- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
According to the new ThoughtLab survey, it takes an average of 128 days to detect a breach and an additional 47 days to respond. Security analysts lose valuable time switching screens during investigations and are slowed by increasingly complex IT environments. Data resides in disparate sources, making it difficult to collaborate and prioritize incident response efforts. In order to stay ahead of threats, organizations need detection and response to be more seamlessly integrated.
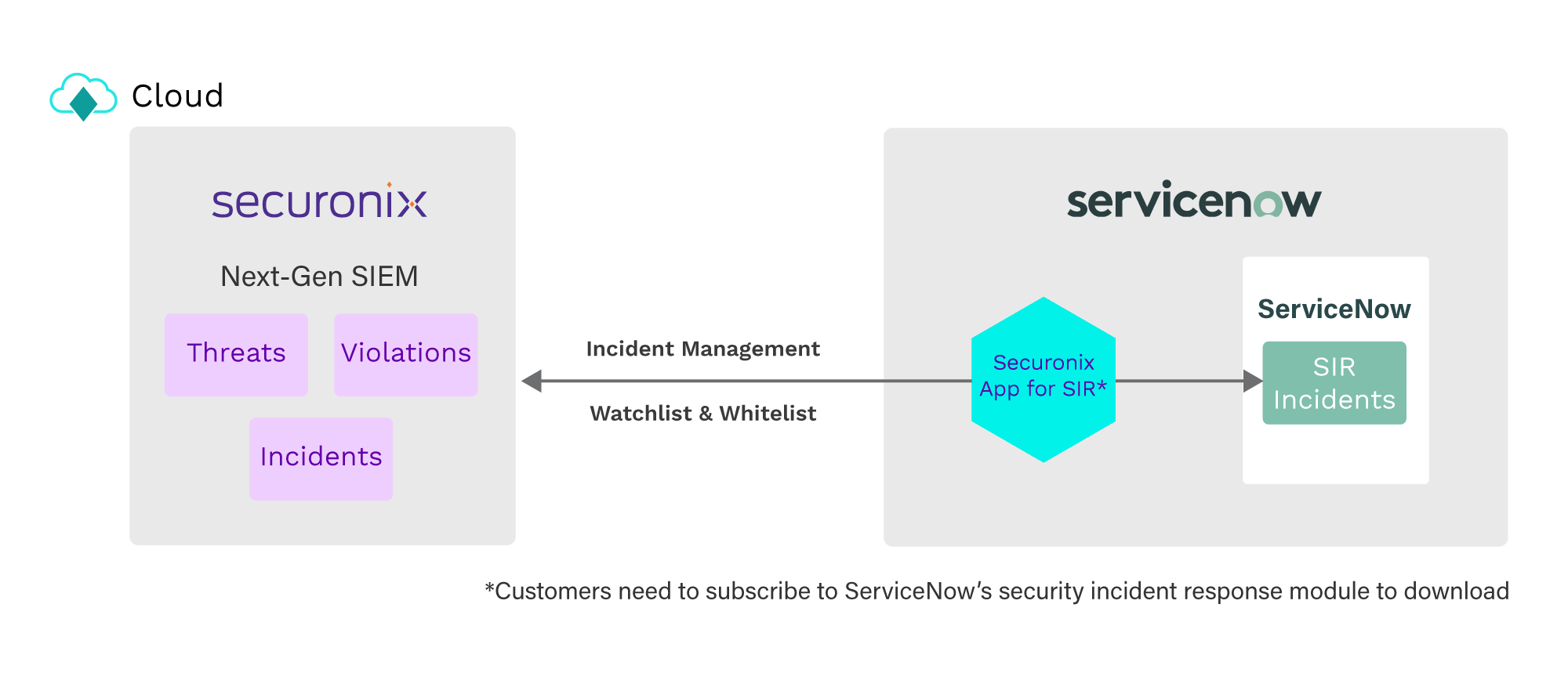
That’s why Securonix is pleased to announce the availability of a new ServiceNow integration app available via the ServiceNow app store. This release allows our customers with ServiceNow to leverage a bi-directional integration and ultimately help their analysts conduct more seamless investigations. The integration between Securonix Next-Gen SIEM and ServiceNow is an upgrade that allows for better communication between the two systems.
The joint solution combines context enrichment and advanced threat detection from Securonix with the security incident management, workflow, and orchestration features of ServiceNow. Ultimately this integration provides SOC analysts, forensic investigators, and CISRT teams with a single collaborative view across the organization. Let’s explore some of these capabilities in more detail.
How It Works
SOC and IT teams can work out of either platform and have the ability to modify SIEM detections directly from ServiceNow. Analyst notes, status changes, and investigation updates in ServiceNow feeds back into Securonix Next-Gen SIEM automatically, allowing you to tune detection as needed and increase collaboration.
- Securonix Next-Gen SIEM identifies actionable alerts (threats, violations) based on machine learning and AI. Alerts can be escalated for incidents within Securonix incident management for investigation.
- The threats trigger playbook actions within Securonix to initiate an incident in ServiceNow through the bi-directional API integration.
- Securonix App for SIR automatically syncs these alerts with ServiceNow through Securonix API and creates a security incident for SOC analysts to investigate. Advanced filtering options allow you to curate alerts to sync and create incidents.
