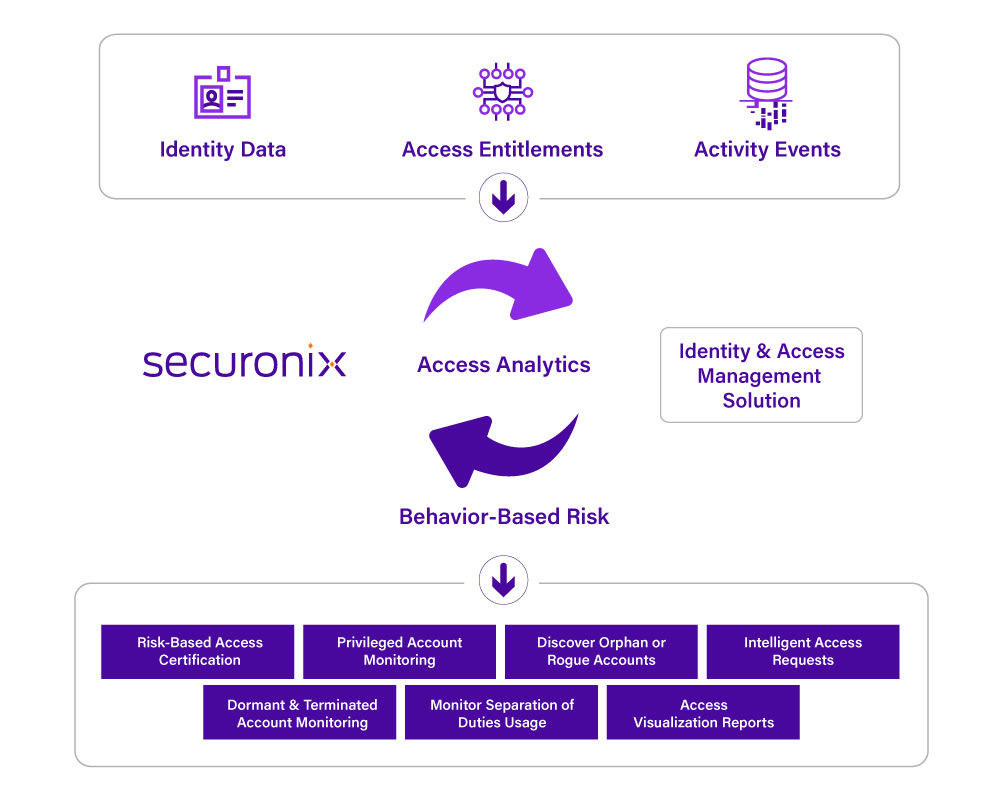
Monitor Privileged and Service Account Usage
Although privileged accounts create risk for organizations, they are essential for admins performing day-to-day operations. Due to the high level of access these accounts are granted, they are often prime targets and an easy entry point for cybercriminals.
By monitoring these accounts using identity analytics and intelligence, unusual behaviors such as privilege escalations, data exfiltration, credential sharing, and account compromise can be detected and resolved before larger damage is done.