- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Securonix Threat Research Security Advisory
Threat Actors are Exploiting the Recent CrowdStrike Outage in an Effort to Deploy Malware and to Stage eCrime Operations
By Securonix Threat Research: Den Iuzvyk, Tim Peck
tldr:
Threat actors have been known to exploit large-scale IT operational issues. Because of this, we’ve witnessed a large uptick in eCrime-related scam operations, phishing attacks, and malware being leveraged in the wake of the CrowdStrike induced outage.

It’s no surprise that threat actors have a tendency to ride global trends and hype to stage their malicious operations. For example, back in 2020 during the pandemic, we were witness to a huge uptick in COVID-19 related cyberattacks ranging from phishing emails promoting fake statistics websites, to actual malware being deployed on the host.
Last week, on July 19, 2024, a critical issue was discovered in a specific content update for the CrowdStrike Falcon sensor affecting Windows operating systems which caused them to crash and to become stuck in a boot-loop. As CrowdStrike Falcon is a massively popular EDR solution, the issue affected critical servers and endpoints causing a world-wide outage. Although a fix has since been deployed and recovery operations are underway, threat actors are eager to ride the hype-train.
While operations at Securonix were unaffected, we will continue to provide information which may relate to assist as the recovery phase is underway. In this report we’ll cover some of the attack vectors and malware that the bad guys are using in light of the recent CrowdStrike incident.
Phishing emails
According to recent data, in general phishing emails are still the number one attack vector that threat actors use in an attempt to compromise systems.
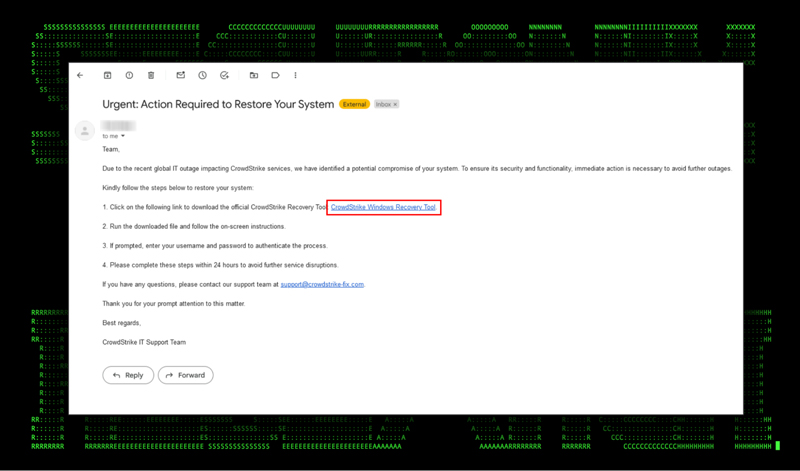
IT support scams are a common form of phishing, often targeting IT staff members or endpoint users. These emails usually contain urgent requests from supposed IT personnel or external technical teams, sometimes posing as business partners, with instructions to patch or mitigate a critical system issue.
In the recent example involving CrowdStrike, IT support scam emails could easily be mistaken for legitimate requests. Here is an example of this type of phishing email:
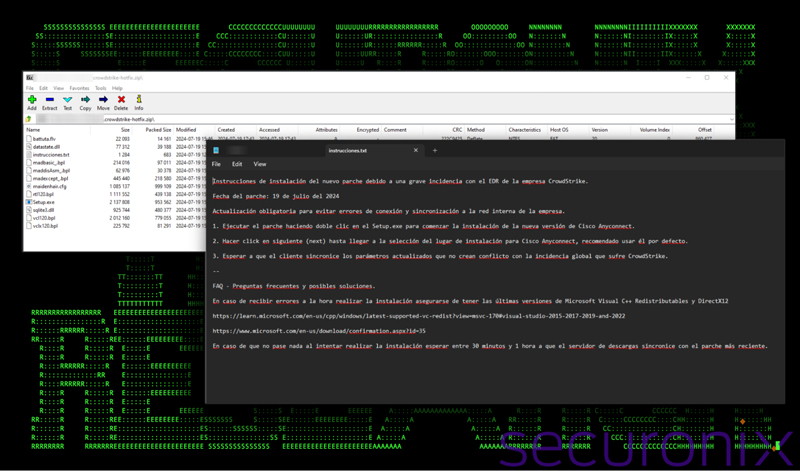
Figure 1: CrowdStrike IT support scam email
Mitigation strategies:
Always exercise extra vigilance when it comes to properly vetting emails which contain an action or request. Some things to look out for include:
- Ensure that the email matches the official domain of the company. Some email clients will notify you via a message or banner indicating that the email was from an “external” source. Phishing emails often use addresses that are similar but slightly altered.
