- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Findlay Whitelaw, Field CTO, Securonix
The cyber security threat landscape has undergone significant changes in recent years, with insider threats increasingly recognized as a formidable challenge. The new 2024 Insider Threat Report, published by Cybersecurity Insiders and commissioned by Securonix, found that 53% of cybersecurity professionals believe insider attacks are more difficult to detect and prevent than external cyber-attacks. This is an increase of more than 10% over the past five years, underscoring a shift in perception that is a crucial development in cybersecurity. It highlights the need for more sophisticated insider threat security strategies, incorporating advanced security solutions, and adopting a layered approach to enhance visibility into user behavior and bolster overall organizational security posture.
One of the key factors contributing to this perception shift is the evolving complexity of insider threats. Unlike external threats, insiders have legitimate access to organizational systems and data. This access allows them to bypass traditional security measures designed to prevent external threats. Additionally, individuals’ motivations behind insider threats vary, ranging from financial fraud, financial gain, personal benefit, revenge, and sabotage, making detection and prevention more challenging.
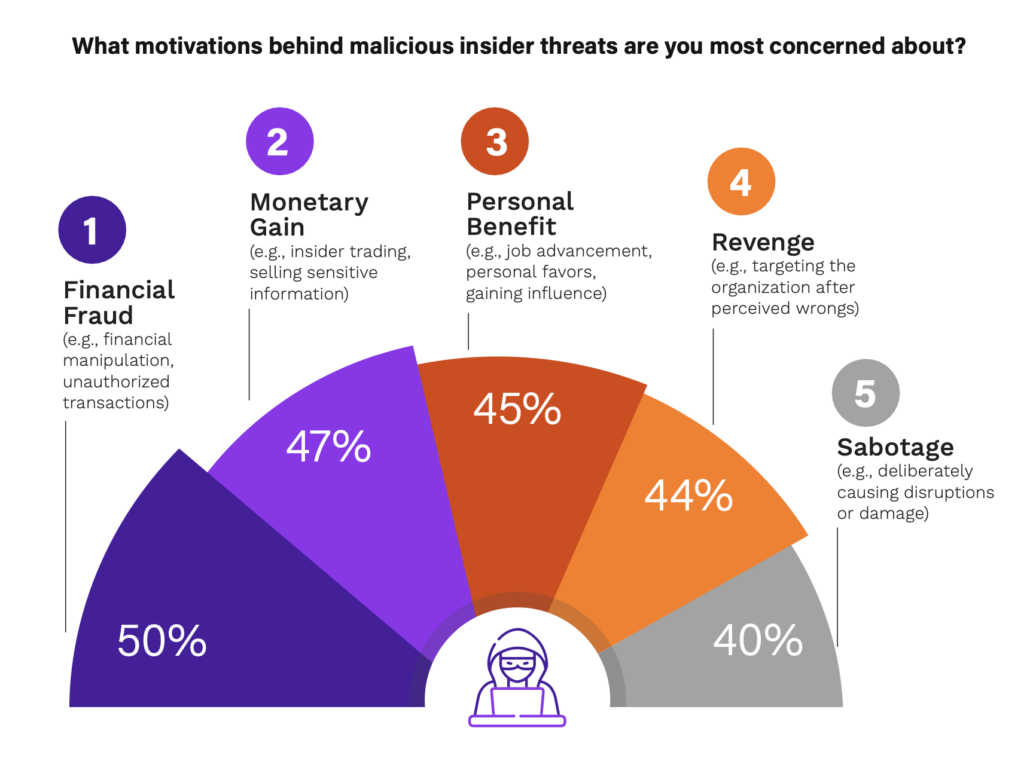 Furthermore, the cybersecurity threat landscape has changed dramatically over the past five years, with the increased adoption of remote and hybrid work models. With employees working remotely and operating outside traditional, controlled, and protected networks, the boundaries between secure corporate environments and potentially vulnerable remotes have blurred. For example, employees are accessing sensitive data from various locations, sometimes on personal or less secure devices, or accessing company resources in public spaces — where there are inherent challenges in monitoring and controlling data access in varied environments. Variability in working environments also makes it more difficult to enforce security policies and monitor for anomalous behavior consistently.
