- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in October 2024. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
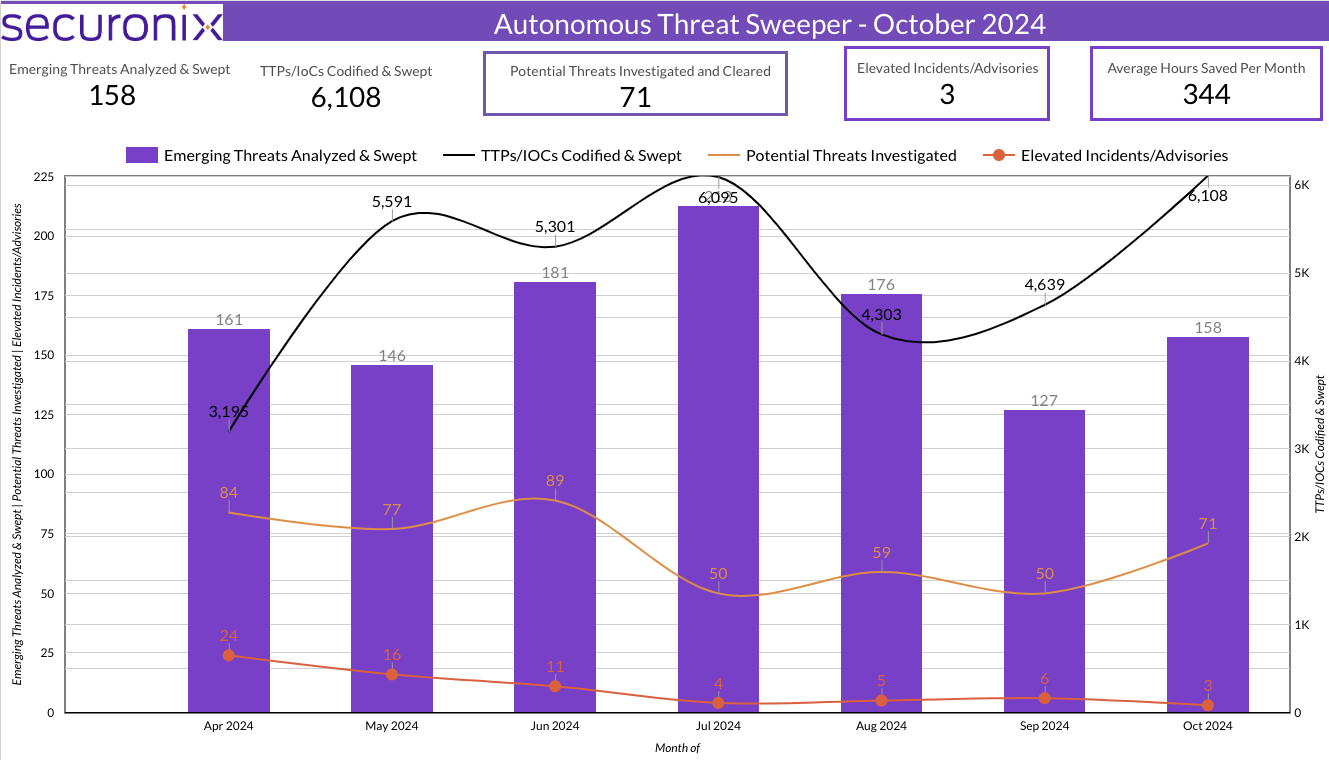
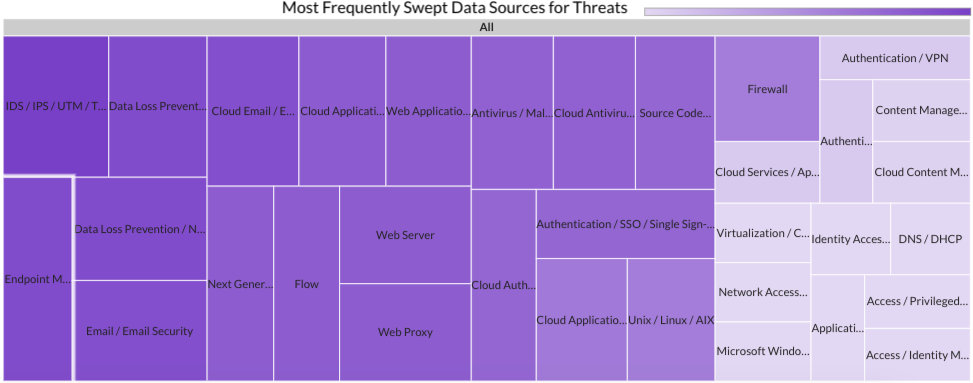
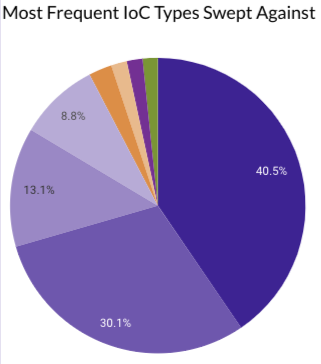
Last month Securonix Autonomous Threat Sweeper identified and analyzed 6,108 TTPs and IoCs, 158 emerging threats, investigated 71 potential threats, and elevated 3 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
 .
. 

New FortiJump vulnerability or CVE-2024-47575
(Originally published in October 2024)
A critical vulnerability, CVE-2024-47575 (also known as “FortiJump”), was identified in FortiManager, affecting both on-premises and cloud versions. The flaw, discovered in collaboration between Fortinet and Mandiant, stems from a missing authentication check in the FortiGate-FortiManager communication protocol (FGFM), specifically in the fgfmsd daemon. This vulnerability allows remote, unauthenticated attackers to execute arbitrary commands on affected systems.
The vulnerability was first exploited in attacks as early as June 27, 2024, by the threat group UNC5820. Fortinet released a patch for the issue on October 23, 2024, following earlier notifications to affected customers. However, as of the time of publication, over 59,000 devices were still exposed, tracked by Shodan.
Attackers exploiting this vulnerability can access FortiManager, potentially compromising all connected FortiGate firewalls and network security devices. This could lead to the theft of sensitive data such as FortiGate configurations and hashed passwords, allowing attackers to escalate their attack and move laterally within the network. Organizations with exposed FortiManager instances are urged to conduct immediate forensic investigations.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this vulnerability.
- Apply the patch provided by Fortinet.
