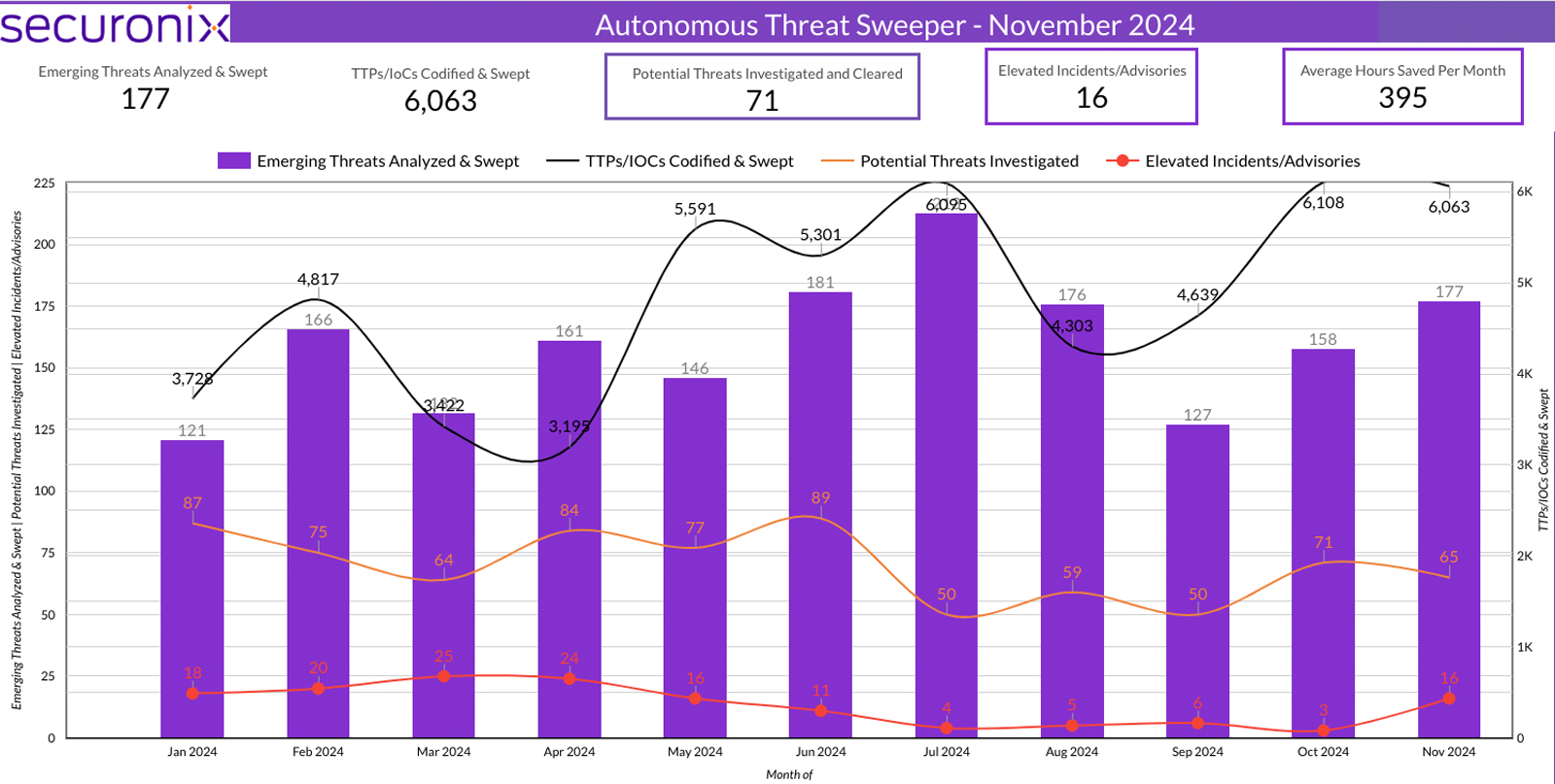
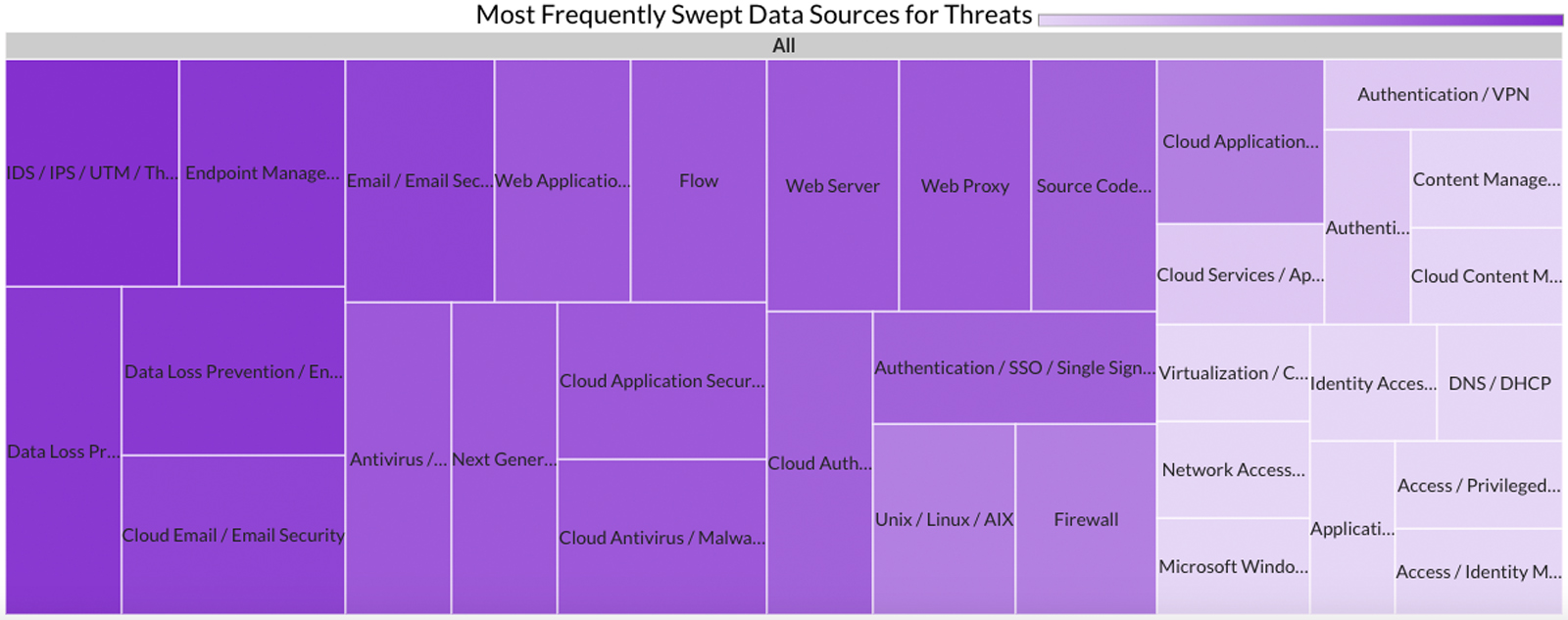
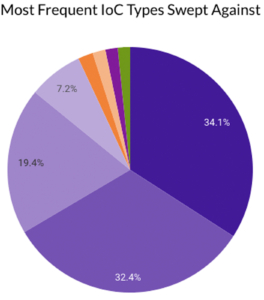
Last month Securonix Autonomous Threat Sweeper identified and analyzed 6,063 TTPs and IoCs, 177 emerging threats, investigated 65 potential threats, and elevated 16 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.

Vulnerability of the Month
(Originally published in November 2024)
This month’s report highlights the discovery of Lunar Peek vulnerabilities, which expose systems to unauthorized access and data breaches. Additionally, several zero-day vulnerabilities in Windows have been identified, putting users at risk of exploitation. Both threats require immediate attention, with ongoing efforts focused on patching and securing affected systems.
