- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Recently, Securonix has engaged with many of our customers to provide an update on three of our newly released products: Autonomous Threat Sweeper (ATS), Securonix Investigate, and Securonix SOAR. Our conversations provided an overview of the products, but they also helped us understand what kind of impact we can have on an organization’s day-to-day activities when battling potential threats. Out of these conversations, two things become clear.
First, if organizations want to keep pace with modern sophisticated threats they need to transform how they operate. Second, L1 security analysts are bogged down by inefficiency. These conversations confirmed hypotheses we already believed:
- The 80/20 rule: A small fraction of the team is experienced enough and holds the key knowledge to understand how new threats can impact the environment. Tier-1 analysts rely on more experienced analysts for institutional and cybersecurity expertise when detecting and responding to threats.
- 3 V’s (Volume, Variety, and Velocity of Threat): Staying ahead of new and emerging threats requires a lot of coordination and manual work. Analysts must patch or update systems to stay on top of future attacks and look through existing data to see if the new threat has already infiltrated the environment.
- Brain Drain: If the experts who curated their own knowledge over the years transition out of the role or company, that domain knowledge is taken with them and is lost to the organization.
Securonix can play a key role in helping organizations transform to be better prepared to tackle modern threats and also make tier-1 analysts more efficient. The best way to show this is by looking at a day in the life of a Tier-1 analysts we will call “SOCrates”.
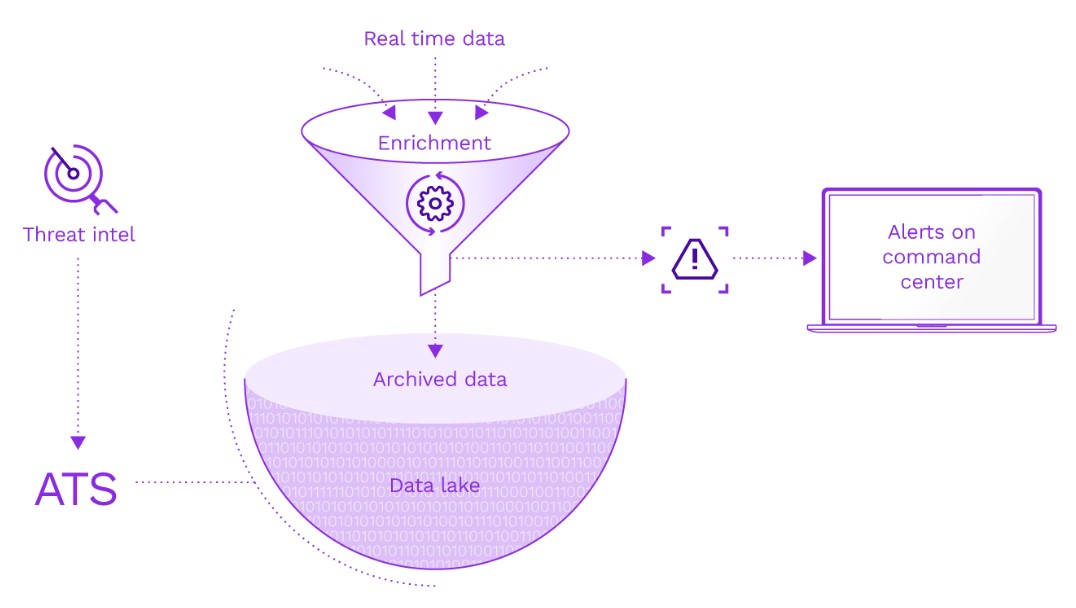
Know your level of exposure with Autonomous Threat Sweeper
SOCrates is under tremendous pressure to keep pace with the velocity of new and emerging threats. As soon as a new threat like Log4J or Sunburst hits the headlines pressure is exerted downwards as the C-suite demands to know the level of impact.
As cyberattacks continue to grow in breadth and scale, it is difficult for SOCrates to conduct fast investigations, especially in instances when a threat may be laying dormant in archived data. He needs autonomous solutions that can assess the exposure to emerging threats on an ongoing basis. Autonomous Threat Sweeper (ATS) provides air-cover for analysts like SOCrates by automating cyber rapid response for emerging threats.
Rapid response takes a massive amount of time and effort. In a typical month, SOCrates probably sees over 30 different threats and incidents that warrant closer review, resulting in over 1200 IOCs on average that must be extracted, codified, and searched for. This can take him upwards of 80 hours for that task alone. And that’s without even finding anything of concern or covering nights and weekends.
SOCrates works hard Monday-Friday, but threat detection is a 24/7 job. New threats come in fast almost daily, and his team must monitor and curate huge amounts of intelligence to determine if their business is exposed and they need to act. ATS helps security teams because it continuously sweeps through data, even on holidays and after hours.
