- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov, Securonix Threat Research Team
Introduction
Securonix Threat Research Team (STR) has been actively investigating the details of the Spectre and Meltdown Side-Channel Information Disclosure Vulnerabilities since last week to help our customers mitigate/respond to the vulnerabilities.
Below is a summary of what we currently know about the vulnerabilities and our recommendations to help increase the chances of mitigating the current and future variants of attacks targeting the vulnerabilities.
*** There will be updated indicators as we perform further analysis. The recommendation is to check this advisory first if you want the latest technical details.
 Figure 1: Securonix Labs – Meltdown Attack In Action Accessing Linux Kernel Memory From Unprivileged Process
Figure 1: Securonix Labs – Meltdown Attack In Action Accessing Linux Kernel Memory From Unprivileged Process
Summary
The Meltdown vulnerability (CVE-2017-5754) exploits side effects of out-of-order execution on modern processors to read arbitrary kernel-memory locations including personal data and passwords effectively enabling attackers to break security boundaries between processes enforced by the hardware. Meltdown can be effectively stopped using software patches e.g. KPTI/Kaiser.
The Spectre vulnerabilities (CVE-2017-5753,CVE-2017-5715) leverage the same fundamental principles as Meltdown but in a slightly different way allowing attackers to break isolation between applications tricking error-free programs into leaking secrets. Spectre is somewhat harder to exploit than Meltdown, but it is much more difficult to stop using software patches and a complete fix is likely going to require new processors.
- Impact:
- Spectre (CVE-2017-5753,CVE-2017-5715): Intel, AMD, and ARM processors (No, Raspberry Pi’s are not affected!)AMD impact is currently unconfirmed. In terms of infrastructure, this likely directly impacts many/most desktop, laptop, server/cloud, and smartphone devices. The vulnerability may allow attackers to read memory contents from other users/processes.
- Meltdown (CVE-2017-5754): All Intel processors since 1995 except Intel Itanium and Intel Atom before 2013. In terms of infrastructure, this likely directly impacts many/most desktop, laptop, and smartphone devices. This also likely to impact cloud providers using Intel CPUs and Xen PV as virtualization as well as cloud providers relying on containers sharing the same kernel viz. Docker, LXC, OpenVZ etc. The vulnerability may allow attackers to read kernel memory.
- Infiltration vector(s): Both Spectre and Meltdown require attackers to be able to execute a malicious payload on the vulnerable targets in some way, which can be in the form of a malicious executable placed on the target as part of an initial infiltration via another exploit vector, or a specially crafted script ran on the target as part of a watering hole-like attack e.g. a malicious Javascript payload.

Figure 2: Spectre Attack In Action Unauthorized Process Reading Linux Kernel Structures (Syscall Table)
Spectre and Meltdown Attacks Technical Overview
As shown in Figures 1 and 2, Spectre and Meltdown can allow attackers to gain access to the kernel/unauthorized process memory locations which may enable attackers to steal sensitive data, including shared secrets, cookies, passwords, and other information.
Here are some of the key high-level steps used in the Meltdown attack to help you get a better idea of how it works:
- Attacker triggers speculative memory reads to kernel pages from an unauthorized process;
- Attacker requests a legitimate non-cached location from memory based on the result of the calculation in #1.
- When the faulting exception from #1 retires, it already issued a load request out to cache ensuring the results were cached in TLB.
- Finally, attacker requests loads to the memory locations for the desired offset and measures the time for the loads. A TLB cache hit will be much quicker than a cache miss at the offset of the value retrieved in #1 compared to other offsets/values, which allows attacker to obtain the sensitive data/gain unauthorized access to kernel data.
An example of one of the key parst of the corresponding x86-64 Assembly code fragment used to trigger speculative code execution in the actual working Meltdown exploit shown above resulting in the cache-based side-channel enabling attackers to read kernel memory is depicted in Figure 3:
 Figure 3: Spectre Attack In Action Unauthorized Process Reading Linux Kernel Structures (Syscall Table)
Figure 3: Spectre Attack In Action Unauthorized Process Reading Linux Kernel Structures (Syscall Table)
Further technical details of the Spectre/Meltdown vulnerabilities are out of scope for this advisory and can be found in a number of online articles including [4,5].
