- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Why being breached is a spectrum and the importance of post-hoc detection
By Oliver Rochford, Security Evangelist, Securonix
Data breaches are often presented in hindsight as a series of events leading up to a single pivotal event such as the public leaking of sensitive files. The problem is that superimposing a tidy narrative onto an attack can help make it easier to understand, especially for a broader audience beyond the security organization. But in reality, modern cyber attacks frequently occur and evolve over indeterminate timeframes, with dormant, active, and hyperactive phases, multiple changes in tactics, techniques, and procedures (TPPs), and shifting objectives.
Let’s consider a current active threat as an example: initial access brokers (IAB). IABs acquire compromised authentication credentials to sell them to other cybercriminals, either by purchasing them from freelancers or by directly harvesting these themselves through traditional cyber-attack techniques like drive-by exploitation or phishing.
If you have been compromised by an IAB, you have been breached. But the breach lies dormant — the risk is not yet fully realized — and has not been leveraged for any particular purpose. The IAB might sell access to your systems and networks to a cybercriminal group that installs a crypto miner to semi-harmlessly run up your electricity bill in the background while generating valuable digital currency for the attackers. Or they might sell your credentials to one of the many ransomware operators that have been known to buy stolen credentials to launch a devastating cyber extortion attack that cripples your business. Both scenarios begin with the same initial access, but the risk they pose and the impact they can have are entirely different.
IABs represent only one small component of a cyber attack. Threats generally evolve in fits and starts to constantly move the goalposts required to successfully detect and respond to a compromise in progress. Malware also does not remain static and is reconfigurable, allowing payload modules to be swapped out pretty much on the fly. Some of today’s more sophisticated attackers are also very elusive and frequently change their tactics so that IOCs are only reused by threat actors for brief periods of time or against a limited number of targets. For example, the command and control infrastructure that was used when an organization was initially breached, including IP addresses and domain names, will likely have gone through multiple iterations by the time you first detect a threat actor.
IOCs Are Often Artifacts of Another Time at the Wrong Time
Imagine being on the lookout for marauding raiders armed with swords and bows on horseback in the twenty-first century, instead of searching for people armed with rifles, and you get the idea. If you don’t have the correct data for that time period, the IOCs are at most of cyber-archeological value. They are essentially artifacts out of another time and are out-of-place anachronisms if not correlated with data from the correct corresponding timeframe. For security teams, this means that not only do most IOCs have an expiration date, but they are also only actually effective for a limited and specific period of time.
The problem is that most real-time detection approaches only protect you from future threats.
Most importantly, the majority of IOCs are only publicly disclosed to end-users after they have been discovered being used for an attack. This results in a signal delay — between when the original attack traffic was seen, and when indicators become widely known and available for detection.
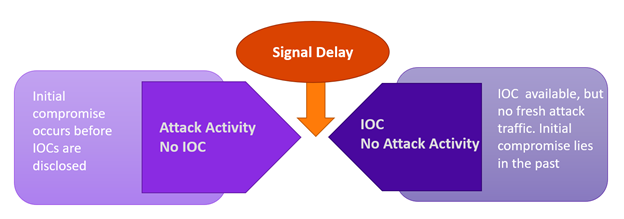
The problem is that most real-time detection approaches only protect you from future threats. They require fresh attack traffic and need to catch an attacker in the act.
In an ideal world, you would know that the domain sending a phishing email is malicious and that the file hash is associated with known malware. Our detection technology would then detect these malicious emails and block them before they even reach the intended victim.
In the real world, the domain that sent the phishing request was taken offline 15 days ago, and there never was a file hash as the attack was fileless using a maliciously-crafted office document.
The shortcomings of relying on “known-known” indicators are well known and we have come up with a number of different approaches to compensate for them, for example through proactive threat hunting, where a human analyst delves into any available security telemetry to discover any nascent compromise. And to minimize threat actor dwell time and reduce the mean time to respond, larger organizations have also conducted cyber rapid response.
Cyber rapid response and threat hunting are powerful when done well. But both require three things that many organizations have in short supply: expertise, time, and long-term historical data.
Retroactive Post-Hoc Detection
Being breached is not a one-off event as there are many different ways that a data breach can unfold. More importantly, you can be a little bit or massively breached — an attacker may have only gained a foothold on an unimportant system, or they may have infiltrated deeper into your networks and systems to install backdoors and gained several credentials with privileged access, making them hard to kick out cleanly even if we do discover them.
The fact that most IOCs are already stale when they become known means that the traditional approach of relying on future attack activity has always been fundamentally flawed. But we were stuck with it because we couldn’t gather, keep, and review sufficient historical data.
Detecting threats and threat activity is the foundation of all incident response and is still one of the most critical areas to impact the mean time to respond (MTTR). But real-time detection is limited to a forward-looking view, even though most of the available data is historical in nature.
What we need is longer-term data retention and a way to sweep through historical event data for IOCs and TTPs as they become available. We need to be able to do this whenever new data becomes available. With this approach, you can look for those IOCs in the time window when they were actually being used. The earlier that we can pinpoint a threat, and the further back we can identify its activity, the better. And that does not just depend on a view of the future, but also on understanding past activity.
This is why Securonix introduced Autonomous Threat Sweeper (ATS) to the market in 2021 to help organizations improve their security posture. We’ve combined the best of both worlds — human analyst-driven threat intelligence curation, threat hunting, and detection engineering together with automated post-hoc detection over vast amounts of historical event data in a security data lake.
While not a silver bullet, ATS is still potent ammunition for security analysts. The fusion of timely, up-to-date, and operationalized threat intelligence with post-hoc detection is one of the measures that will shift the balance back in the defender’s favor by reducing the window of opportunity that attackers have to complete their objective.
Learn more about how Autonomous Threat Sweeper helps organizations with fast and effective cyber rapid response.