- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov, Securonix Threat Research Team
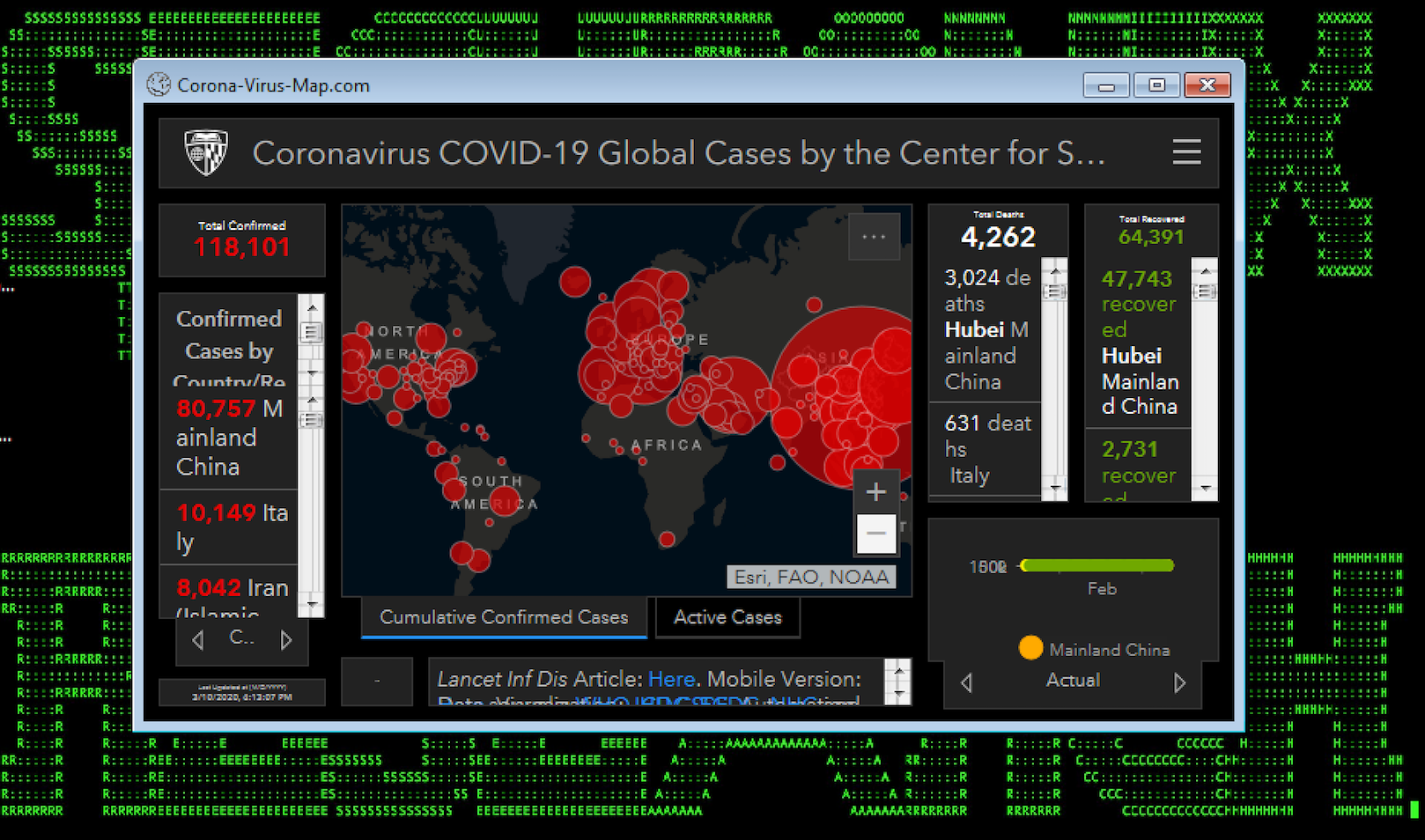
Figure 1: Malware Exploiting Live Coronavirus Map
In recent weeks, as many businesses have been rushing to institute a shift to remote work due to the COVID-19/coronavirus situation, we have been observing malicious threat actors attempting to exploit an increasing number of the associated cyberattack vectors, including:
- Ransomware using weaponized COVID-19/coronavirus-related documents, disrupting critical healthcare and other businesses’ operations.
- Custom COVID-19-themed phishing attacks involving malicious documents to steal remote workforce credentials and infiltrate various organizations.
- Malware using fake live coronavirus maps/tailored monitoring applications for malicious purposes, such as hardware router/DNS hijackers changing IN A records.
- Malicious and trojaned applications/.apks related to coronavirus exploiting remote workforce’s BYOD/Android devices.
- Attacks exploiting remote access/VPN servers, taking advantage of the worldwide increase in the number of remote users [1, 2, 4, 5, 6, 10].
