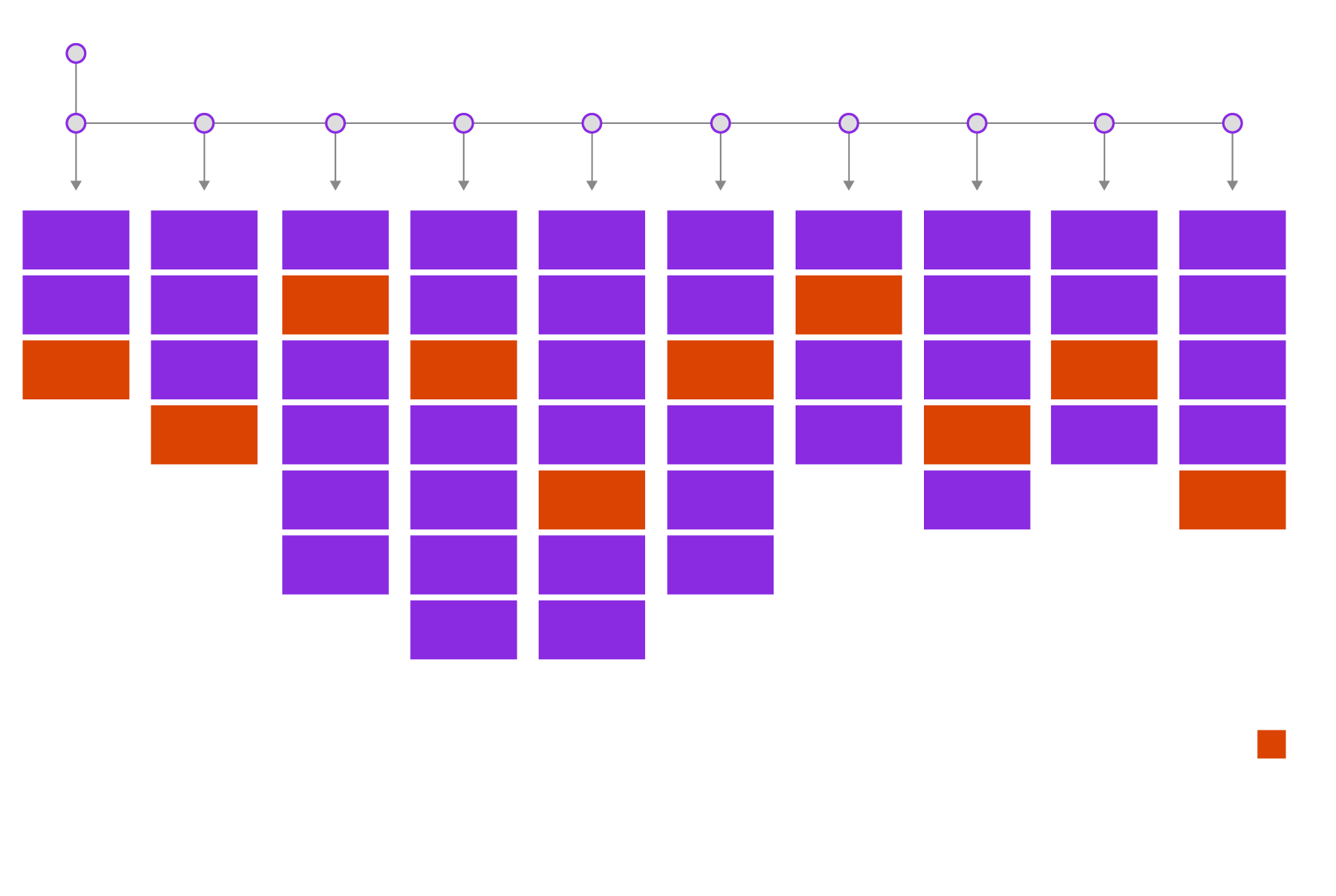
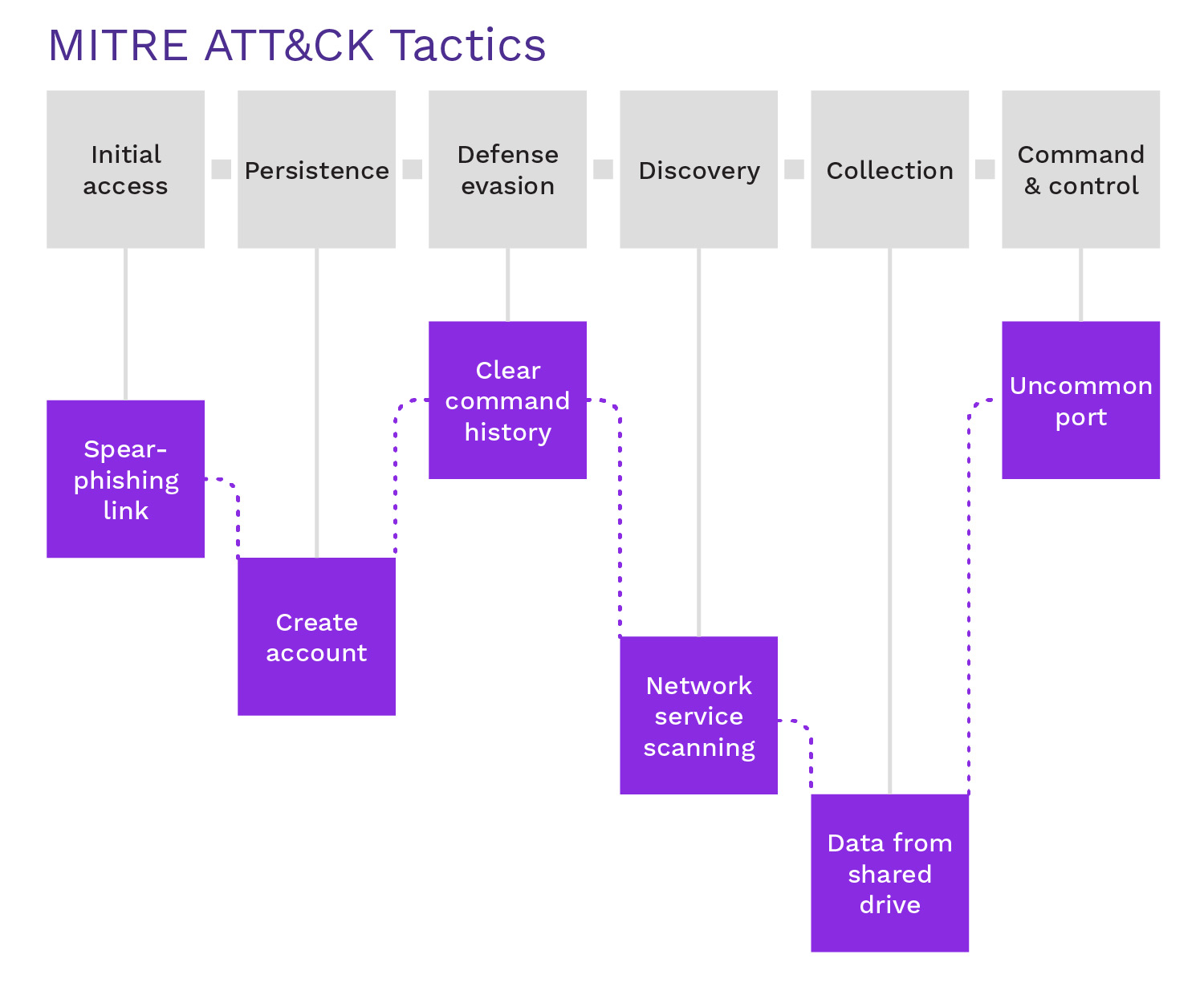
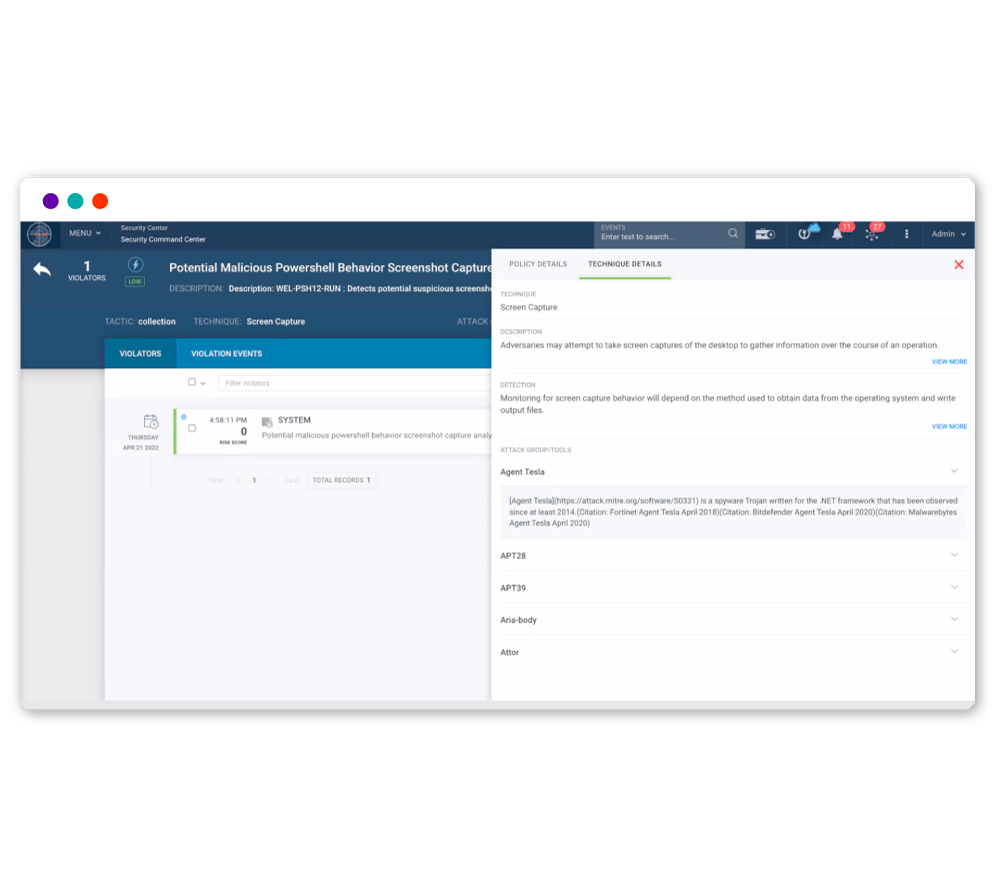