- Limit access to the FortiManager admin interface so that only trusted internal IP addresses are allowed. Avoid exposing FortiManager appliances to the public internet wherever possible.
- Implement strict whitelisting controls to allow only authorized FortiGate devices to communicate with the FortiManager system.
- Ensure that FortiManager does not accept or associate with any unrecognized or unauthorized FortiGate devices.
- Deny unknown FortiGate devices from being associated with FortiManager.
- 12 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Vulnerability: CVE-ID: CVE-2024-47575, FortiJump | Affected Product: FortiManager
ClickFix tactic targets Google Meet users
(Originally published in October 2024)
Threat actors are using fake Google Meet web pages as part of a malware campaign called ClickFix to distribute infostealers targeting both Windows and macOS systems. The attack works by displaying deceptive error messages in web browsers, prompting users to execute malicious PowerShell code manually. This action leads to the installation of malware. On Windows, the attack delivers StealC and Rhadamanthys stealers, while macOS users receive a malicious disk image (“Launcher_v1.94.dmg”) that drops the Atomic stealer. The ClickFix campaign, also known as ClearFake and OneDrive Pastejacking, uses social engineering techniques to bypass security tools by tricking users into running the malware themselves.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this malicious campaign.
- The victim is redirected to a fake page where a pop-up message appears, claiming there is a technical issue with their microphone or headset.
- If they click on “Try Fix,” the page initiates a standard ClickFix infection process. This process involves copying PowerShell code from the website and pasting it into the Windows command prompt, which triggers the malware infection. The malware fetches its payload from the ‘googiedrivers[.]com’ domain.