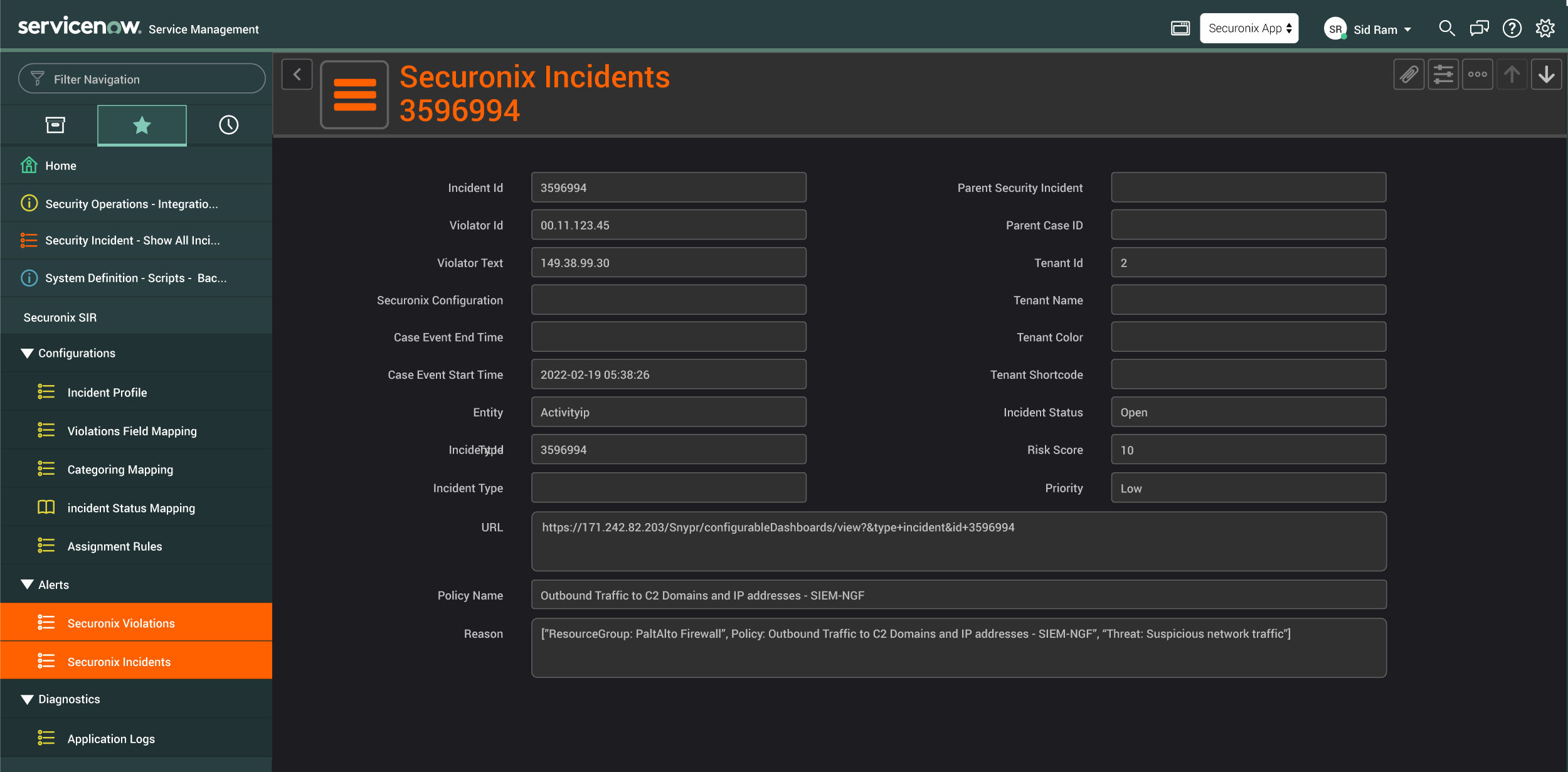
- The incident in ServiceNow includes metadata about the alert along with the complete details of the security violation from Securonix, including the raw alert. This allows analysts to conduct their entire investigation from either platform.
- Analysts can customize the mapping of incident attributes to fit their needs and can also automatically categorize ServiceNow incidents based on the type of Securonix alert generated; thereby automatically triggering downstream workflows, including assigning incidents to specific teams or analysts.
- Any subsequent events associated with the same violation are added to the same incident in ServiceNow, including any analysts’ comments or notes.
- Any updates or actions made in ServiceNow will be reflected in Securonix. This allows you to achieve auto-closure or auto-sync of the status of incidents in Securonix, upon changes in ServiceNow incident status.
Solution Benefits
Improve Your Mean-time-to-Respond
The integration with ServiceNow improves collaboration across platforms and lowers MTTR with real-time ingestion of incidents, threats, and violations. This allows your team members to continue working within their existing ecosystem without context switching, which equates to valuable time savings.
Improve the Analyst Experience
SOC and IT teams can work out of either platform and have the ability to modify SIEM detections such as whitelisting or adding users to a watchlist directly from ServiceNow. Analyst notes, status changes, and investigation updates sync automatically to the SIEM, allowing for better collaboration and easier compliance audits. Ultimately this integration keeps systems in sync and improves the overall analyst experience.
Achieve a Fast Time-to-Value
The Securonix and ServiceNow integration seamlessly connects your SOC and ITSM workflows. Rather than reconfiguring your workflows, you can sync your existing category and incident mapping labels for a fast time-to-value.
Flexible Deployment for MSSPs
This integration allows MSSP partners to broaden their offering and ultimately deliver higher value to their customers. Along with gaining additional operational scalability, MSSPs can support multiple Securonix ServiceNow deployment models including: single, multi-tenant, and managed vs customer-managed. Managed service providers can offer a solution with minimal disruption to their pre-existing custom processes and workflows with the Securonix ServiceNow integration.
Integrating Securonix with your ServiceNow solution provides you with actionable intelligence on your highest risk threats in real-time, so you have the contextual information you need to take action.
Learn More About Securonix and ServiceNow
Securonix ServiceNow Solution Brief
ServiceNow Store – Securonix Incident App







