- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov and Harshvardhan Parashar, Securonix Threat Research Team
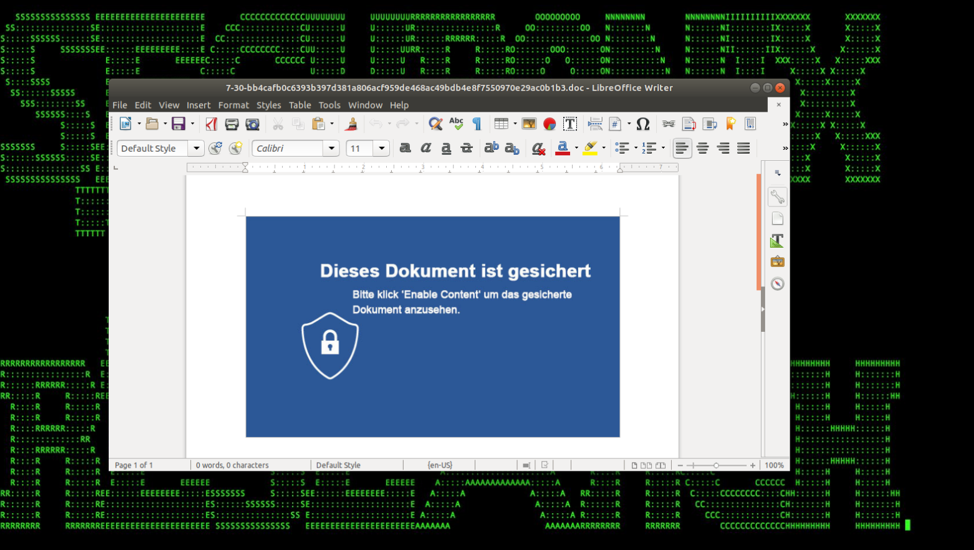 Figure 1: Document with Malicious VBA Macro used in Osiris Germany Campaign
Figure 1: Document with Malicious VBA Macro used in Osiris Germany Campaign
Introduction
The KRONOS malware was first discovered in June 2014 as a Banker Trojan available for purchase in a Russian underground forum for $7,000 [1]. After staying dormant for few years, a new variant of KRONOS, known as Osiris, was discovered in July 2018, with three distinct campaigns targeting Germany, Japan, and Poland [2]. The new variant contains features like TOR network command and control (C2), keylogging, and remote control via VNC along with older features like form grabbing and web-injection [3].
The Securonix Threat Research team has been actively investigating and closely monitoring these high-profile malicious attacks to help our customers prevent, detect, and mitigate the attacks.
Summary
Here is a summary of some of the key details about the KRONOS/ Osiris attacks:
Infiltration vector(s): The primary infiltration vector used by KRONOS/Osiris malware is phishing email campaigns containing specially crafted Microsoft Word documents/RTF attachments with macro/OLE content that cause malicious obfuscated VB stagers to be dropped and executed. In many scenarios the malware is distributed using exploit kits like RIG EK.
The malicious document exploits a well-known buffer overflow vulnerability in Microsoft Office Equation Editor Component—CVE-2017-11882—which allows the attacker to perform arbitrary code execution [4][5].