- The malware payloads include information-stealing malware such as Stealc or Rhadamanthys for Windows. On macOS, the threat actor drops the AMOS Stealer, packaged as a .DMG file named ‘Launcher_v194.’
- In addition to targeting Google Meet, several other malware distribution campaigns have been identified, including those targeting Zoom, PDF readers, fake video games (Lunacy, Calipso, Battleforge, Ragon), Web3 browsers and projects (NGT Studio), and messenger apps (Nortex).
- 138 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Target System: Windows, MacOS | Malware: ClickFix | InfoStealer: StealC, Rhadamanthys stealers, Atomic stealer
Ransomware threat landscape
(Originally published in October 2024)
Keygroup777, Meow, Prince, Dark Angels, and Embargo ransomware groups continue to target high-value sectors using advanced tactics. Keygroup777 employs double extortion, encrypting and threatening to leak data. Meow and Meow Leaks focus on data exfiltration and public leaks to pressure victims. Prince ransomware stealthily infiltrates industries like finance and healthcare. Dark Angels utilizes ransomware-as-a-service, and Embargo spreads via exploits, threatening widespread data leaks.
|
Key Group or keygroup777 ransomware group |
Key Group, also known as keygroup777, is a ransomware group with financial motivations that mostly targets Russian users. The group is well-known for employing the Chaos ransomware builder and negotiating with victims on Telegram. The Key Group operates under a ransomware-as-a-service model, recruiting affiliates to deploy ransomware on victim networks. The group relies on encrypted communication via Telegram to share information about victims, payment instructions, and decryptor tools. Additionally, it details the group’s targeted industries and regions, showing their adaptability in exploiting vulnerabilities to gain unauthorized access. |
|
Meow and Meow Leaks ransomware group |
Meow is a ransomware group that emerged in 2022, linked to the Conti malware family, and is believed to operate under the Ransomware as a Service (RaaS) model. It primarily targets organizations in multiple countries including the United States, the United Kingdom, Nigeria, and Italy, and encrypts files with a .meow extension, demanding payment through email or Telegram. Meow is suspected to be a variant of the Conti group, following the leak of Conti’s source code. In 2023, a decryptor was released, which likely hindered the group’s operations. Meanwhile, “Meow Leaks,” a related but distinct entity, surfaced in 2023, focusing more on data exfiltration than encryption, leading to debate on whether Meow and Meow Leaks are the same group or separate operations. |
|
Prince Ransomware |
In mid-September, researchers identified a campaign delivering Prince ransomware, which impersonated the UK postal service Royal Mail. The campaign primarily targeted organizations in the UK and the US, with most messages originating via contact forms on victim organization’s websites, rather than direct email. The emails contained a PDF attachment that included a Dropbox URL leading to a ZIP file. Inside the ZIP file was another password-protected ZIP containing a shortcut (LNK) file and a text file with the password. Executing the shortcut ran JavaScript that extracted and executed malicious code. Prince ransomware, which is freely available on GitHub, does not offer decryption capabilities and lacks data exfiltration features, making its impact more destructive than typical ransomware. The attack was low-volume, affecting only a small number of organizations. |
|
The Dark Angels Ransomware Group |
The Dark Angels ransomware group, identified in 2022, employs a highly targeted and stealthy attack strategy, focusing on a small number of large companies to maximize financial gains while minimizing attention. Unlike many ransomware groups, Dark Angels avoid third-party brokers, launching their own attacks with sophisticated methods. They use payloads like Babuk, RTM Locker, and RagnarLocker to encrypt files on Windows and Linux/ESXi systems. The group also steals large volumes of sensitive data, often demanding payment to prevent leaks, particularly when they choose not to deploy ransomware. In 2024, they made headlines with a record $75 million ransom demand. |
|
Embargo Ransomware |
A new Rust-based ransomware toolkit used by the Embargo group was first identified in June 2024. The toolkit includes a loader (MDeployer) and an EDR killer (MS4Killer), both custom-compiled for each victim’s environment. MS4Killer targets specific security solutions, disabling them by exploiting a vulnerable driver. Embargo, which made its public debut in May 2024, primarily targets high-profile organizations and uses Rust for its ransomware payloads, allowing for cross-platform attacks on both Windows and Linux systems. The group is part of a broader trend of ransomware developers choosing Rust, following other notable groups like BlackCat and Hive. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware campaigns.
