- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov, Securonix Threat Research Team
Introduction
On June 27, 2017, The Securonix Threat Research team learned of a new large-scale ransomware cyber attack involving the PetrWrap aka GoldenEye aka Nyetya malicious implant instance. We have been actively investigating and closely monitoring this high-profile attack since the attack was launched earlier today to help our customers prevent, detect, and mitigate/respond to the attack.
Here is a work-in-progress summary of what we currently know and our recommendations on possible mitigations and Securonix predictive indicators that can be used to detect this and potentially future variants of this attack.
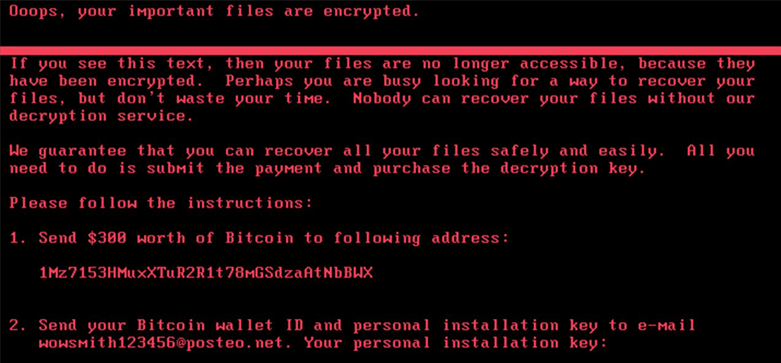
Figure 1: PetrWrap/GoldenEye/Netya Ransomware Prompt
Summary
Here is a summary of some of the key details about this ransomware attack.
Infiltration vector(s): According to the publicly available details, the attack started in Ukraine with patient zero most likely infected through a popular Ukrainian tax accounting software called MeDoc. There are also some preliminary reports of a precursor e-mail campaign for this attack that involved malicious DOC and PDF attachments. Following the initial infection, an initial stager payload was installed, a second-stage payload was then downloaded, and subsequent targets were then infected using an attack vector similar to the WannaCry/WannaCrypt0r high-profile ransomeware from last month, namely Microsoft SMBv1 Remote Code Execution Vulnerability (CVE-2017-0144, CVE-2017-0199,MS17-010) aka EternalBlue or the lateral movement vectors mentioned below. The Eternalblue attack vector involves the SMB ports tcp/139 and tcp/445. In additon, there is one more port associated with the lateral movement vectors below, namely tcp/135.
Lateral Movement: In contrast to WannaCry/WannaCrypt0r, besides the EternalBlue attack vector, the PetrWrap ransomware attack also leverages administrative shares as well as WMI and PSEXEC-based lateral movement atomic attack behaviors (A2Bs) to execute the malicious payload DLL (c:\Windows\perfc.dat) using rundll32 and/or wmic.
Impact: According to some reports, in addition to the targets that were impacted by the original MS17-010 vulnerability (unpatched Windows 7, Server 2008 and earlier systems, including Windows XP, 2003, and Vista), this attack was seen to successfully infect fully-patched Windows 10 systems (this is to be confirmed).
Patches: Based on the publicly available details, the available patches can help mitigate this attack, namely the MS17-010 patch for supported Microsoft platforms that has been available since April, 2017 (see https://technet.microsoft.com/en-us/library/security/ms17-010.aspx); In addition, Microsoft released a KB4012598 patch for Microsoft platforms in custom support such as XP, 2003 (see https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/);
Observed Artifact Hash Values:
027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
4ee2ae805c31ec4f11f3f6ecf56e9c6e2f59dcd517a5a73210b5e5015f63beea
b5ef16922e2c76b09edd71471dd837e89811c5e658406a8495c1364d0d9dc690
17dacedb6f0379a65160d73c0ae3aa1f03465ae75cb6ae754c7dcb3017af1fbd
02ef73bd2458627ed7b397ec26ee2de2e92c71a0e7588f78734761d8edbdcd9f
71b6a493388e7d0b40c83ce903bc6b04
e8fb95ebb7e0db4c68a32947a74b5ff9
da2b0b17905e8afae0eaca35e831be9e
Behaviors
Propagation
As mentioned, the attack can leverage three different propagation vectors, namely an exploit targeting the Microsoft SMBv1 Remote Code Execution Vulnerability for remote code execution, PSEXEC, or WMI. No user action is required for a system to get infected. The exploit works over the tcp/139 and tcp/445 ports. Once a target gets infected, the system attempts to infect other systems via locally connected interfaces.
The Eternalblue-based propagation is performed by connecting to internal/external targets using SMB Trans2 and attempting a transaction on FID 0, checking if the status returned is STATUS_INSUFF_SERVER_RESOURCES, and also checking for the “Multiplex ID” to be set to (0x51) to identify and reuse potential DOUBLEPULSAR backdoor infections to install a malicious payload. The result of the steps above is a likely increase in the volume of the SMBv1 activity from your internal hosts.
“Kill Switch”?
In contrast to the WannaCry/WannaCrypt0r, this attack does not implement a “kill switch.”
