Electronic Medical Record (EMR) Application Security Monitoring
Increase electronic medical record (EMR) security and protect patient data privacy with advanced security monitoring and behavior analytics.
Increase electronic medical record (EMR) security and protect patient data privacy with advanced security monitoring and behavior analytics.

Collect relevant events from widely used EMR applications.

Detect suspicious behavior patterns which indicate an advanced cyberattack.
Visualize activity and threat patterns in your environment.

Get access to out-of-the-box reports for compliance monitoring.



Stolen healthcare records are worth ten times more than credit card numbers on the black market and hackers are following the cash. Manual auditing methods or simple, rule-based methods can help organizations meet basic compliance needs, but they do not protect patient data from insider threats or targeted cyberattacks.
Securonix for EMR Applications helps you increase your EMR application security. It leverages the latest advances in machine learning and artificial intelligence to baseline normal behavior patterns and detect suspicious data access patterns that can be a sign of compromise.
Securonix for EMR Applications integrates with most EMR applications, enabling organizations to rapidly deploy the Securonix solution and realize a rapid return on their investment.
Key use cases include:
Securonix UEBA and Next-Gen SIEM solutions provide a large assortment of connectors, allowing you to collect data from a variety of data sources including HR and IAM applications, network and security devices, endpoints, cloud data sources, and more. Correlating the anomalies in this data, along with EMR events, helps you detect and prioritize the highest-risk threats in your environment and increase your EMR application security.
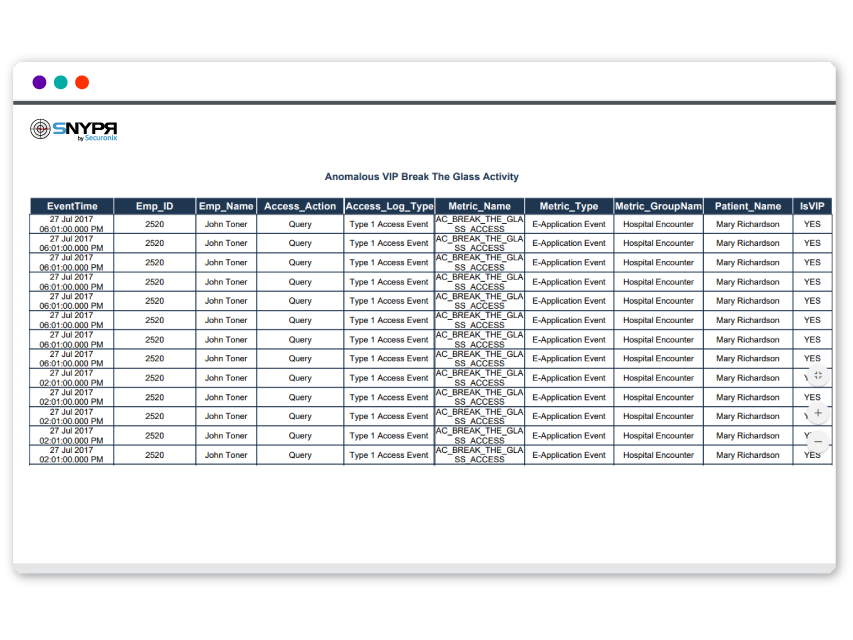
Securonix provides dashboards for EMR data and violations, enabling you to visualize activity and threat patterns in your environment.
The dashboards are fully customizable and shareable. Granular role-based access control can be implemented to limit access by job role.
Securonix is HITRUST CSF certified. Securonix provides out-of-the-box reports for compliance monitoring. Reports can be run on a schedule or run on an ad-hoc basis and cross-references globally recognized standards and business requirements including: HIPAA, PCI, NIST, ISO, and state laws for comprehensive security controls.
Reports can be exported or emailed to designated recipients. All major data formats are supported, including pdf, xls, doc, xml, and csv.

“Securonix is providing us actionable intelligence on threats related to patient data privacy. Our security and privacy teams are more efficient in investigating such threats thus improving our overall HIPAA compliance posture.”
Protecting patient data is essential, and Securonix can help. We help you increase your EMR application security by leveraging the latest advances in machine learning and AI to baseline normal behavior patterns and alert you to compromise.
Thanks for contacting us! We will get in touch with you shortly.
Thanks for contacting us! We will get in touch with you shortly.
We use first and third-party cookies and similar technologies to better understand your use of our website, personalize content, and display tailored advertisements based on your browsing activities. By clicking "Accept", you agree to our use of the above cookies. To reject our use of cookies, click “Deny.” To manage cookies, click “Opt-out preferences.”
Our site uses cookies and similar technologies to analyze site usage, personalize the site, and for online advertising purposes. To manage cookies, click “Opt-out preferences.”