Mitigation and Prevention – Checking for Vulnerable Systems
As part of the recommended mitigation steps, it may be necessary to detect internal systems that are vulnerable to these attacks. In order to find out if any of your Linux systems are vulnerable, you can run e.g. spectre/meltdown vulnerability checker by downloading the code from github (see https://github.com/speed47/spectre-meltdown-checker.git) and then running:
$ sudo sh spectre-meltdown-checker.sh
The sample output from the checker is shown in Figure 4.
 Figure 4: Scanning Linux For Spectre and Meltdown
Figure 4: Scanning Linux For Spectre and Meltdown
If you are using Windows, you can download the Speculation Control Powershell script (see https://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050) and run the following commands to check the status of the speculation control mitigation on your Windows systems to see if they are vulnerable:
PS> # Save the current execution policy so it can be reset
PS> $SaveExecutionPolicy = Get-ExecutionPolicy
PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuser
PS> CD C:\ADV180002\SpeculationControl
PS> Import-Module .\SpeculationControl.psd1
PS> Get-SpeculationControlSettings
PS> # Reset the execution policy to the original state
PS> Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser
Mitigation and Prevention – Securonix Recommendations
Here are some of the Securonix recommendations to help prevent, detect, and mitigate such vulnerabilities within your organization:
- Apply your OS and software updates, including silicon microcode updates and Web browser patches for JS attack vector (see see https://spectreattack.com/#faq-advisory and https://cloudblogs.microsoft.com/microsoftsecure/2018/01/09/understanding-the-performance-impact-of-spectre-and-meltdown-mitigations-on-windows-systems/);
- Make the recommended configuration changes to enable protection;
- Apply the relevant firmware update from the OEM device manufacturer, where feasible (see https://github.com/hannob/meltdownspectre-patches for technical details) i.e.
 Figure 5: Available vendor-specific patch information
Figure 5: Available vendor-specific patch information
For example, if you are using Microsoft servers, Microsoft Windows Server-based machines (physical or virtual) should get the Windows security updates that were released on January 3, 2018, and are available from Windows Update.
You can then make the necessary configuration changes to enable protection:
Make sure to enable Kernel Virtual Address (KVA) feature and then enable mitigations to help protect against speculative execution side-channel vulnerabilities e.g.
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management” /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management” /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
reg add “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization” /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d “1.0” /f
If this is a Hyper-V host: fully shutdown all Virtual Machines. Restart the server for changes to take effect. See https://support.microsoft.com/en-us/help/4072698/windows-server-guidance-to-protect-against-the-speculative-execution for more details.
Note: If you are running untrusted code within your VM instances (for instance, if you allow a customer to upload a binary or a code fragment that they can then execute within your VM instance) and you want to isolate the application binary/code to ensure the code can’t access memory within the VM instance that it should not have access to, you may need to evaluate whether to apply additional security mitigations within each of your VM guest or physical instances.
Detection – Some Examples of Relevant High-Level Behavior Analytics/Predictive Indicators
Note: While the high-level analytics examples below have the potential to detect some of the malicious exploitation/post-exploitation activity associated with Spectre and Meltdown, they may not work for all cases. Specifically, due to the nature of the Spectre and Meltdown vulnerabilities, there can be a number of different attack vectors possible, many of which are low-level and are not visible in logs. For this reason, to mitigate these vulnerabilities, it is critical to focus both on post-exploitation activity as part of a broader set of analytics provided by Securonix and also on reducing your attack surface and applying patches/configuration changes properly to minimize the risk.