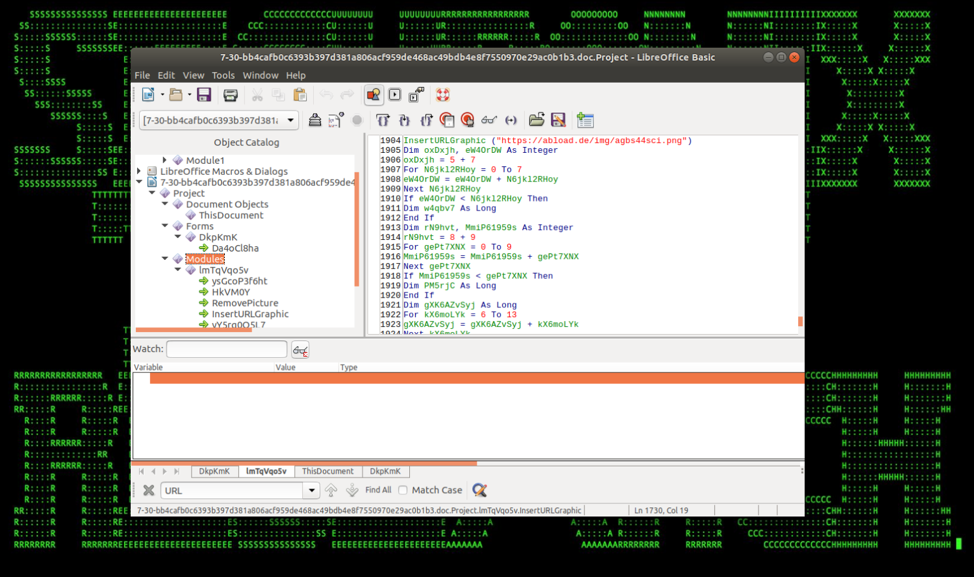 Figure 2: Malicious VBA Script to Download the Latest KRONOS
Figure 2: Malicious VBA Script to Download the Latest KRONOS
C2: The new KRONOS/Osiris malware extensively uses TOR anonymizing network for its command and control. The malicious payload spawns multiple processes named “tor.exe” and connects to multiple distinct host (tor nodes) located in different countries. Figure 3 shows the different TOR nodes the infected system connects to.
Some versions also support remote control through VNC through a modified LibVNCServer library [3].
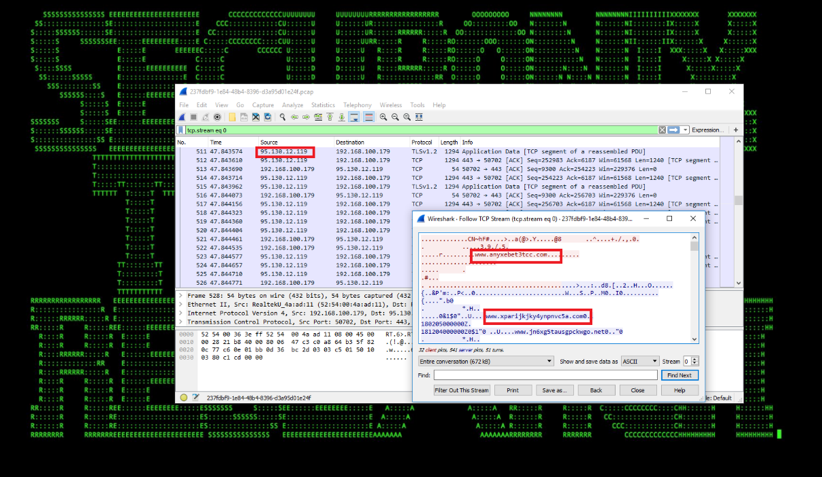 Figure 3: Traffic to TOR Nodes Generated by the KRONOS/Osiris Executable
Figure 3: Traffic to TOR Nodes Generated by the KRONOS/Osiris Executable
Defense Evasion: KRONOS/Osiris uses Anti-VM or Anti-Sandbox mechanisms to evade detection or analysis in a virtual environment [3]. In many cases, the malware also modifies the internet zones settings using registry and lowers the security settings of Firefox to evade being blocked while using man-in-browser attack to webinject into banking websites.
Persistence: In some cases, the malware copies itself to the C:\Users\%\AppData\Roaming\<Generated_GUID>\ along with several DLLs, executables for TOR, and image files. It also writes to the Start Menu and creates a shortcut in the Startup folder “C:\Users\%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”
Collection: KRONOS/Osiris steals sensitive data from multiple sources. The primary method of collection is through a man-in-browser attack to webinject malicious script into banking websites and grabbing form values. The malware downloads the latest configurations (specifies the location of script injection in the website) of target banking websites from the C2 [6].
