- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov, Securonix Threat Research Team
On September 7, 2017, we learned of a massive cyber attack/data breach targeting Equifax. Securonix Threat Research Team has been actively investigating the details of the attack to help our customers detect/mitigate/respond to such attacks.
Here is a summary of what we currently know and our recommendations on some possible Securonix predictive indicators/security analytics that can be used to detect the current and potential future attack variants (there will be updated indicators/security analytics as we receive more information.)
Update 9/14/2017: Equifax has now officially confirmed that the attack vector we described in our original post from 9/8/2017 (Apache Struts Jakarta Multipart Parser Vulnerability – CVE-2017-5638) is indeed the attack vector that was used in this high-profile cyber attack / data breach [8]. We’ve reproduced this real-world attack in practice in our lab and were able to successfully detect the attack using Securonix (see below).
*** If you are not currently collecting/analyzing your Apache Tomcat logs, we strongly recommend that you start collecting the logs and using them in your analysis to ensure that you are able to detect the latest attacks.

Figure 1: Equifax Cyber Attack In Action
- Impact: Here are some of the key details that are currently known regarding the impact of this massive cyber attack/data breach [4]:
- Personally identifiable information (PII) of 145.5 million of US consumers was exposed as part of this attack;
- Credit card data for 209k of US consumer was exposed as part of this attack;
- Consumer dispute documents for 182k of US consumers were exposed to attackers as part of this attack;
- Infiltration vector(s): According to Equifax, the primary attack vector used is the Apache Struts Jakarta Multipart Parser Vulnerability (CVE-2017-5638).
Introduction – Equifax Website
The Equifax Website appears to be leveraging Java/IBM WebSphere/Apache Struts/MyFaces/JavaServer Faces (JSF) components. As can be seen from Figure 2 [1] (the details on the page are available through Google without the need to access the Equifax website directly), the details also indicate a potential information disclosure vulnerability of the current Equifax web server (as of 9/8/2017)).
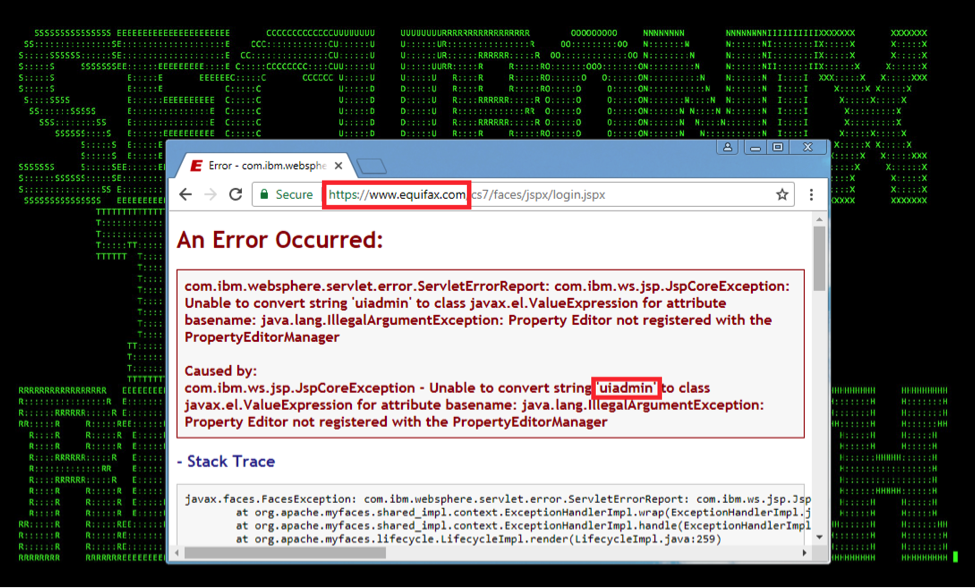
Figure 2: Equifax Web Site Potential Information Disclosure Vulnerability
Equifax Cyber Attack/Data Breach – Infiltration Vector
As mentioned above, as of 9/13/2017, Equifax confirmed that the Apache Struts Jakarta Multipart Parser Vulnerability – CVE-2017-5638 attack vector described in our original post from 9/8/2017 is indeed the attack vector that was used in this high-profile cyber attack / data breach [8].
We’ve reproduced the actual real-world attack used to exploit Equifax in practice based on the publicly available details.