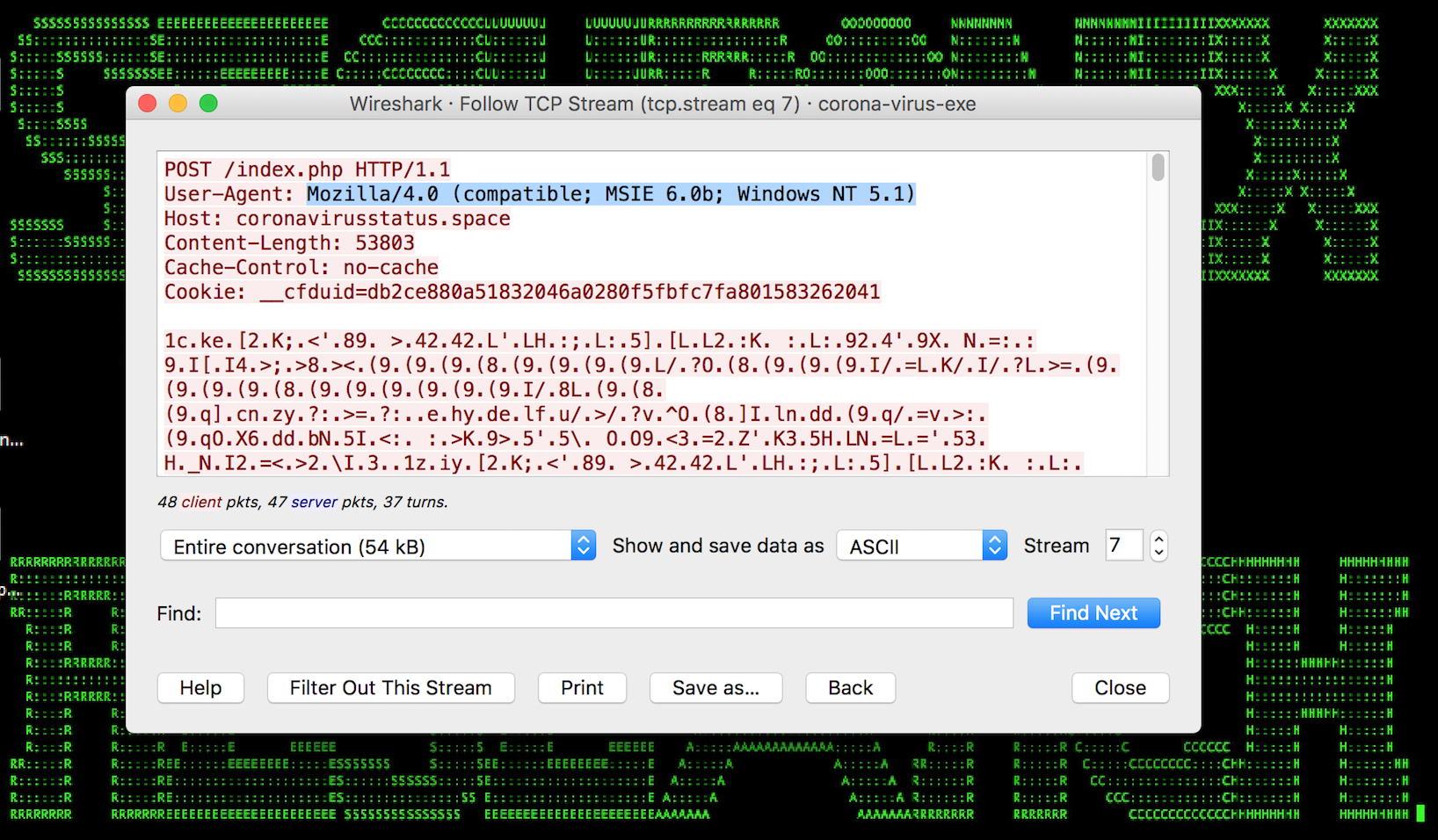
Figure 2: Malware Exploiting Live Coronavirus Map – C2
The Securonix Threat Research Team has been actively investigating and closely monitoring cyberattacks and the current remote workforce/WFH shift to help businesses improve the security of their remote users and help increase the chances of detecting the current and the future critical cyberattacks early in order to minimize possible disruptions to core business operations.
Below is a summary the relevant details with our recommendations to help with remote workforce/WFH monitoring, including some details about the cyberattacks observed as well as examples of some of the key log/data sources and priority use cases, including VPN, 2FA/MFA, and cloud and software-as-a-service (SaaS) applications used by your remote workforce.

Figure 3: COVID-19/Coronavirus-Themed Weaponized Word Document Ransomware
Summary
1.1 What parts of your organization might these recommendations be helpful for?
Security operations/SOC, IT operations, insider threat teams, and human resources.