Observed Artifacts
Hash Values (SHA-256)
22d5ed604be99b7702a2f69fb412bd8b95f36f0a637951a8db35b46147180c3d
3eb389ea6d4882b0d4a613dba89a04f4c454448ff7a60a282986bdded6750741
4af17e81e9badf3d03572e808e0a881f6c61969157052903cd68962b9e084177
b4266752945011bc04f162ea53d4d78dd804dce5bb411c8dcc09fcf2e3ca3b5c
75769405a034d7db09b54b9e227722692a106dd5dc4acf48a60c70cbdc8e3f12
bb4cafb0c6393b397d381a806acf959de468ac49bdb4e8f7550970e29ac0b1b3
4af17e81e9badf3d03572e808e0a881f6c61969157052903cd68962b9e084177
9806d1b664c73712bc029e880543dfa013fdd128dd33682c2cfe5ad24de075b9
3bd4b8caf9ae975bd41dbee1f1719cf7be3efa4f52b8768aba30ba9a40569008
bb308bf53944e0c7c74695095169363d1323fe9ce6c6117feda2ee429ebf530d
Behaviors – KRONOS/Osiris Endpoint Activity
- The KRONOS/Osiris campaign exploits a well-known buffer overflow vulnerability in Microsoft office—CVE-2017-11882. The vulnerability resides in the Equation Editor Component which, when used, runs as its own process (eqnedt32.exe). Because of the way it was implemented, it doesn’t support Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) [7][5]. A malicious document exploits the vulnerability to execute a command to download the latest version of KRONOS. As a result, unusual processes spawned by the Microsoft Equation Editor process (eqnedt32.exe) or the process making a network connection could indicate malicious activity associated with KRONOS.
- The malware performs DLL injection using LoadLibrary API call to inject DLL into a running “explorer.exe” and “firefox” processes (see Figure 4).
- The malware also disables the Firefox security settings and changes the internet zone settings to allow Web injection by modifying the registry values “HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\3”.
- KRONOS connects to multiple TOR nodes in distinct geolocations to download the configuration to be used for web injection in different banking websites.
Detection – Sample Securonix Spotter Search Queries
Some sample Securonix Spotter search queries to assist with detection of the existing infections:
ETDR Process Monitoring (Process Hash Conditions)
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND
(customstring3=22d5ed604be99b7702a2f69fb412bd8b95f36f0a637951a8db35b46147180c3d or