- To mitigate the lateral movement of ransomware, particularly from groups like Keygroup777 and Prince, implement strong network segmentation. Restrict access based on least-privilege principles and ensure critical systems are isolated from general user networks to limit the impact of an attack.
- Meow, Meow Leaks, and Embargo ransomware groups often exfiltrate sensitive data before encryption. Implement strong data loss prevention (DLP) measures and monitor for unusual data transfers or large-scale file movements. Encrypt sensitive data both in transit and at rest to protect it even if stolen.
- As groups like Dark Angels and Embargo exploit unpatched vulnerabilities, it is essential to maintain a rigorous patch management process. Adopting a Zero Trust security model, where all internal and external connections are authenticated and continuously validated, can help prevent unauthorized access to systems.
- Ensure that critical data is backed up regularly and stored in an isolated, offline environment, out of reach of ransomware groups. This is especially important given the double-extortion tactics used by Keygroup777 and the data leak threats from groups like Meow Leaks and Embargo. Test backups regularly for integrity and recovery capability.
- 89 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Key Group or keygroup777 ransomware group include but are not limited to the following:
- Monitor for .huis_bn extension.
TTPs related to the Meow and Meow Leaks ransomware group include but are not limited to the following:
- Monitor for MegaSync executable to a local account on a victim system. It is a cloud storage client, was likely the application used for exfiltration.
- Monitor for the file called truenight.sys. This system file, known for interacting with actions at the kernel-level can kill EDR processes.
TTPs related to the Prince Ransomware include but are not limited to the following:
- Monitor for ZIP file named “PACKAGE-0074752.zip” and “invoice.zip”.
- Monitor for text file named “privacy notice.txt”.
TTPs related to The Dark Angels Ransomware Group include but are not limited to the following:
- Monitor for ChaCha20 encryption.
- Monitor the encryption using a combination of asymmetric ECC and symmetric 256-bit AES in CBC mode.
TTPs related to the Embargo Ransomware include but are not limited to the following:
- Monitor for filename “HOW_TO_RECOVER_FILES.txt”
Tags: Ransomware Group: Key Group or keygroup777, Meow, Prince, Dark Angels, Embargo | Target System: Windows, Linux | Target Location: Russia, United States, United Kingdom, Nigeria, Italy | Target: UK postal service Royal Mail
Recent malware activities
(Originally published in October 2024)
This month saw the resurgence of Bumblebee malware with evasive techniques, and the emergence of PerfCtl malware, which uses system tools for concealment and malicious activities.
The resurgence of Bumblebee malware, particularly after Europol’s Operation Endgame disrupted its activities in May 2024, signals the likely return of the Bumblebee loader. First detected by Google Threat Analysis Group in 2022, Bumblebee is a highly sophisticated downloader malware that primarily targets corporate networks, facilitating the delivery of other payloads such as Cobalt Strike beacons and ransomware.
In the latest campaign, Bumblebee is being used in a multi-stage delivery process, with malicious files disguised as legitimate applications such as Nvidia and Midjourney installers being deployed to infect systems.
Meanwhile, Aqua Nautilus researchers have uncovered a new Linux malware called perfctl. This malware primarily targets Linux servers across various industries, deploying cryptominers and proxy-jacking software by exploiting vulnerabilities and misconfigurations. In its final stage, it fraudulently hijacks server resources.
Perfctl leverages the TOR network for encrypted communication, employs rootkits to hide its presence, and disguises itself as a legitimate system program to avoid detection. Once installed, it replicates itself in multiple directories with fake names, deletes its original files post-execution, and persists as a background service.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat activities.