- Phishing emails often use generic salutations like “Dear Customer” instead of addressing you by name.
- Emails that create a sense of urgency or fear, such as “immediate action required” or “your account will be suspended,” are common tactics used by scammers.
- Hover over links to see the actual URL before clicking. Avoid downloading or opening unexpected attachments.
- Official communications from reputable companies typically do not contain spelling mistakes or poor grammar.
- Look for inconsistencies in branding, such as logos, fonts, and design elements that don’t match the company’s usual style.
- IT scams often include attachments, or links to external files that can install malware on your device. Only open attachments from trusted sources.
- If the email asks you to perform actions outside your usual duties, especially related to IT, verify the request with the sender through a different (internal) communication channel.
Malicious domains
Despite the fact that the outage started just a few days ago, malicious threat actors swiftly began registering deceptive domains to deploy phishing emails, create scam websites, and host malware. Fortunately, CrowdStrike, along with various security research teams, have identified many of these malicious domains.
Below is an example of one of the recently registered and active malicious websites.
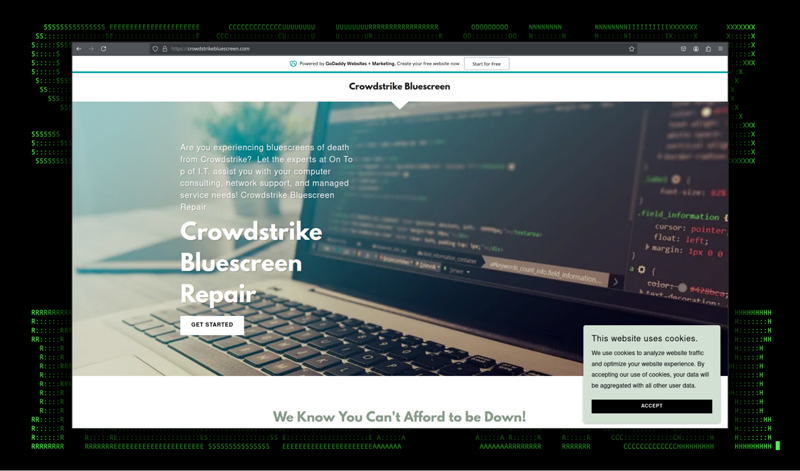
Figure 2: Newly registered and active CrowdStrike “help” website
A growing number of the identified malicious websites are listed in the IoC section towards the end of this report.
Mitigation strategies:
By implementing these strategies, organizations can better protect themselves against threats associated with malicious domains.
- Regularly monitor domain registrations and identify suspicious or spoofed domains related to your organization.
- Implement advanced email filtering solutions to detect and block phishing emails that originate from these malicious domains.
- Use web filtering solutions to block access to known malicious domains and websites, preventing users from inadvertently visiting harmful sites.
- Participate in threat intelligence sharing networks to stay updated on newly identified malicious domains and other emerging threats.
- Conduct regular training sessions for employees to recognize phishing attempts and the dangers of visiting suspicious websites.
Identified malware
Some samples of legitimate malware have already been caught being distributed primarily through phishing emails. In one such example identified by CrowdStrike, HijackLoader was caught targeting LATAM countries masquerading as a required “hotfix”. The loader was designed to silently load Remcos, a remote access trojan (RAT) which would have allowed the attacker full access to the victim’s system.