Operation Lunar Peek: Palo Alto Networks and Unit 42 are tracked exploitation activities related to CVE-2024-0012 and CVE-2024-9474 vulnerabilities. CVE-2024-0012, an authentication bypass in Palo Alto Networks PAN-OS, allows unauthenticated attackers with network access to the management interface to gain administrator privileges, enabling them to perform administrative actions or exploit other vulnerabilities like CVE-2024-9474. Initial threat activity targeting a limited number of device management interfaces was detected on November 18, 2024, originating from IP addresses linked to anonymous VPN services. Post-exploitation activities observed included command execution and malware deployment, such as obfuscated web shells, on compromised firewalls. Fixes for both vulnerabilities are available.
Zero-Day Vulnerability in Windows: A newly discovered zero-day vulnerability in Windows, tracked as CVE-2024-43451, affects the MSHTM engine and can be exploited with minimal user interaction, such as right-clicking, deleting, or moving a file. This vulnerability, which impacts applications using the WebBrowser control in Edge’s Internet Explorer mode, allows attackers to steal NTLMv2 hashes and conduct pass-the-hash attacks. Identified by ClearSky and reported to Microsoft in June 2024, the flaw was actively exploited by a suspected Russian threat actor in attacks targeting Ukrainian entities. Phishing emails with malicious ZIP files, containing a URL file, were used to trigger the vulnerability, leading to the download of additional malware, including SparkRAT. On Windows 10 and 11, the flaw is triggered immediately, while older versions like Windows 7, 8, and 8.1 require multiple attempts to exploit it.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these vulnerabilities.
- To reduce security risks, limit access to the management interface by allowing only trusted internal IP addresses, preventing external access from the internet.
- Palo Alto Networks advises updating to the latest patches to address the CVE-2024-0012 and CVE-2024-9474 vulnerabilities. For detailed information on affected products and versions, refer to the Palo Alto Networks Security Advisories.
- Ensure that all affected systems have been updated with the patches released by Microsoft in the November security update. Regularly check for updates and promptly apply them, especially for critical vulnerabilities like CVE-2024-43451 and CVE-2024-49039, to close security gaps and reduce the risk of exploitation.
- For vulnerabilities like CVE-2024-49039, which involve privilege escalation, organizations should enforce the principle of least privilege. To reduce the impact of potential attacks, limit user and process permissions, especially for those running with low privileges like AppContainers. Additionally, consider using security features like Windows Defender Application Control (WDAC) to restrict which applications can run with elevated privileges.
- 54 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Zero-Day vulnerability in Windows include but are not limited to the following:
- Monitor for the zip file named “humeniuk_liubov_stanislavivna[.]zip”
- Monitor for filename “Certificate_Activate_45052389_005553[.]exe”
Tags: Vulnerability: CVE-2024-0012, CVE-2024-9474, CVE-2024-43451 | Affected Product: PAN-OS, Windows
Rising phishing campaigns
(Originally published in November 2024)
The targeted phishing campaign was detected in November, using deceptive emails to steal sensitive information. The campaign employed social engineering tactics to create urgency.
The CRON#TRAP campaign, uncovered by the Securonix Threat Research team, utilizes a novel attack chain where attackers deploy a custom-made Linux environment emulated through QEMU (Quick Emulator) on compromised endpoints, delivered via phishing emails. The attack employs a malicious shortcut (.lnk) file to trigger the deployment. The emulated Linux environment is pre-configured with a backdoor that connects to an attacker-controlled Command and Control (C2) server, ensuring persistent access to the victim’s system. QEMU’s use as a legitimate tool for development helps it evade detection by traditional antivirus software. The campaign mainly targets North America, with notable activity from the US and Europe, marking the first known malicious use of QEMU outside of cryptomining.
Secondly, a new cyber threat campaign was uncovered called “VEILDrive,” which leverages Microsoft’s SaaS services: Teams, SharePoint, Quick Assist, and OneDrive. Especially OneDrive, for Command & Control (C&C). First discovered in September 2024 during an investigation into a cyberattack on critical U.S. infrastructure, VEILDrive is believed to originate from a Russian threat actor. The attack uses Microsoft’s cloud services to distribute spear-phishing emails and store malware, making detection difficult.