- Enhance EDR Configurations: Regularly review and update EDR settings to ensure they are configured to detect and respond to suspicious activities, including attempts to disable EDR functionalities.
- Implement Layered Security: Utilize a multi-layered security approach that combines EDR with other protective measures, such as firewalls, intrusion detection systems, and advanced threat protection.
- Regular System Updates: Keep all systems and software up to date with the latest security patches to close vulnerabilities that malware might exploit.
- Incident Response Planning: Develop and regularly update an incident response strategy that addresses communication, recovery processes, and containment protocols for different cyber instances.
- Monitor for Anomalous Behavior: Set up monitoring to detect unusual activity that may indicate an ongoing attack, such as unexpected CPU consumption, unauthorized access attempts, or unusual network connections.
- 23 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Bumblebee malware campaign include but are not limited to the following:
- Monitor for Phishing emails with a ZIP file containing an LNK file.
TTPs related to the Perfctl malware campaign include but are not limited to the following:
- Monitor for Changes in System Utilities Like look for indicators of tampering in system utilities (such as ldd, lsof, and top), as attackers may replace them with trojanized versions to mask harmful activity.
Tags: Malware: BumblebeeLoader, PerfCtl | Vulnerability: Polkit vulnerability (CVE-2021-4034)| Target Sector: Corporate networks
The threat group showdown
(Originally published in October 2024)
In October, multiple advanced persistent threat (APT) groups were active. Transparent Tribe targeted government and defense sectors. CerenaKeeper focused on espionage through stealthy data exfiltration, while Stonefly utilized advanced techniques for long-term access. APT37, the North Korean group, continued its cyber-espionage campaigns, primarily aiming at critical infrastructure and sensitive data across various sectors.
|
Transparent Tribe |
The investigation of the infrastructure of the APT group Transparent Tribe (APT36) focuses on identifying its Command and Control (C2) servers. The inquiry was initiated after a Twitter post revealed two IPs linked to Transparent Tribe’s C2 servers. These IPs were found to be part of the Mythic C2 infrastructure, a cross-platform framework typically used for red teaming but also exploited by threat actors. Initial identification of 31,390 servers was narrowed down to 15 linked to ongoing attacks, primarily targeting India. APT36 is distributing malicious Linux files disguised as PDFs to deploy custom payloads like the Poseidon agent, aiming for persistent access. The group is focusing on Linux environments, particularly those used by Indian government sectors, such as BOSS OS and Maya OS. |
|
CerenaKeeper Threat Actor |
ESET researchers have identified a new China-aligned cyber threat actor named CeranaKeeper, which is targeting governmental institutions in Thailand. This group is known for constantly updating its backdoor tools to avoid detection and employs diverse methods to facilitate large-scale data exfiltration. Notably, CeranaKeeper abuses legitimate cloud and file-sharing services like Dropbox and OneDrive to deploy custom backdoors and extraction tools. Additionally, the group uses GitHub’s pull request and issue comment features to establish a covert reverse shell, utilizing the platform as a command-and-control (C&C) server. Some of the group’s tools have been previously linked to another actor, Mustang Panda. |
|
Stonefly Group |
Stonefly, is a financially motivated North Korean threat actor also known as Andariel, APT45, or Onyx Sleet. This group often targets U.S. organizations with the intent of financial gain rather than gathering intelligence. Recently, this group attempted intrusion on three U.S. private organizations but fortunately, the attacker failed to deploy ransomware. Stonefly leverages a backdoor called Preft aka Dtrack with capabilities for uploading and downloading files, executing commands, and installing various executables, VBScript, and BAT files. The group also employs the credential dumping tool Mimikatz alongside keyloggers to harvest sensitive data. |
|
SHROUDED#SLEEP Campaign |