The attack in action is shown in Figure 1. Here is what you might see in your logs when in case an attack similar to the one used against Equifax is used against your organization (Figure 3):
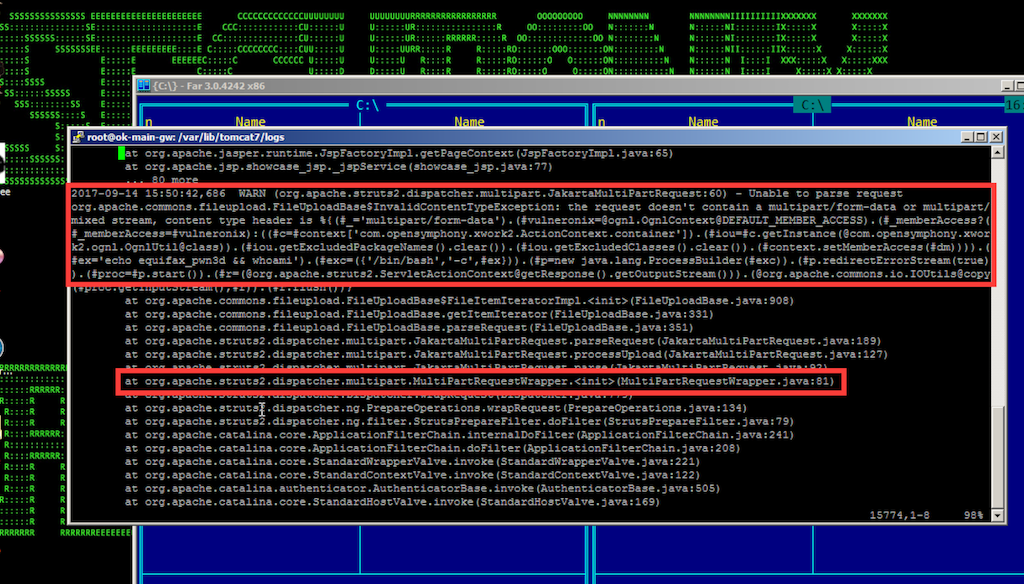
Figure 3: Equifax Cyber Attack in the logs
As can be seen from the Figure above, the attack generates a WARN and it is not immediately obvious even to an experienced security analyst that you may be under an attack, particularly given the amount of logs that needs to be analyzed and the nature of the attack.
Also, it should quite easy for attackers to evade many signature/rule-based detection approaches because of the nature of the vulnerability by simply changing the OGNL payload.
This is why it is critical to be able to leverage machine learning/behavior analytics as part of your security defense-in-depth approach to increase chances of detecting such cyber attacks.
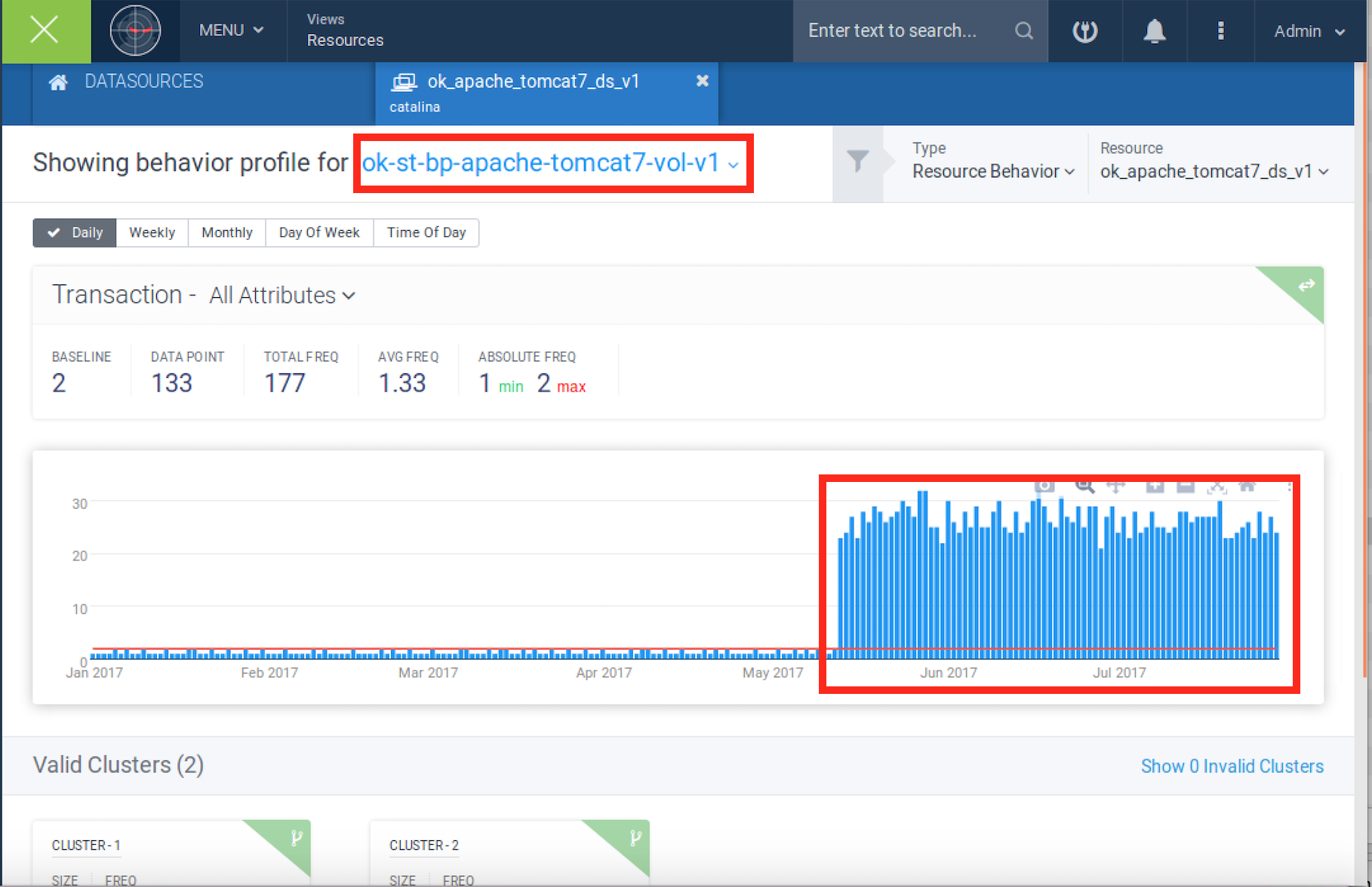
Figure 4: Equifax Cyber Attack – Practical Detection by Securonix – Behavior Profile Example
Mitigation – Securonix Recommendations
- Upgrade to the latest patched version of Struts e.g. Struts 2.5.13+ ASAP;
- Implement a Servlet filter which will validate Content-Type and throw away requests with suspicious values not matching multipart/form-data;
- Change to an alternative multipart parser component e.g. Commons-File Upload, Pell etc.
- Monitor your Apache Tomcat logs, customize logging to enable remote IP address logging in log4j config e.g. AccessLog/RemoteIP valves etc.
Detection – Securonix Behavior Analytics/Security Analytics