Furthermore, the cybersecurity threat landscape has changed dramatically over the past five years, with the increased adoption of remote and hybrid work models. With employees working remotely and operating outside traditional, controlled, and protected networks, the boundaries between secure corporate environments and potentially vulnerable remotes have blurred. For example, employees are accessing sensitive data from various locations, sometimes on personal or less secure devices, or accessing company resources in public spaces — where there are inherent challenges in monitoring and controlling data access in varied environments. Variability in working environments also makes it more difficult to enforce security policies and monitor for anomalous behavior consistently.
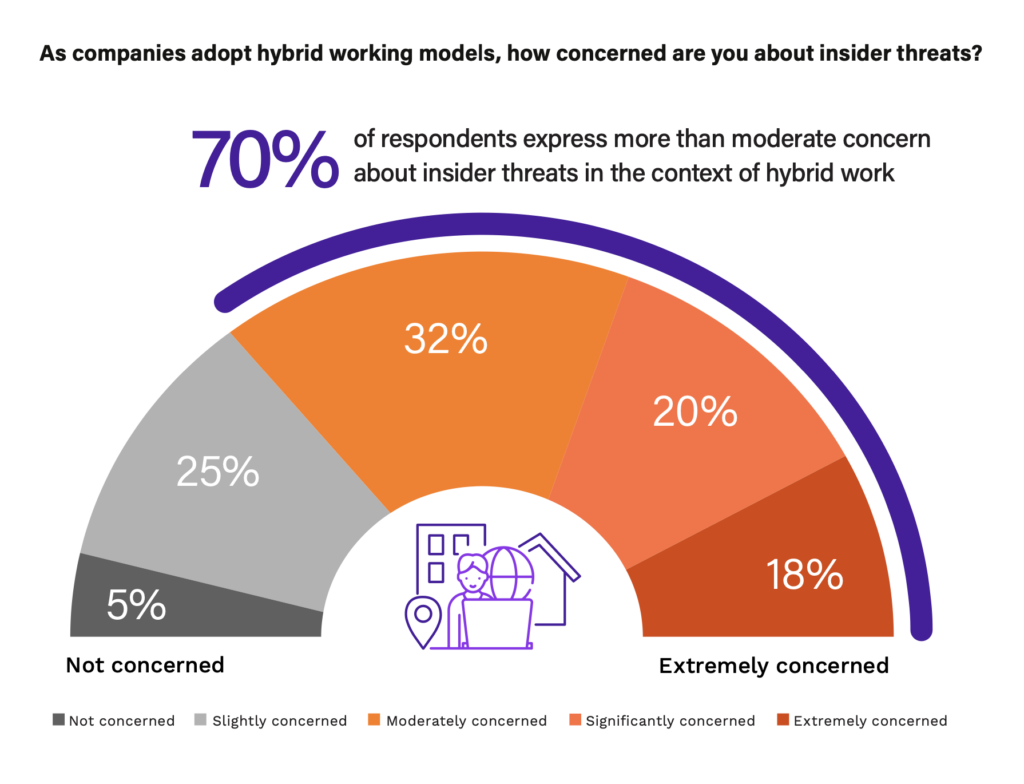
Despite organizations spending more than three years refining approaches to hybrid work since the pandemic, an astounding 70% of cybersecurity professionals feel more than moderately concerned about insider risk in the context of their strategies.
