- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in July. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
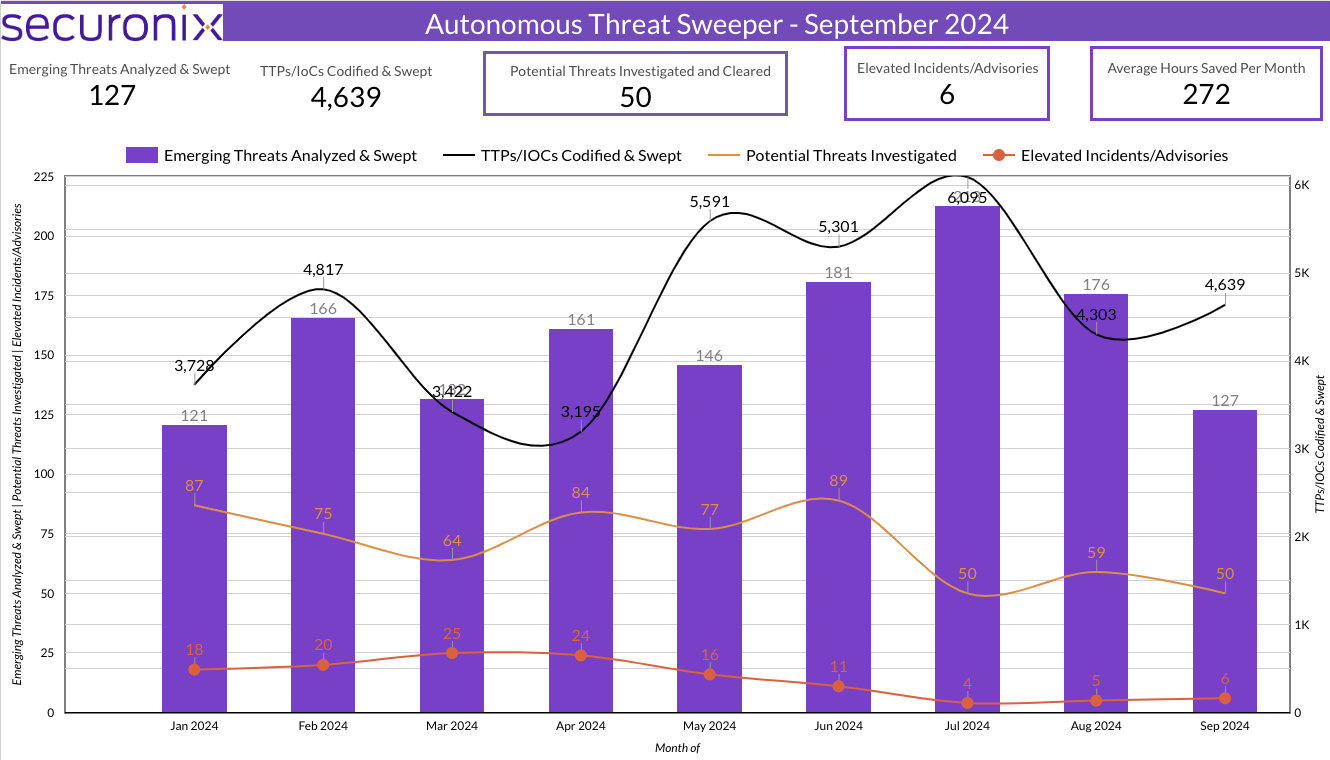
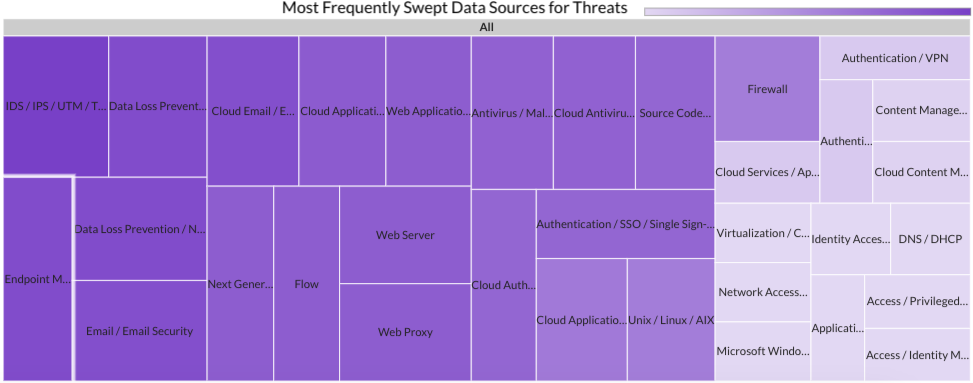
Last month Securonix Autonomous Threat Sweeper identified and analyzed 4,639 TTPs and IoCs, 127 emerging threats, investigated 50 potential threats, and elevated 6 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.