According to the report, a ZIP archive named “crowdstrike-hotfix.zip” was recently uploaded to an online malware-scanning service by a submitter based in Mexico. The archive includes Spanish-language instructions posing as a utility for automating recovery from the recent content update issue. Users are prompted to run Setup.exe to initiate the “patch” installation process.

When the victim extracts the archive, and executes Setup.exe, it will load and execute the HijackLoader’s initial attack chain from within the madBasic_.bpl file via DLL search-order hijacking. This then executes the HijackLoader config file called maidenhair.cfg which allows the Remcos payload to execute and beacon out to a C2 server at 213.5.130[.]58[:]433.
Wrapping up…
As with any large-scale event, threat actors waste no time setting up their infrastructure and malicious campaigns. It is critical for organizations to exercise extreme caution when dealing with these potential threats. As our threat research team continues to monitor the situation, Securonix customers can take advantage of the threat hunting queries below to scan for signs of potential infection.
Threat hunting queries
(remove square “[ ]” brackets and modify the functionality to suit your environment):
- index=activity AND (rg_functionality=”Next Generation Firewall” OR rg_functionality=”Web Proxy”) AND destinationhostname NOT NULL AND (destinationhostname CONTAINS “crowdstrikedoomsday[.]com” OR destinationhostname CONTAINS “winsstrike[.]com” OR destinationhostname CONTAINS “crowdstrike-cloudtrail-storage-bb-126d5e[.]s3[.]us-west-1[.]amazonaws[.]com” OR destinationhostname CONTAINS “crowdstrikecommuication[.]app” OR destinationhostname CONTAINS “failstrike..com” OR destinationhostname CONTAINS “fix-crowdstrike-bsod[.]com” OR destinationhostname CONTAINS “crowdstrike[.]black” OR destinationhostname CONTAINS “crowdstrikedown[.]site” OR destinationhostname CONTAINS “crowdstrikeoopsie[.]com” OR destinationhostname CONTAINS “crowdstrikebsodfix[.]blob[.]core[.]windows[.]net” OR destinationhostname CONTAINS “crowdstrike[.]fail” OR destinationhostname CONTAINS “crowdfalcon-immed-update[.]com” OR destinationhostname CONTAINS “supportportal[.]crowdstrike[.]com” OR destinationhostname CONTAINS “bsodsm8rLIxamzgjedu[.]com” OR destinationhostname CONTAINS “crowdstrike0day[.]com” OR destinationhostname CONTAINS “crowdstrikefail[.]com” OR destinationhostname CONTAINS “crowdstrikehealthcare[.]com” OR destinationhostname CONTAINS “crowdstrike-falcon[.]online” OR destinationhostname CONTAINS “clownstrike[.]co[.]uk” OR destinationhostname CONTAINS “crowdstrike[.]woccpa[.]com” OR destinationhostname CONTAINS “hoo[.]be” OR destinationhostname CONTAINS “crowdstrike-bsod[.]com” OR destinationhostname CONTAINS “crowdstrikebug[.]com” OR destinationhostname CONTAINS “microsoftcrowdstrike[.]com” OR destinationhostname CONTAINS “crowdstrikebluescreen[.]com” OR destinationhostname CONTAINS “crowdstrikeupdate[.]com” OR destinationhostname CONTAINS “crowdstrikeoutage[.]com” OR destinationhostname CONTAINS “crowdstriketoken[.]com” OR destinationhostname CONTAINS “crowdstrikerecovery1[.]blob[.]core[.]windows[.]net” OR destinationhostname CONTAINS “crowdstrikedown[.]com” OR destinationhostname CONTAINS “crowdstrikeoutage[.]info” OR destinationhostname CONTAINS “crowdstrike[.]okta[.]com” OR destinationhostname CONTAINS “crowdstrikeclaim[.]com” OR destinationhostname CONTAINS “supportfalconcrowdstrikel[.]com” OR destinationhostname CONTAINS “crowdstrike[.]orora[.]group” OR destinationhostname CONTAINS “crowdstrike-helpdesk[.]com” OR destinationhostname CONTAINS “clownstrike. .co” OR destinationhostname CONTAINS “crashstrike[.]com” OR destinationhostname CONTAINS “isitcrowdstrike[.]com” OR destinationhostname CONTAINS “fix-crowdstrike-apocalypse[.]com” OR destinationhostname CONTAINS “crowdstrikefix[.]com” OR destinationhostname CONTAINS “crowdstrikefix[.]zip”)
- index=activity AND (rg_functionality=”Next Generation Firewall” OR rg_functionality=”Firewall” OR rg_functionality=”IDS / IPS / UTM / Threat Detection”) AND ipaddress NOT NULL AND ipaddress IN (“52[.]219[.]116[.]113″,”185[.]199[.]110[.]153″,”185[.]230[.]63[.]171″,”185[.]199[.]108[.]153″,”172[.]67[.]216[.]164″,”3[.]33[.]251[.]168″,”104[.]21[.]67[.]233″,”198[.]185[.]159[.]145″,”104[.]21[.]19[.]9″,”104[.]21[.]45[.]162″,”52[.]219[.]121[.]66″,”207[.]171[.]166[.]22″,”185[.]199[.]111[.]153″,”34[.]149[.]87[.]45″,”185[.]199[.]222[.]21″,”13[.]248[.]243[.]5″,”185[.]199[.]109[.]153″,”3[.]33[.]130[.]190″,”192[.]64[.]119[.]170″,”35[.]81[.]42[.]29″,”185[.]53[.]177[.]53″,”34[.]102[.]136[.]180″,”172[.]67[.]220[.]94″,”52[.]219[.]220[.]138″,”15[.]197[.]148[.]33″,”198[.]185[.]159[.]144″,”172[.]67[.]182[.]125″,”54[.]68[.]181[.]161″,”212[.]1[.]210[.]95″,”104[.]247[.]81[.]53″,”104[.]21[.]20[.]201″,”99[.]83[.]213[.]230″,”104[.]21[.]75[.]98″,”20[.]38[.]122[.]68″,”67[.]4[.]148[.]242″,”172[.]67[.]184[.]97″,”75[.]2[.]87[.]65″,”172[.]67[.]206[.]221″,”52[.]88[.]12[.]134″,”89[.]117[.]139[.]195″,”208[.]91[.]197[.]24″,”104[.]16[.]180[.]118″,”52[.]219[.]193[.]130″,”172[.]67[.]158[.]135″,”184[.]168[.]221[.]59″,”15[.]197[.]225[.]128″,”76[.]76[.]21[.]22″,”104[.]21[.]14[.]88″,”34[.]215[.]111[.]121″,”199[.]59[.]243[.]225″,”20[.]60[.]132[.]100″,”192[.]64[.]119[.]34″,”76[.]223[.]105[.]230″,”91[.]195[.]240[.]19″,”3[.]5[.]160[.]162″,”80[.]78[.]22[.]84″,”104[.]18[.]211[.]105″,”54[.]84[.]104[.]245″,”104[.]18[.]19[.]37”)