The North Korean threat actor group APT37, also known as Reaper, RedEyes, or Ruby Sleet, has been observed deploying a new backdoor, VeilShell, in a campaign targeting Cambodia and potentially other Southeast Asian nations. This campaign, identified by the Securonix Threat Research Team as SHROUDED#SLEEP, begins with phishing emails containing a ZIP file that houses a malicious LNK file as the initial payload. The SHROUDED#SLEEP campaign utilizes a rare technique known as AppDomainManager hijacking, which helps to ensure persistence by injecting malicious code into the system. VeilShell, the backdoor deployed, offers a wide range of capabilities, including data exfiltration, registry manipulation, scheduled task creation, and full remote control of the compromised system. |
|
Iranian Cyber Group Targets Critical Sectors |
A joint advisory has been released by the FBI, CISA, NSA, CSE, AFP, and ACSC regarding an ongoing campaign attributed to an Iranian threat actor since 2023. These threat actors are targeting a wide range of critical sectors, including healthcare, government, IT, engineering, and energy. Their primary goal is to steal credentials and gather intelligence on victim networks. They are utilizing brute-force techniques, such as password spraying, and exploiting multi-factor authentication (MFA) methods, like push bombing (where MFA approval requests are sent repeatedly to users until they are accepted), to compromise user accounts and gain unauthorized access to organizational systems. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these threat actors.
- Deploy advanced endpoint detection and response (EDR) tools to monitor and block suspicious activity, particularly targeting malware such as CerenaKeeper and Stonefly.
- Isolate critical systems and sensitive data, limiting lateral movement for threat actors like APT37 and Transparent Tribe.
- Regularly update software and systems to address known vulnerabilities that these groups often exploit for initial access.
- Enforce MFA across all sensitive accounts to prevent unauthorized access, especially in high-value sectors like government and defense.
- 180 IoCs are available on our Threat Labs home page repository and have been swept for Autonomous Threat Sweeper customers.
TTPs related to the Transparent Tribe include but are not limited to the following:
- Monitor for ZIP file named “Document Details.zip”.
- Monitor for Linux desktop entry file “Document Details.pdf.desktop” which is distributed either through phishing emails or malicious websites.
TTPs related to the SHROUDED#SLEEP Campaign include but are not limited to the following:
- Monitor for high volumes of emails with attachments containing scripts or executable files.
- Monitor for suspicious .lnk files with unusual or double extensions (e.g., .xlsx.lnk, .pdf.lnk) and modified icons designed to mislead the user into thinking it’s a legitimate document.
- Track PowerShell executions (e.g., powershell.exe -EncodedCommand) and monitor for unusual script lengths, Base64 decoding, and data extraction from files.
- Monitor for unusual PowerShell command-line arguments or the use of non-standard PowerShell commands like Start-Sleep, Invoke-Expression, and encoded payload execution.
- Regularly check the Startup folder for unauthorized or unknown files (e.g., d.exe, DomainManager.dll`).
- Monitor for newly created scheduled tasks or unexpected task executions.
- Monitor for unusual modifications to .NET configuration files (e.g., d.exe.config) or AppDomainManager hijacking techniques.
TTPs related to the Iranian Cyber Group Targets Critical Sectors include but are not limited to the following:
- Monitor for tools or command-line activity that could indicate credential dumping, such as:
- Use of tools like Cmdkey /list to display usernames and credentials.
- PowerShell scripts designed to enumerate accounts (e.g., use of DomainPasswordSpray.ps1 or queries against Active Directory via LDAP).
- Suspicious execution of Kerberos enumeration tools or attempts to dump Kerberos tickets (e.g., Kerberos SPN enumeration).
Tags: Threat actor: Transparent Tribe,, Stonfly, APT37, CeranaKeeper | Malware: Preft backdoor, VeilShell | Tool: Mimikatz ,TONEINS, TONESHELL, and PUBLOAD | Target Location: U.S, India, Southeast Asia, Cambodia, Thailand | Target Sector: Healthcare, Government, IT, Engineering, Energy, Military Personnel, and Defense Contractors.
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh, Nikhil Kumar Chadha