Here’s how ATS can help SOCrates
The Securonix Threat Labs team provides coverage by staying on the forefront of threat research. They use the latest threat research to extract IOCs and analyze/codify TTPs to develop detection content. ATS then uses these queries to automatically sweep through vast amounts of historical event data in the security data lake before compiling the threat findings into reports. When a threat is detected in his environment, ATS automatically creates incidents and sends alerts proactively to SOCrates. So when the CISO comes breathing down his neck, he’ll already have all of the answers.
Get context with a click of a button with Securonix Investigate
Everyday SOCrates has to investigate a number of alerts. These alerts often require him to seek out and gather information about the entities involved. This means he has to comb through multiple internal systems and external sources to find the intelligence to understand the nature of each alert.
SOCrates has a SIEM that enriches content at the time of ingestion, but context is dynamic and changes. That content has to be re-enriched from time to time. If SOCrates uses outdated intelligence then the information he provides to the team could be inaccurate, leading to uninformed decision-making and inaccuracy when mitigating a potential threat.
Once he finds useful information he often has to reach out to other team members and more senior analysts to get their perspective. Traditionally he would turn to external tools like email, instant messenger and ticketing systems. These tools are fine at the moment, but if a similar incident arises in the future and he needs to look back on those conversations it is very difficult to quickly find information. As you can imagine, this process of collecting data and sharing insights takes a lot of time and effort.
How Securonix Investigate can help SOCrates
Securonix Investigate can speed this process up. With Securonix Investigate SOCrates gets context on-demand and instantly shares findings and retains information. SOCrates no longer has to manually search and collect data from a bunch of systems and external websites and forums. He can now bring all the context from these sources into the investigation either with a click of a button or automatically. In other words, instead of SOCrates going and getting the intelligence he needs, the intelligence is brought to him.
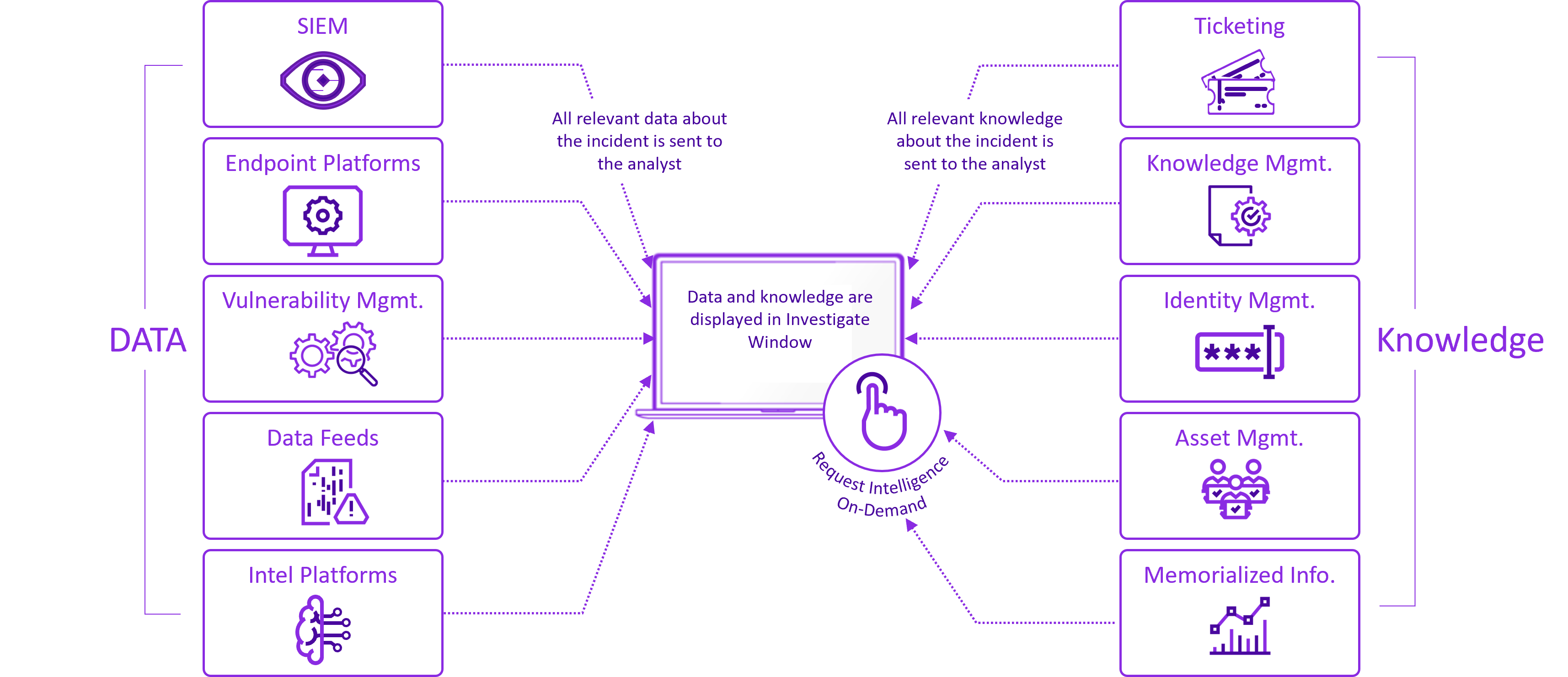
When SOCrates wants to note information within an investigation and share what he has found, he doesn’t need to leave the investigation and pivot to external tools like email. He can annotate directly within the Securonix Investigate window. SOCrates can also share insights across the organization or within trusted groups through dedicated communication channels. Think of dedicated channels being set up for trusted groups like red, blue, and purple teams. Another example is setting up a communication channel for known vulnerabilities or watchlists. The communication channels maintain continuity by communicating information type and urgency to identify patterns and improve the team’s overall ability to react to data.