Lazarus group activity
In 2024, the Lazarus Group has intensified its cyber campaign, particularly targeting developers through financially motivated schemes. The campaign is exemplified by the “Contagious Interview” tactic, which lures job-seekers into downloading a compromised Node.js project containing BeaverTail malware. This malware, initially identified by PANW researchers as a JavaScript variant in late 2023, has since evolved to include a native macOS version discovered in July 2024.
In August 2024, Group-IB researchers uncovered a fraudulent Windows video conferencing app impersonating a legitimate application, later identified as another manifestation of BeaverTail. Further investigation revealed new malicious repositories on code-sharing platforms linked to Lazarus malware, including an updated Python version of BeaverTail that boasts enhanced capabilities.
The term “Lazarus” is often used to describe North Korean threat actors, specifically those operating under the Reconnaissance General Bureau (RGB) of the Korean People’s Army. It categorizes actors into six distinct groups: Alluring Pisces (Bluenoroff), Gleaming Pisces (Citrine Sleet), Jumpy Pisces (Andariel), Selective Pisces (TEMP.Hermit), Slow Pisces (TraderTraitor), and Sparkling Pisces (Kimsuky). Each group specializes in various cyber operations, including intelligence gathering, financial crime, and destructive attacks.
Notable operations linked to these groups include the 2014 Sony Pictures hack, the 2017 WannaCry ransomware attacks, and numerous attacks on cryptocurrency exchanges. These groups have been active since 2007 and have developed unique malware families targeting Windows, macOS, and Linux systems. The ongoing evolution of their tactics and tools highlights their significance in cybersecurity, particularly as they continue to support North Korean government objectives through espionage and geopolitical disruption.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threats.
- Be cautious when recruiters urge you to do tasks or download software, especially if they include executable files.
- Always ensure that the companies and recruiters conducting job interviews are legitimate and appropriately established.
- Be careful of links and attachments in unsolicited emails or communications purporting to be from recruiters or companies.
- Before accessing any files or applications, scan them with up-to-date antivirus and anti-malware software.
- 156 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Lazarus group include but are not limited to the following:
- Monitor for fake video conferencing application named FCCCall.
Tags: Threat Group: Lazarus | Malware: BeaverTail
EDRKillShifter disables EDR and antivirus
Trend Micro has identified a cybercriminal group known as Water Bakunawa, responsible for the RansomHub ransomware. This group employs advanced anti-EDR techniques, making it difficult for security solutions to detect their activities. RansomHub attacks exploit the Zerologon vulnerability (CVE-2020-1472) to gain unauthorized control of networks.
The ransomware has targeted various industries, including water and wastewater, IT, commercial and government services and facilities, healthcare, agriculture, financial services, manufacturing, transportation, and communications, often through spear-phishing attempts. Victims are threatened with the public release of compromised files unless ransom payments are made.
A significant feature of RansomHub is its affiliate model, along with the introduction of a new evasion tool called EDRKillShifter. This tool disrupts endpoint detection and response (EDR) solutions, ensuring persistent presence within compromised systems by exploiting vulnerable drivers and adapting to evolving detection methods.
Recently, the FBI reported that RansomHub has targeted 210 organizations across multiple sectors, highlighting the urgent need for organizations to adopt more robust security measures to counter these sophisticated attacks.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this threat activity.
- Enhance EDR Configurations: Regularly review and update EDR settings to ensure they are configured to detect and respond to suspicious activities, including attempts to disable EDR functionalities.