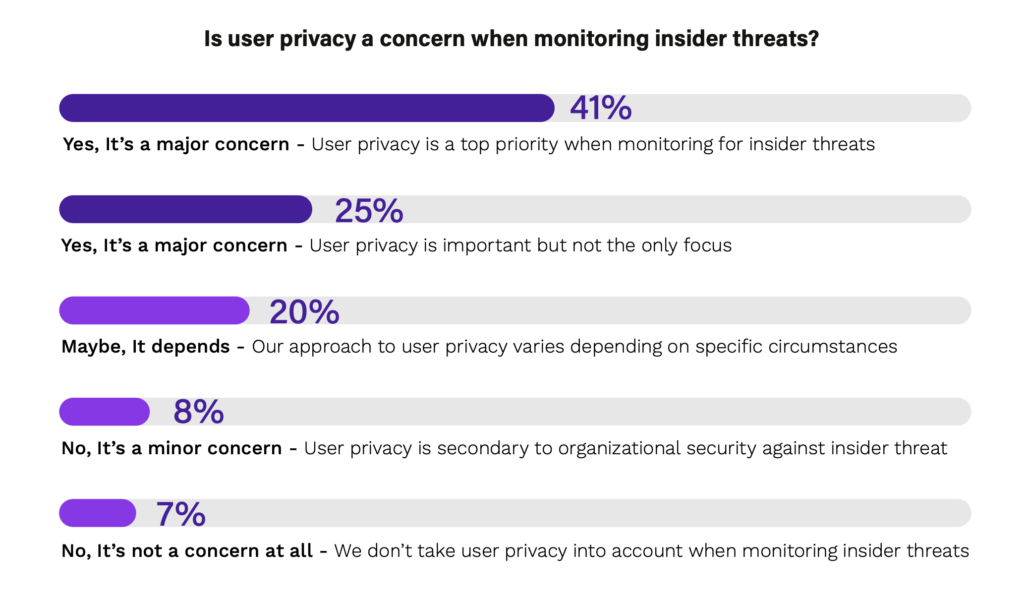
Another factor influencing the perception of insider threats is the challenge of balancing employee privacy with security measures. Monitoring and mitigating insider threats frequently involves observational strategies. While essential for security, these policies and procedures might be overly intrusive if not managed with care and transparency. It is important to balance security and privacy, ensuring no unintended consequences or impacts on employee trust and morale, which is often overlooked. Organizations must navigate complex legal and ethical considerations to implement effective insider threat programs without infringing on employee privacy. This is also reflected in the 2024 Insider Threat Report, as 66% of respondents cited that user privacy is a major concern when monitoring insider threats.
As detection technologies like artificial intelligence (AI) and machine learning (ML) become more advanced, organizations can better identify external threats. However, these technologies are still adapting to defend against internal threats. Cultural and psychological aspects that influence the detection of insider threats can be more subtle and complex. Understanding and monitoring the behavioral aspects of insider threats requires a different approach.
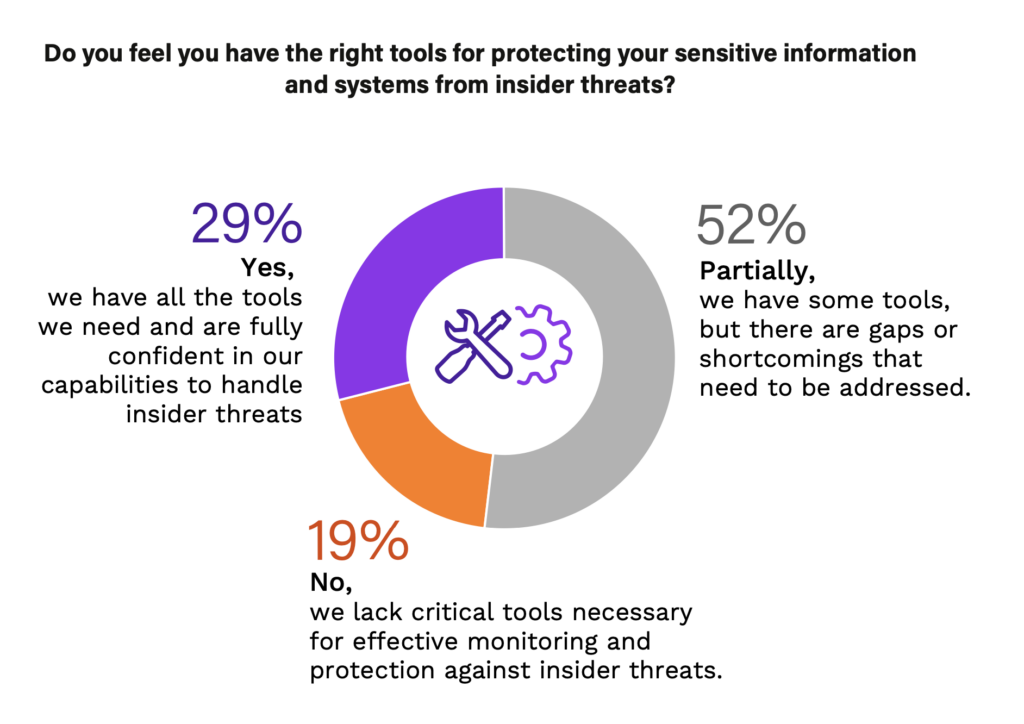
Organizations are increasingly turning to advanced technologies like AI, ML, user and entity behavior analytics (UEBA), and security information and event management (SEIM) to combat the rising challenges of insider threats. These technologies offer the ability to analyze behavior patterns and identify anomalies indicating insider threats and aggregate, analyze, and report on security data from various sources across the networks, providing real-time monitoring, event correlation, and alerting for potential security incidents. However, the sophistication of these technologies also means that the skills required to manage them are more advanced, which can be a barrier for some organizations. Surprisingly, the report found that 71% of cybersecurity professionals had little to no cover in protecting sensitive information and systems from insider threats, and they should consider these technological tools as part of their insider threat program strategy.
