Manufacturing and Supply Chain Cybersecurity
Secure Your Manufacturing & Supply Chain Operations Against Emerging Threats
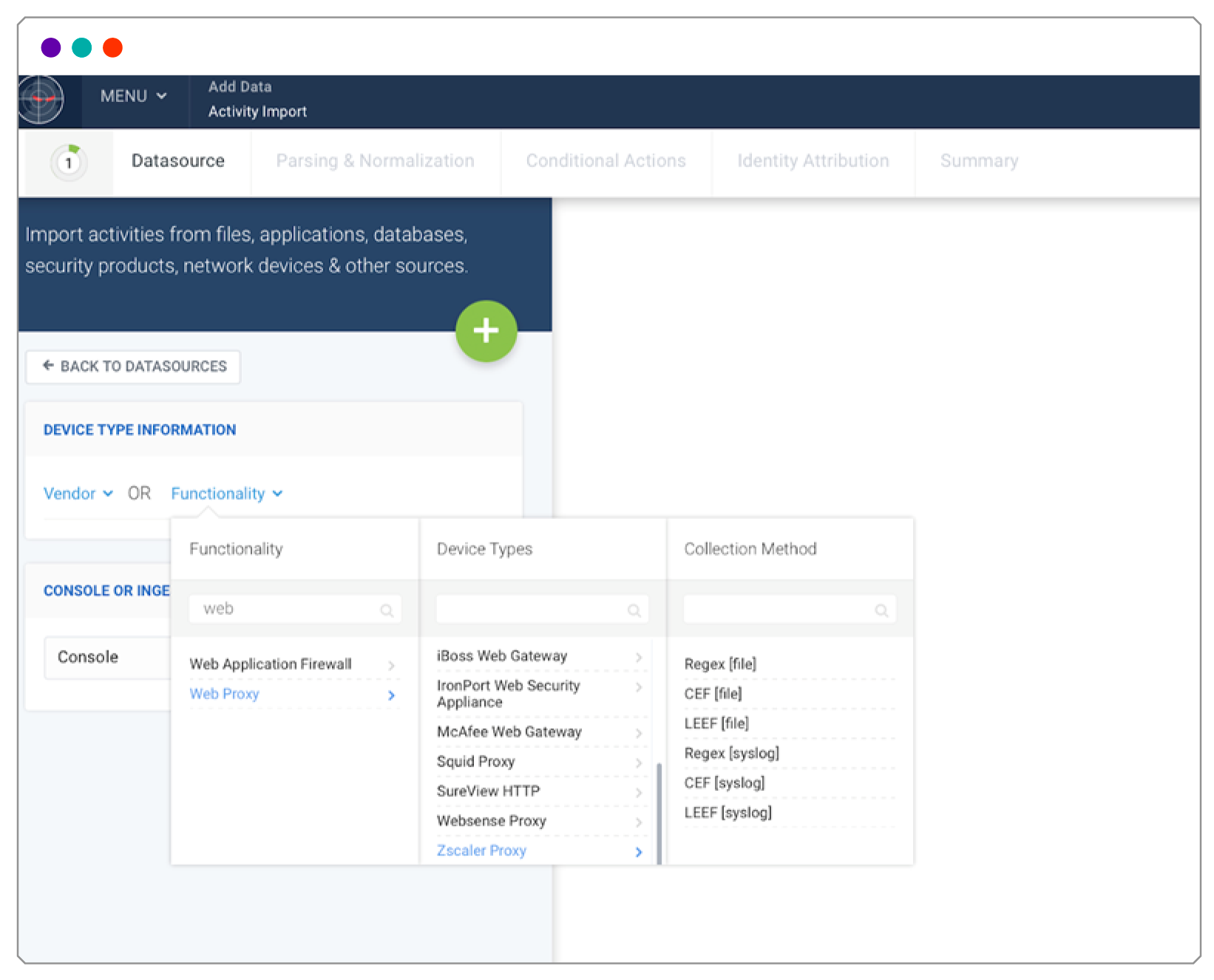
Manufacturing and supply chain industries are prime targets for cyber threats, from ransomware attacks to supply chain compromises. With complex global networks and increasing digital transformation, organizations must stay ahead of evolving threats. Securonix provides AI-driven threat detection, response, and compliance solutions tailored for manufacturers and supply chain operators.