- Implement Layered Security: Utilize a multi-layered security approach that combines EDR with other protective measures, such as firewalls, intrusion detection systems, and advanced threat protection.
- Regular System Updates: Keep all systems and software up to date with the latest security patches to close vulnerabilities that ransomware might exploit.
- Incident Response Planning: Develop and regularly update an incident response plan that outlines steps to take in the event of a ransomware attack, including communication and recovery processes.
- Monitor for Anomalous Behavior: Set up monitoring systems to detect unusual activity that could indicate a ransomware attack in progress, such as unauthorized access attempts or unusual data encryption activities.
- 15 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the EDRKillShifter campaign include but are not limited to the following:
- Monitor for batch script files named “232.bat”, “tdsskiller.bat”, “killdeff.bat”, and “LogDel.bat”.
Tags: Ransomware: Ransomhub | Tool: EDRKillShifter | Threat Group: Water Bakunawa | Vulnerability: Zerologon vulnerability (CVE-2020-1472) | Target Sector: water and wastewater, IT, commercial and government services and facilities, healthcare, agriculture, financial services, manufacturing, transportation, and communications
Active ransomware activities
Head Mare is a hacktivist group active since 2023, targeting organizations in Russia and Belarus amid the Russo-Ukrainian conflict. They exploit vulnerabilities like CVE-2023-38831 in WinRAR to execute code and deliver malicious payloads. The group encrypts victims’ devices using LockBit and Babuk, demanding ransoms for decryption. Their toolkit includes the PhantomDL backdoor and PhantomCore remote access trojan. To disguise their activities, they create tasks and registry entries mimicking Microsoft processes, and they distribute malware through phishing campaigns featuring misleading file extensions. Head Mare also leaks sensitive information on X, focusing on sectors such as government, transportation, energy, manufacturing, and the environment.
Abyss Locker ransomware emerged as a critical threat in 2023, targeting industries such as finance, healthcare, manufacturing, and technology. Initially focused on Windows systems, it quickly expanded to Linux environments, particularly VMware ESXi. Known for its advanced encryption and multi-extortion tactics, Abyss Locker not only encrypts files but also exfiltrates sensitive data to force victims into paying ransom. The group employs sophisticated methods, including lateral movement and threats to expose data on a TOR-based site.
Truesec’s analysis suggests a strong connection between the Cicada3301 ransomware and ALPHV/BlackCat, potentially indicating a rebranding or fork by former ALPHV members. Both are written in Rust, use the ChaCha20 encryption algorithm, and share similar operational commands and ransom note decryption methods. This follows ALPHV’s exit scam in March 2024, where they claimed an FBI takedown after stealing $22 million. Additionally, Cicada3301 may collaborate with the Brutus botnet, linked to brute-force attacks on network appliances and observed shortly after ALPHV’s shutdown, further linking the two groups.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware campaigns.
- Implement Robust Cybersecurity Measures: Ensure comprehensive security protocols, including firewalls, intrusion detection systems, and endpoint protection, to safeguard against advanced threats like ransomware and hacktivist activities.
- Regularly Update and Patch Systems: Maintain up-to-date software and firmware to close vulnerabilities that attackers might exploit.
- Backup Data Regularly: Establish a routine for data backups and ensure that backups are stored securely and are easily recoverable in the event of an attack.
- Develop an Incident Response Plan: Prepare a clear plan for responding to security breaches, including communication strategies and recovery processes.
- Monitor Dark Web Activity: Stay informed about potential threats by monitoring the dark web for any leaks or mentions of your organization.
- 75 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Cicada3301 ransomware include but are not limited to the following:
- Monitor for ChaCha20 encryption.
- Monitor for filename “RECOVER-“ransomware extension”-DATA.txt”.
TTPs related to the Abyss Locker ransomware include but are not limited to the following:
- For Windows users:
- Monitor for salsa_20 encryption algorithm.
- Monitor for .abyss extension.
- Monitor for filename “WhatHappened.txt”.
- For Linux users:
- Monitor for .crypt extension.
- Monitor for directory “README_TO_RESTORE”.