- index=activity AND rg_functionality=”Endpoint Management Systems” AND filehash NOT NULL AND filehash IN (“4f450abaa4daf72d974a830b16f91deed77ba62412804dca41a6d42a7d8b6fd0″,”d6d5ff8e9dc6d2b195a6715280c2f1ba471048a7ce68d256040672b801fda0ea”,”02f37a8e3d1790ac90c04bc50de73cd1a93e27caf833a1e1211b9cc6294ecee5″,”6010e2147a0f51a7bfa2f942a5a9eaad9a294f463f717963b486ed3f53d305c2″,”835f1141ece59c36b18e76927572d229136aeb12eff44cb4ba98d7808257c299″,”c44506fe6e1ede5a104008755abf5b6ace51f1a84ad656a2dccc7f2c39c0eca2″,”931308cfe733376e19d6cd2401e27f8b2945cec0b9c696aebe7029ea76d45bf6″,”52019f47f96ca868fa4e747c3b99cba1b7aa57317bf8ebf9fcbf09aa576fe006″,”48a3398bbbf24ecd64c27cb2a31e69a6b60e9a69f33fe191bcf5fddbabd9e184″,”be074196291ccf74b3c4c8bd292f92da99ec37a25dc8af651bd0ba3f0d020349″,”b1fcb0339b9ef4860bb1ed1e5ba0e148321be64696af64f3b1643d1311028cb3″,”2bdf023c439010ce0a786ec75d943a80a8f01363712bbf69afc29d3e2b5306ed”,”b6f321a48812dc922b26953020c9a60949ec429a921033cfaf1e9f7d088ee628″,”5ae3838d77c2102766538f783d0a4b4205e7d2cdba4e0ad2ab332dc8ab32fea9″)
Indicators of compromise (IoCs):
- crowdstrike.phpartners[.]org
- crowdstrike0day[.]com
- crowdstrikebluescreen[.]com
- crowdstrike-bsod[.]com
- crowdstrikeupdate[.]com
- crowdstrikebsod[.]com
- www.crowdstrike0day[.]com
- www.fix-crowdstrike-bsod[.]com
- crowdstrikeoutage[.]info
- www.microsoftcrowdstrike[.]com
- crowdstrikeodayl[.]com
- crowdstrike[.]buzz
- www.crowdstriketoken[.]com
- www.crowdstrikefix[.]com
- fix-crowdstrike-apocalypse[.]com
- microsoftcrowdstrike[.]com
- crowdstrikedoomsday[.]com
- crowdstrikedown[.]com
- whatiscrowdstrike[.]com
- crowdstrike-helpdesk[.]com
- crowdstrikefix[.]com
- fix-crowdstrike-bsod[.]com
- crowdstrikedown[.]site
- crowdstuck[.]org
- crowdfalcon-immed-update[.]com
- crowdstriketoken[.]com
- crowdstrikeclaim[.]com
- crowdstrikeblueteam[.]com
- crowdstrikefix[.]zip
- Crowdstrikereport[.]com
- iscrowdstrikefixed[.]com
- iscrowdstrikestilldown[.]com
- crowdstrikeoutage[.]info
- whatiscrowdstrike[.]com
- isitcrowdstrike[.]com
- crowdstrikefail[.]com
- crowdstrikeoopsie[.]com
- crowdstrike[.]fail
- crowdstruck[.]us
- crowdstruck[.]me
- howtofixcrowdstrikeissue[.]com
- www.fix-crowdstrike[.]com
- Crowdstrokeme[.]me
- www.crowdstrikeswag[.]com
- spain.crowdstrikebenefits[.]com
- us.crowdstrikebenefits[.]com
- Japan.crowdstrikebenefits[.]com
- pay.crowdstrikecure[.]com
- pay.crowdstrife[.]com
- pay.crowdstrikerecovery[.]com
- 52.219.116[.]113
- 185.199.110[.]153
- 185.230.63[.]171
- 185.199.108[.]153
- 172.67.216[.]164
- 3.33.251[.]168
- 104.21.67[.]233
- 198.185.159[.]145
- 104.21.19[.]9
- 104.21.45[.]162
- 52.219.121[.]66
- 207.171.166[.]22
- 185.199.111[.]153
- 34.149.87[.]45
- 185.199.222[.]21
- 13.248.243[.]5
- 185.199.109[.]153
- 3.33.130[.]190
- 192.64.119[.]170
- 35.81.42[.]29
- 185.53.177[.]53
- 34.102.136[.]180
- 172.67.220[.]94
- 52.219.220[.]138
- 15.197.148[.]33
- 198.185.159[.]144
- 172.67.182[.]125