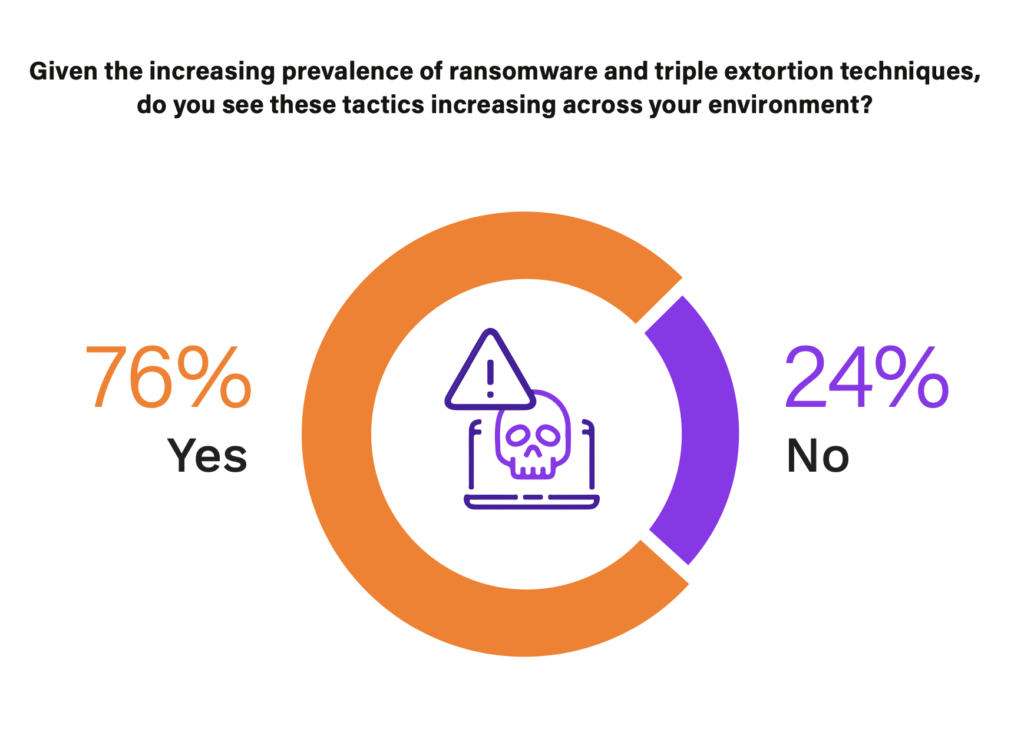
As external cybersecurity defenses improve, it has become harder for external attackers to penetrate them, making the insider route more appealing. External threat actors can tailor their attacks to be more effective and less detectable. An example in practice and plausible correlation is the rise of triple extortion attacks in the context of increasing concerns about insider threats. Taking this scenario into account with the shift to remote working and external attackers trying to penetrate from within presents an intriguing correlation and the rise of triple extortion attacks. These unintentional insiders could unwittingly become a link in the attack chain, either by coercion or manipulation. This sentiment is being felt within the field, with 76% of respondents citing an increase in triple extortion techniques across their environment.
Addressing insider threats requires a holistic approach that supports insider threat management technologies like UEBA and SEIM. It involves creating a culture of security awareness to strengthen the human firewall, where employees are educated about the risks and responsibilities of insider threats. Regular training, transparent communication, and involving employees in developing security policies are essential to this approach.
The shift in the perception regarding the difficulty of detecting and preventing insider threats compared to external cyber-attacks reflects a growing awareness in the cybersecurity community. This awareness drives the adoption of more sophisticated technologies and holistic strategies to mitigate these risks. As the cybersecurity and insider threat landscape continues to evolve, organizations must remain vigilant and adaptable, ensuring they can handle the complexities of modern-day insider threats.