Tags: Ransomware: Cicada3301, Abyss Locker, LockBit, Babuk | Malware: PhantomDL backdoor, PhantomCore | Vulnerability: CVE-2023-38831 | Target Sector: Government, Transportation, Energy, Manufacturing, Environment, Finance, Healthcare, and Technology | Target Location: United States, Germany, the United Kingdom, Sweden, Switzerland, Canada, Georgia, Italy, and Hong Kong
Activities of threat groups
The threat posed by Russian Military Cyber Actors, specifically GRU Unit 29155, is significant and multifaceted. These actors have been conducting sophisticated cyber operations against US and global critical infrastructure since at least 2020, with objectives including espionage, sabotage, and reputational harm. They have deployed destructive malware like WhisperGate against Ukrainian organizations and have targeted NATO members and other countries across various sectors. Their tactics include exploiting vulnerabilities in public-facing applications, using phishing-resistant multifactor authentication (MFA) to bypass security measures, and leveraging a range of publicly available tools for reconnaissance and lateral movement within networks. The threat actors are also known for their ability to obfuscate their activities, making detection and attribution more challenging.
The cyber espionage group UNC2970, suspected to have a North Korea nexus, has been actively engaging in a sophisticated backdoor deployment campaign using a trojanized PDF reader. By masquerading as legitimate job recruiters for prominent companies, UNC2970 targets senior-level employees in U.S. critical infrastructure sectors with the intent of gaining access to sensitive and confidential information. The group employs a multi-stage infection chain that begins with a phishing lure delivered as a password-protected ZIP archive containing an encrypted PDF and a modified version of the SumatraPDF viewer. Once the victim opens the PDF with the trojanized viewer, the MISTPEN backdoor is deployed via the BURNBOOK launcher, establishing persistence and command-and-control communication.
UNC1860 is an Iranian state-sponsored threat actor, likely affiliated with Iran’s Ministry of Intelligence and Security (MOIS), known for its persistent and opportunistic cyber operations across the Middle East. Specializing in the collection of specialized tooling and passive backdoors, UNC1860 has been identified as a probable initial access provider, adept at gaining persistent access to high-priority networks, particularly in the government and telecommunications sectors. Their tradecraft includes the use of GUI-operated malware controllers, such as TEMPLEPLAY and VIROGREEN, and passive backdoors repurposed from legitimate software, like an Iranian anti-virus filter driver, to evade detection. UNC1860’s activities align with other Iran-based threat actors, such as Shrouded Snooper and Scarred Manticore, and are indicative of Iran’s broader strategy to leverage cyber capabilities for espionage and potentially disruptive operations within the region.
The FBI, U.S. Cyber Command, Department of the Treasury, and the UK’s NCSC have issued a joint Cybersecurity Advisory regarding ongoing cyber activities by the Iranian Government’s Islamic Revolutionary Guard Corps (IRGC). These threat actors are targeting individuals involved in Iranian and Middle Eastern affairs, including government officials, journalists, and political campaign personnel. They employ social engineering tactics, such as impersonating contacts and email service providers, to gain access to victims’ accounts and sensitive information.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these threat actors.
- User Education and Awareness: Regularly train users on recognizing phishing attempts and other social engineering tactics. Encourage vigilance when opening emails or attachments from unknown sources.
- Software Updates and Patch Management: Ensure all systems and software are up-to-date with the latest security patches to mitigate vulnerabilities.
- Endpoint Protection: Implement robust antivirus and anti-malware solutions on all devices. Utilize behavior-based detection methods to identify and block threats.
- Network Security Measures: Employ firewalls, intrusion detection/prevention systems, and segmentation to protect sensitive data and limit the potential impact of breaches.
- Access Control: Enforce strict access controls based on the principle of least privilege. Regularly review user permissions and promptly revoke access for former employees.
- Multi-Factor Authentication (MFA): Implement MFA for critical systems and accounts to add an additional layer of security against unauthorized access.
- 176 IoCs are available on our Threat Labs home page repository and have been swept for Autonomous Threat Sweeper customers.