customstring3=3eb389ea6d4882b0d4a613dba89a04f4c454448ff7a60a282986bdded6750741 or
customstring3=or4af17e81e9badf3d03572e808e0a881f6c61969157052903cd68962b9e084177 or
customstring3=b4266752945011bc04f162ea53d4d78dd804dce5bb411c8dcc09fcf2e3ca3b5c or
customstring3=75769405a034d7db09b54b9e227722692a106dd5dc4acf48a60c70cbdc8e3f12 or
customstring3=bb4cafb0c6393b397d381a806acf959de468ac49bdb4e8f7550970e29ac0b1b3 or
customstring3=4af17e81e9badf3d03572e808e0a881f6c61969157052903cd68962b9e084177 or
customstring3=9806d1b664c73712bc029e880543dfa013fdd128dd33682c2cfe5ad24de075b9 or
customstring3=3bd4b8caf9ae975bd41dbee1f1719cf7be3efa4f52b8768aba30ba9a40569008 or
customstring3=bb308bf53944e0c7c74695095169363d1323fe9ce6c6117feda2ee429ebf530d)
ETDR Process Monitoring (Trivial Process Name Conditions)
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND (sourceprocessname contains EQNEDT32.EXE and (destinationprocessname is NOT NULL or destinationprocessname!=’-’))
ETDR Process Monitoring (Process Name, Network Connection Conditions {Sysmon})
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND baseeventid = 3 AND destinationprocessname contains EQNEDT32.EXE
ETDR Process Monitoring (Process Name, Network Connection Conditions {Sysmon})
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND baseeventid = 3 AND destinationprocessname contains EQNEDT32.EXE
ETDR Process Monitoring (CommandLine Conditions {Sysmon})
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND destinationprocessname contains EQNEDT32.EXE and customstring1 CONTAINS “/stext” OR customstring1 CONTAINS “/scomma”
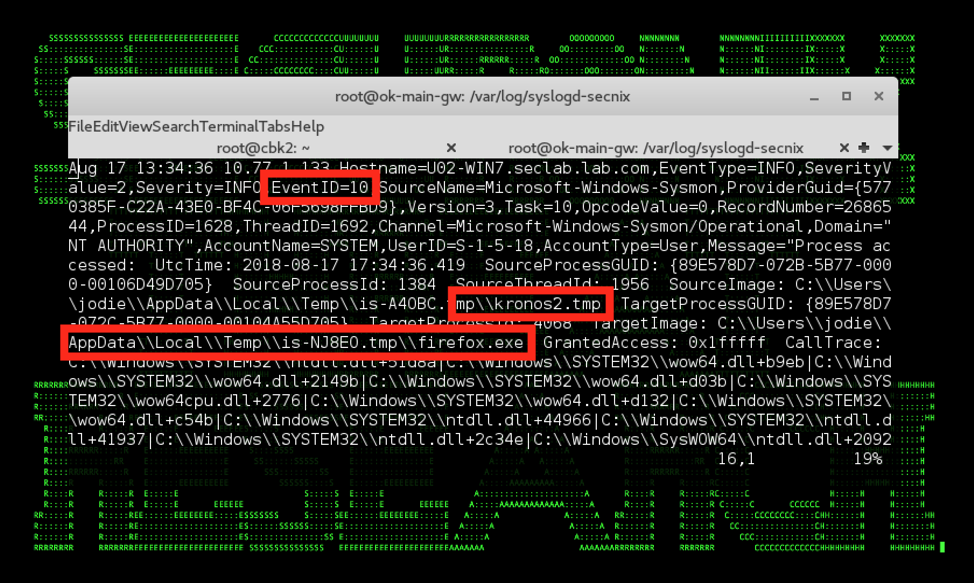 Figure 4: KRONOS/Osiris in Endpoint Logs – Firefox.exe Process Migration
Figure 4: KRONOS/Osiris in Endpoint Logs – Firefox.exe Process Migration
Securonix Detection – Some Examples of Securonix Predictive Indicators
Below are some high-level examples of the relevant Securonix behavior analytics/predictive indicators that could help detect this and potentially other future variants of the KRONOS/Osiris threat in your environment. In addition, Figure 5 shows a practical example of detection of the KRONOS/Osiris attacks using Securonix.