1.2 What are the details of some of the relevant cyberattacks observed by Securonix Threat Research in the wild?
In addition to the malicious COVID-19 live map app identified earlier (see Figures 1 and 2), some additional cyberattack examples observed recently include:
Example #1: COVID-19/Coronavirus-Themed Weaponized Word Document Ransomware
This ransomware appears to be a variant of SNSLocker, and is pushed through a malicious COVID-19 situation report (sitrep) email (see Figure 3).
Once a user opens the document, this is immediately followed by the sensitive data being encrypted by the ransomware (see Figure 4).
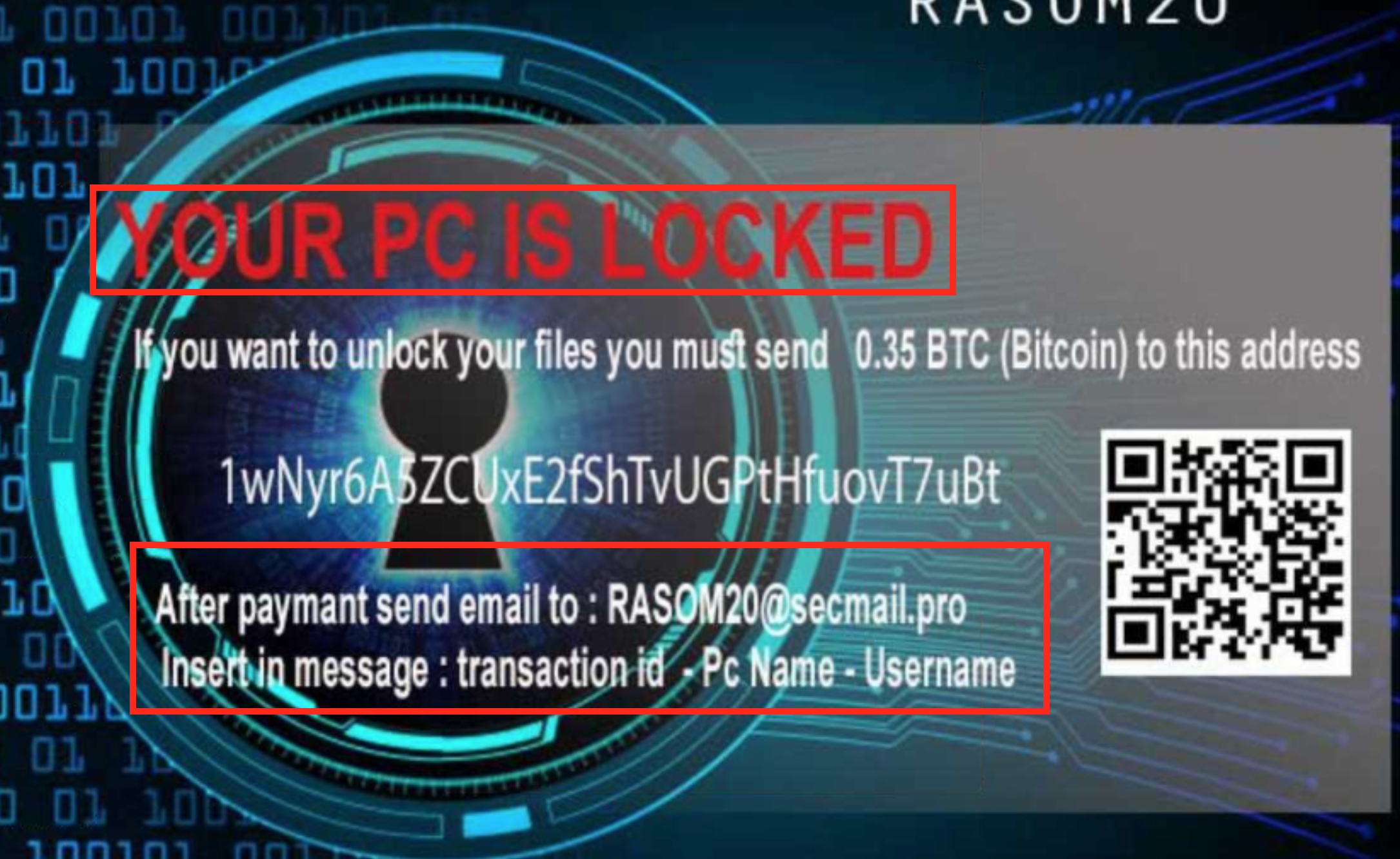
Figure 4: COVID-19/Coronavirus-Themed Weaponized Word Document Ransomware – Encrypted Desktop
Example #2: COVID-19/Coronavirus-Themed Malicious Credential Stealer
The malicious implant is pushed through different types of emails, including a fake COVID-19 infection notification email (see Figure 5) and a COVID-19 relief email.