1.1 Recommended Data Sources
- #1 – EDR – Endpoint Logs (Sysmon, Bit9/Carbonblack etc);
- #2 – WEB – Web Server Logs (Apache Tomcat etc);
- #3 – EFL – External Firewall Logs (Palo Alto etc);
- #4 – PXY – Proxy/Reverse Log (Squid, Bluecoat etc).
1.2. Some Examples of Relevant High-Level Behavior Analytics/Predictive Indicators
Here are some of the high-level examples of the relevant Securonix predictive indicators to increase the chances of early detection of the malicious activity associated with the Equifax cyber attack and potentially other future variants of attacks carried out by the malicious threat actor(s) involved.
#1 – Suspicious Process/Service Activity Anomalies
- Suspicious Process Activity Rare Process/MD5 For User/Host Anomaly
- Suspicious Process Activity Unusual Parent-Child Relationship For User/Host Anomaly
- Suspicious Process Network Activity Unusual App Destination Port Anomaly
#2 – Suspicious Web Server Tomcat Access Anomalies
- Suspicious Tomcat Activity Unusual Warning Increase For Adapter Anomaly
- Suspicious Tomcat Activity Unusual Warning For Adapter Anomaly
- Suspicious Tomcat Activity Unusual Servlet Exception Anomaly
- Suspicious Tomcat Activity Unusual Web App Deployment Directory/Potential Webshell Anomaly
#3 – Suspicious Network Activity Anomalies
- Suspicious Network Activity Unusual Outbound Traffic Volume Anomaly
- Suspicious Network Activity Traffic to Rare Domains Anomaly
- Suspicious Network Activity HTTP Server Unusual Endpoint Access Anomaly
The detection of this high-profile cyber attack in action using Securonix is shown in Figures 4 and 5.