Suspicious Process/Service Activity Anomalies
- Suspicious Process Activity – Targeted – Potential Phishing Sequence II Malicious Payload Open Browser Modality Analytic
- Suspicious Process Activity – Rare Parent-Child Relationship For Host Analytic
- Suspicious Process Activity – Process Execution From Previously Unseen File Paths Analytic
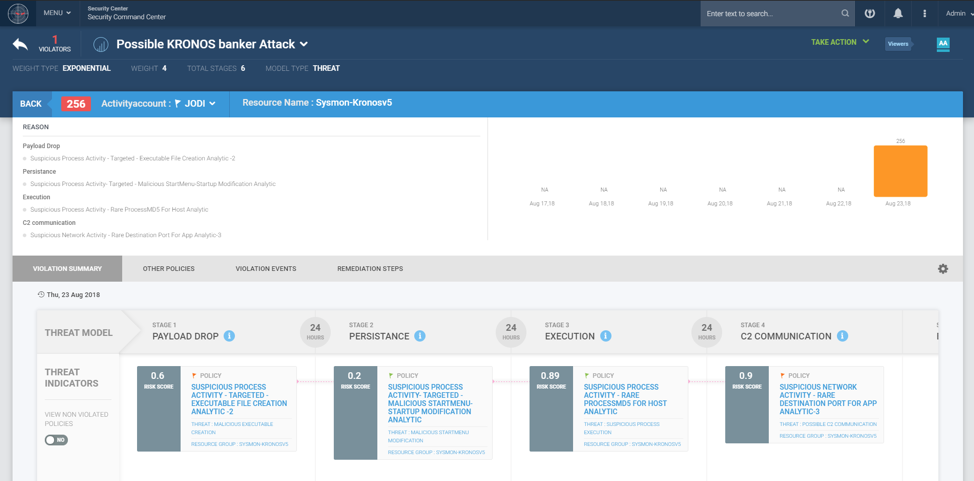 Figure 5: KRONOS/Osiris Securonix Detection in Practice Using Security Analytics
Figure 5: KRONOS/Osiris Securonix Detection in Practice Using Security Analytics
- Suspicious Proxy Activity – Targeted – Traffic Threat Intel TOR Connection Analytic
- Suspicious Proxy Activity – Traffic To DGA Domains Analytic
- Suspicious Process Activity – Targeted – MS Equation Editor Spawning a Child Process
And a number of other Securonix behavioral analytics/predictive indicators that could help detect such attacks, including PXY-PAN5-TAN, DNS-IPB1-TPN, EDR-SYM41-RUN, EDR-SYM43-RUN, EDR-SYM44-RUN, EDR-SYM38-ERI, and EDR-SYM28-RUN.
Mitigation and Prevention – Securonix Recommendations
Here are some of the Securonix recommendations to help customers prevent and/or mitigate the attack:
- Patch operating systems, software firmware on your infrastructure and especially the Microsoft Office products as KRONOS exploits a well-known Microsoft Office vulnerability (refer https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882), and consider leveraging a centralized patch management system.
- Implement end-user security training program since end-users are the primary phishing targets and it is important for them to be aware of the threat of banking Trojan and how it occurs.
- Block all the connections to the known TOR nodes on the proxy and firewall.
References
[1] Etay Maor, The Father of Zeus: Kronos Malware Discovered. July 11, 2014. https://securityintelligence.com/the-father-of-zeus-kronos-malware-discovered/. Last Accessed: August 8, 2018
[2] Proofpoint, Kronos Reborn. July 24, 2018. https://www.proofpoint.com/us/threat-insight/post/kronos-reborn. Last Accessed: August 8, 2018
[3] Yaroslav Harakhavik and Nikita Fokin. Osiris: An Enhanced Banking Trojan. July 31, 2018. https://research.checkpoint.com/osiris-enhanced-banking-trojan/. Last Accessed: August 8, 2018
[4] Embedi. Skeleton in the closet. MS Office vulnerability you didn’t know about. 14 November, 2017. https://embedi.com/blog/skeleton-closet-ms-office-vulnerability-you-didnt-know-about/. Last Accessed: August 8, 2018
[5] Microsoft. CVE-2017-11882 | Microsoft Office Memory Corruption Vulnerability. November 29, 2017. https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882. Last Accessed: August 8, 2018
[6] Malwarebytes Labs. Inside the Kronos malware – part 2. August 29, 2017. https://blog.malwarebytes.com/cybercrime/2017/08/inside-kronos-malware-p2/. Last Accessed: August 8, 2018
[7] Yanhui Jia, Taojie Wang and Zhibin Zhang. Analysis of CVE-2017-11882 Exploit in the Wild. https://researchcenter.paloaltonetworks.com/2017/12/unit42-analysis-of-cve-2017-11882-exploit-in-the-wild/. Last Accessed: August 8, 2018