An additional benefit to having the ability to annotate and share intelligence is that the organization can retain all the learning and insight from past investigations. This intelligence can be found quickly and leveraged against future incidents and it can be used to train new analysts as they join the team.
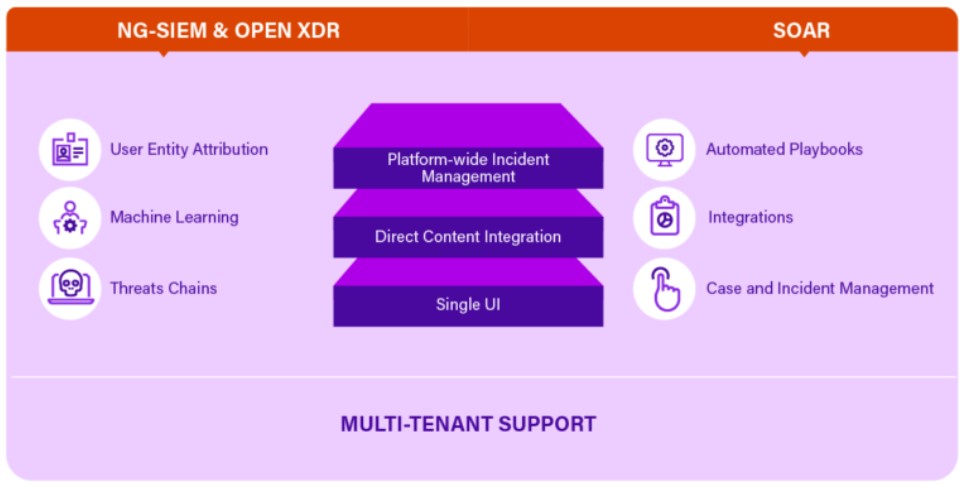
Simplify detection and response with Securonix SOAR
L1 Analysts like SOCrates face a barrage of alerts daily and are bogged down by complex environments that require him to context switch to investigate and respond to threats. Rapid response is essential to lower organizational risk but analysts like SOCrates are struggling to keep pace with attacks.
SOAR can alleviate these pain points, however, not all SOAR offerings are created equal. A standalone or OEM SOAR, for example, would allow SOCrates to automate some workflows, but he would still have to toggle between multiple screens and replicate data across multiple systems during investigations. He longs for the day when he can detect, investigate, and respond to a threat in a single UI.
In order to remediate a threat SOCrates first needs to be able to understand user/ entity attribution across multiple alerts. He is bombarded by disparate alerts and manually has to stitch them together and attribute them to a single entity. Without this context, remediation will continue to be a manual process. He needs a solution that can streamline the entire threat detection and response process into a seamless workflow.
How Securonix SOAR can help SOCrates
Securonix is innovating in the SOAR market by offering a SOAR that is built-in to the SIEM, not bolted on, and shares a single code base with our Next-Gen SIEM. Our integrated SOAR offering aligns content for detection and response, underlying data models, and workflows so Socrates can rely on the automation to be up-to-date and precise. Since our SOAR playbook actions are embedded in the SIEM workflow, SOCrates can use a single platform and UI to streamline the end-to-end incident response cycle. By adding SOAR to your Securonix SIEM deployment you can reduce resource needs and eliminate human touchpoints which allow analysts like SOCrates to become more efficient.
Conclusion
Security professionals like SOCrates deal with ever-evolving threats everyday. Organizations need solutions that complement their security team’s knowledge and skills and minimize the tedious tasks required to detect and mitigate threats.
Securonix is continuously working with some of the world’s largest security organizations to create more autonomous innovations designed to up-level your security operations. As trusted partners, we free you from redundant and time-consuming tasks so that you can focus on what you are really good at… mitigating potential and real threats. Through these recent innovations, we strive to deliver new capabilities and content that empowers security teams to quickly detect, analyze, and act on the threats that can directly impact your bottom line.
Request a demo and speak with our experts to learn more.







