- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Authors: Brian Robertson, Senior Product Marketing Manager & Solay Adaikkalavan, Director of Product Management
Every organization has experts who are masters of their environment. These are the people that all other analysts look to when they hit a wall investigating an incident. During investigations, these experts leverage vast amounts of knowledge they accumulated over the years. Additionally to the in-house experts, collaboration tools like Slack or Microsoft OneDrive, Confluence, Google Sheets, etc. contain a wealth of insights derived through discussions within the organization. We define tribal knowledge as the combination of longtime security experts and the knowledge within your systems. Tribal knowledge often holds the key to understanding if the incident is in fact a threat, how it got there, and what impact it had or will have. In other words, this tribal knowledge is irreplaceable.
Unfortunately, cybersecurity experts are in high demand and often leave for new opportunities. When the experts leave, they take this wealth of historical knowledge that they curated over the years with them. When that role is backfilled it takes time for the new team member to understand the environment and how certain types of incidents were addressed.
To compound the loss of experts, collaboration tools also contain important historical information but it’s challenging to collect and use this data for investigations. Solutions like Slack and Teams do a great job of connecting team members to share information at a certain point in time. These solutions however, often lack an effective way to search for details within conversations from the past.
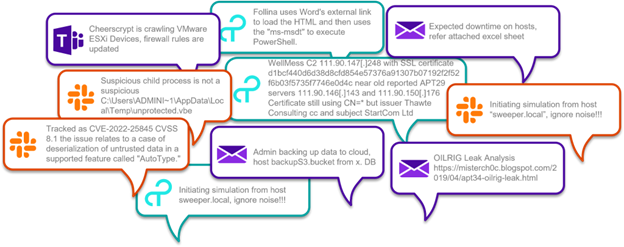
Often Security Operations teams use multiple tools to convey information during an investigation. The information is often not retained for long periods of time or is difficult to find during future investigations.
To use an analogy, think about using an application like WhatsApp to communicate with your neighbors. Within the app there are conversations around recommendations for plumbers, electricians, dog walkers, babysitters, landscapers, etc. When messages about recommended services are being made, you pay little attention, because you don’t need those services right now. Perhaps, one day later, you have a plumbing issue and you do not have a regular plumber to rely on. You would want a plumber who is recommended by people you know, such as your neighbors. You have two choices:
- Scroll through all the conversation feeds looking for recommended plumbers.
- Ask the community again which plumbers they recommend, hoping that the people who responded previously will respond again.
As you can imagine both approaches take a good amount of time. While you are performing either of these tasks the plumbing issue could be causing more damage to your house.
One of the things that can delay an investigation is for an analyst to have to go search for the necessary details about entities within an incident. Often events are discussed using collaboration tools. But like the analogy above when certain entities are discussed you may not make note of them because the details are not needed at the time. However, a few weeks later that particular entity comes up in an investigation and you recall seeing something about it in a past message. Now you have to go and search a bunch of conversations from weeks ago to find that information knowing even the smallest detail can provide the key to an investigation next steps. With a cumbersome manual process it could take a lot of time to find that detail or you may just give up.
Organizations need an effective way to retain and bring this tribal knowledge to the forefront of an investigation.
Stepping up to a new approach
Recently Securonix introduced a new way of addressing issues of missing or hard to find tribal knowledge with a product called Securonix Investigate. Securonix Investigate is designed to expedite investigation and response by delivering on-demand context and enabling analysts’ collaboration. If you are curious as to how the on-demand context works within Securonix Investigate see the blog we wrote.
The analyst collaboration capabilities of Securonix Investigate allows you to communicate details across the IT and security team. You can quickly and easily convey information about the type and urgency of an incident. This information helps you to identify patterns and improve your ability to react to data. It allows you to annotate, document and share observations during an investigation. Through the process of collaboration, organizations can document insights and findings, or “tribal knowledge”, that can be shared across the team and leveraged against future investigations.
Abstract details from conversations
Securonix Investigate allows you to instantly fetch a wealth of tribal knowledge contained within your collaboration tools like Slack and Confluence. The conversations that occur between team members contain critical details about entities that may be under investigation. Securonix Investigate makes it easier to abstract those insights within collaboration tool conversations when conducting an investigation. This streamlined process reduces the need to manually search through multiple tools. Securonix Investigate allows your team to more effectively take advantage of information about specific entities by pulling details into the investigation that may have been overlooked in the past.
Annotate your investigation at a click of a button
Securonix Investigate allows you to directly connect insight and information that traditionally was only located in the heads of your top analysts to incidents under investigation. The process starts with an entity under investigation such as a user, IP address or URL. With a single click security analysts can pull up the Annotate window that retains the entity information, but also allows your experts to make notes and assign the annotation to a dedicated communication channel. If that entity is under investigation in the future the information annotated will be displayed in the investigation window.
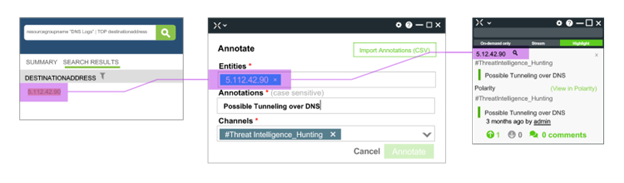
The process of annotation retains the entity identifier, allowing analysts to add comments and communicate details across dedicated communication channels. When that entity is part of future investigations the comments will be instantly added to the new investigation.
Share information across dedicated teams
In the process outlined above we mentioned dedicated communication channels. Dedicated communication channels let you share information either across the entire team or within specific trusted group channels. These messages can also be integrated with the instant messenger and collaboration tools already in use like Slack.
For example, you are performing penetration testing and need to share specific information within the red team, share other information within the blue team, and share certain information within both the red and blue team that makes up the purple team. By creating dedicated communication channels information and key insights can be shared within each individual trusted group.
You can set up groups for essentially any topic that you can imagine. Examples include critical IOCs, specific departments, threat research, identified vulnerabilities, watchlists, whitelists, etc. Each channel can be color coded to highlight certain high-priority channels. This color coding also makes it easy to recognize patterns.
Retain knowledge to up-level your team
As you go through the process of sharing information across teams, you are creating a proven set of findings, insights and knowledge about incidents investigated in the past. This information is not only available to the author, but it becomes available across the team. This harnessed tribal knowledge provides the foundation to up-level your team by transferring expertise from senior to lower-tier analysts. Additionally, in the future when similar incidents present themselves the team can make consistent decisions based on past learnings to speed mitigation.
Unleash the power of tribal knowledge
Securonix Investigate gives organizations a better way to develop, organize and retain tribal knowledge. By improving analyst collaboration across the team, insights and ideas can be quickly shared during an investigation. That knowledge is then stored and can be easily recalled during future investigations. It is this readily available curated knowledge that empowers all security analysts to be more informed and more efficient when investigating incidents that have the potential to significantly impact your business.
To See Securonix Investigate in action, view the online demo here!