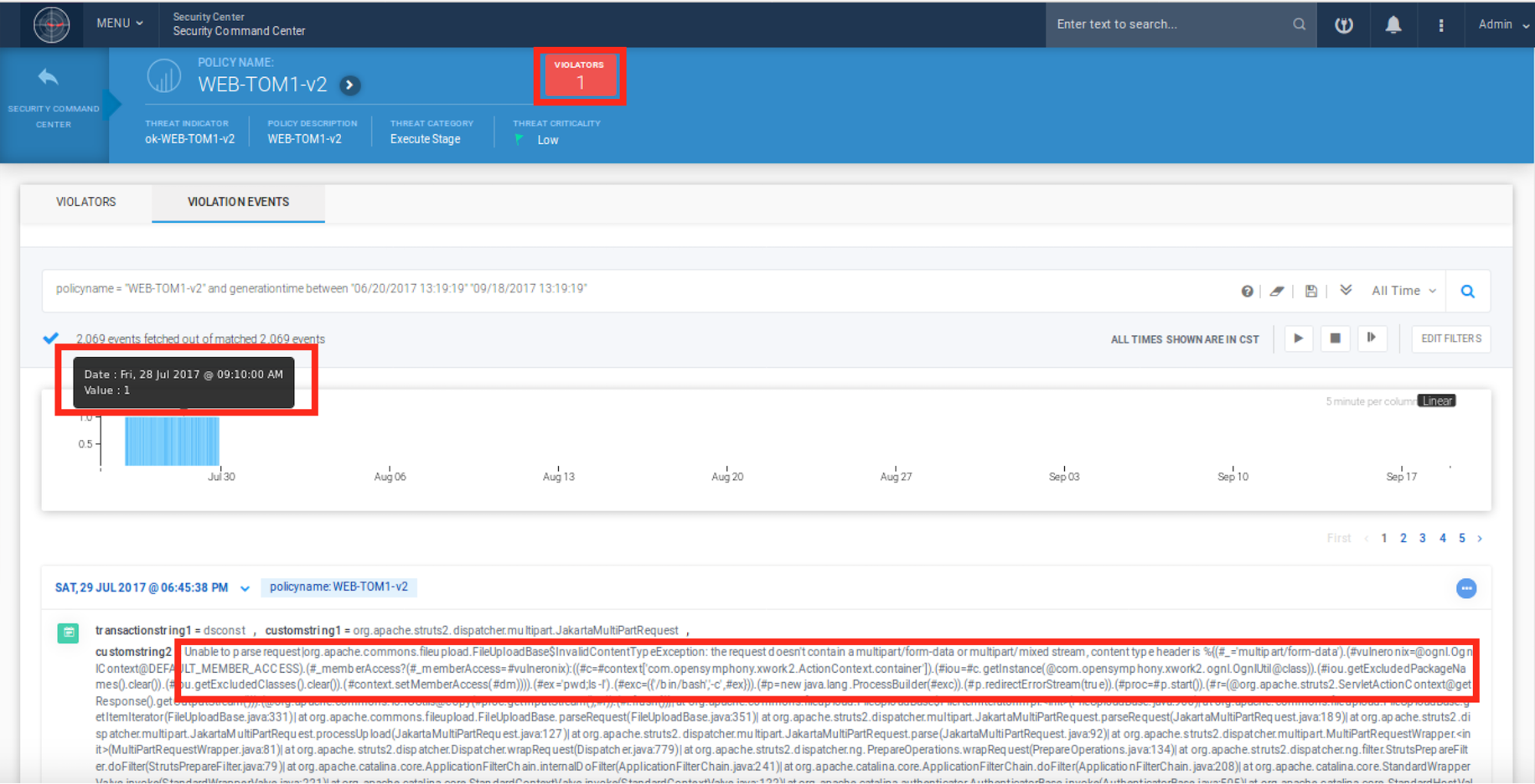
Figure 5: Equifax Cyber Attack – Practical Detection by Securonix
References
[1] Notdan@Twitter. Cmon Equifax. You have ALL OF OUR INFO. 8 September 2017. https://twitter.com/notdan/status/905914760398376961. Last accessed: 09-08-2017.
[2] Apache Myfaces Core JIRA. Security Issue: includeViewParameters re-evaluates param/model values as EL expressions. 22 November 2011. https://issues.apache.org/jira/browse/MYFACES-3405. Last accessed: 09-08-2017.
[3] Apache Myfaces Core JIRA. Security Issue: Issue with some JSF Artifacts eligible for injection. 8 September 2017. https://issues.apache.org/jira/browse/MYFACES-4138. Last accessed: 09-08-2017.
[4] Matthew Schwartz. Equifax Breach: 8 Takeaways. 8 September 2017. https://www.bankinfosecurity.com/equifax-breach-8-takeaways-a-10278. Last accessed: 09-08-2017.
[5] Warlop. Apache Struts 2.5 < 2.5.12 – REST Plugin XStream Remote Code Execution Exploit. 6 September 2017. https://www.exploit-db.com/exploits/42627/. Last accessed: 09-08-2017.
[6] nixawk–Rapid7–Metasploit. CVE-2017-5638 – Apache Struts2 S2-045 Exploit. 7 March 2017. https://github.com/rapid7/metasploit-framework/issues/8064. Last accessed: 09-08-2017.
[7] Baird Equity Research. Equifax Data Breach. 7 September 2017. https://baird.bluematrix.com/docs/pdf/dbf801ef-f20e-4d6f-91c1-88e55503ecb0.pdf. Last accessed: 09-13-2017.
[8] Equifax. Cybersecurity Incident & Important Consumer Information. 14 September 2017. https://www.equifaxsecurity2017.com. Last accessed: 09-14-2017.
[9] Immunio. Apache Struts 2 Vulnerability Exploits. https://github.com/immunio/apache-struts2-CVE-2017-5638. Last accessed: 09-14-2017.