The implant then downloads a second stage malware (different variants possible) with some of the logs observed shown in Figure 6.
The downloaded stagers attempt to perform further malicious actions, including:
- Stealing web browser cookies, enumerate system information and shares
- Stealing cryptocurrency wallets
- Exfiltrating stolen information
- And more
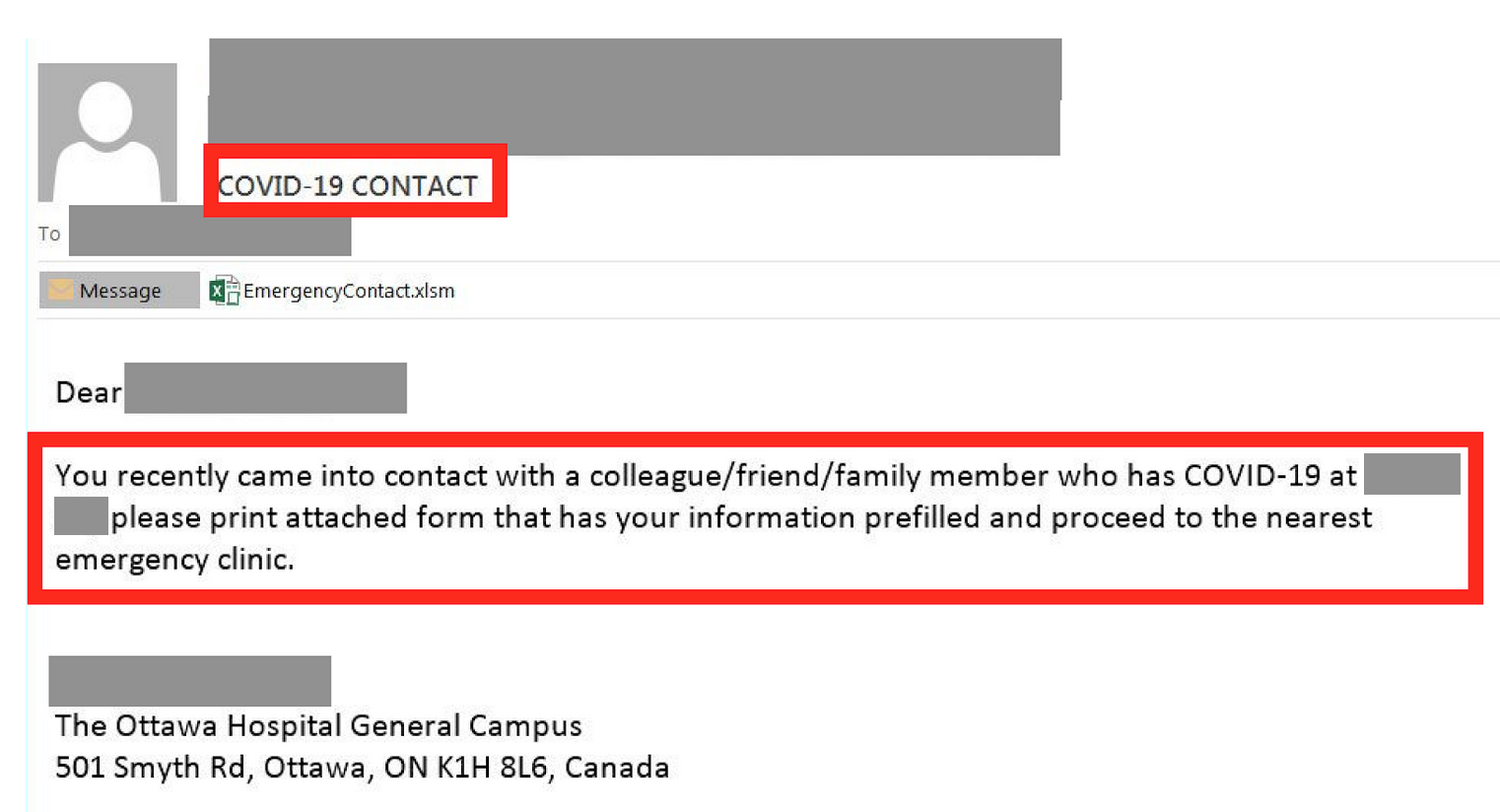
Figure 5: Fake COVID-19 Infection Phishing Email
1.2 What are some of the recommended log/data sources to monitor in order to increase the chances of detecting these and other relevant cyberattack variants as part of remote workforce/WFH monitoring?
Some of the relevant log/data sources we recommend include:
- VPN server logs (Examples: Pulse Secure*, Cisco, Citrix, PAN, and others, including *crashes, system, and software* severity levels/VPN logs).