Tags: Threat actor: GRU Unit 29155, UNC2970, UNC1860, Shrouded Snooper, Scarred Manticore, Storm-0861 | Malware: WhisperGate, MISTPEN backdoor | Tool: BURNBOOK launcher | Target Location: North Atlantic Treaty Organization (NATO) in Europe and North America, as well as countries in Europe, Latin America, Central Asia, Middle East | Target Sector: Telecommunications, Government
Attacks against government entities
The China-linked advanced persistent threat (APT) group known as Stately Taurus has been observed using Visual Studio Code as a tool in espionage operations targeting Southeast Asian government entities. This group is exploiting the embedded reverse shell feature in Visual Studio Code, a technique first highlighted in September 2023. The recent campaign appears to continue a previous attack on an unnamed Southeast Asian government. By utilizing either the portable version of Visual Studio Code or an installed version, attackers can execute the command `code.exe tunnel` to gain access to a web environment linked to the infected machine, allowing them to run commands and deliver additional malware. The group is reported to have used OpenSSH for executing commands, transferring files, and moving laterally within the network.
Iraqi government networks have recently been targeted in an extensive cyber attack campaign by the Iranian state-sponsored group known as OilRig (also referred to as APT34 and several other names). This campaign specifically focused on key Iraqi organizations, including the Prime Minister’s Office and the Ministry of Foreign Affairs. Active since at least 2014, OilRig has a history of using phishing techniques to deploy custom backdoors for information theft. The latest campaign introduces new malware families named Veaty and Spearal, which can execute PowerShell commands and harvest files. Unique command-and-control (C2) mechanisms are employed, including a custom DNS tunneling protocol and compromised email accounts for issuing commands and exfiltrating data.
Additionally, a new HTTP-based backdoor called CacheHttp.dll targets Microsoft IIS servers, allowing for command execution based on incoming web requests. This backdoor is an evolution of previous malware associated with APT34 and is designed for advanced command execution and file manipulation.
Since June 2023, the threat actor known as Tropic Trooper has targeted unnamed government entities in the Middle East and Malaysia with a persistent cyber campaign. This group, also referred to as APT23, Earth Centaur, KeyBoy, and Pirate Panda, has historically focused on sectors like government and healthcare in Taiwan, Hong Kong, and the Philippines. The campaign was identified in June 2024, noting the use of a new version of the China Chopper web shell on an open-source Umbraco CMS. The attack aimed to deploy the Crowdoor malware, a variant of the SparrowDoor backdoor, but ultimately failed. The operation involved exploiting vulnerabilities in widely used web applications, including Adobe ColdFusion and Microsoft Exchange Server.
The use of the China Chopper web shell as a .NET module and the subsequent deployment of tools for network scanning and lateral movement underscores a strategic shift in Tropic Trooper’s tactics. Upon detection of their backdoors, the group attempted to upload new samples to avoid further detection, indicating a heightened risk of future intrusions.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these threat actors.
- Regular Security Audits: Conduct thorough security assessments to identify vulnerabilities in government networks.
- Employee Training: Implement regular training sessions on recognizing phishing attempts and other social engineering tactics.
- Network Segmentation: Isolate sensitive systems and data to limit the impact of a potential breach.
- Code Analysis Tools: Use static and dynamic analysis tools to inspect code for vulnerabilities, especially in development environments like VSCode.
- Regular Updates: Keep all software, including development tools, up to date to protect against known vulnerabilities.
- Input Validation: Ensure rigorous input validation and sanitization in web applications to prevent code injection attacks.
- 48 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to this Stately Taurus include but are not limited to the following:
- Monitor for batch script files named startcode.bat and Listeners.bat.
- Monitor for filename win1.exe.
- Monitor for DLL sideloading to load the ShadowPad module (imjp14k.dll).
TTPs related to this OilRig include but are not limited to the following:
- Monitor for filenames Avamer.pdf.exe, Protocol.pdf.exe, IraqiDoc.docx.rar.
Tags: Backdoor: ToneShell, ShadowPad, Passive IIS backdoor, CacheHttp.dll, Crowdoor, SparrowDoor, Veaty, Spearal | Target Sector: Government | Affected Product: Visual Studio Code, content management platform | Affected Region: Southeast Asia, Iraq, Middle East.
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh, Nikhil Kumar Chadha