Here are some high-level examples of some of the relevant Securonix behavior analytics/predictive indicators based on the key Spectre/Meltdown attack vectors to increase the chances of early detection of the malicious exploitation/post-exploitation activity associated with the Spectre and Meltdown attack vectors:
- Suspicious Process Activity – Peak Exception Volume For Process Analytic
- Suspicious Process Activity – Rare Parent-Child Relationship For Host Analytic
- Suspicious Process Activity – Targeted – Executable File Creation Analytic
- Suspicious Proxy Activity – Peak HTTP/S Outbound Volume For Host Analytic
- Suspicious Cloud Activity – Rare StartInstance Source Analytic
- Suspicious Cloud Activity – Rare AWS S3 Source Address For Bucket Analytic
- Suspicious Cloud Activity – Rare AWS S3 Operation For Bucket Analytic
- Suspicious Cloud Activity – Diurnal AWS S3 Access For Bucket Analytic
etc.
It is important to keep in mind that there are many other attack vectors and log sources/data sources that need to be considered depending on the potential attack surface/cloud infrastructure used by your organization e.g. Microsoft Azure, AWS etc.
References
[1] nixCraft. How to check Linux for Spectre and Meltdown vulnerability. January 8, 2018.https://www.cyberciti.biz/faq/check-linux-server-for-spectre-meltdown-vulnerability/. Last accessed: 1-8-2018.
[2] Cisco Talos Blog. Meltdown and Spectre. January 8, 2018. http://blog.talosintelligence.com/2018/01/meltdown-and-spectre.html. Last accessed: 1-8-2018.