Note: In order to enable the proper visibility, consider reviewing your VPN policies to ensure split-tunneling is disabled as it may impact visibility.
- Cloud application/software-as-a-service (SaaS) logs used by your remote workforce/WFH users (Examples: Office 365*, Box, and others).
- Single-sign-on (SSO) and 2FA/MFA logs (Examples: Duo, Okta, and others).
- EDR/Remote workstation logs, email gateway logs, CASB, and other logs (see further details below).
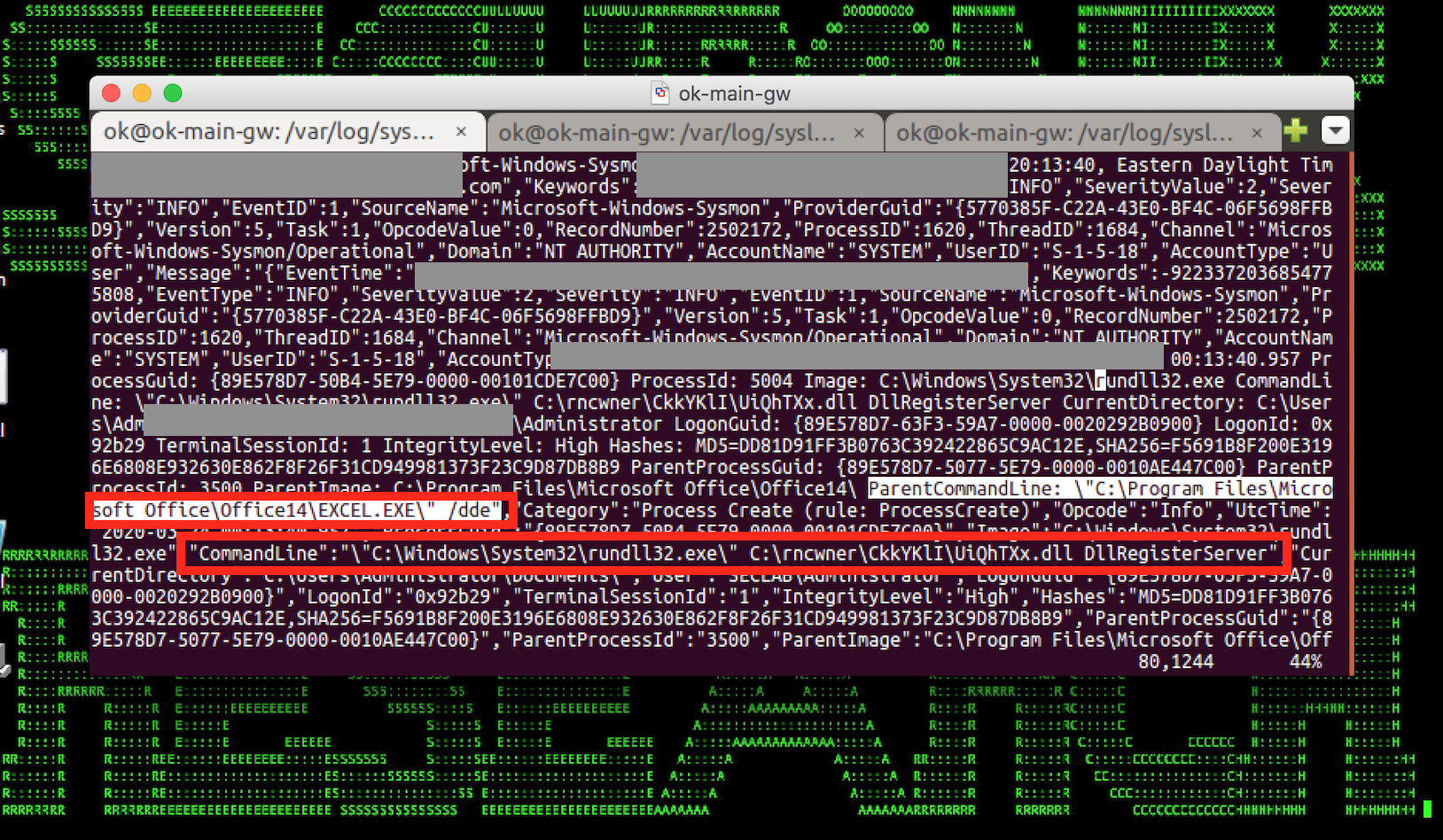
Figure 6: Fake COVID-19 Infection Phishing Email – Initial Weaponized doc Exploit Loading a Malicious dll