The malware associated with VEILDrive is a Java-based .jar file with transparent, non-obfuscated code, which is unusually readable and well-structured. Despite its simplicity, it evaded detection by both a top-tier Endpoint Detection and Response (EDR) tool and all security engines on VirusTotal, highlighting a gap in current detection strategies. This campaign, which began in August 2024, showcases a novel use of cloud infrastructure for evading traditional security defenses and emphasizes the need for updated detection techniques in high-risk environments.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these phishing campaigns.
- Monitor Common Malware Staging Directories: Focus on monitoring script-related activities in world-writable directories. In the case of the recent campaign, threat actors staged their QEMU instance from the user’s home directory at `%HOME%\datax`.
- Deploy Robust Endpoint Logging for PowerShell Detection: Implement strong endpoint logging capabilities, especially for PowerShell detections. Use tools like Sysmon and enable PowerShell logging to improve detection coverage at the process level.
- Restrict External Access in Microsoft Teams: By default, Microsoft Teams allows “External Access,” permitting one-on-one chats with outside contacts. If this feature is not essential, consider disabling it. For external communication, use the guest or member features, limiting access to high-privileged users.
- Limit Remote Administration Tools: Restrict remote administration tools to approved applications. For example, Quick Assist can be downloaded from the Microsoft Store, so block its use unless explicitly required. Use measures like AppLocker, Windows Firewall rules, or MDM management to enforce these restrictions.
- 28 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the CRON#TRAP campaign include but are not limited to the following:
- Monitor for .lnk files that invoke PowerShell commands or batch scripts, particularly those that extract and execute files from unusual locations (e.g., %HOMEPATH%\datax\data\start.bat).
- Monitor for the execution of fontdiag.exe or any executable that resembles QEMU or virtualization-related processes (e.g., qemu.exe, fontdiag.exe renamed from QEMU).
- Monitor for silent virtualized environments (emulated Linux) that run with the -nographic flag. These environments may appear as background processes without visible windows or typical user interaction.
- Monitor for the use of commands related to system enumeration and diagnostics (e.g., uname -a, df, ls -hal, get-host-user, get-host-shell) from unusual or non-standard processes.
- Monitor for the use of tools like filetool.sh -b, which can back up and restore configurations in virtualized environments, ensuring persistence even after reboots or virtual machine resets.
TTPs related to the VEILDrive campaign include but are not limited to the following:
- Monitor for the creation of scheduled tasks that execute unknown or unauthorized applications (e.g., ROMServer.exe, javaw.exe -jar).
- Monitor for suspicious registry keys or run entries (e.g., entries under HKCU\Software\Microsoft\Windows\CurrentVersion\Run) that could enable persistence.
Tags: Campaign: CRON#TRAP, VEILDrive | Attack Type: Phishing, Spear-phishing | Target Application: Teams, SharePoint, Quick Assist, OneDrive | Target Country: North America, US, Europe
Ransomware threat landscape
(Originally published in November 2024)
Interlock, Yamir, and BianLian ransomware groups continue to target high-value sectors using advanced tactics. Interlock employs double extortion, big-game hunting, and threatening to leak data. Yamir ransomware used RustyStealer for exfiltrating the data of organizations. BianLian Ransomware targets the critical sector with new data exfiltration-based extortion tactics.