However, it may be possible to vaccinate your systems against the specific malicious implant variant that was involved in the attack on 6/27/17 by proactively creating the files used by malicious implant (requires administrative privileges) i.e.
attrib +R C:\Windows\perfc
attrib +R C:\Windows\perfc.dll
attrib +R C:\Windows\perfc.dat
(see https://download.bleepingcomputer.com/bats/nopetyavac.bat for further details);
Host Activity
– Master Boot Record (MBR) Overwrite
The malicious implant attempts to overwrite MBR (PhysicalDrive0) and adds a scheduled task to reboot the infected target one hour after the overwrite. It is critical NOT to reboot the computer since the reboot will cause the new MBR to be loaded, which will then cause the files on the infected target to be encrypted (the files are not encrypted until the reboot happens).
– Covering Tracks – Windows Event Log Clearing
To cover its tracks, the malicious implant clears the Windows Event Logs on the target using wevtutil cl Setup & wevtutil cl System & wevtutil cl Security & wevtutil cl Application
– Covering Tracks – USN Change Journal Clearing
To further cover its tracks, the malicious implant uses fsutil.exe to delete the update sequence number (USN) change journal, which provides a log of all changes made to files on the volume (C:).
– Required Token Privilege Adjustment
The malicious implant leverages the WinAPI AdjustTokenPrivileges requesting SeShutdownPrivilege and SeDebugPrivilege.
Some of the commands ran by malicious implant on the target include:
The commands can be used in the Securonix Rule-based policies leveraging ETDR log sources/data sources (see below).
Command and Control etc.
– There are reports of an DOC-based infection vector that was used by the malicious implant involving a malicious DOC/XLS attachment downloads viz. Order-20062017.doc from the following sites (you can remove the extra dot):
french-cooking..com
coffeeinoffice.xyz
followed by a second stage download of an MSHTA payload:
myguy.xls
The payload is then saved to C:\myguy.xls.hta & mshta.exe is executed on the payload
– The staging/C2 IP addresses likely associated with this attack are as follows (consider TI/lookup blocking in Securonix, you can remove the extra dot):
84.200.16..242
95.141.11..108
111.90.139..247
Mitigation & Prevention – Checking for Vulnerable Systems
Many of the mitigation steps for this attack are similar to the mitigation and prevention steps for WannaCry/WannaCrypt0r we provided earlier. In particular, as part of the recommended mitigation, it may be necessary to detect internal systems that are vulnerable to this attack.
In order to find out if any of the Windows systems are vulnerable, you can run the MS17-010_SUBNET python script from https://github.com/topranks/MS17-010_SUBNET as follows:
$ ./smb_ms17_010.py 10.7.1.0/24
You can also check for some possible targets for the PSEXEC-based lateral movement or WMI-based lateral movement of the attack by using a trivial scan e.g.
# nmap -sS -O -p139,445 10.7.1.0/24
Note: It is important NOT to reboot the target since the encryption of the files on the target begins after the malicious MBR bootloader starts running after the reboot.
Mitigation & Prevention – Securonix Recommendations
Here are some of the Securonix recommendations to help customers prevent and/or mitigate the attack propagation:
- If SMBv1 is not required for BAU, reference these recommendations to disable on all internal systems as soon as possible: https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
- Block tcp/139, tcp/445, and tcp/1024-1035 for ingress from the Internet, partners etc as soon as possible;
- Patch all impacted Windows systems as soon as possible using the MS17-010 Microsoft Tuesday bulletin: https://technet.microsoft.com/library/security/MS17-010
- Consider restricting WMI & administrative share access in your environment as much as possible.
- Consider patching your Microsoft Office as required using the following patch https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0199.
Detection – Examples of Securonix Predictive Indicators
Here is a summary of some of the possible Securonix predictive indicators to increase the chances of early detection of this and potentially other future variants of this attack on your network:
1 – Suspicious Process/Service Activity Anomalies (ETDR logs)
- Rare Process Compared to Past Behavior (Event Rarity, Process Hash, Process Name)
- Rare Service Creation Compared to Past Behavior (Event Rarity, Service Name)
- Process Execution From Previously Unseen File Paths (Event Rarity, Process Name, Execution Path)
- Malicious Process Execution (Threat Intel Policy)
- Suspicious System Activity Log Clearing Anomaly (Targeted e.g. 1102)
- Suspicious Source IPC Share Access Anomaly (Rare,5145)
- Suspicious Source Administrative Share Access Anomaly (Rare)
- Unusual Privilege Set Assignment For User Anomaly (Rare)
2 – Suspicious Network Activity Anomalies (Firewall, Netflow)
- Unusual Source for SMBv1 Request Anomaly (Rare)
If you have any further questions regarding this high-profile threat and how Securonix can be leveraged to detect the behaviors associated with the threat, please do not hesitate to contact Aditya at [email protected] or Oleg at [email protected].
References
[1] Alexander Chiu. New Ransomware Variant “Nyetya” Compromises Systems Worldwide. Talos Intelligence Blog. 27 June 2017.
[2] Sheera Frenkel. Global Cyberattack: What We Know and Don’t Know. New York Times. 27 June 2017.
[3] Global Ransomware Attack Causes Turmoil. BBC News. 27 June 2017.
[4] Catalin Cimpanu. Vaccine, not Killswitch, Found for Petya (NotPetya) Ransomware Outbreak. Bleeping Computer. 28 June 2017.