1.3 What are some of the priority use cases recommended?
Some of the priority relevant use cases recommended (high-level) include:
- Unusual severity event for your VPN server device
- Account authentication from a rare geolocation
- VPN connection from anonymous proxy
- Connection to a rare domain for a peer group followed by an executable download
- Landspeed anomaly
- Emails from typosquatted domain
- Abnormal number of emails sent to a rare external recipient
- Abnormal amount of data sent to a rare external recipient
- Unusual VPN session length
- Unusual amount of data for VPN session compared to peers
- Unusual sensitive data access increase for a user
- And others (see details below)
2.1 Detection – Sample Spotter Search Queries
Please find below sample Spotter search queries to assist with the detection of some of the existing infections:
Note: Because of the rapidly changing attack landscape, based on our experience, the lifecycle of many of the IOC/domains/IP/artifacts can often be hours or 1-3 days, so the recommendation is not to rely on IOCs alone and to implement the use cases/predictive indicators for the best possible protection.
(rg_functionality contains “proxy” or rg_functionality contains “firewall”) and (destinationaddress = “193.37.212.173” or destinationaddress = “45.128.134.14” or destinationaddress = “95.179.242.6” or destinationaddress = “95.179.242.27” or destinationaddress = “199.247.25.102” or destinationaddress = “95.179.156.97” or destinationaddress = “31.170.167.123” or destinationaddress = “169.62.254.79” or destinationaddress=”169.47.124.22” or destinationaddress =”169.46.89.149” or destinationaddress = “70.40.216.90” or destinationaddress =”34.91.87.40” or destinationaddress = “58.158.177.102” or destinationaddress = “209.141.54.161”)
Destination Host Detections on Network Logs
(rg_functionality contains “Proxy” or rg_functionality contains “firewall”) and (destinationhostname contains “coronavirusstatus.space” OR destinationhostname contains “coronavirus-map.com” OR destinationhostname contains “blogcoronacl.canalcero.digital” OR destinationhostname contains “coronavirus.zone” OR destinationhostname contains “coronavirus-realtime.com” OR destinationhostname contains “coronavirus.app” OR destinationhostname contains “bgvfr.coronavirusaware.xyz” OR destinationhostname contains “coronavirusaware.xyz” OR destinationhostname contains “corona-virus.healthcare” OR destinationhostname contains “survivecoronavirus.org” OR destinationhostname contains “vaccine-coronavirus.com” OR destinationhostname contains “coronavirus.cc” OR destinationhostname contains “bestcoronavirusprotect.tk” OR destinationhostname contains “Coronavirusupdate.tk” Or destinationhostname contains “insiderppe.cloudapp.net” or destinationhostname contains “gulf-builders.com” or destinationhostname contains “corona-virus2019.us” or destinationhostname contains “marchadvertisingnetwork”)
File Hash Detections on Endpoint Logs
rg_functionality contains “Endpoint” and ( filehash=”73DA2C02C6F8BFD4662DC84820DCD983” OR filehash = “73DA2C02C6F8BFD4662DC84820DCD983” or filehash = “1BEBA1640F5573CBAC5552AE02C38F33” or filehash = “2b35aa9c70ef66197abfb9bc409952897f9f70818633ab43da85b3825b256307” or filehash = “0b3e7faa3ad28853bb2b2ef188b310a67663a96544076cd71c32ac088f9af74d” or filehash = “13c0165703482dd521e1c1185838a6a12ed5e980e7951a130444cf2feed1102e” or filehash = “Fda64c0ac9be3d10c28035d12ac0f63d85bb0733e78fe634a51474c83d0a0df8” or filehash = “126569286f8a4caeeaba372c0bdba93a9b0639beaad9c250b8223f8ecc1e8040” or filehash = “203c7e843936469ecf0f5dec989d690b0c770f803e46062ad0a9885a1105a2b8” or filehash = “238a1d2be44b684f5fe848081ba4c3e6ff821917” or filehash = “FEAF44B633EAC0D968701059C0952650BABEDB6862547C43018F81C0B76AB559” or filehash = “70DC6ED09FE1816BE0E1F13EB096B9567C246F8AA139F33ACBA42017CFECB869” or filehash = “E47B43A0AD9AB160598D8756A5FB9904668A1BA419C6B280BCC04B5DFB15267”)