| Interlock ransomware group | InterLock ransomware first appeared in the cyber threat arena in September 2024 and is believed to be linked with Rhysida ransomware group. They launch big-game hunting and double extortion attacks against global organizations including healthcare, technology, and the public sector in the U.S., as well as manufacturing in Europe and encrypt files with a .interlock extension and place a ransom note to respond within 96 hours under threat of leaking the data and notifying the media. The ransomware operators operate a data leak site Worldwide Secrets Blog where they post victim’s leaked data. They primarily use RDP for lateral movement within the victim’s network along with tools like AnyDesk and PuTTY. Additionally, they apply Azure Storage Explorer and AZCopy to exfiltrate data to an attacker-controlled Azure storage blob. |
| Ymir Ransomware | Ymir ransomware represents an evolution in the ransomware landscape because of a unique combination of technical features and tactics. The threat actor leveraged an unconventional blend of memory management functions – malloc, memmove, and memcmp to execute malicious code directly in the memory. They targeted the organization in Colombia and used RustyStealer to harvest corporate credentials before deploying Ymir ransomware. The ransomware operators use ChaCha20 encryption and encrypt the files with .6C5oy2dVr6 extension and generate a ransom note titled INCIDENT_REPORT.pdf in affected directories. |
| BianLian Ransomware | A joint advisory has been released by the FBI, CISA, and ASD’s ACSC regarding an ongoing #StopRansomware effort related to BianLian Ransomware group. The group has been active since at least 2022 and is believed to operate from Russia with its several affiliates. They primarily target critical infrastructure organizations in the U.S. and Australia and are involved in the development, deployment, and data exfiltration-based extortion tactics. The group often gains access through RDP credentials, uses open-source tools, and exfiltrates victim data via FTP, Rclone, or Mega. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware campaigns.
- To mitigate the lateral movement of ransomware, particularly from group Interlock, implement strong network segmentation. Restrict access based on least-privilege principles and ensure critical systems are isolated from general user networks to limit the impact of an attack.
- Ymir and BianLian often exfiltrate sensitive data before encryption. Implement strong data loss prevention (DLP) measures and monitor for unusual data transfers or large-scale file movements. Encrypt sensitive data both in transit and at rest to protect it even if stolen.
- To mitigate from BianLian Ransomware disable command-line and scripting activities and permissions. Update Windows PowerShell or PowerShell Core to the latest version and uninstall all earlier PowerShell versions.
- 33 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Interlock ransomware group include but are not limited to the following:
- Monitor for .interlock extension.
- Monitor for apple-online[.]shop and upd_2327991.exe
TTPs related to the Ymir ransomware group include but are not limited to the following:
- Monitor for ChaCha20 encryption
- Monitor for filename INCIDENT_REPORT.pdf
TTPs related to the BianLian Ransomware include but are not limited to the following:
- Monitor for the portable executable version of an Impacket tool (secretsdump.py)
- Monitor for .bianlian extension.
Tags: Ransomware Group: Interlock, Ymir, BianLain | Target Location: U.S, Europe, Columbia, Australia | Target: Healthcare, Technology, Public sector, Manufacturing, and Critical Sector.
Emerging malware threats
(Originally published in November 2024)
The Pygmy Goat campaign has evolved as a sophisticated attack that targets network infrastructure devices, including Sophos XG firewalls. The malware maintains stealth and persistence by using techniques such as LD_PRELOAD and raw socket protocols. Its use of ICMP port knocking and SSH hooks for command-and-control initiation, as well as the ability to alter tasks, capture packets, and proxy traffic, demonstrate its potential for long-term exploitation.
Meanwhile, Palo Alto researchers discussed the FrostyGoop campaign (also known as BUSTLEBERM), which began in 2024 as an OT-centric malware attack on industrial control systems. The malware particularly targeted the Modbus TCP protocol to damage essential infrastructure, resulting in a two-day heating outage that affected over 600 buildings in Ukraine.
The attack focused largely on municipal energy systems, using flaws in MikroTik routers or exposed OT devices to get access. FrostyGoop’s capabilities include delivering Modbus commands to modify ICS devices, creating system failures, and using JSON configurations to launch targeted attacks. Although it was designed to attack ENCO control devices, it may now attack any Modbus TCP-compatible system.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat activities.
- Patch Vulnerabilities: Update MikroTik routers, ENCO devices, and other OT/ICS devices to protect against known vulnerabilities.
- Implement Layered Security: To ensure full security, use Next-Generation Firewalls, Industrial OT Security, and Advanced Threat Prevention.
- Improve Threat Detection: Use Cortex XDR, XSIAM, and Advanced WildFire to do behavioral analytics, threat hunting, and malware blocking.
- Monitor for Anomalous Behavior: Track suspicious network activity, unauthorized Modbus TCP operations, and default credential usage.
- 14 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Pygmy Goat campaign include but are not limited to the following:
- Monitor for LD_PRELOAD usage to detect potential code injection attempts.
