- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Research/Labs R&D
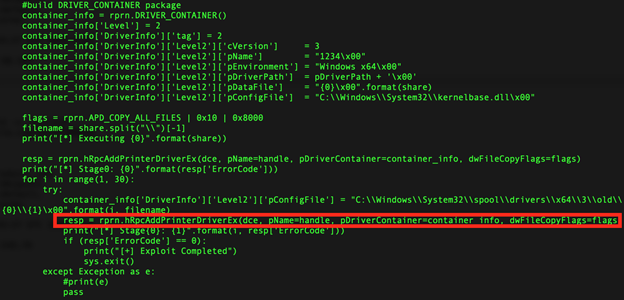
Figure 1: Example of Common PrintNightmare Exploit Variant Code
Introduction
Securonix Threat Labs R&D/Securonix Threat Research team has been actively monitoring and investigating the details of the critical PrintNightmare attacks (see Figure 1) [1, 3] targeting zero-day Microsoft Windows Print Spooler Service RCE Vulnerabilities (CVE-2021-1675, CVE-2021-34527).
Below are some of the key technical details and our recommendations on some possible Securonix predictive indicators/security analytics that can be used to detect the current and potentially future attack variants (the indicators may be updated as we receive more information).
Summary
What you need to know
- A high severity zero-day vulnerability is being exploited by threat actors, targeting the Windows Print Spooler service on Microsoft Windows Domain Controllers.
- This is a post-authentication vulnerability (attackers need to have pre-existing access credentials/foothold in your environment in order to exploit this.)
- CVE-2021-34527 allows attackers to take over affected servers via remote code execution with SYSTEM privileges, allowing them to install programs, view, change, or delete data, and create new accounts.
- Microsoft has confirmed that the vulnerability exists in ALL versions of windows, but is still validating on which versions it is fully exploitable.
What you can do
A patch that fully covers all PrintNightmare attack vectors is currently not available, and many recommended mitigations are impractical for some enterprise printing configurations. Instead focus on increased monitoring and rapid response.
Update: Microsoft has now released an out-of-band update for several versions of Windows to address CVE-2021-34527 (see https://msrc.microsoft.com/
PrintNightmare Attacks – Example of Recommended Log/Data Sources
To increase the chances of detecting this malicious activity associated with the PrintNightmare attacks, some of the key recommended log/data sources to collect/leverage:
- NTA logs w/SMB/opnum logging
- Raw endpoint logs w/process network activity visibility
- FIM/Endpoint logs w/file creation telemetry
- Microsoft Windows Printservice Admin/ops logs
Some of the additional recommended logs that might be helpful as well (Note – these might be of limited value for direct detection, but might detect some of the precursor/post-attack activity indirectly through some of the other existing detection use case available):
- Powershell logs
- RDP logs
- Windows Security/System logs
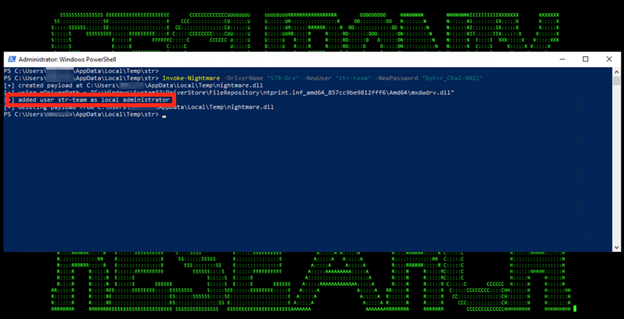
Figure 2: PrintNightmare Attack in Action
PrintNightmare Attacks – Attack Insights and Some Relevant Detection Observations
From our security analysis of the PrintNightmare attacks and monitoring of the real-world attacks targeting the attack/related vulnerabilities (see Figure 2), some relevant technical observations to help with detection/hunting are as follows:
- Based on our analysis of the relevant code/semantics of the attack vectors involved, the recommendation is to check/monitor RPC connections to RpcAddPrinterDriverEx() (opnum 89). Some of the known real-world attacks leverage this RPC function over a dozen times as part of exploitation attempts, which can also be used as an indicator.
Note – This security detection use case requires the ability to monitor NTA logs/RPC traffic.
- Monitoring for unusual processes spawned by spoolsv.exe and also for *rare* low/medium integrity processes making SMB RPC connections.
Note – This security detection use case requires raw endpoint logs/ability to monitor process activity; also, for spoolsv part, the recommendation is to use this to seed your threat hunting as in some environments this can be noisy.
- Checking for unusual *file creation* activity involving the following path: *:\\Windows\\System32\\spool\\drivers\\x64\\*\\old\\*.