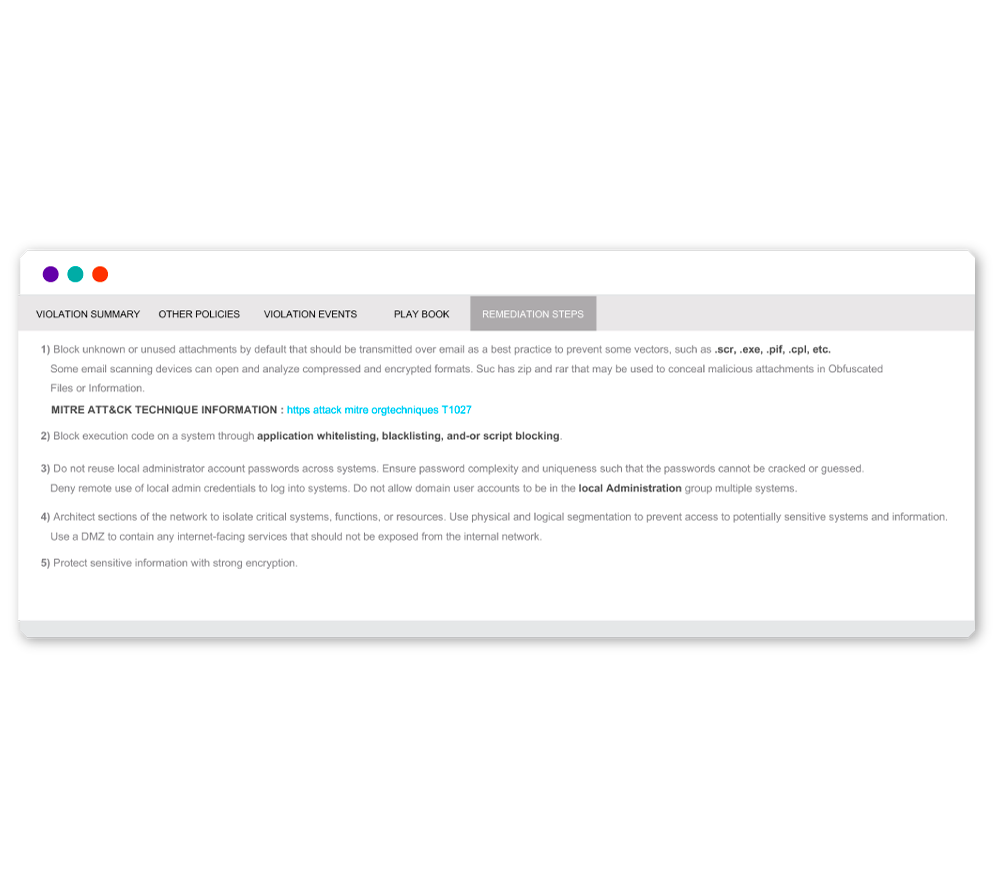
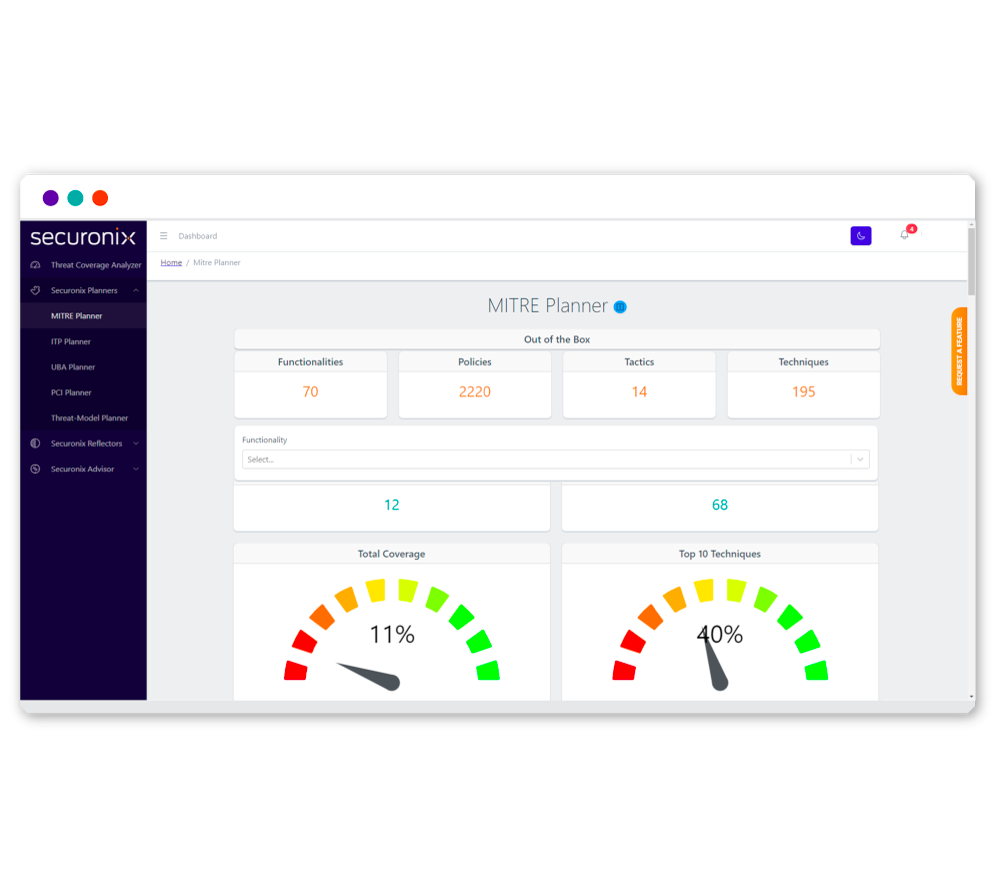
Automatically Align Events to MITRE ATT&CK
Connect related malicious activity to properly prioritize threats.
Securonix automatically links malicious activity to streamline threat prioritization, helping your security team stay ahead of evolving attacks.