- Monitor for ICMP port knocking activity as a sign of covert C2 initiation.
- Monitor for raw socket operations to identify potential evasion techniques in network communications.
TTPs related to the FrostyGoop campaign include but are not limited to the following:
- Monitor for Modbus TCP Commands
- Monitor for Exposed OT Devices
- Monitor for Abnormal JSON Configurations
Tags: Malware: Pygmy Goat backdoor, FrostyGoop | Vulnerability: MikroTik router | Target Sector: Municipal energy systems, Network infrastructure | Affected Product: Sophos XG firewalls, ENCO control devices, ICS/OT systems | Target Location: Ukraine
Active threat group spotlight
(Originally published in November 2024)
In November, TA455 targeted the aerospace industry using social engineering tactics. BrazenBamboo focused on data exfiltration, leveraging a custom post-exploitation toolkit named ‘DeepData’. TAG-110 continued exploiting vulnerabilities in public-facing apps, using custom malware tools HATVIBE and CHERRYSPY. New cyber threat cluster Venture Wolf has been targeting industries with MetaStealer since November 2023.
| Venture Wolf threat group | A new threat actor cluster, named Venture Wolf, has been discovered, with its activity traced back to November 2023. The group primarily uses loaders to deliver MetaStealer, a type of information-stealing malware, targeting various industries such as manufacturing, construction, IT, and telecommunications.
The attack chain involves the delivery of compressed archives containing a loader (with .com or .exe extensions) along with phishing documents (e.g., JPG, PNG, PDF, DOCX, ODT files) as decoys. The loader, which is a Portable Executable (PE) file, uses obfuscated code and encrypted WinAPI function names to evade detection. In many cases, the loader injects the payload into a dummy .NET file or directly into the RegAsm.exe process. |
| TA455 group | The Iranian hacking group TA455, linked to the Islamic Revolutionary Guard Corps (IRGC), has been observed using tactics similar to North Korean groups in a campaign targeting the aerospace industry. Starting in September 2023, the group used fake job offers to distribute the SnailResin malware, activating the SlugResin backdoor. The attacks also involved social engineering strategies to deliver two backdoors, MINIBIKE and MINIBUS. TA455 shares operational similarities with other groups like Smoke Sandstorm (formerly Bohrium) and Crimson Sandstorm (formerly Curium). |
| BrazenBamboo group | Chinese threat group “BrazenBamboo” has been using a custom post-exploitation toolkit called “DeepData” to exploit a zero-day vulnerability in Fortinet’s FortiClient Windows VPN client, enabling them to steal user credentials. The vulnerability allows the extraction of credentials from memory after users authenticate with the VPN. Researchers at Volexity discovered and reported the flaw to Fortinet in July 2024, which was acknowledged by the company shortly after.
DeepData is a modular tool that uses plugins for targeted data theft, including one for FortiClient that locates and decrypts credentials stored in the software’s memory. These credentials are then exfiltrated to the attacker’s server using another malware, DeepPost. BrazenBamboo, known for developing advanced malware like LightSpy (a multi-platform spyware) and DeepPost, uses this vulnerability to gain initial access to corporate networks and expand their espionage activities. |
| TAG-110 | A cyber espionage campaign attributed to a Russian-linked threat actor, TAG-110, has targeted organizations in Central Asia, East Asia, and Europe since at least 2021. The group, also tracked as UAC-0063 by CERT-UA, uses custom malware tools like HATVIBE and CHERRYSPY to attack government entities, human rights groups, and educational institutions. Key targets include Central Asian countries, such as Tajikistan, Kyrgyzstan, and Kazakhstan, likely for intelligence gathering to support Russia’s geopolitical interests. The group exploits vulnerabilities in public-facing web applications and uses phishing emails to deploy its malware, designed for data exfiltration. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these threat actors.
- Deploy advanced email filtering solutions to block malicious attachments (e.g., .exe, .com, PDF, DOCX) and detect phishing attempts that deliver these malicious files. By scanning and filtering out suspicious attachments and links in emails, organizations can significantly reduce the risk of initial infection through the delivery of loaders and decoy files used in MetaStealer campaigns.
