- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Labs
Recently Madhukar Raina, a Senior Threat Hunter at Securonix Threat Labs wrote SysmonSimulator, a tool that provides instructions on how to generate Sysmon event logs for simulating attack techniques. With SysmonSimulator, threat detection teams can now test EDR detections and correlation rules. The source code is available on Github and can be modified for specific requirements.
Building SysmonSimulator
The idea for building SysmonSimulator came to Madhukar when he found that when testing use cases, he often needed to manually create raw events for SIEM rule correlation. This would require him to search for multiple tools to generate log data for different attack scenarios. It took him time to identify the tools and create the log data, an activity that needed to be repeated for each series of tests. To reduce the manual work and automate the process, he built SysmonSimulator and shared it for threat hunters to use in their tests.
“The best thing about SysmonSimulator is that it can be used to test SIEMs and EDRs without introducing anything malicious into the system. This simplifies the process of rule validation when you edit rules on your SIEMs and need to generate logs to validate the alerts. It is really easy to simulate the logs and you save a lot of time in terms of finding attack tools to generate logs for different activities,” says Madhukar.
SysmonSimulator gives analysts a way to simulate attack techniques to test the detection solutions. In this exercise, Madhukar uses Sysmon as an example and demonstrates how to simulate event IDs logged by Sysmon to show what kind of logs are generated and why it is important from the monitoring perspective.
What is Sysmon?
Sysmon is an open source host-level monitoring and tracing tool developed by Mark Russinovich and contributors from Microsoft. It fetches information about the operations performed on the system and logs them into the Windows Event Viewer. Threat detection teams get more information in addition to the existing Windows events to better understand detections for different attack scenarios.
Madhukar chose Sysmon for the exercise as it is an open-source tool and used by many organizations to monitor the system activities and to build use cases in the lab environments. It also provides an option to generate more fine-tuned and specific event logging using a set of XML rules, which can be modified as needed in its XML config file by the user.
Getting Started With SysmonSimulator
“Understanding Sysmon Events using SysmonSimulator” explains how to install and configure Sysmon and provides step-by-step guidance on using SysmonSimulator to simulate logs for tests.
For this exercise, Madhukar configured SysmonSimulator to perform event simulations for important Windows events as follows:
– Process Events: Process Creation, Process Termination, Process Access, Process Image Tampering
– File Events: File Create, File Create Time Change, File Stream Creation Hash, File Delete, File Delete Detected
– Named Pipes Events: Named Pipe Creation, Named Pipe Connect events
– Registry Actions: Registry Object create and delete, Value Set, Key and Value Rename
– Image/Module Loading and Create Remote Thread
– Network Connections and DNS Query events
– Raw Access Read
– Clipboard Capture
It also provides instructions to simulate the WMI Events. Windows Management Instrumentation (WIMI) Event Subscription is a documented technique in the MITRE ATT&CK framework. Because of its ubiquitous nature, WMI is exploited by threat actors to achieve persistence through installing event filters, providers, consumers, and bindings that execute code when a defined event occurs to establish persistence on a system.
Using SysmonSimulator
SysmonSimulator can be handy for threat hunters. “If a detection engineer wants to understand each event individually, it can be done by specifying the -eid parameter (SysmonSimulator.exe -eid <event_id>). An option to simulate all the event logs at once using the parameter -all (SysmonSimulator.exe -all) has been added in the latest release. Since the source code is available, anyone can modify the child process to be created/terminated, including selecting the remote process to be accessed, parameters for DNS query and network connections,” says Madhukar.
To access this start with the help section of SysmonSimulator:
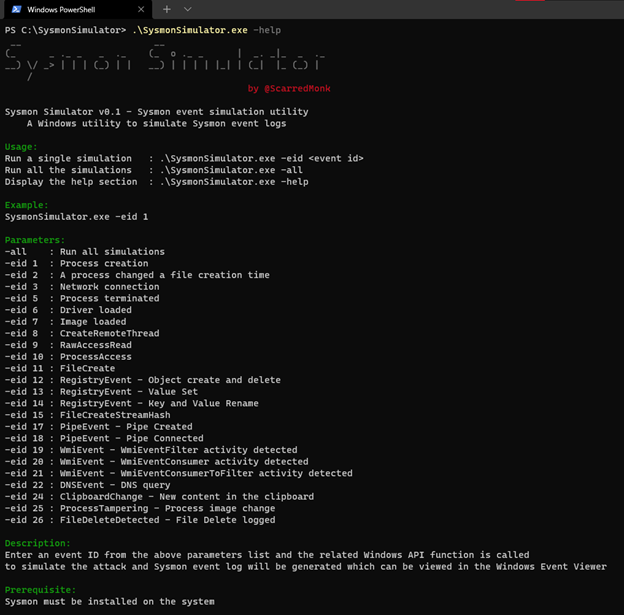
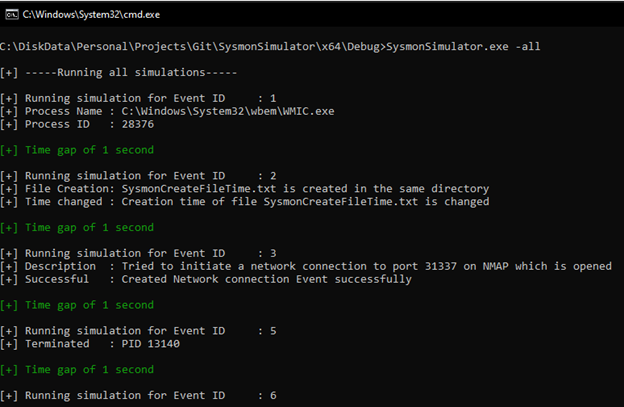
If you choose the -all parameter, it performs the simulations for all events automatically as shown in the below screenshot:
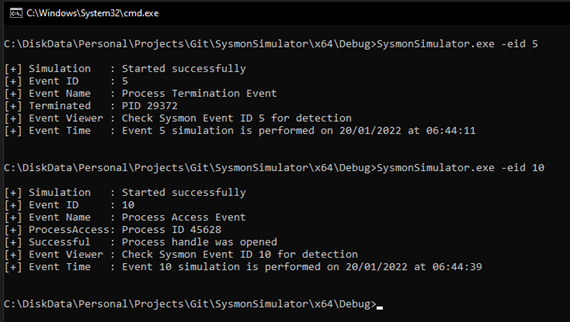
You can execute the individual event simulations as shown below:
Read more about using SysmonSimulator for a detailed step-by-step guide on how to get started. This post will be helpful for those who want to understand in depth how Sysmon detects different types of events in Windows and how those attacks can be simulated using different Win32 API functions.
Securonix Threat Labs leverages data science, detection engineering, threat research and threat hunting to stay at the forefront of emerging threats. Closely integrated with the product team, Securonix Threat Labs also publishes up-to-date IoCs and threat hunting queries on Sigma, allowing security teams to tap into a vast community of collective defense and stay current on the latest threat research.