[3] Lucian Armasu. Meltdown, Spectre Can Be Exploited Through Your Browser. January 4, 2018. http://www.tomshardware.com/news/meltdown-spectre-exploit-browser-javascript,36221.html. Last accessed: 1-8-2018.
[4] Jann Horn et al. Meltdown and Spectre. Google Project Zero. January 3, 2018. https://spectreattack.com/#faq-fix. Last accessed: 1-8-2018.
[5] Google Project Zero. Reading Privileged Memory With Side Channel. January 3, 2018.https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html. Last accessed: 1-8-2018.
[6] Pavel Boldin. Meltdown Exploit. January 7, 2018.https://github.com/paboldin/meltdown-exploit. Last accessed: 1-8-2018.




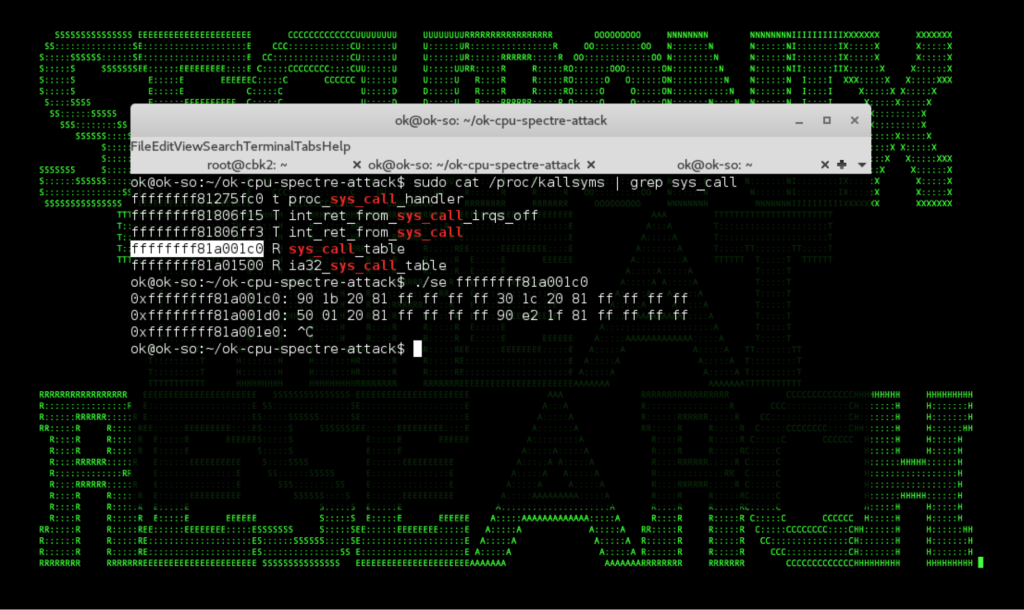 Figure 1: Securonix Labs – Meltdown Attack In Action Accessing Linux Kernel Memory From Unprivileged Process
Figure 1: Securonix Labs – Meltdown Attack In Action Accessing Linux Kernel Memory From Unprivileged Process
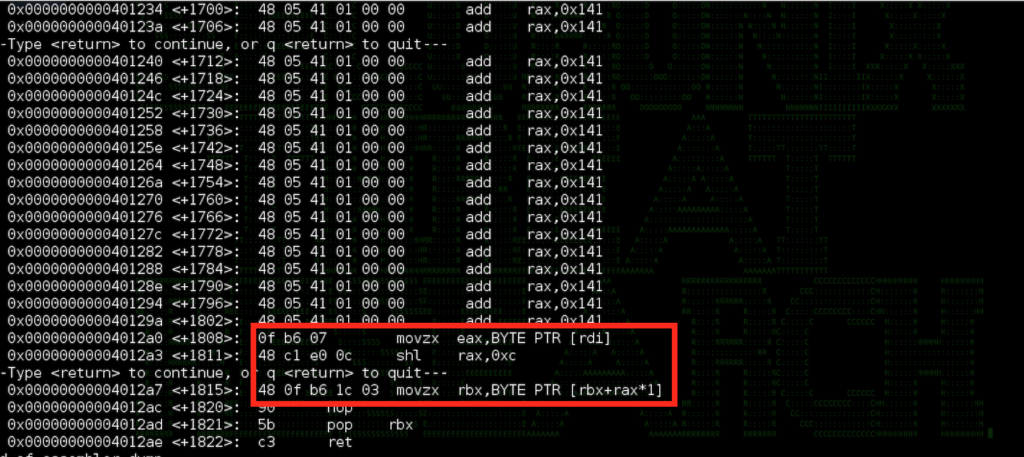 Figure 3: Spectre Attack In Action Unauthorized Process Reading Linux Kernel Structures (Syscall Table)
Figure 3: Spectre Attack In Action Unauthorized Process Reading Linux Kernel Structures (Syscall Table)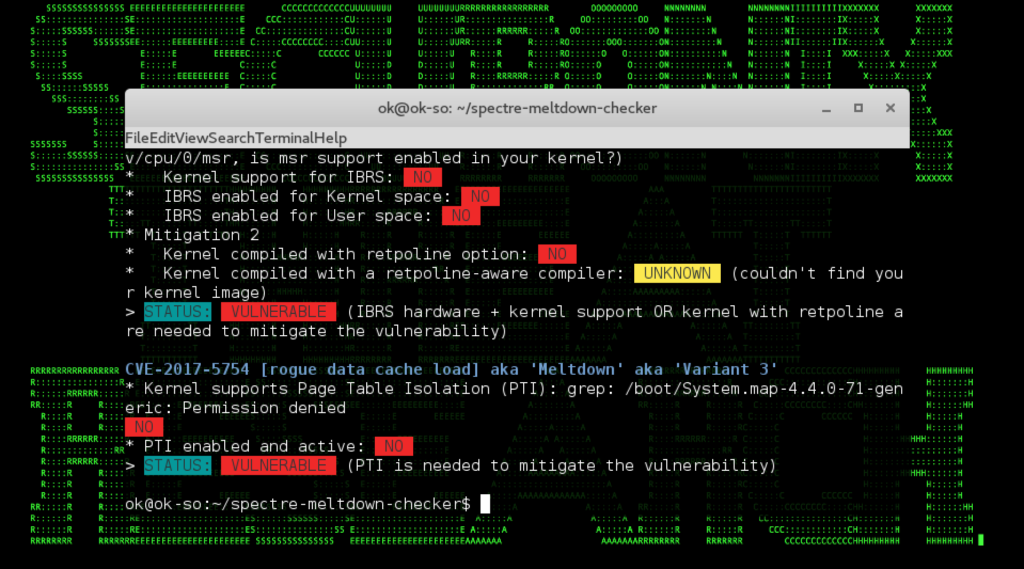 Figure 4: Scanning Linux For Spectre and Meltdown
Figure 4: Scanning Linux For Spectre and Meltdown Figure 5: Available vendor-specific patch information
Figure 5: Available vendor-specific patch information