Note – This security detection use case might require FIM/custom SACL file creation monitoring.
PrintNightmare Attacks – Threat Hunting – Sample Spotter Search Queries
Please find below some examples of the trivial Spotter queries to assist with initial threat hunting/retrohunting/identifying some possible attack behaviors based on the details above.
Note: Because of the rapidly changing attack landscape, the recommendation is not to rely on static IOAs/queries alone and to also implement the relevant Securonix analytics/predictive indicators for the best possible protection (see below).
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND resourcecustomfield7 ENDS WITH “spoolsv.exe” | rare destinationprocessname transactionstring1
(^str_devicecustomstring4_eventcode = “4909” OR ^str_devicecustomstring4_eventcode = “808”) AND message CONTAINS “0x45A” AND message CONTAINS “The print spooler failed to load a plug-in module”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “11” AND filename STARTS WITH “C:\Windows\System32\spool\drivers\x64\”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “7 ” AND resourcecustomfield5 STARTS WITH “C:\Windows\System32\spool\drivers\x64\” AND resourcecustomfield5 NOT ENDS WITH “kernelbase.dll” AND resourcecustomfield5 NOT ENDS WITH “unidrv.dll”
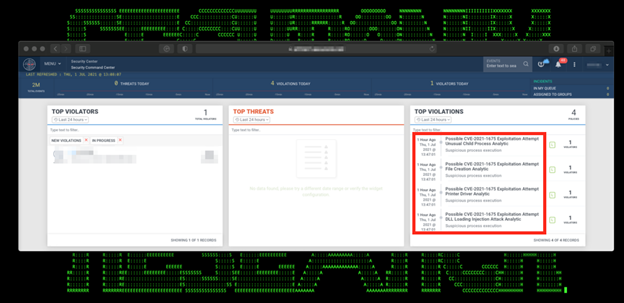
Figure 3: Example of the PrintNightmare Attacks Detection in Securonix Labs
PrintNightmare Attacks – Securonix Detection Update
Some high-level examples of some of the relevant Securonix behavior analytics/predictive indicators to increase the chances of early detection of the malicious activity associated with the PrintNightmare attacks including potential future variants of attacks (see Figure 3):
- Possible PrintNightmare Attack Peak RpcAddPrinterDriverEx() Malicious Driver Load Attempts Analytic
- Possible Print Server Exploitation Unusual Print Service Error Analytic
- Possible CVE-2021-1675 Exploitation Attempt Unusual Child Process Analytic
- Rare Parent-Child Relationship For User Analytic
- Possible CVE-2021-1675 Exploitation Attempt File Creation Analytic
- Possible CVE-2021-1675 Exploitation Attempt DLL Loading Injection Attack Analytic
and others.
Mitigation – Securonix Recommendations
Some possible actions recommended that can potentially help proactively mitigate the impact of the malicious exploitation activity associated with the PrintNightmare attacks:
- As per CISA and Microsoft guidances, disabling Windows Print spooler services in your DC and systems that do not print and/or GPO-based disabling of remote printing/inbound access to spooler (where feasible) [1, 4].
- Temporarily stopping Print Spooler service on your Domain Controllers (if feasible) and restarting after a patch is made available/deployed.
- Since some of the PrintNightmare exploit variants leverage a DLL dropped into *:\Windows\System32\spool\drivers, in some cases, a temporary workaround can be to restrict the ACLs on the drivers directory, e.g. Powershell-based example [2]:
$Path = “C:\Windows\System32\spool\drivers”
$Acl = (Get-Item $Path).GetAccessControl(‘Access’)
$Ar = New-Object System.Security.AccessControl.FileSystemAccessRule(“System”, “Modify”, “ContainerInherit, ObjectInherit”, “None”, “Deny”)
$Acl.AddAccessRule($Ar)
Set-Acl $Path $Acl
References
[1] US Cert. PrintNightmare, Critical Windows Print Spooler Vulnerability. July 1, 2021. https://us-cert.cisa.gov/ncas/current-activity/2021/06/30/printnightmare-critical-windows-print-spooler-vulnerability
[2] F. Viggiani. Fix for PrintNightmare CVE-2021-34527 exploit to keep your Print Servers running while a patch is not available. June 29, 2021. https://blog.truesec.com/2021/06/30/fix-for-printnightmare-cve-2021-1675-exploit-to-keep-your-print-servers-running-while-a-patch-is-not-available/
[3] Microsoft. Security assessment: Domain controllers with Print spooler service available. January 11, 2021. https://docs.microsoft.com/en-us/defender-for-identity/cas-isp-print-spooler
[4] Microsoft. Windows Print Spooler Remote Code Execution Vulnerability. July 1, 2021. https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527