Malicious File Attachment Detections on Inbound Emails
rg_functionality contains “email” and (filename contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR filename contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR filename contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR filename contains “CoronaVirusSafetyMeasures_pdf.exe” OR filename contains “CoronaVirusSafetyMeasures_xls.exe” OR filename contains “LIST OF CORONA VIRUS VICTIM.exe” OR filename contains “POEA HEALTH ADVISORY re-2020 Novel Corona Virus.pdf.exe” OR filename contains “POEA Advisories re-2020 Novel Corona Virus.2.pdf.exe” or filename contains “COVID-19.MARCH19.844531512”)
Malicious File/Process Detections on Endpoints
rg_functionality contains “EDR” and (destinationprocessname contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR destinationprocessname contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR destinationprocessname contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR destinationprocessname contains “CoronaVirusSafetyMeasures_pdf.exe” OR destinationprocessname contains “CoronaVirusSafetyMeasures_xls.exe” OR destinationprocessname contains “LIST OF CORONA VIRUS VICTIM.exe” OR destinationprocessname contains “POEA HEALTH ADVISORY re-2020 Novel Corona Virus.pdf.exe” OR destinationprocessname contains “POEA Advisories re-2020 Novel Corona Virus.2.pdf.exe”)
Malicious File/Process Detections on Windows
rg_functionality contains “Windows” and (filename contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR filename contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR filename contains “CORONA VIRUS AFFECTED CREW AND VESSEL.xlsm” OR filename contains “CoronaVirusSafetyMeasures_pdf.exe” OR filename contains “CoronaVirusSafetyMeasures_xls.exe” OR filename contains “LIST OF CORONA VIRUS VICTIM.exe” OR filename contains “POEA HEALTH ADVISORY re-2020 Novel Corona Virus.pdf.exe” OR filename contains “POEA Advisories re-2020 Novel Corona Virus.2.pdf.exe”)
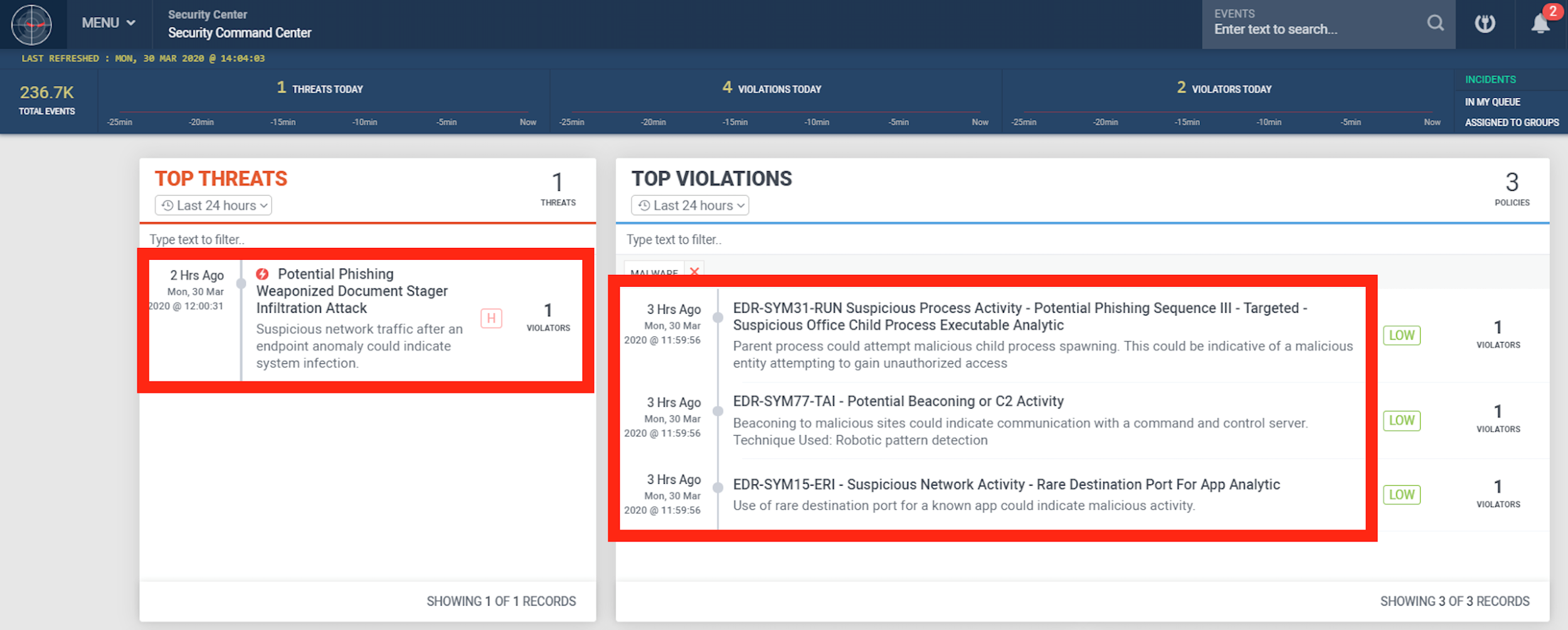
Figure 7: Fake COVID-19 Infection Phishing Email – Initial Weaponized doc Exploit Loading a Malicious dll
2.2 Securonix Detection – Some Examples of Securonix Predictive Indicators
Here is a summary of some of the relevant Securonix predictive indicators to increase the chances of early detection of these and future variants of such attacks on your network:
- Suspicious Process Activity – Targeted – Executable File/Script Creation Analytic – ATT&CK T1086
- Suspicious Process Activity – Targeted – Disable AV Monitoring Registry Analytic – ATT&CK T1089
- Suspicious Process Activity – Targeted – Potential Phishing Sequence II Malicious Payload Open Browser Modality Analytic – ATT&CK T1193
- Suspicious Proxy Activity – Unusual Useragent for a Source Analytic – ATT&CK T1193
- Suspicious Process Activity – Targeted – Potential Multi-Browser/RDP/VNC Credential Dumping Activity Analytic – ATT&CK T1503
- Suspicious Registry Activity – Targeted – Autorun Changes Analytic – ATT&CK T1060
- Suspicious Network Activity – Potential Beaconing/C2 Analytic – ATT&CK T1043
- Suspicious Process Activity – Potential Phishing Sequence III – Rare Office Child Process Analytic – ATT&CK T1193
and others.