- 54.68.181[.]161
- 212.1.210[.]95
- 104.247.81[.]53
- 104.21.20[.]201
- 99.83.213[.]230
- 104.21.75[.]98
- 20.38.122[.]68
- 67.4.148[.]242
- 172.67.184[.]97
- 75.2.87[.]65
- 172.67.206[.]221
- 52.88.12[.]134
- 89.117.139[.]195
- 208.91.197[.]24
- 104.16.180[.]118
- 52.219.193[.]130
- 172.67.158[.]135
- 184.168.221[.]59
- 15.197.225[.]128
- 76.76.21[.]22
- 104.21.14[.]88
- 34.215.111[.]121
- 199.59.243[.]225
- 20.60.132[.]100
- 192.64.119[.]34
- 76.223.105[.]230
- 91.195.240[.]19
- 3.5.160[.]162
- 80.78.22[.]84
- 104.18.211[.]105
- 54.84.104[.]245
- 104.18.19[.]37
- 213.5.130[.]58:443 – Remcos C2 IP
| File Name | SHA-256 Hash |
| Crowdstrike-hotfix.zip
|
C44506FE6E1EDE5A104008755ABF5B6ACE51F1A84AD656A2DCCC7F2C39C0ECA2 |
| Setup.exe | 5AE3838D77C2102766538F783D0A4B4205E7D2CDBA4E0AD2AB332DC8AB32FEA9 |
| instrucciones.txt | 4F450ABAA4DAF72D974A830B16F91DEED77BA62412804DCA41A6D42A7D8B6FD0 |
| maddisAsm_.bpl | 52019F47F96CA868FA4E747C3B99CBA1B7AA57317BF8EBF9FCBF09AA576FE006 |
| madexcept_.bpl | 835F1141ECE59C36B18E76927572D229136AEB12EFF44CB4BA98D7808257C299 |
| rtl120.bpl | B1FCB0339B9EF4860BB1ED1E5BA0E148321BE64696AF64F3B1643D1311028CB3 |
| vcl120.bpl | B6F321A48812DC922B26953020C9A60949EC429A921033CFAF1E9F7D088EE628 |
| datastate.dll | 6010E2147A0F51A7BFA2F942A5A9EAAD9A294F463F717963B486ED3F53D305C2 |
| maidenhair.cfg | 931308CFE733376E19D6CD2401E27F8B2945CEC0B9C696AEBE7029EA76D45BF6 |
| battuta.flv | BE074196291CCF74B3C4C8BD292F92DA99EC37A25DC8AF651BD0BA3F0D020349 |
| Remcos | 48A3398BBBF24ECD64C27CB2A31E69A6B60E9A69F33FE191BCF5FDDBABD9E184 |
References:
- INTERPOL report shows alarming rate of cyberattacks during COVID-19
https://www.interpol.int/en/News-and-Events/News/2020/INTERPOL-report-shows-alarming-rate-of-cyberattacks-during-COVID-19 - REMEDIATION AND GUIDANCE HUB: FALCON CONTENT UPDATE FOR WINDOWS HOSTS
https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/ - Q1 2024 Cyber Threat Landscape Report: Insider Threat & Phishing Evolve Under AI Auspices
https://www.kroll.com/en/insights/publications/cyber/threat-intelligence-reports/q1-2024-threat-landscape-report-insider-threat-phishing-evolve-under-ai - Falcon Sensor Content Issue from July 19, 2024, Likely Used to Target CrowdStrike Customers
https://www.crowdstrike.com/blog/falcon-sensor-issue-use-to-target-crowdstrike-customers/ - Threat Actors Exploit Recent CrowdStrike Outage to Ramp Up Suspicious Domain Creation
https://cyble.com/blog/threat-actors-exploit-recent-crowdstrike-outage-to-ramp-up-suspicious-domain-creation/ - Likely eCrime Actor Uses Filenames Capitalizing on July 19, 2024, Falcon Sensor Content Issues in Operation Targeting LATAM-Based CrowdStrike Customers
https://www.crowdstrike.com/blog/likely-ecrime-actor-capitalizing-on-falcon-sensor-issues/