- Implement advanced email security solutions to detect and block phishing emails, especially those containing attachments disguised as job-related documents. These solutions should be capable of detecting malicious ZIP files, DLL side-loading techniques, and suspicious executable files (like “SignedConnection.exe”). Additionally, using web filtering tools to block access to known malicious websites (e.g., careers2find[.]com) and scrutinizing traffic to unusual domains (e.g., GitHub used for C2) can help prevent the initial compromise.
- Limit access to the VPN, especially for high-risk users or critical systems, and enforce strict access controls. Continuously monitor VPN login activity for unusual or unauthorized logins, such as attempts from unexpected IP addresses or abnormal usage patterns, which could indicate an ongoing attack.
- Since TAG-110 relies on exploiting security flaws in public-facing web applications (such as the Rejetto HTTP File Server), it is critical for organizations to regularly update and patch all software, particularly those accessible via the internet. This includes applying security patches for web applications, network infrastructure, and operating systems to close known vulnerabilities that the attackers may exploit. Additionally, organizations should implement robust web application firewalls (WAFs) and other perimeter defenses to detect and block malicious activities targeting these vulnerabilities.
- 178 IoCs are available on our Threat Labs home page repository and have been swept for Autonomous Threat Sweeper customers.
TTPs related to the Venture Wolf threat group include but are not limited to the following:
- Monitor for archives containing a loader with the .com (and occasionally .exe) extension.
- The loader creates a suspended process to inject malicious payloads (e.g., by using CreateProcessW with the CREATE_SUSPENDED flag). Any new or unusual processes in a suspended state should be flagged for investigation.
- Monitor for the use of “VirtualAllocEx” to allocate memory in the suspended, as this is often associated with code injection.
- Monitor for the process uses “WriteProcessMemory” to write suspicious or encrypted data into a memory location, this indicates possible code injection.
- Monitoring for the use of “Wow64SetThreadContext” or “SetThreadContext” to change the execution context of a thread may help identify processes trying to execute injected code.
- Monitor for section names such as .enigma1, .vmp0, .themida
TTPs related to the BrazenBamboo Threat Actor include but are not limited to the following:
- Monitor for processes with unusual memory consumption, particularly the FortiClient process, where credentials could be residing in unencrypted memory.
- Monitor for the presence of files associated with DEEPDATA, such as: deepdata.zip, data.dll (DEEPDATA Loader), frame.dll, ffmpeg.dll, vertdll.dll, iumdll.dll, ucrtbase_enclave.dll (Core DEEPDATA files), msenvico.dll (FortiClient plugin library)
- Monitor for the presence of files like mod.dat that may contain encrypted malware components that are decrypted and executed by the loader (data.dll).
- Monitor for suspicious outbound network communication to known C2 servers: DEEPDATA: Ports 28443, 28992, 28993 and LIGHTSPY: Ports 52202, 43202, 54602
- The Windows variant of LIGHTSPY uses UDP for its unique handshake, specifically a 102-byte packet starting with 0x1A5F2E1. Monitor for this UDP traffic pattern on your network.
- Monitor for unexpected exfiltration attempts via HTTPS (particularly to api/third/file/upload/), usually over port 29983 (or other custom ports set by the operator). The localupload.exe tool be used for this purpose.
- Monitor for suspicious or unauthorized DLL injections into legitimate processes (e.g., ffmpeg.dll, frame.dll), which are indicative of plugin execution.
- Monitor for new or unusual system processes that might be associated with malware running in the background, such as localupload.exe, LIGHTSPY orchestrator, or other tools associated with DEEPDATA.
Tags: Threat actor: Venture Wolf, TA455, BrazenBamboo, TAG-110, UAC-0063 | Target Sector: Manufacturing, Construction, IT, Telecommunications, Aerospace, Government entities, Human Rights groups, Educational Institutions | Malware: SnailResin | Target Location: Central Asia, East Asia, Europe, Tajikistan, Kyrgyzstan, Kazakhstan | Tools: HATVIBE, CHERRYSPY, DeepData
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh, Nikhil Kumar Chadha