Threat Model: Potential VPN Account Compromise
Detect suspicious land speed, and authentication from rare countries combined with multi-factor authentication anomalies.
Primary log sources – VPN, SSO, MFA
Threat Model: Possible Privilege Elevation for Remote Connections
Primary log sources – VPN, SSO, Host logs including Windows/Unix
Threat Model: Data Exfiltration from Remote Connections
Detect users authenticated to VPN or at a rare timeslot attempting exfiltration.
Primary log sources – VPN logs, SSO Logs, Web proxy, Email gateway, DLP feeds
Threat Model: Suspicious Data Aggregation Attempts
Detect users authenticated to VPN or at a rare timeslot attempting to aggregate data.
Primary log sources – VPN logs, SSO Logs, Cloud Content Management systems, Database logs, Firewall logs, Windows Network/Object share logs, Unix logs
Threat Model: Suspicious Data Aggregation Attempts
Detect users authenticated to VPN or at a rare timeslot attempting unauthorized collaboration.
Primary log sources – VPN logs, SSO Logs, Cloud Content Management systems
Threat Model: Phishing Leading to Information Disclosure/IP Theft
Detect users that were phished and observed exfiltrating data.
Primary log sources – Email, Web proxy, Firewall
Threat Model: Mailbox Compromise
Detect users that were phished attempting exfiltration via mailbox compromise.
Primary log sources – Email, Email audit, EDR, Web proxy, Email gateway, DLP feeds
Threat Model: Phishing Leading to Sabotage
Detect users that were phished attempting intentional sabotage.
Primary log sources – Email, Web proxy, Windows, Unix, PIM/PAM logs
Threat Model: Account Compromise/Sharing Detection
Detect user accounts that indicate a possible compromise.
Primary log sources – VPN, CASB, MFA logs
and others.
Some examples of the successful detection of these real-world attacks in practice in the Securonix Labs are shown in Figure 7.
References
- Fortinet. Attackers taking advantage of Coronavirus Media Frenzy. https://www.fortinet.com/blog/threat-research/attackers-taking-advantage-of-the-coronavirus-covid-19-media-frenzy.html
- Forbes. Coronavirus Scam Alert. https://www.forbes.com/sites/thomasbrewster/2020/03/12/coronavirus-scam-alert-watch-out-for-these-risky-covid-19-websites-and-emails/
- Colin Hardy. Malware analysis archives.
- Krebs on Security. Live Coronavirus Map Used to Spread Malware. https://krebsonsecurity.com/2020/03/live-coronavirus-map-used-to-spread-malware/
- GB Hackers on Security. Chinese APT Hackers Exploit Coronavirus. https://gbhackers.com/malware-via-weaponized-coronavirus-lure-documents/#cybersecurity
- Reason Security. Covid 19 Info Stealer. https://blog.reasonsecurity.com/2020/03/09/covid-19-info-stealer-the-map-of-threats-threat-analysis-report/
- https://krebsonsecurity.com/2020/03/live-coronavirus-map-used-to-spread-malware/
- https://www.us-cert.gov/ncas/current-activity/2020/03/06/defending-against-covid-19-cyber-scams
- CISA risk management for Novel coronavirus. https://www.cisa.gov/sites/default/files/publications/20_0306_cisa_insights_risk_management_for_novel_coronavirus.pdf
- Recorded Future. Coronavirus Panic Exploits. https://www.recordedfuture.com/coronavirus-panic-exploit/
- MB Threat Intel. Threat Intelligence Team. https://twitter.com/MBThreatIntel.
- Lukas Stefanko. Android Coronavirus. https://lukasstefanko.com/2020/03/android-coronavirus-malware.html







